Source: Bitrace
1. Investigation background
Based on distributed consensus and economic incentives, blockchain provides new solutions for the establishment, storage, and transfer of value in an open, permissionless network space. However, with the rapid development of the encryption ecosystem in the past few years, cryptocurrency has been increasingly used in various risky activities, providing more hidden and convenient value for online gambling, online black industry, money laundering and other activities. transfer method.
At the same time, cryptocurrency is one of the important infrastructures in the encryption industry. A large number of web3 companies also use stablecoins such as USDT as the main method of fund collection and payment. However, such companies generally lack sound risk control mechanisms such as AML, KYT, and KYC, resulting in USDT that has been used for risky activities flows into business addresses without restriction, causing pollution to the address funds of the company itself and its customers.
This report aims to disclose the usage methods and scale of cryptocurrency in risky encryption activities, and to track the flow of funds related to risky activities through on-chain data, so as to shed light on the threat of risky encryption funds to web3 companies.
2. Investigation objects
The social harm caused by illegal and criminal activities on the Internet is becoming increasingly serious. This harm includes not only direct infringement on personal property and social public security, but also indirect legal risks to individuals or business entities caused by upstream and downstream industries related to illegal and criminal activities. . In recent years, all countries have stepped up their efforts to crack down on illegal and criminal activities on the Internet, and have made some progress in criminal legislation and Internet ecological research. However, cybercrime is still a problem that is difficult to completely solve, especially with the emergence of new cyberspaces such as blockchain. Traditional online gambling, online black and gray products, money laundering, etc. have all used cryptocurrency or encryption infrastructure in risky activities. This in turn creates obstacles to relevant legal identification and law enforcement supervision.
2.1 Online Gambling
Gambling refers to betting money or things of material value on an event with an uncertain outcome. The main purpose is to win more money or material value, and at the same time, participants gain spiritual pleasure through the game of money and property. Online gambling refers to gambling behavior using the Internet. There are many types of gambling. Basically, all the main gambling methods in real life can be carried out on the Internet.
In China, anyone who establishes a gambling website on a computer network for the purpose of profit, or acts as an agent for a gambling website to accept bets, falls under the category of "opening a casino" as stipulated in Article 303 of the Criminal Law. If citizens of the People's Republic of China gather to gamble or open casinos in surrounding areas outside the territory of our country, with the aim of attracting citizens of the People's Republic of China as the main source of customers, and this constitutes a crime of gambling, they may also be held criminally responsible in accordance with the provisions of the Criminal Law.
However, in other countries or regions, the legal definitions of gambling and casino openings are different:
According to the Gambling Ordinance of Hong Kong, China, except for regulated horse racing, football betting and Mark Six lottery, or other licensed gambling establishments (such as mahjong parlors), and gambling activities exempted from the law, other gambling activities are is illegal;
According to the U.S. Unlawful Internet Gambling Enforcement Act, it is illegal to conduct transactions with online gambling websites through financial institutions. However, state legislation is uneven, and there are differences in the determination of the direction of law enforcement for online gambling laws and illegal and related activities;
According to a statement from the Gambling Inspection and Coordination Bureau of Macau, China, the Macau SAR government has never issued an online gambling license. Therefore, any information and betting websites promoting online gambling activities in the name of the Macau SAR government are false and illegal. The public can conduct online gambling on such websites. Betting is not protected by the laws of the Macau SAR.
It can be seen that online gambling is not illegal in all countries or regions, and the gambling funds used by online gambling platforms that are licensed and regulated by local government departments cannot be regarded as risk funds. Therefore, Bitrace’s investigation into online gambling activities is limited to gambling platforms that operate gambling businesses without a license, gambling platform agents that accept bets from users outside the scope of operating licenses, and payment institutions that provide fund settlement services for the first two.
For traditional online gambling platforms and their agents, such institutions help gamblers settle funds by building their own centralized cryptocurrency recharge, transaction, and withdrawal systems or accessing cryptocurrency payment tools. Due to the anonymous nature of cryptocurrency, It will be difficult for government agencies to regulate or enforce such behavior. For the new hash online gambling platform, this type of platform is set up in the blockchain network. Gamblers' betting, bet settlement, fund precipitation and collection are all managed through smart contracts, with wider spread and faster development and change.
2.2 Internet black and gray products
Cyber black and gray industries refer to large-scale and chain-based industries that are formed in the process of implementing or helping to implement illegal and criminal activities through various technical means for the purpose of seeking illegitimate benefits in cyberspace. In essence, they are for the purpose of obtaining illegal benefits. Or disrupt the online ecological order. At present, cryptocurrency and some encryption industry infrastructure have been greatly integrated into the entire black and gray network ecology.
Traditional Internet black and gray products increase the deceptiveness and destructiveness of certain illegal activities by introducing cryptocurrencies into illegal activities, or using encryption tools to replace original technical means, and reduce upstream and downstream activities from being perceived or sanctioned by government departments. Opportunity. The new blockchain black and gray products directly target the encrypted assets of cryptocurrency investors or institutions, which is an illegal and criminal activity native to the encryption industry.
This report only discloses some of the typical black and gray activities that utilize cryptocurrency.
2.3 Money laundering
Money laundering is an act of legalizing illegal income. It mainly refers to using illegal income and the income generated to cover up and conceal its source and nature through various means to make it legal in form. Its actions include but are not limited to providing capital accounts, assisting in converting property forms, assisting in transferring funds or remitting them overseas. Cryptocurrencies—especially stablecoins—have been exploited by money laundering activities quite early on due to their low transfer costs, de-geographicalization, and certain anti-censorship characteristics. This has also led to cryptocurrencies being criticized. One of the main reasons.
Traditional money laundering activities often use the cryptocurrency OTC market to exchange from legal currency to cryptocurrency, or from cryptocurrency to legal currency. The money laundering scenarios are different and the forms are diverse, but no matter what, the essence of this type of behavior is In order to block law enforcement officials from investigating financial links, including accounts at traditional financial institutions or accounts at cryptographic institutions.
Different from traditional money laundering activities, the laundering target of new cryptocurrency money laundering activities is the cryptocurrency itself, and the encryption industry infrastructure including wallets, cross-chain bridges, decentralized trading platforms, etc. will be illegally used.
3. The use of cryptocurrency in online gambling activities
3.1 Forms of Cryptocurrency Utilization on Traditional Online Gambling Platforms
In recent years, it has become very common for online gambling platforms and their agents to accept cryptocurrency as chips, including:
Some online gambling platforms have independently established complete centralized management systems for cryptocurrency recharge, transactions, and withdrawals. Gamblers need to purchase cryptocurrency (mainly USDT) from a third-party platform and transfer it to the recharge address assigned by the online gambling platform to each gambler to obtain chips. After the gambler initiates a currency withdrawal application, the platform will start from the unified The hot wallet address transfers funds to the target address, and its business implementation logic is consistent with that of mainstream cryptocurrency trading platforms.
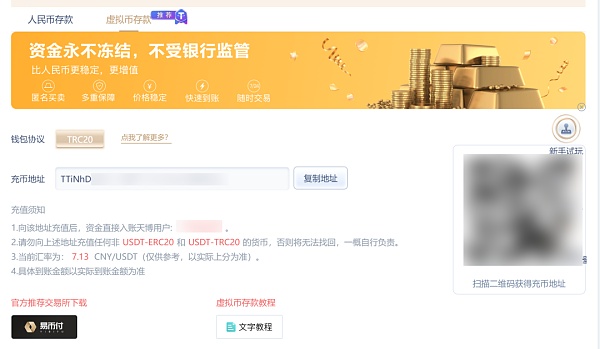
Some online gambling platforms provide gamblers with deposit and withdrawal channels by accessing encrypted payment tools. Gamblers do not recharge USDT directly to the online gambling platform, but transfer money to the payment platform account, and the withdrawal needs are also met by the latter. Fund settlements are carried out regularly between online gambling platforms and payment platforms, so their business details can be mined through fund correlation.
Take a gambling platform that uses USDT to accept bets as an example. The platform helps gamblers make USDT deposits and withdrawals by connecting to a cryptocurrency payment platform. Bitrace conducted a fund audit on one of the hot wallet addresses. Between January 27, 2022 and February 25, 2022, this address processed a total of more than 1.332 million USDT deposit and withdrawal order requests from gamblers.
In the practice of fund analysis, it is found that generally online gambling platforms with larger business scale will build their own cryptocurrency deposit and withdrawal function sections, while the majority of small and medium-sized online gambling platforms will choose to access cryptocurrency payment platforms. According to the monitoring of the DeTrust address fund risk audit platform, between September 2021 and September 2023, a total of more than 46.45 billion USDT flowed directly into traditional online gambling platforms, or encrypted payment platforms that provide deposit and withdrawal services for online gambling platforms.
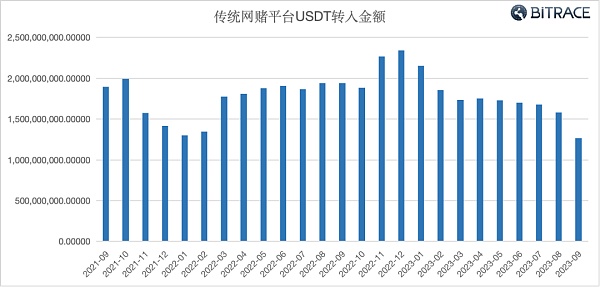
Among them, changes in the scale of online gambling funds in 2021 correspond to the development of the cryptocurrency secondary market that year. The growth in scale from November 2022 to January 2023 may be related to the large number of gambling activities during the World Cup that year.
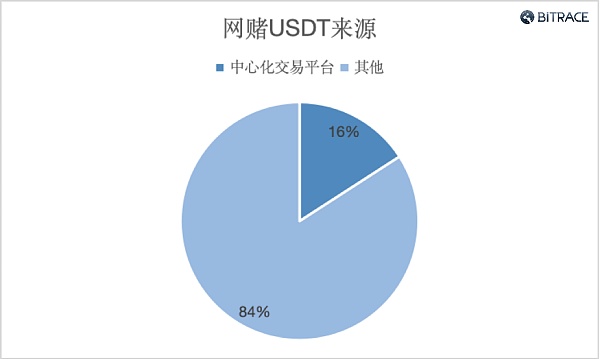
An analysis of the sources of USDT from addresses transferred to online gambling platforms shows that more than 7.43 billion USDT came directly from centralized trading platforms, accounting for 16% of the total inflow. This batch of funds is either the gamblers recharging directly from the exchange address to the online gambling platform, or the casino and its agents perform fund turnover through the trading platform. Considering that the second-level address funds of other addresses also come from the centralized trading platform, This figure is clearly an underestimate. This shows that centralized cryptocurrency trading platforms are being utilized to serve the online gambling industry.
3.2 New Hash Online Gambling Cryptocurrency Utilization Form
Each transaction on the blockchain will correspond to a unique hash value. This value is randomly generated and cannot be forged. Therefore, some online gambling platforms have developed a hash guessing game based on this. The rule is to guess the transaction hash. Whether the last digit or numbers are odd or even, large or small, determines the outcome of the guessing action and divides the bets.
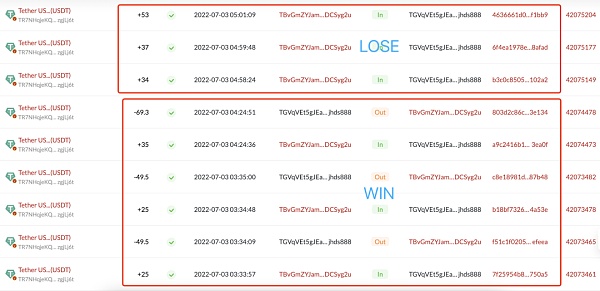
Take the typical "guess the tail number" gameplay as an example. The gambler needs to initiate a transfer to the betting address. If the hash value of the transfer ends with a specific number or letter, the gambler wins, and the platform returns the double after deducting some points. Double the chips; if the last numbers do not match, the gambler loses and the chips will not be returned.
Therefore, such online gambling addresses on the chain often manifest themselves as high-frequency, fixed-amount fund transactions with multiple addresses, resulting in a huge scale of fund interactions.
Finally, this type of hash online gambling was once very popular due to its fast pace and fair gameplay, with a large number of variant gameplays and platforms. However, because the gameplay is too transparent and the funds are easily stolen by hackers, currently this type of gameplay is Both scale and market share have been greatly reduced.
4. The use of cryptocurrency in black and gray industry activities
4.1 Utilization forms of traditional black and gray cryptocurrency
4.1.1 Investment and financial management fraud
Investment and financial management fraud is a type of online investment fraud. Scammers often claim to be "experts in the industry" through social media and other channels, and lure the victim into a false platform (usually an APP) by understanding, caring about, and soliciting the victim. Invest and defraud investment funds. In these fraudulent APPs, investors start to invest large amounts after receiving small or even large profits through investing, gambling, buying and selling goods, buying and selling securities, etc. However, at this time, basically all the funds will be lost and never returned. . When the victim discovered that the funds in the APP could not be “cash withdrawn” and the so-called “experts” could not be contacted, he suddenly realized that he had been deceived.
This type of traditional online investment fraud has also begun to use cryptocurrency or encryption tools to defraud in recent years, taking emotional fraud and black and gray USDT scoring fraud as examples.
4.1.1.1 Emotional fraud
Emotional fraud is often combined with investment fraud, but the main victim group is non-crypto users. Fraudsters create perfect online personalities and use the form of online dating to induce online dating partners to purchase USDT to participate in cryptocurrency investments, such as currency exchange arbitrage, derivatives trading, liquidity mining, etc.
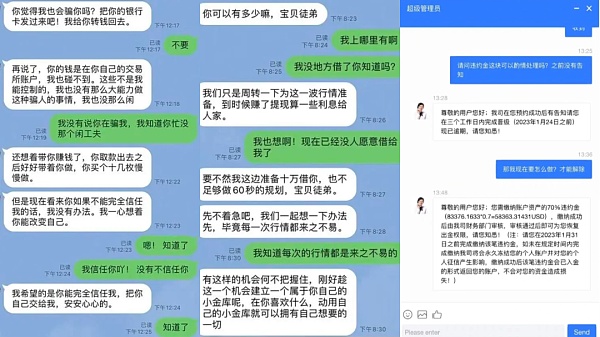
The victim's "investment" earns a large amount of money in a short period of time and is encouraged to invest more. But in fact, the victim’s USDT did not really participate in the so-called arbitrage activities. Instead, it was transferred out for cleaning after being transferred to the platform. At the same time, the victim’s withdrawal request would be rejected by the platform for various reasons, until the victim finally found out that he Being deceived.
4.1.1.2 Black and Gray USDT Score Fraud
The black and gray USDT scoring fraud is a fraudulent method disguised as money laundering scoring. The platform generally claims to be an order-taking platform for laundering USDT funds involved in the case, but in fact it is an investment scam. Once participants invest a large amount of USDT, the platform will Returns will be refused for various reasons.
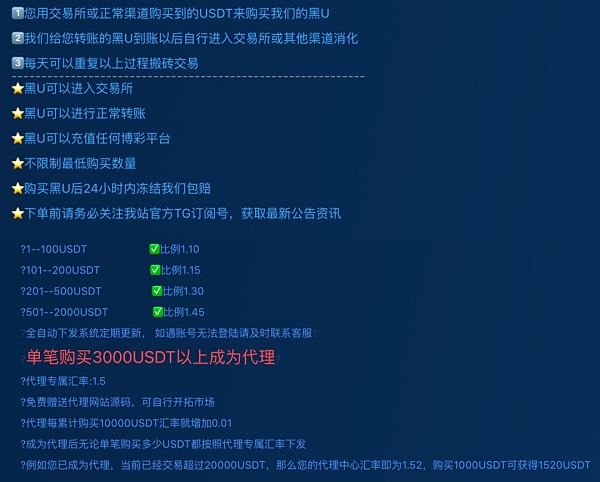
Take a "Black U Benchmark Platform" that is still in operation as an example. It allows users to use "Clean U" to exchange for "Black U" at an "exchange rate" of 1:1.1~1.45. The user collects the Black U and then transfers it to other platforms. Sell it, and the excess part is the income from the user's "running points".
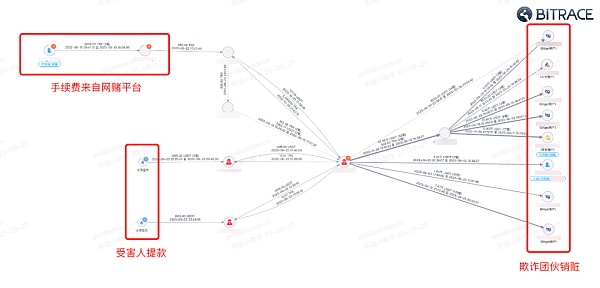
So far, the fraud gang has illegally obtained more than 870,000 USDT through the same method. 784 independent addresses transferred USDT to fraudulent addresses, but only 437 addresses received the money back. Nearly half of the participants did not succeed in "arbitrage".
4.1.2 Fake APP
Fake Apps refer to those apps that criminals use various means to repackage genuine Apps and pass them off as genuine. Fake Apps that combine cryptocurrency mainly include fake wallets and fake Telegram apps.
4.1.2.1 Fake wallet APP
Fake wallet APP currency theft is a method of stealing money by inducing others to download and install a fake wallet APP with a backdoor to steal the wallet seed phrase and then illegally transfer other people's assets. Coin thieves place fake wallet APP download links on search engines, unofficial mobile app stores, social platforms and other channels. After the victim downloads and installs the app and creates or synchronizes the wallet address, the seed phrase will be sent to the coin thief. Once the victim transfers a larger amount of crypto-assets, the stolen coins will be transferred away in batches or automatically.
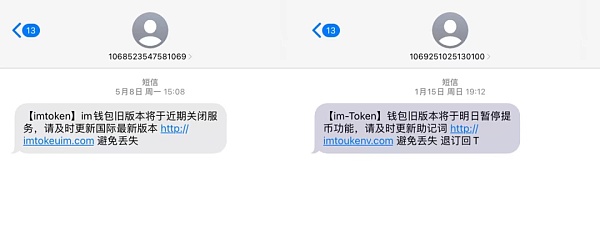
At present, this method has been highly industrialized. The business of the fake wallet development team and the operation and promotion team are completely separated. The former only participates in product development and maintenance, and sells product solutions by recruiting agents around the world; the latter only needs to promote the fake wallet APP. That’s it, you don’t even need to understand the principles of encryption.

Multi-signature theft is a variant of fake wallet theft. Multi-signature technology means that multiple users sign a digital asset at the same time. It can be simply understood that a wallet account has multiple people with signature and payment rights at the same time. If an address can only be signed and paid by one private key, the expression is 1/1, and the expression of multi-signature is m/n. That is to say, a total of n private keys can sign an account, and when m addresses When you sign, you pay for a transaction.
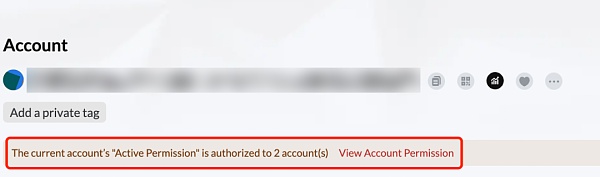
The essence of traditional fake wallet theft is to share wallet control rights with the victim. The coin thief cannot prevent the victim from transferring assets. However, based on the principle of multi-signature technology, the coin thief will immediately transfer the victim to the victim after installing the fake wallet APP. When the personal address is added to the multi-signature, the wallet owner himself will not be able to transfer the assets in the wallet, and can only transfer them in but not out, and the currency thief will be able to transfer the assets at any time, which often depends on the victim. time to transfer large amounts of funds.
4.1.2.2 Fake Telegram APP
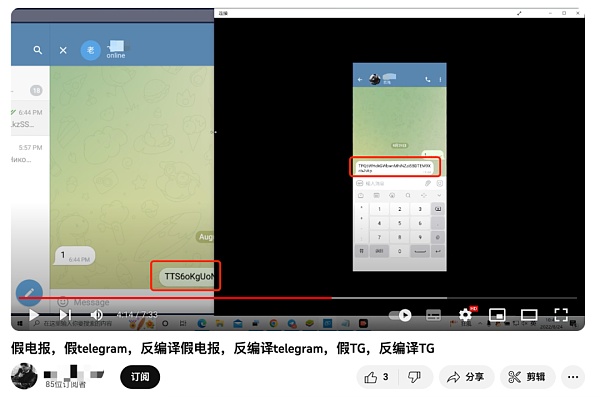
The classic application of fake APPs in cryptocurrency-related black and gray products is the malicious backdoor implantation into the Telegram APP. The latter is a social software commonly used by cryptocurrency investors, and many over-the-counter trading activities rely on this software. Fraudsters will use social engineering attack methods to induce the target to "download" or "update" the fake Telegram APP. Once the target user pastes the blockchain address through the chat box, the malware will identify the replacement and send the malicious address, causing the counterparty to Send funds to a malicious address without the attacker knowing it.
4.1.3 Third-party payment guarantee for black and gray products
Third-party payment guarantee means that after the buyer and seller reach a commodity transaction intention or agreement online, the buyer pays the payment to a third party first, and the third party temporarily keeps it. After the buyer receives the goods and inspects them correctly, he notifies the third-party intermediary, and the third-party Pay the payment to the seller to complete the entire transaction. It is actually an online payment service method that uses a third party as a credit intermediary to temporarily supervise the payment of goods for both buyers and sellers before the buyer confirms receipt of the goods. During this transaction, the third-party intermediary will charge a certain percentage of service fees.
Currently, some black and gray third-party payment guarantee platforms, in addition to traditional legal currency channels, have also begun to widely use Tether (mainly trc20-USDT) as guaranteed funds to provide services including illegal currency exchange, illegal commodity transactions, and illegal collection. Payment guarantee services are provided for transactions including agency payments and cryptocurrency transactions involved in the case. Although the transaction types are different, the transaction process is consistent.
Usually one of the buyer and seller will pay the payment guarantee platform to place an advertisement in the advertising area, either in a specific area of the website or in the official Telegram group. The advertisement will indicate the transaction type, transaction requirements, payment method, etc. detail.
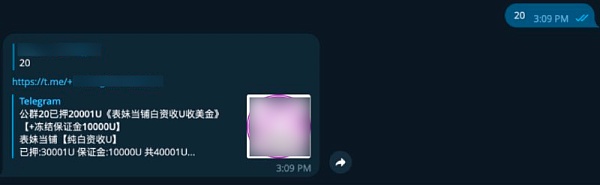
After the buyer and seller complete the negotiation, they need to contact the customer service of the payment guarantee platform to establish a "special group". The special group is a non-public telegram group used only for transaction communication. Its members include buyers, sellers and special group robots. In principle, one-to-many transactions are not allowed. , and no irrelevant personnel are allowed to be brought in.
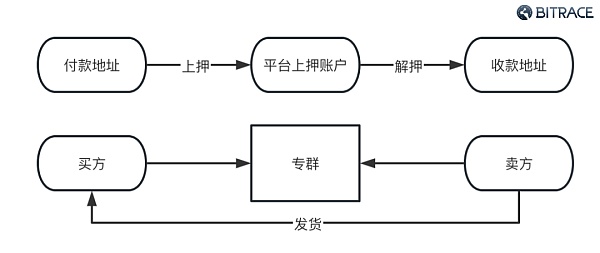
The buyer needs the buyer to transfer the payment to the official account of the guarantee platform and provide the certificate. This process is called "pledge". The trader will notify the seller to deliver the goods after confirming the payment; then the seller will start to send the goods after receiving the trader's delivery notice. The buyer then confirms receipt of the goods and notifies the trader to release the loan. After receiving the buyer's receipt confirmation or loan notice, the trader deducts the commission and releases the loan to the seller and provides the loan voucher; finally, the seller confirms receipt payment, the transaction is completed.
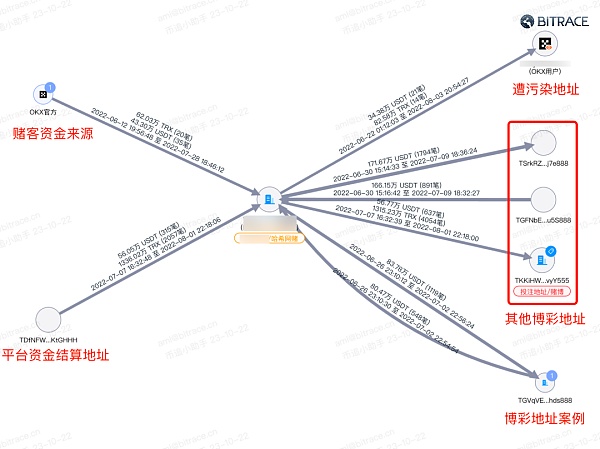
The platform does not allocate independent addresses to users for fund isolation in each transaction. Instead, all deposits are sent to the same deposit address within a period of time, causing this address to directly receive a large amount of funds related to online gambling and black and gray industries. , money laundering and other risk funds. At the same time, because of its huge scale of funds, it also confuses the direction of funds to a certain extent and creates obstacles for investigators’ tracking activities.
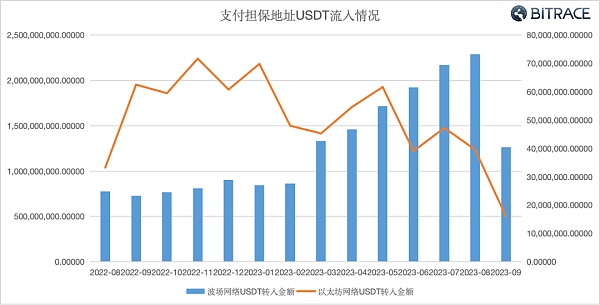
A fund audit of platform addresses known to guarantee illegal trading activities found that the size of their guaranteed funds has been in a growing trend in the past 12 months, including more than 17.07 billion USDT on the TRON network and more than 670 million on the Ethereum network. USDT, indicating that most of the illegal transactions secured by such platforms occur on the TRON network.
4.2 New forms of use of black and gray cryptocurrency
4.2.1 Authorization to steal coins
Authorized currency theft is a currency theft technique that illegally transfers other people's assets by stealing the USDT management rights of other people's addresses. Public chains such as Tron and Ethereum allow users to transfer the operation rights of a certain asset in the wallet to other addresses. The latter will thus obtain the management rights of part or all of the assets of the address, and can call the contract at any time to authorize the address in the address. Asset transfer.
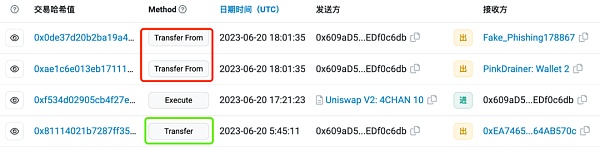
This kind of malicious stolen currency authorization request is usually disguised as a payment link, airdrop claim entrance, interactive contract and other honeypots. Once the victim is induced to interact, an asset in the address - usually USDT - will be authorized to the recipient without restrictions. The stolen currency address was transferred away by calling the "TransferFrom" method at a later time.
Coin thieves often deceive the target victim into clicking on the phishing link and running the fraudulent smart contract. At this time, the victim's wallet seed phrase is not leaked, so by canceling the authorization in time, certain losses can still be recovered.
4.2.2 Zero transfer phishing
Zero-transfer phishing is a scam that targets cryptocurrency investors who don’t use wallet apps properly. By sending a large number of USDT transactions with an amount of 0 to an unspecified blockchain address, the interaction record of the target address can be increased without permission. If an unspecified person attempts to copy the address from the existing transfer record on the smart device when initiating a transfer to an address, it is possible to send funds to the wrong address, causing losses.
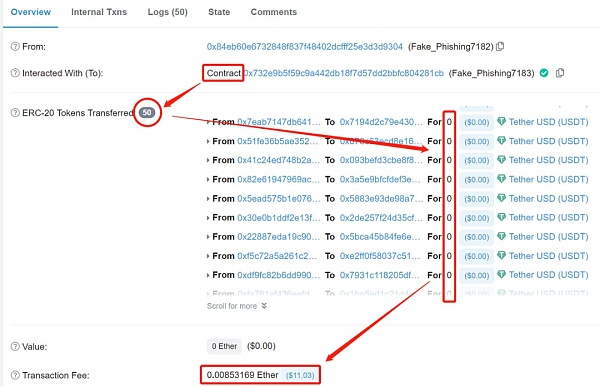
Bitrace conducted a fund analysis on a large number of fraudulent addresses that have been marked as phishing addresses in the Tron network, and defined transactions with transfer amounts of less than 1 USDT from these addresses as a phishing activity, and transactions with more than 10 USDT as fraudulent proceeds.
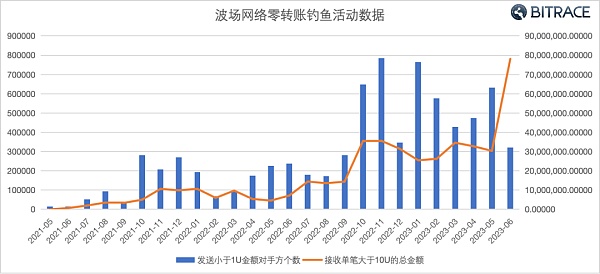
Our research shows that the activity and damage scale of zero-transfer phishing activities have been expanding. As of now, more than 451 million USDT funds in the TRON network have been lost due to phishing attacks.
4.2.3 Fake platform currency arbitrage fraud
A common method of arbitrage fraud involving fake platform coins is that the fraudster falsely claims to have developed a certain "smart arbitrage contract". Participants only need to invest a certain amount of cryptocurrency into the contract to obtain an excess amount of another well-known cryptocurrency. Currencies (such as Binance Coin, Huobi Points, OK Coin, etc.), after obtaining "arbitrage gains", participants can earn profits by liquidating them in the third-party trading market.
Early tests with small amounts will indeed return real excess cryptocurrency, but once the victim invests a large amount, fake tokens will be returned, and the latter does not have any market value. This fraud technique is old but effective, and there are still a large number of variants active in the cryptocurrency investor community. It not only causes financial losses to ordinary investors, but also causes negative damage to the brand equity of the impostor.
4.2.4 Tron’s beautiful account address trading
Like traditional black and gray property activities, criminals in encrypted black and gray property also need to create or purchase virtual identities before carrying out illegal and criminal activities. In traditional black and gray property activities, it is bank accounts and identity information. In encrypted black and gray property activities, is the blockchain address. Usually, such addresses are customized and obtained from professional good-number address service providers.
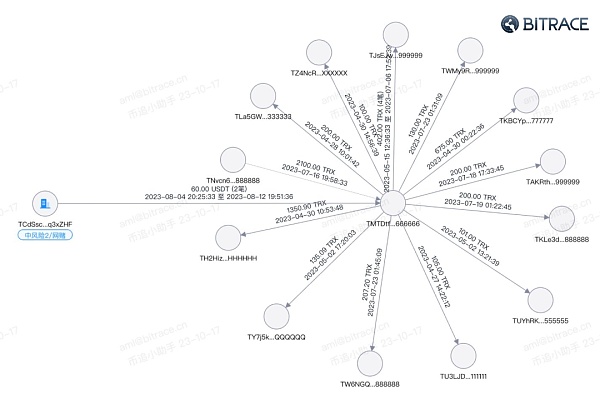
In online gambling activities, Hash online gambling platform operators are often users of Tron’s beautiful account addresses. They will purchase beautiful accounts in bulk from professional beautiful account service providers and use these beautiful accounts as business addresses. Realize functions including fund receipt and payment, storage, transfer or acceptance of bets, fund settlement, etc.
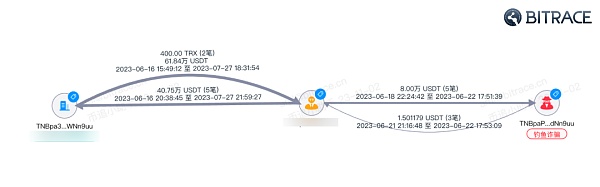
In the black and gray product activities, the customization of beautiful accounts directly gave birth to a more refined variant of zero-transfer fishing - fishing with the same tail number. Compared with ordinary widespread zero USDT transfers targeting unspecific blockchain objects, same-number phishing is often customized. Fraudsters will copy the first and last numbers of the target's commonly used counterparty addresses and transfer more money. amount.
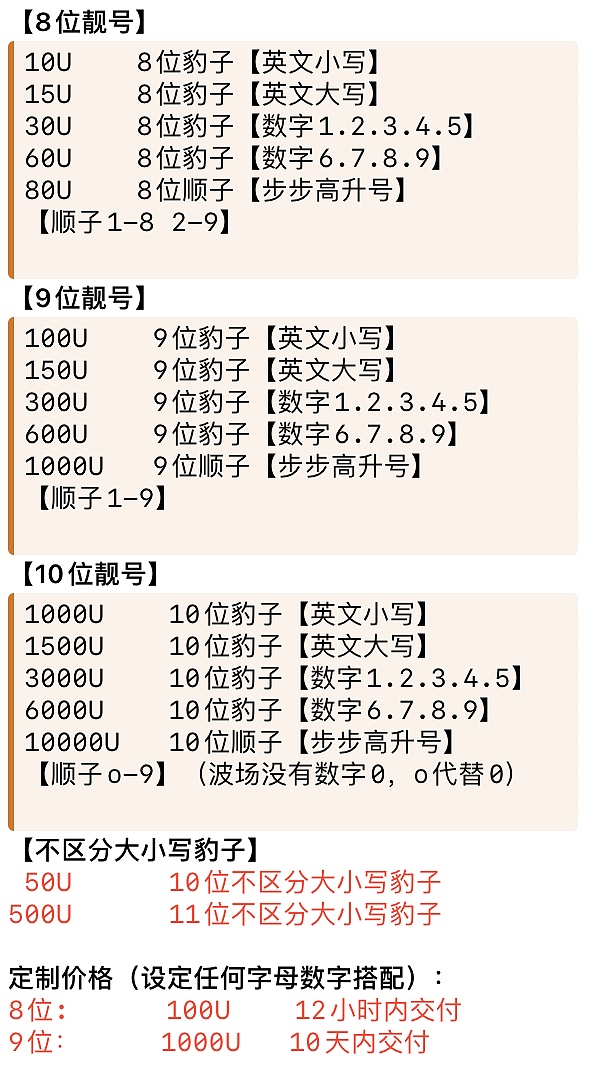
The cost of this kind of fishing activity is not cheap. According to the quotation of a certain TRON account service provider, it can be seen that an eight-digit customized address takes 12 hours to be delivered and sells for 100 USDT. The same eight-digit account only costs 100 USDT. 10USDT is required.
In addition to the TRON account service providers, some Telegram APP group chat robot service providers, website source code service providers, batch transfer tool service providers, SEO quick queuing service providers and other groups also provide similar assistance to participants in illegal activities. This article will not disclose too much about the circumstances of profiting from it.
5. Use of Cryptocurrency in Money Laundering Activities
5.1 Traditional money laundering cryptocurrency utilization forms
The use of cryptocurrencies in traditional money laundering activities aims to transfer payments from high-risk users to the accounts of low-risk users, thereby circumventing the risk control measures of payment institutions. This usually takes the form of exchanging the legal currency involved in the case into crypto funds in the cryptocurrency over-the-counter market, or exchanging the crypto funds involved in the case into legal currency, in order to block the capital link and avoid tracking and crackdowns.
A typical scenario of laundering stolen money is that after fraudsters defraud the victim of cash, they quickly split the funds into small amounts and transfer them to multiple bank cards in succession, and then organize "Kanan" to withdraw the cash, and then transfer the cash to individuals such as cars or airplanes. or public transportation to the location of the money laundering gang. In the past, this cash was often used to purchase commodities, or converted into foreign exchange and flowed out of the country, but now it is more often used to purchase USDT offline. This batch of USDT will then either be converted into cash in the cryptocurrency OTC market, or It will be directly flown out of the country or other money laundering groups for further processing. In this process, the over-the-counter trading market of the U platform, payment guarantee platform, and centralized trading platform all played an important role.
5.1.1 Run U platform
The PaU platform is a new method of money laundering. Its basic model is to combine digital currency transactions with traditional "running score" platforms. First, the platform organizers recruited USDT traders by purchasing large amounts of USDT and transferring them to overseas exchanges to sell them to earn the price difference. They then required the traders to register digital currency exchange accounts with their real names and bind bank cards under their personal names. Block movers need to purchase a certain amount of USDT as a trading deposit and pledge it to the "Benchmark" platform. The platform organizer will open an account for the block mover on the platform to mark the amount and unit price of USDT available for sale based on the amount of USDT deposit paid by the block mover. , and also note the recipient’s bank account and other information. When overseas telecom fraud and other criminal gangs need to receive stolen money, they will first place an order with the perpetrator to purchase USDT through the "Banfen" platform, and then instruct the victim to transfer money to the bank account reserved by the perpetrator on the platform. When the victim will be After the fraudulent money is transferred to the fraudster's account, the fraudster confirms the transaction on the platform, thus completing the first transfer of the stolen money. After that, the perpetrators used the stolen money to continue to purchase USDT from the exchange and withdraw the coins to the benchmarking platform in a repetitive cycle, earning the USDT price difference and platform commission in the process.
This kind of activity is called "Card back U" by money laundering gangs, which can help upstream criminals and money laundering gangs completely avoid the risks of stolen money and real-name authentication on the trading platform.
5.1.2 Score Racing Team
In addition to recruiting score-scoring personnel to launder stolen money, money launderers also often use the more direct "score-scoring fleet" model to launder money. The form is basically the same as that of PaoU, but the difference is that its cryptocurrency OTC transactions occur offline and are delivered in cash. First, the fleet leader will recruit a large number of real people to register for real-name bank card accounts. When upstream criminals (so-called "material owners") illegally obtain stolen money (so-called "material"), they will contact the fleet leader through an illegal third-party payment guarantee platform to take orders; Then a large amount of funds will be split and transferred to multiple bank cards under the control of the team. If the money is first-hand black money, it is called "first-hand material". If it is second-hand or third-hand black money, it is called "second-hand material". "Materials" and "Three Materials", the latter has lower financial risks and lower commissions; then the fleet leader will drive with the driver to pick up the corresponding card owner to withdraw cash from a local ATM. After multiple cash withdrawals, the fleet leader will continue to use his personal Or use public transportation to transport the cash to a designated location for offline transactions; finally, with the intervention of a third-party payment guarantee platform, the fleet leader transfers the cash to the target to earn commission, and the other party transfers USDT to the guarantee address to complete the money laundering process.
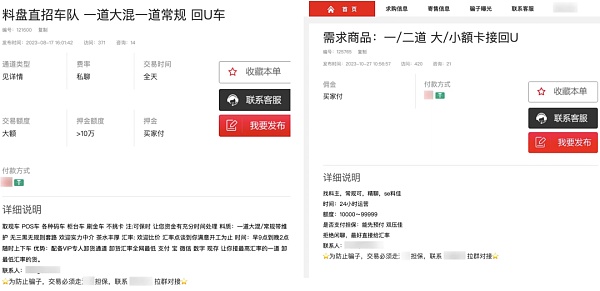
This type of money laundering activity takes the form of multi-layer bank account transfers, ATM cash withdrawals, and offline cryptocurrency transactions. It not only interrupts the fund tracking link many times, but also circumvents bank fund supervision.
Bitrace conducted a fund audit on some addresses in the Tron network that were marked as having money laundering risks and with a fund size exceeding 1 million USDT. The audit period was from September 2021 to March 2023, and the audit content was USDT transfer.

Data shows that from September 2021 to March 2023, addresses with money laundering risks in the TRON network have inflowed a total of more than 64.25 billion USDT, and the scale of funds has not been affected by the bear market in the cryptocurrency secondary market. It is not difficult to see the success of its business. Participants are not investors in the true sense.
5.2 New forms of money laundering cryptocurrency utilization
For cybercriminals native to the crypto industry, anonymous exchanges based on cryptographic infrastructure and on-chain obfuscation are the most commonly used methods for laundering funds.
5.2.1 Confusion of funds on the chain
On-chain fund splitting and currency mixing platforms are the most common channels for fund confusion.
Fund splitting means that criminals use complex and multi-layered transactions to transfer virtual currencies step by step through different wallet addresses and accounts, and finally transfer them to the wallet addresses of overseas associates, thereby severing the connection between capital input and output and blurring the virtual currency. The purpose of the transaction link. This method is equally effective in cryptocurrency money laundering activities and is a common method used by black and gray industry practitioners to handle funds.
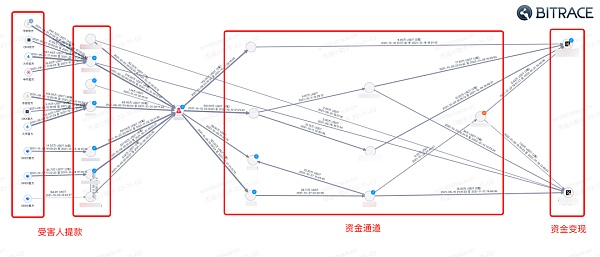
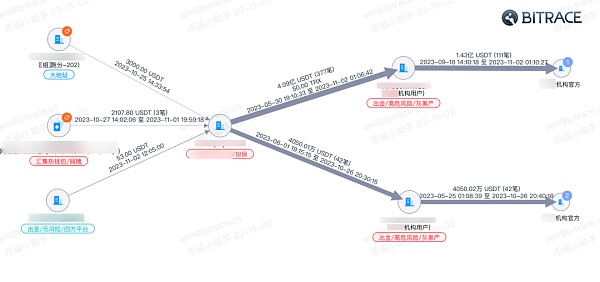
Take the address canvas of an investment and financing fraud case as an example. After collecting the victim’s encrypted funds, the illegal gains were split through several fund channels, and finally collected into a few exchange account addresses to complete the funds. Realize.
Coin mixing is to mix the user's cryptocurrency with other users' currencies, and then transfer the mixed currency to the target address to cover up the original currency flow path, making it difficult to track the source and destination of the cryptocurrency. Therefore, many cryptocurrency mixing platforms have been sanctioned by governments of various countries, including the most well-known Tornado.cash, which was sanctioned by the Office of Foreign Assets Control (OFAC) of the U.S. Department of the Treasury on August 8, 2022. Some of the Ethereum addresses related to them are included in the list of specially formulated nationals in the United States. Once added to this list, the property and property rights of individuals or related entities will face the risk of being frozen.
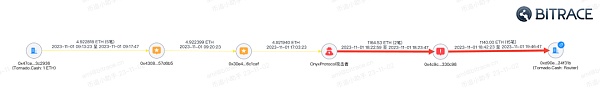
But despite this, since the currency mixing contract of Tornado.Cash is public and unlicensed, other users can still perform currency mixing activities by directly calling the contract. Take the OnyxProtocol attack that occurred on November 1, 2023 as an example. The attacker obtained the address handling fee through the currency mixing platform and further laundered funds.
5.2.2 Anonymous exchange on the chain
KYC-free trading platforms and cross-chain bridges are the two most important on-chain anonymous exchange channels.
So far, except for a few physical addresses that have been sanctioned, this type of encryption infrastructure has not implemented more risk controls on risky encryption funds or high-risk encryption addresses. As a result, illegal funds are often able to pass through these addresses immediately after an attack. Channel for exchange.
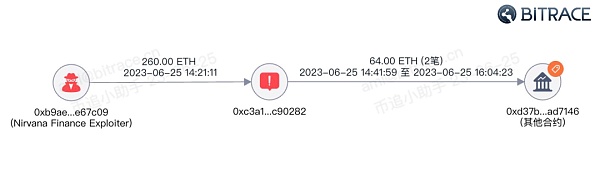
Take the Nirvana Finance attack that occurred on June 25, 2023 as an example. After the attacker illegally obtained the victim institution’s encrypted funds, he immediately transferred part of the funds to THORWallet DEX, which is a permissionless and highly capable A private decentralized trading platform that allows users to directly conduct cross-chain exchanges between blockchains without disclosing transaction information. Therefore, THORWallet can be seen in many encryption security incidents that have occurred in the past. DEX appears in the fund cleaning process.
6. Risky encryption funds contaminate web3 corporate addresses
6.1 Address pollution on centralized trading platforms
Centralized trading platforms are one of the most important places for laundering risky USDT funds. In this report, Bitrace audited 126 hot wallet addresses of common centralized trading platforms, and conducted an audit of crypto funds related to online gambling, black and gray industries, and money laundering activities. The inflow situation from January 2021 to the present has been fully investigated.
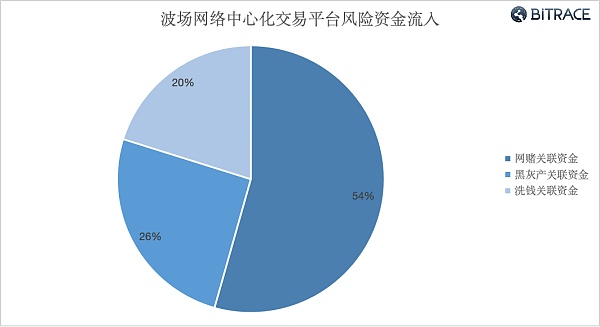
From January 2021 to September 2023, a total of more than 41.52 billion USDT at risk flowed into some centralized trading platforms in the Tron network, including 22.579 billion USDT related to online gambling, 10.570 billion USDT related to black and gray assets, and 8.373 billion money laundering Linked to USDT.
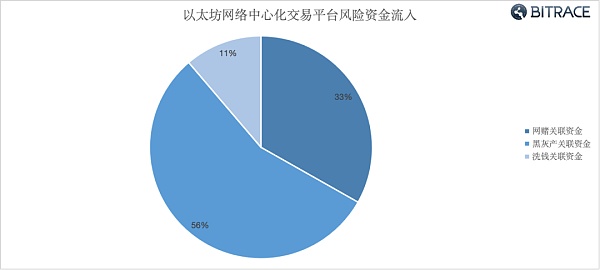
From January 2021 to September 2023, a total of more than 3.315 billion risky USDT flowed into some centralized trading platforms in the Ethereum network, including 1.1 billion online gambling-related USDT, 1.842 billion black and gray industry-related USDT, and 372 million money laundering Linked to USDT.
It is not difficult to see from the total amount of risk funds and the proportion of risk funds that the scale of illegal utilization of USDT in the Tron network is larger than that of the Ethereum network, and the proportion of risk funds in the online gambling category is higher. This is consistent with what has been observed in practice. The situation is consistent - casino agents and ordinary gamblers prefer to use Tron USDT to save handling fees.
6.2 OTC market address pollution
In addition to the OTC sector of centralized trading platforms, certain payment platforms, cryptocurrency investor groups, and acceptor communities will establish OTC markets of a certain scale. Such venues lack complete KYC and KYT mechanisms and cannot handle transactions. It is difficult to judge the counterparty's capital risk, and it is difficult to limit risk funds afterwards, and a higher proportion of risky USDT will often flow into it.
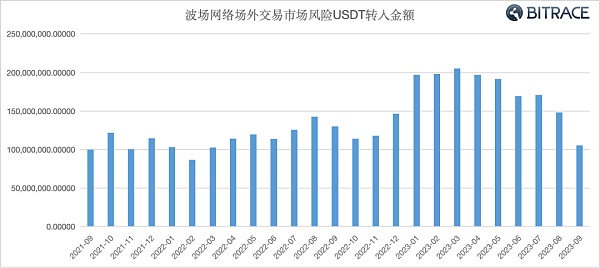
Bitrace conducted a fund audit on addresses with typical OTC market characteristics and a fund size of more than 1 million USDT. The data shows that in the past two years, these addresses have flowed into at least 3.439 billion USDT associated with risk activities, and the inflow volume has increased over time. Increasing and basically not affected by the winter in the secondary market.
6.3 Encrypted payment platform address pollution
As one of the infrastructures in the field of decentralized finance, cryptocurrency payment tools provide fund settlement services for blockchain institutions on the one hand, and certain cryptocurrency acceptance services for ordinary users on the other. Therefore, they face the same risks as encryption. Capital pollution.
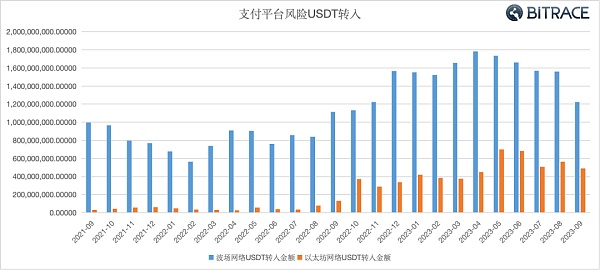
Bitrace conducted a fund audit on major crypto payment platform addresses that mainly serve customers in Southeast Asia and East Asia. The data shows that between January 2021 and September 2023, a total of more than 40.51 billion USDT at risk flowed into these addresses, of which 334.6 billion were in the Tron network. 100 million USDT, and the Ethereum network is 7.04 billion USDT. At almost all times, the risk of USDT in the TRON network pollutes the cryptographic payment platform more seriously than the Ethereum network.
7. Conclusions and suggestions
Participants in online gambling, black industry, money laundering and other activities are making extensive use of cryptocurrencies, including USDT, to enhance the anonymity of funds and avoid tracking by regulatory and law enforcement agencies. The direct result is that Web3 companies that operate compliant encryption businesses and ordinary cryptocurrency investors lack the ability to identify financial risks and passively collect such crypto funds related to risky activities, which in turn causes the fund addresses to be contaminated and even involved. case.
Industry organizations should strengthen their awareness of capital risk control, actively establish cooperation with local law enforcement agencies, and access threat intelligence services provided by security vendors to perceive, identify, prevent, and block risky encrypted funds to protect their business addresses and user addresses from pollute.
7.1 Strengthen awareness of capital risk control
In addition to basic know-your-user (KYC) activities - verifying customers' true identity, transaction execution, source of funds, etc. in accordance with the law, industry institutions must also perform customer abnormal transaction monitoring and management responsibilities (KYT) and report violations in a timely manner Trading and risk profile. Conduct hierarchical management of users with suspicious risky financial activities, and adopt management measures to restrict some or all platform functions.
7.2 Actively understand local laws and regulations and cooperate with law enforcement agencies
Platforms need to establish or entrust a professional team to conduct compliance docking and review of law enforcement requests from around the world, assist in identifying, combating, and preventing currency-related criminal activities, reduce the economic losses caused, and avoid fund contamination of platform business addresses and user accounts.
7.3 Establish a threat intelligence network and information sharing mechanism
Industry organizations need to pay attention to open source network intelligence and keep an eye on attack addresses and funds related to current encryption security incidents to ensure that they can counter the funds involved in the flow into the platform as soon as possible; they also need to access external threat intelligence sources to communicate with Encrypt data and cooperate with security companies to establish DID portraits for users, and adopt appropriate risk control restrictions for addresses that are associated with risky addresses and lack good interaction history. And on this basis, establish and maintain an open threat intelligence database shared by the entire industry to ensure the security and trust of the entire industry.





