Author: Ryan Yoon, Yoon Lee | Tiger Research
Key Points
Truly Permissionless Deployment: Unlike competitors requiring approval processes or whitelists, Hyperlane allows any developer to instantly deploy and connect to different chains without gatekeeping, creating an access model fundamentally different from other interoperability protocols.
Flexible Modular Security: While other bridging protocols use fixed security models, Hyperlane's Interchain Security Module (ISM) allows applications to configure their own security requirements (from basic validator signatures to multi-layered verification), enabling both rapid small transactions and high-security asset transfers on the same infrastructure.
Developer-First Architecture: Hyperlane's TypeScript SDK, CLI tools, and comprehensive documentation lower the technical barriers for cross-chain integration, allowing interchain message passing through simple APIs without complex custom implementations.
1. A Turning Point in Blockchain Connectivity
The blockchain ecosystem is transitioning from isolated development to true interconnectivity. Projects are no longer building closed environments but increasingly seeking integration within a broader network.
[The rest of the translation follows the same professional and accurate approach, maintaining the technical nuances and specific terminology as requested.]For example, Ethereum's EVM supports 18 decimal places, while Solana's SVM uses 9 decimal places. Overcoming even small differences while maintaining security and reliability is one of Hyperlane's key technical achievements.
Hyperlane introduced the "Hyperlane Warp Route" to address the challenges of connecting different chains. Hyperlane Warp Route is a modular cross-chain asset bridge that supports permissionless token transfers between chains and enables the movement of various assets across different environments.
In essence, Hyperlane Warp Route operates based on the nature and use cases of assets. Sometimes they function like vaults, sometimes like currency exchange offices, and sometimes like direct wire transfers—each route type provides an appropriate method for each scenario. All these processes leverage Hyperlane's interchain messaging to run in different virtual machine environments.
Native Token Warp Routes: Support direct cross-chain transfers of native fuel tokens (such as ETH) without wrapping.
Collateralized ERC20: Lock ERC20 tokens as collateral on the source chain for cross-chain transfers.
Synthetic ERC20: Mint new ERC20 tokens on the target chain to represent the original token.
Multi-Collateral Warp Routes: Allow multiple collateral tokens to provide liquidity.
Dedicated Warp Routes: Add advanced features or integrate specific use cases (such as vaults, fiat-backed tokens).
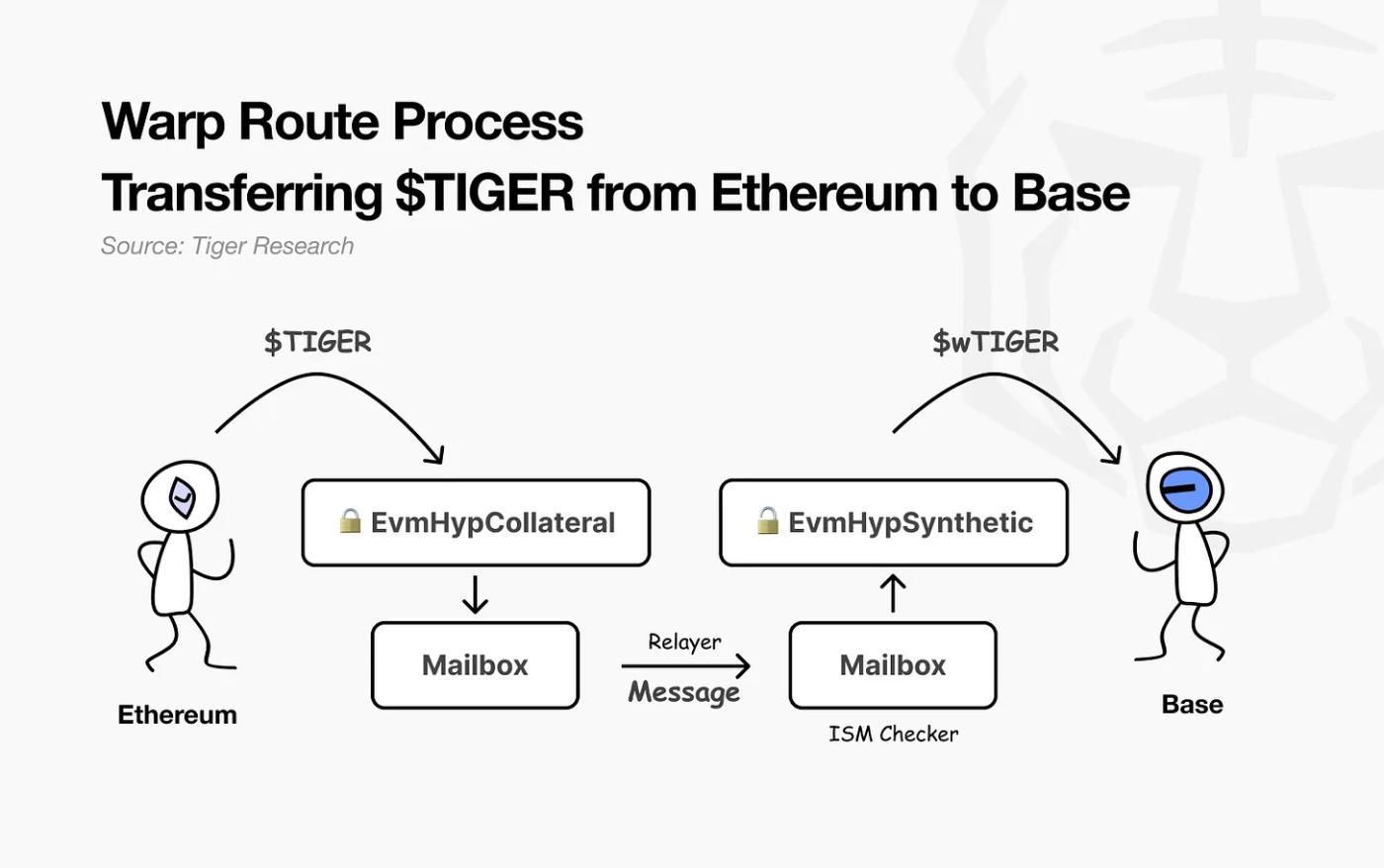
Let's examine a practical example using the lock-and-mint model. A developer named Ryan wants to transfer Tiger tokens ($TIGER) issued on Ethereum to the Base network.
Ryan first deploys a Hyperlane Warp Route contract on Ethereum and deposits $TIGER tokens into this contract (EvmHypCollateral). Then, the Ethereum Mailbox generates and sends a message instructing the Base network to mint a wrapped version of the Tiger token.
Upon receiving the message, the Base network uses the Interchain Security Module (ISM) to verify its authenticity. If verification is successful, the Base network will directly mint wrapped Tiger tokens ($wTIGER) to the user's wallet.
Hyperlane Warp Route plays a crucial role in expanding Hyperlane's vision of modular, permissionless interoperability across different chains. Developers only need to configure contracts according to each chain's characteristics. The remaining process—message transmission, verification, and delivery—is handled by Hyperlane's infrastructure, enabling developers to achieve cross-environment connections without dealing with complex translation mechanisms.
4.1. Preparing for Accelerated Growth
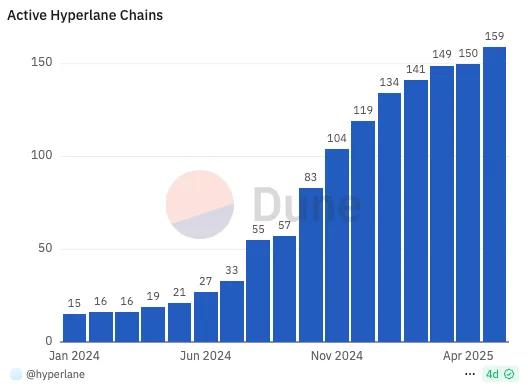
Source: Dune
Hyperlane currently supports over 150 blockchain networks, including ETH, Solana, and Avalanche. With billions of dollars in bridged assets, the protocol has clearly moved beyond the experimental stage into commercial-scale deployment.
One of the most notable trends is the emergence of network effects. As more chains connect to Hyperlane, the motivation for other chains to join also grows. New entrants can instantly access the liquidity, user base, and interoperability of connected networks. Developers favor infrastructure with broad chain compatibility, while users seek greater utility and flexibility across assets.
Two core competitive advantages are driving Hyperlane's growth:
Unparalleled connectivity across over 150 chains - far surpassing competitors.
Permissionless architecture, significantly reducing access friction and accelerating ecosystem expansion.
These advantages together provide Hyperlane with a structurally superior growth trajectory compared to traditional interoperability solutions.
4.2. Empowering $HYPER Utility
With the launch of the HYPER token in April 2025, Hyperlane faces the primary challenge of ensuring the token's long-term utility. The key question is whether HYPER can evolve from a speculative asset to a functional, indispensable part of protocol operations.
Hyperlane first introduced the "Expansion Rewards" program to ensure users receive more rewards as they engage more with the ecosystem. The program allocates 25.5% of the total token supply, distributing $HYPER tokens every three months based on each user's protocol usage. Users accumulate points through activities, which are then proportionally converted into token rewards. This model functions much like a credit card rewards system - the more you use, the more you earn.
Two reward mechanisms further reinforce this structure:
Chain Bonus: Provides an additional 25% reward for transactions on chains using Hyperlane as the primary bridge.
Long-Term Holding Bonus: Offers up to 60% additional rewards for users continuously holding staked $HYPER (stHYPER).
This system aims to reward high usage and long-term participation, effectively encouraging loyal users to become economic stakeholders in the protocol's growth.
The incentive model's goal is clear: the more users interact with the protocol and remain active, the greater their rewards. If this four-year plan operates as expected, it is anticipated to generate a powerful network effect throughout the Hyperlane ecosystem. These dynamics follow a self-reinforcing cycle:
Increased usage leads more chains to seek integration
Network expansion creates broader cross-chain options for users
More options accelerate new user acquisition
For networks like Hyperlane experiencing rapid chain expansion, this reward structure can significantly enhance user satisfaction and serve as a catalyst for further growth.
However, the concentrated utility model also brings risks. Since $HYPER's primary use case is closely tied to Hyperlane's interoperability protocol, any decline in bridge total demand or cross-chain activity could directly impact token demand. Continuous monitoring of market conditions and usage trends will be crucial.
Source: Symbiotic
Another core function of HYPER is network security. Users can stake HYPER to obtain stHYPER (a liquid staking token), supporting the economic security of Hyperlane's default ISM. Validators (responsible for verifying cross-chain message validity) receive staking rewards for correct validation. Conversely, if they sign invalid messages or engage in malicious behavior, their staked tokens will be slashed. This slashing is distributed among all stakers and used to compensate affected users.
Ultimately, $HYPER tokens are designed to be more than just a trading asset. By combining usage incentives, stake-based security, and long-term participation, it becomes a fundamental component of the Hyperlane network. This architecture creates a self-reinforcing cycle:
More protocol usage leads to more $HYPER distribution
More staking enhances network security
Higher reliability attracts more users and chains
If this mechanism operates as expected, $HYPER will play a core role in both network operations and security assurance - supporting the sustainability and growth of the entire Hyperlane ecosystem.
4.3. Enhancing Security
Perhaps most impressively, Hyperlane has maintained stable operations throughout its development without major security incidents. This record is due to the stable management of its multi-sig validator group and a conservative approach to default configurations.
Strengthening security remains an ongoing priority. Through its bug bounty program, Hyperlane offers rewards up to $2.5 million for identifying critical smart contract vulnerabilities. This has proven to be an effective mechanism for incentivizing security researchers to actively participate.
That said, risks remain - especially considering the protocol's open-source and permissionless nature. Continuous monitoring is necessary, particularly where user-independent custom modules might introduce unforeseen vulnerabilities.
4.4. Becoming Core Infrastructure for an Interoperable Web3 Era
As interoperability becomes a basic requirement for Web3, Hyperlane's progress and potential have even greater significance. If its vision is realized, users will be able to interact with blockchain-based services without even considering which chain they are interacting with.
This represents a blueprint for a truly unified blockchain ecosystem. At this critical moment, Hyperlane's next steps will be key to determining the extent to which this vision can be achieved.







