Introduction: In early June 2025, the cryptocurrency market was once again in turmoil due to a dramatic interaction between whale trader James Wynn and Binance founder CZ(CZ). Wynn publicly called out to CZ on social media, seeking dialogue, and CZ responded in his own unique way, and took the opportunity to throw out the idea of building a "dark pool" perpetual contract decentralized exchange (DEX). This series of events not only pushed deep-seated issues such as DEX transparency, user privacy protection, and MEV attacks to the forefront again, but also triggered extensive discussions and deep reflections in the industry on the future form of DEX. The different views of industry experts such as Alliance DAO founder Qiao Wang have added multiple dimensions to this discussion.
Chapter 1: The fall of the whale and the request for help - the fuse of the incident
James Wynn, one of the protagonists of the incident, is a controversial and legendary trader in the cryptocurrency field. He is famous for high-leverage, high-risk transactions on perpetual contract DEX platforms such as Hyperliquid. He once set an amazing record of turning a PEPE token contract with a principal of thousands of dollars into tens of millions of dollars in a short period of time. He was once dubbed the "Contract God of War" and "Hyperliquid's No. 1 Whale" by the community. Wynn is happy to disclose his trading strategies and positions on social media, attracting a large number of followers, but his aggressive trading style and huge exposure to market fluctuations also laid hidden dangers.
From the end of May to the beginning of June 2025, the market situation suddenly changed. James Wynn encountered ruthless sniping in the market during his high-leverage operations in both long and short directions. According to multiple sources and his subsequent statements, Wynn experienced multiple large-scale liquidations in just a few days, and the amount of losses gradually climbed from the initially reported $17.5 million to a staggering nearly $100 million. He pessimistically stated on social media that he was "hunted", implying that his liquidation was not a simple market behavior, but a premeditated, organized and targeted attack, which took advantage of the transparency of the DEX order book to accurately strike the liquidation line of his highly leveraged positions.
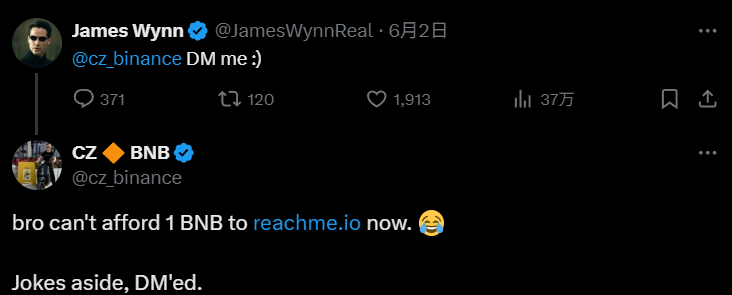
Under tremendous financial and psychological pressure, on June 2, James Wynn publicly sent a message to Binance founder CZ(CZ) on the X platform, expressing his urgent desire to establish a dialogue channel. Wynn emotionally questioned the market manipulation behavior and directly @CZ hoped to communicate privately. This public "help request" quickly set off the crypto community.
CZ's response was also quite dramatic. He first opened with a slightly teasing "Brother, you can't even take out 1 BNB for reachme.io now?" Reachme.io is a paid private messaging platform launched by CZ in March 2025, which aims to filter information by charging a small fee (such as 0.1 or 0.2 BNB) and promising to reply to paid messages. This joke not only hinted at Wynn's predicament at the time, but also cleverly promoted his new platform. Then, CZ changed the subject, "Just kidding, I've already sent a private message." This shows that he has noticed Wynn's predicament and is willing to communicate privately.
This brief interaction quickly became a hot topic in the crypto community due to the identities of both parties and the sensitivity of the incident. It was not only a look at a "fallen"whale, but more importantly, it directly led to CZ's subsequent thinking about the deep-seated problems of DEX and its solutions.
Chapter 2: CZ’s “Dark Pool” DEX Concept — Hitting the Pain Point of Transparency
Shortly after interacting with James Wynn, CZ published his profound reflections on the current DEX, especially the drawbacks of perpetual contract DEX, on the X platform, and formally proposed the idea of building a "dark pool" perpetual DEX.
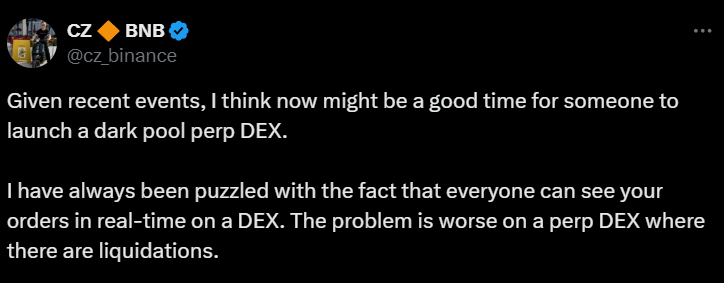
CZ made it clear in his tweet: “Given recent events (referring to James Wynn’s liquidation), I think now might be a good time to launch a dark pool perpetual decentralized exchange (DEX).” He then elaborated on his core confusion: “I have always been confused about the fact that everyone on DEX can see your orders in real time. This problem is even more serious on a perpetual decentralized exchange with liquidation.”
He further explained the potential risks that come with transparent order books:
- Front-running and MEV attacks : In the order book of a centralized exchange (CEX), although orders are also public, they are usually not directly associated with a specific individual. However, in a DEX, especially on a transparent blockchain, once the intention of a large order is exposed, it is easy to be captured by a MEV (Maximal Extractable Value) robot. These robots can make large traders' orders be traded at a worse price by preempting orders and creating "sandwich attacks", thereby increasing transaction costs and slippage. CZ figuratively calls it "others may buy first, which is actually front-running."
- Liquidation point exposure and malicious sniping : For perpetual contracts (or futures), the transparency of order and position information, especially the exposure of liquidation prices, is a more fatal problem. "If others can see your liquidation point, they may try to push the market to liquidate you. Even if you have $1 billion, others may gang up on you. This may be what we have seen recently." These words obviously point directly to James Wynn's experience. On a transparent DEX, attackers can clearly see the weak links of large leveraged positions, and by selling or buying at a specific price, they can accurately "detonate" these positions, thereby triggering chain liquidations and even manipulating local markets.
- Reference to Traditional Finance - Dark Pools : CZ pointed out that large traders in the field of traditional finance (TradFi) widely use "dark pools" to trade in order to avoid the above problems. "Large traders in TradFi use dark pools, which are usually 10 times larger than 'open pools' (i.e. ordinary order books)." Dark pools are private trading venues where orders from buyers and sellers are not publicly displayed before execution, thereby protecting trading intentions, reducing market shocks, and obtaining better execution prices.
Based on the above pain points, CZ proposed the core design concept of his "dark pool" perpetual DEX:
- Hide the order book : Either do not display the order book, or do not display the user's deposit and specific position information at all.
- Delayed disclosure : or deferring the disclosure of this information until a certain point after the transaction is completed.
- Technical Implementation Path : CZ specifically mentioned the use of "Zero-Knowledge Proofs (ZKPs) or similar cryptographic technologies" to achieve this transaction privacy and order confidentiality. ZKPs allow one party (the prover) to prove to another party (the verifier) that it has certain information or has completed certain calculations without revealing the specific content of this information, which is highly consistent with the dark pool DEX's need to hide transaction details. In addition, there is also a view that technologies such as Atomic Swaps and Hash Time Lock Contracts (HTLCs) may also play a role in building such systems.
CZ said he would "start researching" this direction. As one of the most influential figures in the cryptocurrency industry, CZ's statement undoubtedly dropped a bombshell on the future development of DEX, and also indicated that Binance, an industry giant, might personally explore this track.
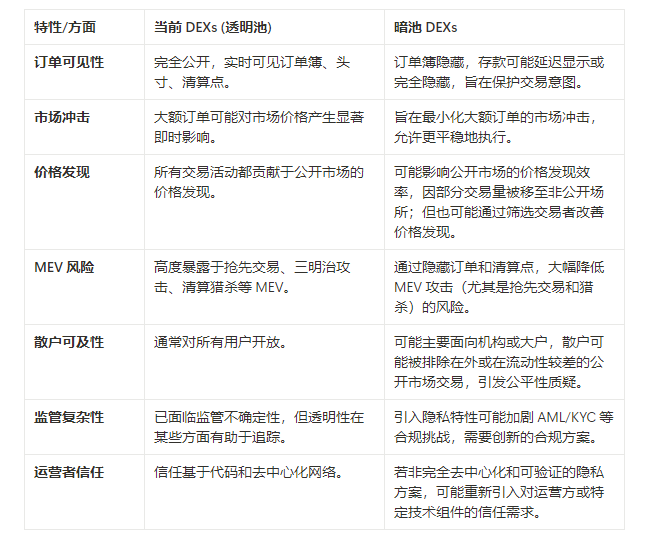
Chapter 3: The "double-edged sword" of transparency - the dilemma of the existing DEX mechanism and "counterparty information theory"
CZ's criticism of the shortcomings of DEX transparency touches on the core pain points of the current decentralized trading ecosystem. Although transparency, openness, and verifiability are the core advantages of blockchain technology, in the specific scenario of financial transactions, excessive transparency may become an "Achilles' heel."
- The "ghost" of MEV : MEV is a common problem on blockchains, especially smart contract platforms such as Ethereum. It refers to the behavior of miners (or validators, sorters, etc.) extracting additional value from user transactions through their power to package and sort transactions. Common types of MEV include:
- Front-running : Monitor pending large transactions in the mempool, place orders in advance at slightly higher (buy orders) or slightly lower (sell orders), and then reverse the process to make a profit after large transactions push up or down the price.
- Sandwich Attacks : Placing a buy order and a sell order before and after a large transaction (or vice versa) to "sandwich" it and thus arbitrage with no or low risk.
- Liquidation : Monitor the insufficiently collateralized positions of the lending agreements on the chain, preemptively trigger liquidation and obtain liquidation rewards. The liquidation of high-leverage positions on the perpetual contract DEX is a big "feast" for MEV robots. The existence of MEV makes ordinary users, especially large traders, like "swimming naked" when trading on DEX. Their trading intentions and potential profits are always coveted, resulting in increased transaction costs (high slippage) and deteriorating user experience. According to reports from Chainalysis and other institutions, MEV causes losses of up to hundreds of millions of dollars to DeFi users each year.
- Liquidity hunting and market manipulation : On perpetual contract DEX, due to the existence of high leverage, users' positions and estimated liquidation prices are relatively transparent on some platforms. This provides "sharks" with large amounts of funds with the opportunity to "target and blast". They can push prices to the intensive liquidation area by dumping or pulling up the market in a short period of time, triggering chain liquidations, thereby absorbing funds at low prices or selling at high prices, and exacerbating market volatility. James Wynn's experience is widely regarded as a typical case of such "liquidity hunting".
- The paradox of transparency and market efficiency : CZ also acknowledged the possible positive effects of transparency, namely, "increasing transparency allows market makers to absorb your large orders." In a fully transparent market, market makers can have a clearer understanding of market depth and order flow, thereby providing liquidity more efficiently. However, this ideal state is often difficult to achieve in an environment full of MEV and malicious actors.
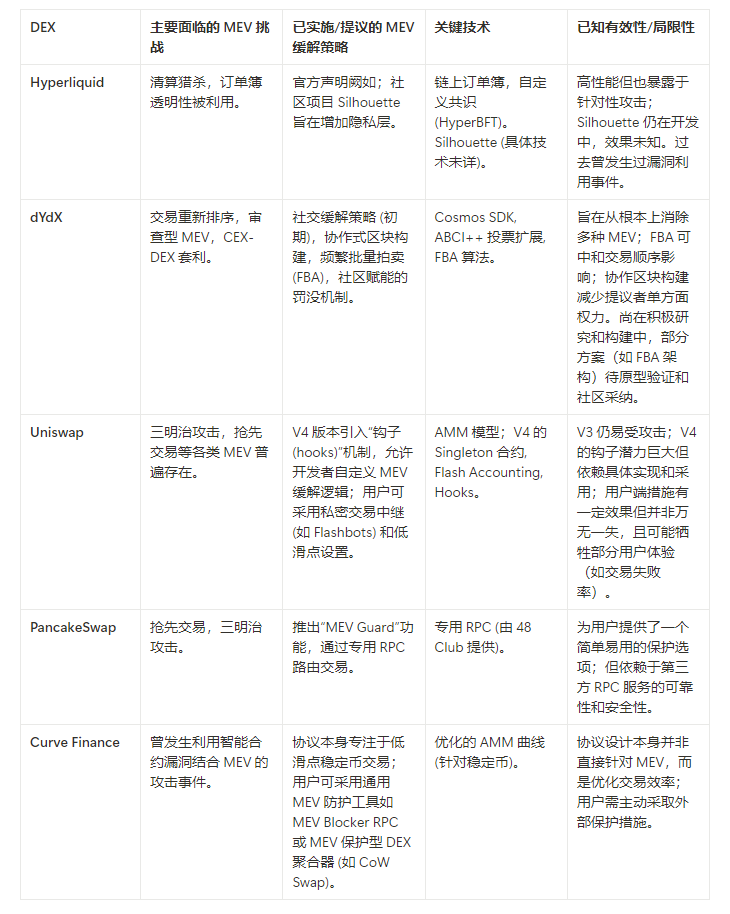
- Comparison of MEV mitigation strategies of mainstream DEXs:
Qiao Wang’s “Counterparty Information Theory” — From the perspective of market makers
However, not everyone fully agrees that dark pools are the ultimate solution for DEX. Qiao Wang, founder and core contributor of Alliance DAO, provided a different perspective from the perspective of market makers (MM), adding an important balanced perspective to the discussion.
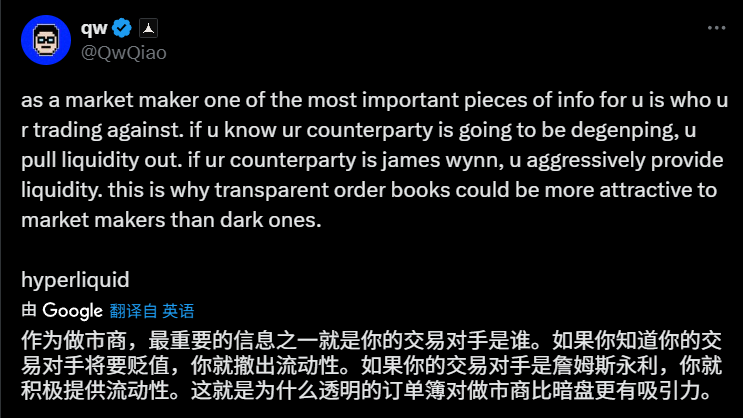
Qiao Wang said: "For a market maker, the most important piece of information is to know who you are trading with. If the counterparty is degenping (usually refers to those traders who take high risks, chase hot spots, and lack careful consideration), the market maker will withdraw liquidity. If the counterparty is James Wynn (representing those traders who may be "educated" by the market because of their aggressive style, but whose behavior patterns are relatively predictable and sometimes even bring trading opportunities), they will actively provide liquidity. This is why transparent order books may be more attractive to market makers than dark pools."
The core of Qiao Wang's point is the importance of "information symmetry" and "counterparty risk assessment" to market makers. In a transparent order book, market makers can judge the type and potential intentions of counterparties by analyzing information such as order flow and trading behavior patterns. This helps them better manage risks, adjust quotation strategies, and decide whether to provide liquidity and how deep liquidity to provide.
- Counterparty portrait : By observing the transparent market, market makers can identify which are "toxic flows" (usually referring to trading flows that have information advantages or intend to manipulate the market, which will cause market makers to lose money) and which are relatively "harmless" retail flows or arbitrage flows. In the face of the former, market makers will choose to avoid; in the face of the latter, they are happy to provide services and earn the spread.
- Alpha information and trading behavior : Qiao Wang further pointed out: "All other things being equal, whale with actual alpha information (unique information or strategic advantages that can bring excess returns) are more inclined to trade on (centralized) exchanges/dark pools. But this has no effect on Hyperliquid, because most contract whale do not have alpha information. They become whales through reckless risk-taking, which is simply the product of survivor bias." This passage reveals a cruel reality: many so-called "whale" who call the shots on perpetual contract DEXs, their success does not come from real information advantages or superb trading skills, but more from the huge profits they have made through extremely high risk exposure in a specific market cycle, which is the result of "survivor bias". The behavior patterns of such traders (such as James Wynn) are often public and predictable, and even their liquidation itself may become a trading opportunity for other market participants. For such "pseudo-alpha"whale, transparent order books may be more beneficial to market makers because their behavior is easier to interpret and exploit. Traders who truly possess alpha information will try every possible means to hide their trading intentions, and dark pools are naturally their first choice.
Qiao Wang's point of view reminds us that the design of DEX needs to strike a delicate balance between protecting ordinary users, preventing malicious manipulation, and ensuring market liquidity and market maker enthusiasm. Complete darkness may breed new uncertainties, while selective transparency may be more beneficial to specific types of markets and participants. This also explains why CZ also retained a hint of hesitation in his proposal: "I don't want to argue about which statement is right or wrong. Different traders may prefer different types of markets."
Chapter 4: Technical Path and Challenges of Dark Pool DEX
CZ's "dark pool" DEX concept is not a castle in the air, and there is a certain amount of technical exploration and theoretical support behind it. However, putting this concept into practice still faces many technical and non-technical challenges.
Exploration of technical implementation paths:
- Zero-knowledge proof (ZKPs) : This is the technical solution first recommended by CZ. The core advantage of ZKPs is "proving knowledge without leaking knowledge". In dark pool DEX, ZKPs can be used for:
- Confidential Transactions : Users can submit encrypted orders and use ZKPs to prove the validity of the order to the smart contract (such as sufficient account balance, compliance with order parameters, etc.) without revealing the specific price and quantity of the order.
- Hidden balances and positions : Users’ account balances and positions can also be managed through ZKPs, with proofs generated by users only when necessary (such as during margin checks or liquidations), and no plaintext data is stored on the chain.
- Privacy protection of matching engine : The order matching process can also be carried out off-chain or in a trusted execution environment (TEE), and only the matching results and necessary proofs are put on the chain. At present, teams such as StarkWare (StarkNet), zkSync, and Aztec have made significant progress in ZK Rollup and privacy solutions, providing a technical foundation for building privacy DEX.
- Multi-party secure computation (MPC) : MPC allows multiple parties to jointly calculate a function, and each party cannot know the input data of other parties. In the DEX scenario, MPC can be used to build a decentralized order matching and clearing mechanism to ensure that the transaction intentions of all parties are not disclosed during the order matching process.
- Trusted Execution Environments (TEEs) : Hardware-level security technologies such as Intel SGX can provide an isolated execution environment that ensures the confidentiality and integrity of the code and data running in it. The storage and matching of order books can be performed in a TEE, thus hiding it from the outside world.
- Commit-Reveal Schemes : Users submit transactions in two phases. In the first phase, an encrypted commitment (hash value) is submitted, and in the second phase, the specific transaction content is revealed. This can prevent front-running to a certain extent, but it has a certain impact on latency and user experience.
- Batch Auctions : Orders within a period of time are collected and matched at a unified clearing price. This can reduce the impact of MEV because all transactions within a block are settled at the same price, making front-running unprofitable. CoW Protocol (formerly Gnosis Protocol) is a typical representative of the batch auction mechanism.
Challenges:
- Technical complexity and cost : Advanced cryptographic technologies such as ZKPs have high implementation barriers and high computational overhead, which may lead to increased transaction delays and higher gas fees. How to optimize performance and cost while ensuring security and privacy is a core technical challenge.
- User experience and adoption threshold : The operation process of dark pool DEX may be more complicated than traditional transparent DEX, requiring users to understand new concepts and tools. How to design a simple and easy-to-use user interface and lower the user threshold is the key to promotion.
- Liquidity fragmentation and guidance : If dark pool DEX fails to attract sufficient liquidity and trading depth is insufficient, it may lead to increased slippage, offsetting its privacy advantage. In a market with fierce competition among many DEXs, how to guide liquidity and establish network effects is a major challenge. Qiao Wang's point of view also implies that if market makers are deterred from dark pools due to information asymmetry, liquidity problems will become more prominent.
- Compliance and regulatory risks : Although the anonymity and privacy of dark pools can protect well-intentioned users, they can also be used by malicious actors for money laundering, illegal financing and other activities. How to meet the privacy needs while complying with the AML (anti-money laundering) and KYC (know your customer) regulations in different jurisdictions is a very tricky balance. Regulators are often cautious or even opposed to completely anonymous trading systems.
- Centralization risk : Some dark pool designs (such as reliance on centralized sorters or specific TEE hardware) may introduce new centralized risk points or single points of failure. How to ensure that dark pool DEX does not lose its "decentralized" nature while pursuing privacy also requires careful consideration.
- Effectiveness of price discovery mechanism : The transparency of the order book is an important mechanism for price discovery in traditional markets. Dark pools, while hiding orders, may also affect the efficiency and transparency of price discovery, leading to price differences with “open pools” and thus creating arbitrage opportunities, but may also make the prices in dark pools unfair.
Chapter 5: Responses to existing DEXs and explorers of the privacy track
Faced with problems such as MEV and privacy leaks, existing DEX and DeFi protocols are not indifferent, and some solutions and privacy-focused explorers have emerged.
MEV mitigation measures for existing mainstream DEXs:
- dYdX : As the leading perpetual contract DEX, dYdX adopted an independent application chain architecture based on Cosmos SDK in its V4 version. Its proposed solutions include improving processing speed and reducing on-chain footprint through off-chain order books and matching engines. In addition, dYdX is also exploring mitigating MEV through fairer transaction sorting mechanisms (such as frequent batch auctions FBA) and cooperation with validators (such as through encrypted memory pools or threshold encryption). Its community has discussed combating MEV by "delaying transaction execution" or "randomizing transaction order", and allowing users to set higher slippage tolerance to deal with front-running transactions.
- Uniswap : As the leader of spot DEX, Uniswap introduced the "Hooks" function in its V4 version, allowing developers to customize the behavior of the liquidity pool, which provides the possibility of integrating MEV mitigation tools (such as MEV-Blocker, Flashbots Protect, etc.) or implementing more complex order types. Users can also submit private transactions through third-party services (such as MistX, ArcherSwap).
- PancakeSwap : In its “MEV Guard” feature, PancakeSwap works with block builders to try to send users’ transactions directly to builders to avoid being captured by MEV bots in the public memory pool.
- CoW Protocol : By sending transaction intentions to the solver network and matching them in batch auctions, it aims to provide users with MEV protection and optimal execution prices.
- Flashbots : Although not a DEX, Flashbots provides services such as MEV-Boost, which allows block producers to receive private transaction bundles from searchers, which to a certain extent regulates the MEV market and provides users with a channel to avoid conventional MEV attacks.
However, most of these measures are mitigation measures and do not fundamentally solve the inherent problems of transparent DEX. Some solutions rely on trusted third parties, while others may sacrifice some decentralization or increase transaction complexity.
Privacy-focused DEXs and protocols:
Before CZ proposed the idea of dark pool DEX, a number of projects in the crypto field had already been working hard on the privacy trading track:
- Penumbra : A privacy-focused cross-chain DEX that uses zero-knowledge proofs to shield transaction amounts, types, and user identities, aiming to provide a completely private trading environment.
- Railgun : An on-chain privacy system that allows users to deposit tokens into private balances through smart contracts and transfer and interact with DeFi protocols without revealing the source, amount, or destination.
- Aztec Network : Through its zk-Rollup technology (such as zk.money), it provides privacy protection for transactions on Ethereum. Users can conduct transactions within its privacy layer and ultimately settle on the Ethereum mainnet.
- Secret Network : A privacy-centric L1 blockchain whose smart contracts ("secret contracts") run in a trusted execution environment (TEE) and encrypt data by default, providing underlying support for building privacy DEX and DeFi applications.
- Renegade : A project that aims to build a dark pool DEX based on multi-party computation (MPC) and zero-knowledge proof, focusing on providing privacy protection and MEV resistance for institutional-grade transactions.
- Silhouette : According to Bankless, this is a project that aims to add a layer of privacy to existing order book DEXs such as Hyperliquid, allowing users to submit encrypted orders which will be decrypted only after matching. It is still in the development stage.
The exploration of these projects provides practical references and technical reserves for CZ's dark pool DEX concept. Their success and failure experiences will also provide valuable lessons for later generations.
Chapter 6: Potential Market Impact and Future Outlook of Dark Pool DEX
Once CZ's "dark pool" perpetual DEX concept is successfully implemented and widely accepted by the market, it will undoubtedly have a profound impact on the existing cryptocurrency trading ecosystem.
Potential Market Impact:
- Attract institutional investors and large traders : Institutional investors and high-net-worth traders have a strong demand for transaction privacy and reducing market impact. If dark pool DEX can effectively solve these pain points, it is expected to attract a large number of institutional funds that were originally deterred from DEX due to concerns about MEV and front-running.
- Reshape the DEX competition landscape : Currently, the DEX track is highly competitive and homogenized. A dark pool DEX with good experience, security and reliability will form a strong differentiation advantage and may change the market share of existing DEX.
- New challenges to CEX : Although CEX still has advantages in user experience, fiat currency deposits and withdrawals, DEX is superior in asset self-custody, transparency (referring to transparency of rules, not transparency of transaction process) and anti-censorship. If dark pool DEX can make up for its shortcomings in transaction privacy and efficiency, it may further erode the market share of CEX, especially in the field of pure coin-to-coin transactions and derivatives.
- Promoting innovation and application of privacy technology : CZ’s appeal and Binance’s resource investment may greatly promote the research and development and application of privacy-enhancing technologies such as ZKPs and MPC in the DeFi field, giving birth to more innovative privacy solutions.
- Triggering a discussion about "fairness" : The emergence of dark pools may intensify discussions about market fairness. On the one hand, it protects large traders; on the other hand, as Qiao Wang worries, if liquidity is mainly concentrated in dark pools, it may be disadvantageous to small and medium-sized retail investors and some market makers who are accustomed to transparent markets, forming a certain degree of "market segmentation" or "information asymmetry."
Future Outlook and Thoughts
CZ's "dark pool" DEX concept is a concentrated outbreak and response to the deep contradictions of DEX under the catalysis of a specific event (James Wynn's liquidation). It represents the continuous exploration of the balance point between transaction efficiency, user protection and market fairness in the evolution of DEX.
- Possibility of hybrid model : In the future, the DEX market is unlikely to be completely monopolized by dark pools or open pools. What is more likely to emerge is a hybrid model, that is, a DEX platform provides both "open pool" and "dark pool" options, or through a layered design, different types of traders and orders can independently choose the most suitable trading environment.
- Evolution of regulation : With the increase of privacy DeFi applications such as dark pools, the attitudes and policies of regulators will continue to evolve. How to prevent risks while encouraging innovation and achieve "responsible privacy" will be a common challenge faced by regulators and projects. Compliance tools based on ZKPs (such as proving that a user is not on a sanctions list without revealing their specific identity) may become a solution.
- The importance of user education : Whether it is a dark pool or other complex DeFi products, user education is crucial. Users need to understand the pros and cons of different mechanisms, potential risks, and how to protect themselves.
- "Alpha" and "Noise" : Qiao Wang's discussion on "alpha information" and "survivor bias whale" reminds us to make a deeper analysis of market phenomena and trading behaviors. Not all those who seek privacy are "smart money", and not all those who are active in transparent markets are "lambs to be slaughtered". The complexity of the market and the diversity of participants determine that there is no perfect solution once and for all.
James Wynn's explosion tragedy unexpectedly became a catalyst for DEX reflection and evolution. CZ's "dark pool" concept points out a possible direction for this evolution. This road is destined to be full of technical challenges, theoretical games and market tests. But just like the development process of blockchain technology itself, it is in the continuous trial and error, iteration and pursuit of better solutions that the boundaries of DeFi can be continuously expanded and its vitality can be demonstrated. In the future, we may see a new paradigm of decentralized trading that is more diversified, more resilient, and better able to meet the needs of different users. And the discussion on transparency and privacy, fairness and efficiency will always accompany it.







