On Feb 23, 2025, the Hegic Options protocol was exploited, resulting in a loss of approximately $80k.
Hegic is a decentralized options trading protocol built on Ethereum, enabling users to trade call and put options for crypto assets like ETH and wBTC in a trustless, non-custodial manner. It operates on a peer-to-pool model, where liquidity providers deposit assets into pools that fund options contracts. Users can purchase options with customizable strike prices and durations, while liquidity providers earn premiums and rewards for their contributions.
However, the exploited contract is quite old and may not have been used in production. It was exploited because there were some funds inside the contract - a relatively large amount.
Key information
Attacker: https://etherscan.io/address/0x4B53608fF0cE42cDF9Cf01D7d024C2c9ea1aA2e8
Vulnerable Contract: https://etherscan.io/address/0x7094E706E75E13D1E0ea237f71A7C4511e9d270B#code
Attack Tx1: https://etherscan.io/tx/0x260d5eb9151c565efda80466de2e7eee9c6bd4973d54ff68c8e045a26f62ea73
Attack Tx2: https://etherscan.io/tx/0x444854ee7e7570f146b64aa8a557ede82f326232e793873f0bbd04275fa7e54c
Exploit Analysis
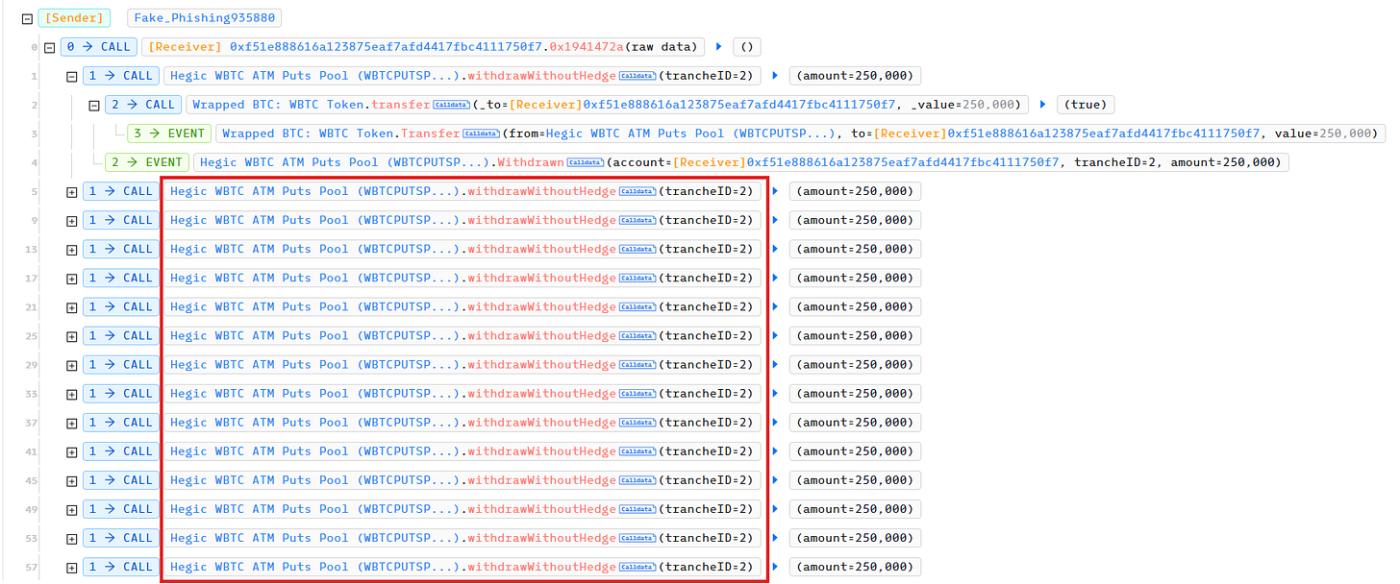
Looking at the attack transaction, we can see that the withdrawWithoutHedge function is called repeatedly inside the malicious transactions.
It seems like the attacker just needed to call the withdrawWithoutHedge function inside a for loop to drain the contract. How is this possible? Is there any restriction on the withdrawWithoutHedge function? Let's take a look at the source code of the withdrawWithoutHedge function.
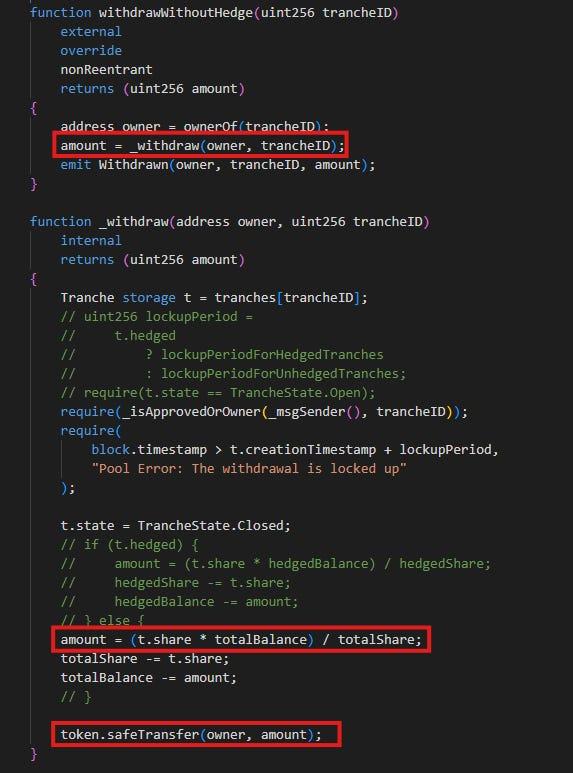
The withdrawWithoutHedge function is an external function that calls the _withdraw function. Inside the _withdraw function, we can see that the amount to be transferred is calculated from the t.share of the current "tranche". However, the t.share is not updated after withdrawal. From the code, we can see that the line which performs the state check for the current tranche (require(t.state == TrancheState.Open)) has also been commented out.
The vulnerable contract is the Hegic WBTC Puts Pool contract, which is quite an old contract that was deployed on Jan 04, 2022. However, the contract has had almost no interaction since then.
Lessons Learned
This exploit demonstrates why protocols must diligently track and manage funds in legacy or deprecated contracts. Additionally, thorough code review and auditing should be mandatory before any contract deployment to production environments to prevent similar vulnerabilities.