By integrating machine learning, knowledge graphs, and automated decision-making technologies, "Wuxiang" can independently complete the entire closed-loop process from threat detection to impact assessment and response, achieving truly autonomous decision-making and goal-driven operations. Its "Agentic AI Architecture" is designed to simulate the collaborative logic of a human security team: using the "brain" to integrate network security knowledge bases to support planning capabilities, the "eyes" to perceive network environment dynamics in fine-grained detail, and the "hands and feet" to flexibly invoke diverse security tool chains, forming an efficient information-sharing research network through multi-agent collaboration, with division of labor and information sharing.
In technical implementation, "Wuxiang" adopts the "ReAct Mode" (Act-Observe-Think-Act cycle) and the "Plan AI + Action AI dual-engine architecture" to ensure dynamic error correction in complex tasks. When tool invocation is abnormal, the system can autonomously switch to backup plans without interrupting the process. For example, in APT attack analysis, Plan AI acts as an "organizer" to break down task objectives, while Action AI serves as an "investigation expert" to execute log parsing and threat modeling, with both advancing in parallel based on real-time shared knowledge graphs.
At the functional module level, "Wuxiang" has built a complete autonomous decision-making ecosystem: agent personas simulate security analysts' reflective and iterative thinking to dynamically optimize decision paths; tool invocation integrates host security log queries, network threat intelligence retrieval, and LLM-driven malicious code analysis; environment perception captures host assets and network information in real-time; knowledge graphs dynamically store entity associations to assist decision-making; multi-agent collaboration enables parallel task execution through task decomposition and information sharing.
Currently, "Wuxiang" performs most exceptionally in three core application scenarios: alert investigation, traceability analysis, and security report generation.
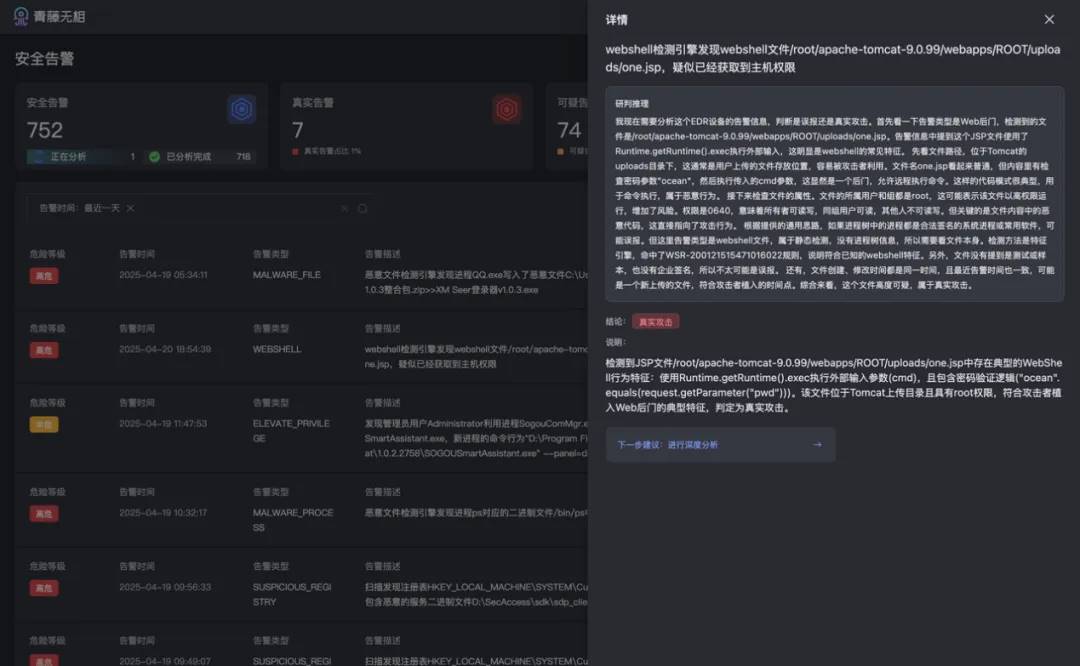
In traditional security operations, identifying the authenticity of massive alerts is time-consuming and labor-intensive. Taking a local privilege escalation alert as an example: Wuxiang's alert investigation agent automatically analyzes threat characteristics, invoking tool chains such as process permission analysis, parent process tracing, and program signature verification, ultimately determining it as a false positive—without any human intervention. In Qingteng's existing alert testing, the system has achieved 100% alert coverage and 99.99% investigation accuracy, reducing manual workload by over 95%.
Facing real threats like Webshell attacks, the agent performs cross-dimensional correlation through code feature extraction and file permission analysis to confirm attack validity within seconds. Traditional in-depth traceability, which previously required multi-department collaboration and took days (such as upload path restoration and lateral impact assessment), is now automatically linked by the system through host logs, network traffic, behavior baselines, and other data streams, generating a complete attack chain report and compressing the response cycle from "days" to "minutes".
"Our core is to reverse the collaborative relationship between AI and humans, treating AI as a partner and achieving a leap from L2 to L4, from assisted driving to advanced autonomous driving," shared Hu Jun, co-founder and VP of Product at Qingteng. "As AI adapts to more scenarios with higher decision success rates, it will gradually take on more responsibilities, thus changing the division of responsibilities between humans and AI."
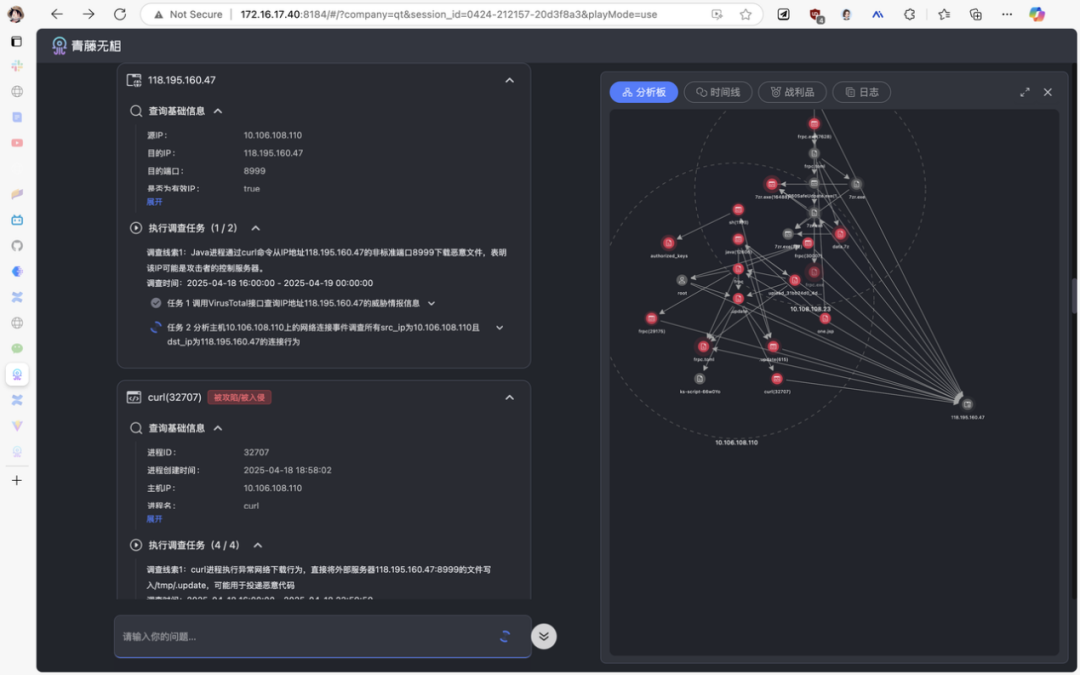
In the traceability analysis scenario, a Webshell alert first triggers the "Wuxiang AI" multi-agent security team collaboration: the "investigation expert" locates the one.jsp file based on the alert, generating parallel tasks such as file content analysis, author tracing, same-directory investigation, and process tracking, with the "security investigator" agent invoking file log tools to quickly lock down the java (12606) process as the write source, with this process and associated host 10.108.108.23 (discovered through access logs with high-frequency interactions) subsequently included in the investigation.
The agent dynamically expands clues through the threat graph, progressively delving from a single file to processes and hosts, with the investigation expert synthesizing task results to comprehensively assess risks. This process compresses what would take humans hours to days into mere tens of minutes, restoring the attack chain with precision surpassing high-level human security experts, tracking lateral movement paths without blind spots—red team assessments also show it is difficult to evade its comprehensive investigation.
"Large models are better than humans because they can thoroughly investigate every nook and cranny, rather than excluding low-probability scenarios based on experience," Hu Jun explained. "This means both breadth and depth are improved."
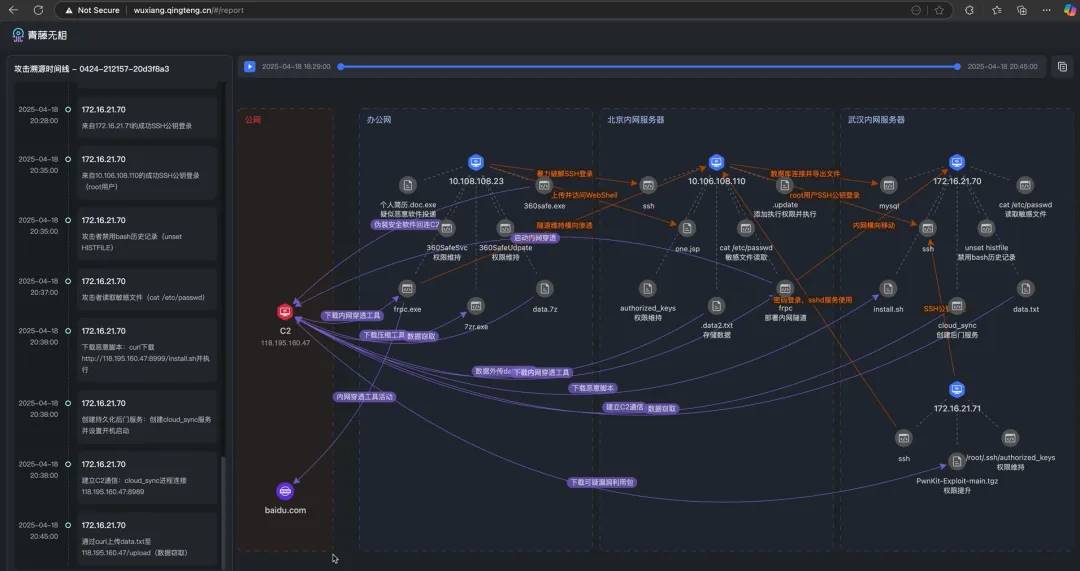
After completing complex attack scenario investigations, organizing alerts and investigation clues to generate reports is often time-consuming and labor-intensive. However, AI can achieve one-click summarization, clearly presenting the attack process through a visualized timeline, like a movie showcasing key nodes—the system automatically curates key evidence to generate key frames of the attack chain, incorporating environmental context information to ultimately create a dynamic attack chain graph that presents the entire attack trajectory in an intuitive, three-dimensional manner.
04 Conclusion
Clearly, AI technology development brings dual challenges to cybersecurity.
On one hand, attackers use AI to achieve automated, personalized, and covert attacks; on the other hand, defenders need to accelerate technological innovation to enhance detection and response capabilities through AI. In the future, the AI technology competition between attackers and defenders will determine the overall cybersecurity landscape, with the refinement of security agents being key to balancing risks and development.
The security agent "Wuxiang" brings new changes in security architecture and cognitive aspects.
Essentially, "Wuxiang" changes how AI is used, with its breakthrough lying in fusing multi-dimensional data perception, protection strategy generation, and decision explainability into an organic whole—transforming from the previous mode of using AI as a tool to empowering AI to work autonomously and automatically.
By correlating heterogeneous data such as logs, text, and traffic, the system can capture APT activity traces before attackers construct a complete attack chain. More critically, its decision process's visualized reasoning explanation makes the traditional tools' "knowing the what but not the why" black-box alerts a thing of the past—security teams can not only see threats but also understand the evolutionary logic behind them.
This innovation's essence is a paradigm shift in security thinking from "mending the fold after losing a sheep" to "preparing for a rainy day," redefining the rules of attack-defense confrontation.
"Wuxiang" is like a hunter with digital intuition: by real-time modeling micro-behavioral characteristics like memory operations, it can extract hidden custom Trojans from massive noise; the dynamic attack surface management engine continuously evaluates asset risk weights, ensuring protection resources are precisely directed to critical systems; while the intelligent threat intelligence digestion mechanism transforms daily thousands of alerts into actionable defense instructions, even predicting attack variant evolution directions—when traditional solutions are still struggling with existing intrusions, "Wuxiang" is already predicting and blocking the attacker's next move.
"The birth of the AI Intelligence Central System (high-level security agent) will completely reshape the cybersecurity landscape. And the only thing we need to do is to seize this opportunity thoroughly," said Zhang Fu.








