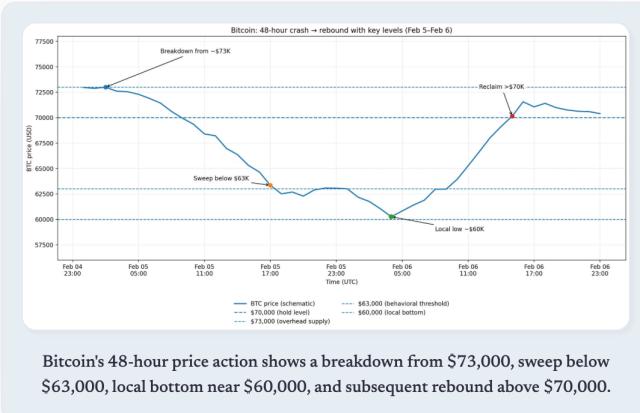
Author: Jonas Nick
Source: https://blog.blockstream.com/the-key-to-frost-what-is-distributed-key-generation/
Authors: Jonas Nick, Kiara Bickers, Tim Ruffing
The original article was published in August 2024.
For most people in the Bitcoin community, "Multisig" is a familiar concept: a multisig transaction requires permission from multiple participants to be valid. However, we need to distinguish between " n-of-n " multisig and " t-of-n " threshold signatures; the former refers to n participants, all of whom need permission; while the latter refers to t (a smaller number of participants) being sufficient to authorize the transaction. Using multisig, MuSig-DN , and MuSig2 multisig schemes, as well as threshold signature schemes like FROST (proposed by Komlo and Goldberg), can reduce transaction costs and improve the privacy of multisig wallets.
To date, FROST has only been used in experimental environments within the Bitcoin community. In this article, we will explain the reasons for this situation and how we are working to bring FROST into Bitcoin's production environment—through our recently released draft BIP for the "ChillDKG" distributed key generation protocol.
So first, what are the advantages of using the FROST threshold signature scheme?
Using MuSig2 and FROST can provide privacy and efficiency benefits.
Using schemes like MuSig2 or FROST, even if multiple participants are involved in the signing process, the result is only one signature.
This not only provides participants with privacy advantages—the final transaction looks just like a regular single-signature wallet transaction—it also streamlines transactions, reduces transaction size, and thus lowers transaction fees. All good things!
Video: Blockstream Research Director Andrew Poelstra explains the MuSig2 protocol and its benefits.
MuSig2 and FROST reduce transaction costs for Bitcoin multi-signature wallet users to the same level as regular single-signature wallets. This cost advantage is extremely important for systems with a large number of signers and frequent transactions—such as consortium sidechains like Liquid and Fedimint . Traditional multi-signature scripts leave identifiable fingerprints, allowing blockchain observers to identify multi-signature transactions; however, transactions from FROST-based wallets are indistinguishable from those from regular single-signature wallets on the blockchain. Therefore, it offers enhanced privacy compared to traditional multi-signature wallets.
While MuSig2 has been adopted in the Bitcoin industry, FROST (at least to our knowledge) has not achieved the same level of adoption. This may be surprising, given the existence of multiple FROST implementations, such as ZF FROST (from the Zcash Foundation), secp256kfun (from Lloyd Fournier), and an experimental implementation in libsecp256k1-zkp (from Jesse Posner and Blockstream Research). FROST even has an IETF (Internet Engineering Task Force) specification: RFC 9591 (although this specification is incompatible with Bitcoin due to Taproot key adjustment and x-only public key format). One plausible explanation is that FROST's key generation process is significantly more complex than MuSig2's.
Unsolved mystery: FROST has not yet entered the production environment.
FROST essentially consists of two parts: key generation and signing. While its signing process is very similar to MuSig2's, its key generation process is much more complex. FROST's key generation process can be trusted or distributed.
- In the "Trusted Key Generation" process, a "Trusted Processor" generates the key and then distributes the key fragments to the signers. This processor represents a single point of failure: if they are malicious or have been hijacked, the FROST wallet is at risk of being compromised.
- In Distributed Key Generation (DKG), although a trusted processor is no longer required, it also presents unique challenges: all participants need to engage in an interactive key generation "ritual"; only after the ritual is completed can signing begin.
Video: Andrew Poelstra discusses FROST bringing threshold signatures
Core challenge: Agreement
DKGs typically require a secure—that is, authenticated and encrypted—communication channel among participants to distribute secret value fragments to each signer; and a secure agreement mechanism. The purpose of a secure agreement mechanism is to ensure that all participants ultimately agree on the outcome of the DKG, including not only parameters (such as the generated threshold public key), but also whether errors occurred or the ritual was interrupted due to misconduct by a participant.
However, the IETF specification completely ignores the DKG, and the FROST implementations mentioned above also fail to implement secure consent mechanisms, leaving this task to the users of the codebase. But implementing consent mechanisms is not simple: countless protocols exist, each with its own preferences, ranging from simple echo broadcast shemes to complete Byzantine consensus protocols; moreover, their security and usability guarantees vary significantly (though there are also some subtle differences).
Despite the quagmire of this consent protocol, DKG’s specific preferences for the consent mechanisms it relies on are often not clearly communicated to engineers, leaving them confused.
ChillDKG: A standalone DKG designed for FROST
To overcome this obstacle, we propose "ChillDKG," a new "out-of-the-box" DKG protocol tailored for FROST usage ( draft ). We provide a detailed description in the form of a BIP draft; the BIP itself is intended to serve as a specification to guide implementers.
The key feature of ChillDKG is its independence: the establishment of secure channels and secure consent is completed within the protocol itself, hiding all the underlying complexities and presenting only a simple, mis-usable API. Therefore, ChillDKG is ready for real-world use, relying on no initiation assumptions other than that each signer is aware of the set of co-signers, identified by a single public key. ChillDKG is based on the "SimplPedPop" protocol; Blockstream Research participated in the design and formal security proofs of the latter, as detailed in the paper "Practical Schnorr Threshold Signatures Without Algebraic Group Patterns" published at CRYPTO 2023, authored by Chu, Gerhart, Ruffing (from Blockstream Research), and Schröder.
Other design goals of ChillDKG include:
- Wide applicability : ChillDKG supports a wide range of practical scenarios, from situations where signing devices are all held by a single person and interconnected, to situations where multiple holders residing in different locations each manage their own signing devices.
- Simple Backup : ChillDKG allows wallets to be recovered solely from the device seed word and public data (the same for all DKG participants) without needing to back up the secret values from other signers in a secure location. Therefore, an attacker who obtains the public backup data cannot acquire the secret signing key, and if a user loses their backup, it can be retrieved from other honest signers.
The ChillDKG BIP is currently in the draft stage, and we are seeking feedback on design choices and implementation details. While the specification is largely complete, it lacks test vectors, and we are also considering adding some additional features (such as "recognizable termination"). Once finalized, this BIP can be combined with a BIP written for FROST signing to instantiate the complete FROST protocol.
(over)