When these 10 dangerous signals appear, it means you may have been targeted by hackers.
Written by: Christoper Rosa
Translated by: AididiaoJP, Foresight News
Even This Cybersecurity Expert Almost Fell for It
Last weekend, news spread that a massive dataset containing 16 billion user identities began circulating online, including both previously leaked information and recently stolen login data. It is currently unclear who updated and republished this dataset. Although most of the database is a reorganization of past data breach incidents, the newly updated data is unsettling. This dataset is considered one of the largest single collections of exposed accounts in history.
Hackers are using this data to launch various attacks, and I became one of their targets.
The phishing attack launched against my personal devices and accounts on June 19 was the most sophisticated attack I have encountered in my decade-long cybersecurity career. The attackers first created the illusion that my accounts were under attack on multiple platforms, then impersonated a Coinbase employee offering "help". They combined classic social engineering techniques with coordinated tactics across SMS, phone, and forged emails, all designed to create a false sense of urgency, credibility, and scale effect. This fake attack was widespread and highly authoritative, which was the key to its deceptive nature.
The following will detail the attack process, analyze the danger signals I noticed, and the protective measures I took. I will also share key lessons and practical advice to help crypto investors safeguard their security in an increasingly threatening environment.
Historical and recently leaked data can be used by hackers to implement highly targeted multi-channel attacks. This once again confirms the importance of layered security protection, clear user communication mechanisms, and real-time response strategies. Both institutional and individual users can gain practical tools from this case, including verification protocols, domain name identification habits, and response steps that can help prevent a momentary oversight from evolving into a major security vulnerability.
SIM Card Hijacking
The attack began around 3:15 PM Eastern Time on Thursday with an anonymous text message claiming someone was trying to trick the mobile carrier into leaking my phone number to others, a technique known as SIM swapping.
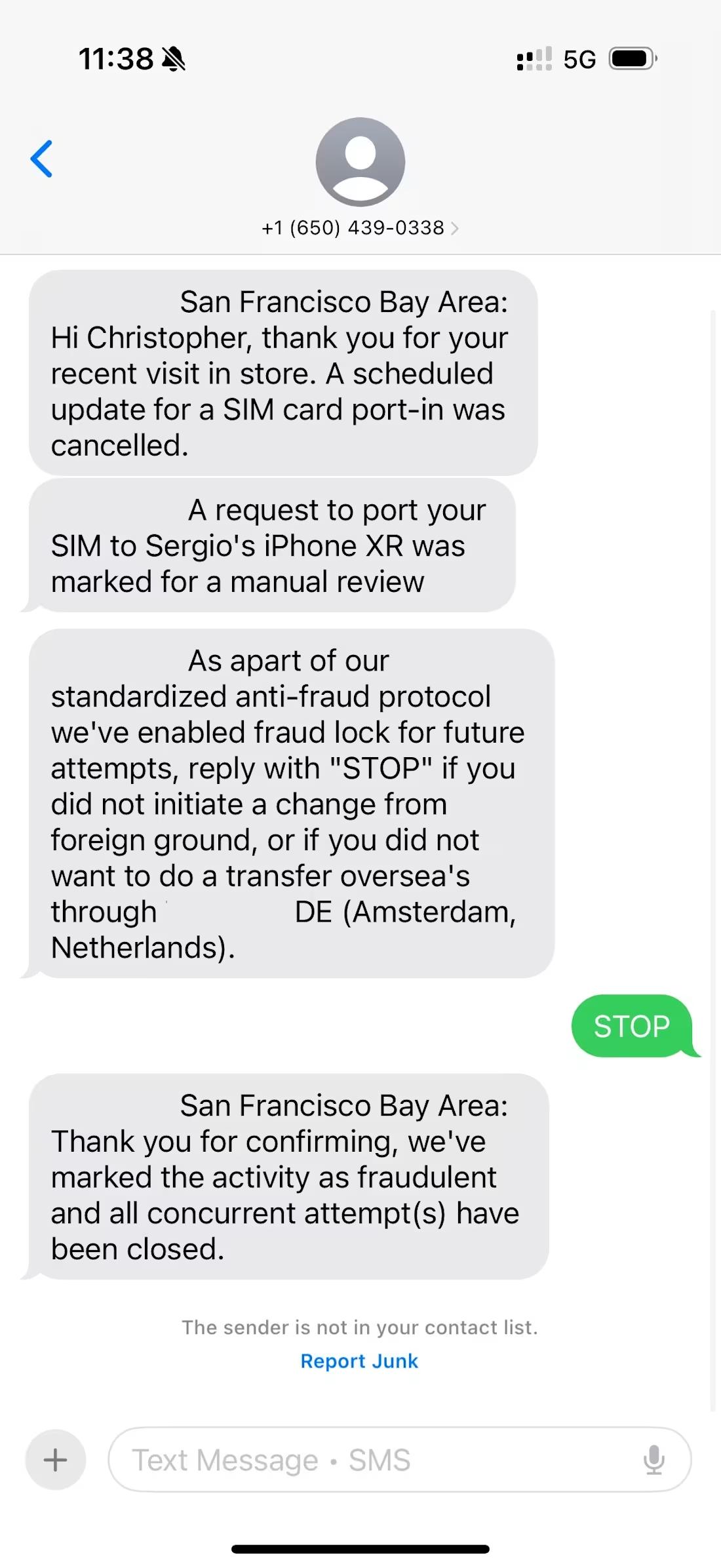
Note that this message did not come from a short message service number, but from a regular 10-digit phone number. Legitimate companies send SMS from short codes. If you receive a text from an unknown standard-length number claiming to be a company, it is likely a scam or phishing attempt.
These messages also contained contradictory content. The first SMS showed the leak was from the San Francisco Bay Area, while subsequent messages said it occurred in Amsterdam.
A successful SIM swap is extremely dangerous because attackers can obtain one-time verification codes used by most companies to reset passwords or access accounts. However, this was not a real SIM swap; the hackers were laying the groundwork for a more sophisticated scam.
(Translation continues in the same manner for the entire text)Mason subsequently sent a link to vault-coinbase.com, claiming it could review the security settings discussed in the first call. After completing the review, assets could be transferred to Vault, at which point my network security professionalism would finally emerge.
After entering the case number he provided, the opened page displayed the so-called "Removed API Connection" and "Create Coinbase Vault" buttons. I immediately checked the website's SSL certificate and found that this domain, registered only a month ago, had no connection to Coinbase. Although SSL certificates can usually create an illusion of legitimacy, official corporate certificates have clear ownership, and this discovery made me stop operations immediately.
Coinbase clearly states that they never use unofficial domains. Even when using third-party services, it should be a subdomain like vault.coinbase.com. Any operations involving exchange accounts should be performed through the official app or website.
I expressed my doubts to Mason, emphasizing that I only wanted to operate through the official app. He argued that app operations would cause a 48-hour delay, and the account would be locked after 24 hours. I refused again to make a hasty decision, and he then said he would escalate the case to the "Level 3 Support Team" to try to restore my Coinbase One protection.
After hanging up, I continued to verify the security of other accounts, and my sense of unease grew stronger.
Call from the "Level 3 Support Team"
About half an hour later, a Texas number called. Another American-accented person claimed to be a Level 3 investigator processing my Coinbase One recovery request. He said a 7-day review period was needed, during which the account would remain uninsured. He also "thoughtfully" suggested opening multiple Vaults for different chain assets, which seemed professional but actually never mentioned specific assets, only vaguely referring to "Ethereum, Bitcoin, etc."
He mentioned applying to the legal department to send chat records, and then began promoting Coinbase Vault. As an alternative, he recommended a third-party wallet called SafePal, though SafePal is indeed a legitimate hardware wallet, this was obviously a prelude to gaining trust.
When I questioned the vault-coinbase.com domain again, the other party still tried to alleviate my doubts. At this point, the attacker might have realized it was difficult to succeed and finally abandoned this phishing attack.
Contacting Coinbase's Real Customer Service
After ending the call with the second fake customer service representative, I immediately submitted a request through Coinbase.com. The real customer service representative quickly confirmed that there were no abnormal logins or password reset requests on my account.
He suggested immediately locking the account and collecting attack details to submit to the investigation team. I provided all fraudulent domains, phone numbers, and attack methods, and specifically asked about the sending permissions of no-reply@info.coinbase.com. The customer service acknowledged this was very serious and promised that the security team would conduct a thorough investigation.
When contacting exchange or custodian customer service, always use official channels. Legitimate companies will never actively contact users.
Experience Summary
Although I narrowly avoided being scammed, as a former network security professional, this near-miss experience made me deeply uneasy. Without professional training, I might have been deceived. If it were just an ordinary unknown call, I would have hung up immediately. It was the attackers' carefully designed series of actions, creating a sense of urgency and authority, that made this phishing attempt so dangerous.
I have summarized the following danger signals and protection recommendations, hoping to help crypto investors safeguard their funds in the current network environment.
(Translation continues in the same manner for the rest of the text)Revoke access rights for any applications or services you no longer use or cannot identify.
Enable real-time account alerts at available points
Notifications for logins, withdrawals, or security setting changes provide key early warnings of unauthorized activities.
Report all suspicious activities to the official support team of the service provider
Early reporting helps prevent broader attacks and contributes to the overall security protection of the platform.
Conclusion
For financial institutions, IT security teams, and executives, this attack highlights how hackers can bypass even the most mature security defenses when historical data is repurposed and combined with real-time social engineering. Threat actors no longer rely solely on brute force attacks but execute coordinated cross-channel strategies to gain trust and deceive users by mimicking legitimate workflows.
We must not only protect system and network security but also identify threats and take action to protect ourselves. Whether working at a crypto institution or managing crypto assets at home, everyone must understand how personal security vulnerabilities can evolve into systemic risks.
To defend against these threats, institutions must implement layered defense, such as domain name monitoring, adaptive authentication, multi-factor authentication against phishing, and clear communication protocols. Equally important is for enterprises to cultivate a cybersecurity literacy culture, ensuring every employee from engineers to executives understands their role in protecting the company. In today's environment, security is not just a technical function but a responsibility that must be shared from individuals to the entire organization.








