On January 3, 2024 , according to monitoring by Beosin's EagleEye security risk monitoring, early warning and blocking platform, the Radiant Capital project suffered a flash loan attack from an attacker.
The attacker stole more than 1,900 ETH, worth more than 4.5 million US dollars, through 3 transactions. The stolen funds are currently still stored at the attacker's address. The Beosin security team analyzed this incident immediately.

Vulnerability analysis
The root cause of this incident is that the Radiant Capital project used precision expansion and rounding in the process of calculating the number of tokens. This allowed the attacker to control the precision and combine it with rounding to expand the profit point. attack.
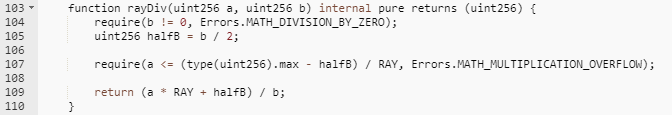
Observing the above code, the rayDiv function passes in two uint256 data a and b. The whole process can be abbreviated as (a*RAY+b/2)/b, where RAY is the precision extended data, which is 10^27, then the result It is equivalent to a*RAY/b+0.5, which implements the rounding function. The error of this calculation method mainly comes from b. If b is extremely small compared to a, then the error will be negligible, but if b has the same order of magnitude as a , then the error may reach a itself.
For example: if a*RAY=10000, b=3, then the calculated result is 3333, which is 1/10000 smaller than the actual value; and if a*RAY=10000, b=3000, the calculated result is 3, 1/10 smaller than the actual value.
In this incident, the attacker manipulated the value of b so that the value of b and the value of a have the same order of magnitude, making the calculation equivalent to 3/2.0001=1, and the calculated value is 1/3 smaller than the actual value.
Attack process
Let’s take a look at the hacker’s attack process:
1. The attacker first borrowed 3 million USDC through AAVE flash loan to use as start-up funds for the attack.
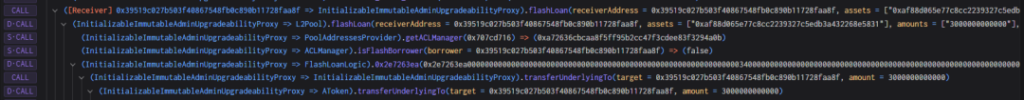
2. The attacker pledged 2 million USDC to the Radiant contract and obtained 2 million rUSDCn certificate tokens. 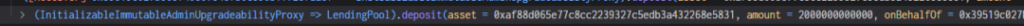
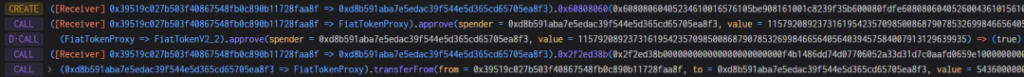
3. The attacker performs a flash loan through the Radiant contract, borrows 2 million USDC, returns the 2 million USDC in the callback function, and withdraws the USDC pledged in the second step. Finally, the flash loan function calls the transferfrom function. Transfer the attacker's USDC to the contract with interest. At this time, a handling fee of 9/10000 will be charged, and the handling fee collected becomes the liquidity of the pool.
4. By repeating step 3 many times, the attacker controls the liquidityIndex to be very large, liquidityIndex=271800000000999999999999998631966035920.
5. Next, the attacker creates a new contract and puts 543,600 USDC into it, because 5436 (USDC value) is exactly twice the 2718 (liquidityIndex value) in step 4, which can facilitate rounding control.
6. The attacker mortgaged all 543,600 USDC into the Radiant contract and obtained the same amount of rUSDCn. 
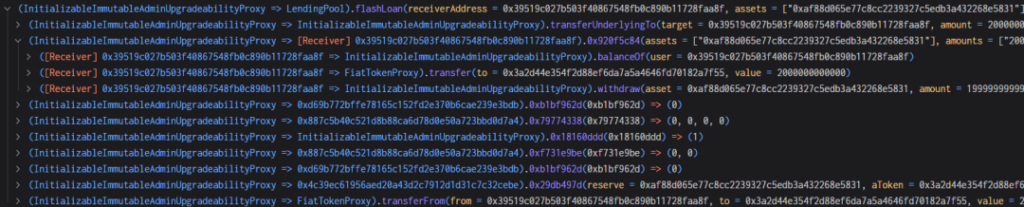
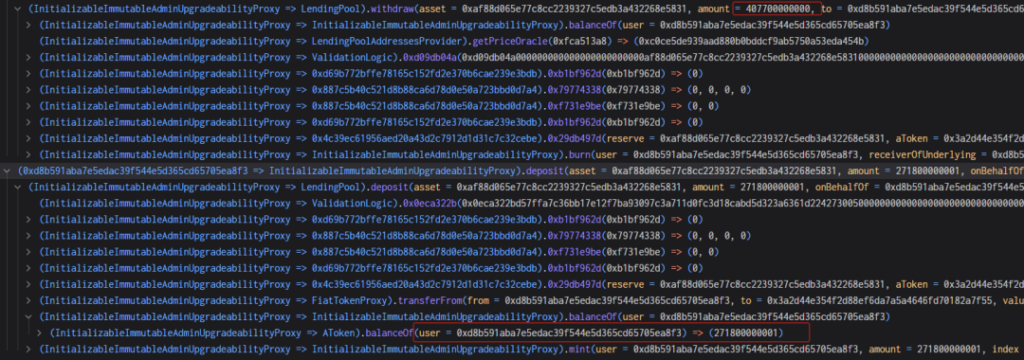
7. The attacker withdraws 407,700 USDC and should have destroyed 407,700 rUSDCn. However, as mentioned above, the burn function performs precision expansion and rounding calculations.
40770000000000000000000000000000000000/271800000000999999999999998631966035920=1.49999999, and the rounding result is 1, causing the result to be 1/3 smaller.
As shown in the picture below, 407,700 USDC should have been destroyed, but 271,800 were left, indicating that only 271,800 were destroyed, and the attacker withdrew 407,700 USDC.
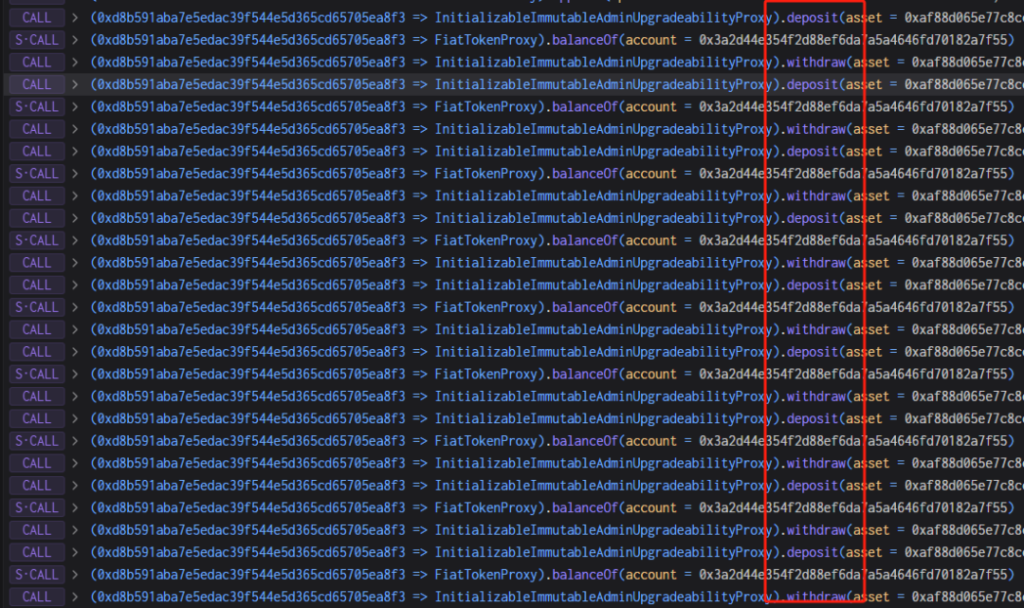
8. The attacker exploits the vulnerability in step 7 to repeat the pledge withdrawal operation, and the withdrawal is always 1/3 more than the pledge amount, and finally exchanges all the USDC in the pool.
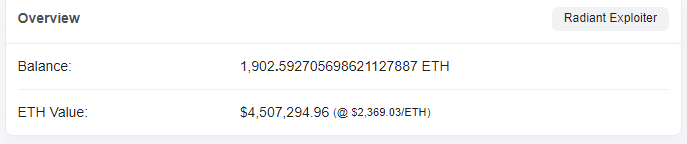
Money tracking
As of press time, the 1,902 ETH stolen have been stored in the hacker's address and have not been moved. Beosin Trace will continue to monitor the funds.
As 2024 begins, we have already witnessed two cases of large-scale thefts. (Review of yesterday’s security incidents: What happened to the first case of the year, the $80 million stolen Orbit Chain incident? ) This series of events once again reminds us that in the Web3 ecosystem, security prevention is still crucial. important!
Extended reading: The Orbit Bridge cross-chain bridge was hacked for US$81.5 million, and the Orbit Chain ecosystem plummeted overall
As a leading blockchain security company in the world, Beosin has established branches in more than 10 countries and regions around the world. Its business covers program code security audit before the project is launched, security risk monitoring, early warning and blocking, virtualization during project execution, etc. "One-stop" blockchain security products + services such as currency stolen asset recovery, security compliance KYT/AML, etc. The company is committed to the secure development of the Web3 ecosystem and has provided blockchain security technology services to more than 3,000 companies around the world. , including HashKey Group, Amber Group, BNB Chain, etc., has audited more than 3,000 smart contracts and public chain mainnet, including PancakeSwap, Ronin Network, OKCSwap, etc.








