Author: Kalle Rosenbaum & Linnéa Rosenbaum

This chapter discusses how to protect your private financial information. It explains what "privacy" means in the context of Bitcoin, why it's important, and what it means that "Bitcoin is pseudoonymous." The chapter also analyzes how privacy data can be compromised, including both on-chain and off-chain leaks. Then, it discusses why Bitcoin should be fungible (i.e., any two Bitcoins can be exchanged for each other), and how fungibility and privacy are closely related. Finally, the chapter introduces some measures you can take to improve your own and others' privacy.
Bitcoin can be described as a semi-anonymous (using pseudonyms) system (see further discussion in Section 3.3 of this chapter), meaning users can use multiple pseudonyms (in the form of public keys). At first glance, this seems like a very good way to protect users from being identified, but in reality, it is extremely easy for people to unintentionally disclose their private financial information.
3.1 What does privacy mean?
The term "privacy" has multiple meanings in different contexts. In the context of Bitcoin, it generally means that users are not required to disclose their financial information to others; disclosure is solely voluntary.
But whether you realize it or not, there are many possibilities for privacy breaches. Data can be leaked from public blockchains or from other sources, such as malicious individuals intercepting your internet connection.
3.2 Why is privacy important?
The importance of privacy to Bitcoin seems obvious, but there are likely some aspects that you might not immediately think of. On the Bitcoin Talk forum , Gregory Maxwell listed the reasons he believes privacy is important, including free markets, security, and personal dignity:
Financial privacy is a prerequisite for the efficient functioning of a free market: if your suppliers and customers can see all your transactions (regardless of your wishes) when you do business, then you essentially cannot freely set prices. In isolation, if your accounts lack privacy, then your private operations lose their informational leverage: if you don't have sufficient privacy when paying your landlord, your landlord will see that you just got a raise and then raise your rent accordingly.
Financial privacy is also essential for personal security: if thieves can see all your income, earnings, and savings, they can use this information to target and rob you. Without privacy, malicious individuals have more ways to steal your identity, steal your valuables from your doorstep, or pretend to be someone you're dealing with… They can even tell you exactly how much money they want to swindle from you.
Financial privacy is also a necessary condition for personal dignity: Nobody likes having their income and spending habits commented on by a sleazy coffee shop employee or a noisy neighbor. Nobody wants to be interrogated by desperate parents about why they bought condoms (or sex toys). Your employer doesn't need to know which church you donate to. If we lack privacy, then only in a fully enlightened, unbiased world, where no one has undue power over others, can we retain our dignity and freely engage in legitimate transactions.
——Gregory Maxwell, Bitcoin Talk forum (2013)
Maxwell also discusses the issue of interchangeability, which we will cover in later chapters of this book; and we will also explain that privacy and the enforcement of laws are not contradictory.
3.3 Kana
As we mentioned earlier, in Bitcoin, people use pseudonyms, and these pseudonyms are the public keys. You often hear in the media that "Bitcoin is anonymous," which is inaccurate. Anonymity and pseudonymity are different.
Andrew Poelstra explained the forms of anonymity in transactions in a Bitcoin Stack Exchange post :
Complete anonymity means that when you spend money, there are absolutely no clues as to where the money came from or where it went. In theory, this is possible using cryptographic techniques such as "zero-knowledge proofs."
— Andrew Poelstra on Anonymity, Bitcoin Stack Exchange (2016)
The difference is that in a currency used under a pseudonym, you can track payments between pseudonyms, while in a currency used anonymously, you cannot. Because Bitcoin payments are traceable (using pseudonyms), it is not an anonymous system.
As we've mentioned, the encryption used in Bitcoin is public-key cryptography, but the actual encryption used is an address derived from that public key. Why use the address as a pseudonym instead of something else (like a descriptive name such as "watchme1984")? The Bitcoin Stack Exchange user "Tim S." explains it well :
For Bitcoin's core concept to be realized, you must ensure that the coins can only be spent using a single, given private key. This means that whatever you allow to own the coins must be (to some extent) bound to a public key.
Using arbitrary pseudonyms (such as custom usernames) means you must associate that pseudonym with a public key to use public/private key cryptography. This deprives users of the ability to securely create addresses/pseudonyms offline (for example, before someone can send money to the username "tdumidu," you must first declare within the blockchain that the username "tdumidu" is held by a public key "a1c…" and include a transaction fee so that others have a reason to accept it), reduces anonymity (because it encourages the reuse of pseudonyms), and unnecessarily bloats the blockchain. It also creates a false sense of security, making people think they are paying someone they know (if I registered the username "Linux Torvalds" before Linus, it's mine; people think they are donating to the founder of the Linux operating system, but they are actually giving money to me).
— Tim S. On kana, Bitcoin Stack Exchange (2014)
By using addresses (or public keys), we achieve important goals, such as eliminating the need to register pseudonyms in advance, reducing the incentive to reuse the same pseudonym, preventing blockchain bloat, and making it more difficult to impersonate others.
3.4 Blockchain Privacy
"Blockchain privacy" refers to the information that is revealed when you initiate a transaction on the blockchain. Every transaction discloses some information, including the transactions you send and the transactions you receive.
Satoshi Nakamoto discusses privacy within the blockchain in Chapter 7 of the Bitcoin white paper :
As an additional firewall, users should use a new key pair for each transaction to prevent them from being associated with the same owner. Transactions with multiple inputs will still expose some connections, inevitably revealing that these inputs belong to the same owner. The risk is that if the relationship between a public key and its owner is exposed, these connections could expose other transactions belonging to the same owner.
— Satoshi Nakamoto, Bitcoin: A Peer-to-Peer Electronic Cash System (2008)
The Bitcoin white paper summarizes the main privacy issues in blockchain as "address reuse" and "address clustering." The first issue, as the name suggests, is the reuse of the same address; the second issue refers to the ability to determine with a certain degree of certainty that a group of addresses belong to the same user.
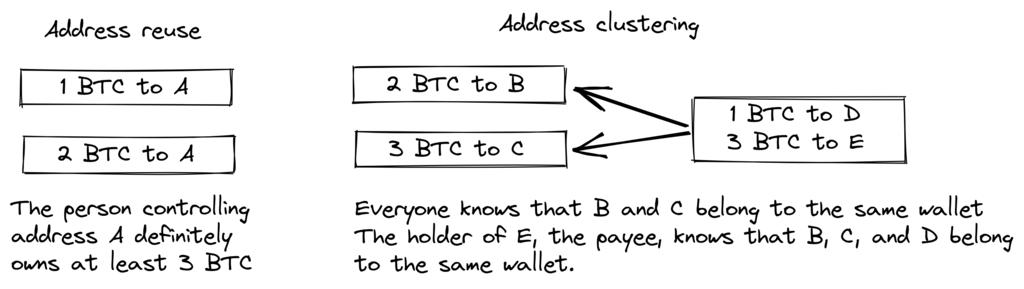
Figure 3. Standard privacy breach scenario on blockchain -
Chris Belcher explains in detail the different types of privacy breaches that can occur within the Bitcoin blockchain. I recommend that you at least read the first few sections under the heading "Blockchain attacks on privacy."
In summary, privacy within the Bitcoin blockchain is not perfect. Users need to put in a significant amount of work to achieve private transactions. Most users are not prepared to go that far for privacy. There also seems to be a clear conflict between privacy and ease of use.
Another important aspect is that the measures you take to protect your own privacy will also affect other users. If you are careless about your own privacy, the privacy of others may be compromised as a result. Gregory Maxwell explains this very clearly in the same Bitcoin Talk post we linked earlier , and includes an example:
The same thing happens in real life… A well-meaning white-hat hacker played a “brainwallet” hacking game in an online chat room (IRC) and found a private key containing about 250 BTC. We could identify the owner just from this address because they received a payment from a Bitcoin service that reused the address, and the white-hat hacker was able to persuade the service to hand over the user's contact information. He actually found the user on their phone, who was shocked and confused—but also relieved that they hadn't lost their money. Ultimately, it was a happy ending. (This isn't the only case… just one of the more interesting ones so far).
——Gregory Maxwell, Bitcoin Talk forum (2013)
In this case, we should certainly thank this well-intentioned hacker, but don't expect to encounter such hackers all the time.
3.5 Privacy without Blockchain
While blockchain has proven to be a significant source of privacy breaches, many other types of breaches are unrelated to blockchain, some quite subtle, ranging from keyloggers to internet traffic analysis. To understand these methods, reread Chris Belcher's article , especially the section under the heading "Non-blockchain attacks on privacy."
Among the many types of attacks, Belcher mentioned the possibility of others snooping on your internet connection, such as your internet service provider (ISP):
If an adversary sees a transaction or block being transmitted from your node, and no one has previously forwarded this transaction (or block) to you, then they can be almost 100% certain that you created the transaction and mined the block. Because internet connectivity is unavoidable, this adversary can link this revealed information to your IP address.
——Chris Belcher, Bitcoin wiki
However, the most significant privacy breaches come from cryptocurrency exchanges. Due to legal requirements commonly known as "KYC (Know Your Customer)" and "AML (Anti-Money Laundering)," exchanges and related companies in jurisdictions with such laws often have to collect users' personal information and build massive databases about which users own which Bitcoins. These databases are huge and attractive targets for malicious governments and criminal groups. There is indeed a market for this type of data, with hackers stealing it and selling it to the highest bidder. Worse still, the companies managing these databases are often inexperienced in protecting financial data; in fact, most are young startups, and we know of several known breaches, such as those at MobiQwik in India and HubSpot .
To reiterate, protecting your data from these various attacks is difficult, and you may ultimately not be able to do it completely. You must make trade-offs between convenience and the privacy that best suits your needs.
3.6 Interchangeability
In the context of currency, "fungibility" means that a coin can be exchanged for any other coin of the same kind. We briefly touched upon this interesting term in Section 3.2 . In an article discussing it, Gregory Maxwell points out :
Financial privacy is also a necessary condition for Bitcoin's homogeneity: if you can meaningfully distinguish one coin from another, their homogeneity is weak. If our homogeneity is actually too weak, then decentralization is impossible: if an important figure can publish a list of stolen coins and state that they will not accept payments from those coins, then you must carefully check the coins sent to you against that list and return the coins on the list (in case you receive money you can't spend). Then everyone is trapped checking blacklists published by different authorities just to avoid receiving unwanted coins. This increases friction and transaction fees, and makes Bitcoin (as a currency) less valuable.
——Gregory Maxwell, Bitcoin Talk forum (2013)
Here, he's referring to the dangers of a lack of homogeneity. Imagine you own a UTXO (Bitcoin coin). The history of this UTXO typically traces back several steps, involving many past transaction outputs. If any of these outputs were involved in any illegal, unwanted, or suspicious activity, potential recipients of your coins might reject them. If you assume your recipients will check your coins against centralized whitelists or blacklists, you might also start checking the coins you receive, just to be on the safe side. As a result, poor homogeneity is further exacerbated.
Adam Back and Matt Corallo gavea presentation on homogeneity at Scaling Bitcoin in Milan in 2016. Their ideas were consistent:
Bitcoin requires homogeneity to function properly. If you receive money but can't spend it, you'll start to doubt its usability. If you have doubts about the money you receive, you'll naturally seek out taint check services to check if "these coins are problematic," and then people will start refusing transactions. Essentially, this process transforms Bitcoin from a decentralized, permissionless system into a centralized, permissioned system; what you're receiving is essentially an "IOU" (IOU) from a blacklisted provider.
——Matt Corallo and Adam Back, Fungibility Overview (2016)
It appears that privacy and homogeneity are closely related. If privacy is weak—for example, coins from unwanted individuals might be blacklisted—homogeneity will also be weak. Similarly, if homogeneity is weak, privacy will be weakened: if a blacklist already exists, you'll inquire with the blacklist provider whether a particular coin can be received, which exposes your IP address, email address, and other sensitive information. These two characteristics overlap extremely closely, making it difficult to discuss either one in isolation.
3.7 Privacy Protection Measures
To help people protect their privacy, many technologies have been developed. One of the most prominent is, as Satoshi Nakamoto stated in the white paper, using a dedicated address for each transaction; but other measures exist. This article does not intend to guide readers to become privacy ninjas. However, "Bitcoin Q+A" provides a brief summary of privacy-enhancing technologies , ordered somewhat by ease of implementation. Reading it, you'll notice that Bitcoin privacy often must be addressed alongside privacy issues outside of Bitcoin. For example, you shouldn't boast about how much Bitcoin you have; you should use Tor and a VPN. This article also lists some privacy protection measures directly related to Bitcoin:
Full node
If you don't use your own full node, you'll be exposing a lot of information about your wallet to service providers across the internet. Running a full node is a great first step.
Lightning Network
There are many protocols on Bitcoin, such as the Lightning Network and the Liquid sidechain developed by Blockstream, which can provide some privacy benefits.
CoinJoin
This is a way to allow many people to combine their individual transactions into a single transaction, making it more difficult for blockchain analytics to determine who is paying whom.
In aninterview at the Breaking Bitcoin conference, Chris Belcher provided an interesting real-world example of improving privacy:
There's a Bitcoin casino. Online gambling is illegal in the US, so any Coinbase customer who deposits funds directly into Bustabit will have their account frozen because Coinbase is constantly monitoring them. Bustabit did a few things. First, they used a technique called "change avoidance," which allowed them to see if they could construct a transaction without giving change. This saved on miner fees and hindered blockchain analysis. Additionally, they put their heavily reused deposit addresses on joinmarket. From then on, Coinbase customers were no longer frozen. It seems that after this, Coinbase's monitoring service couldn't analyze whether its customers were participating in Bustabit. Therefore, these analytical algorithms can be defeated.
— Chris Belcher on “Breaking Bitcoin Privacy,” Breaking Bitcoin Conference (2019)
He mentioned this case on the Bitcoin wiki's privacy page, as well as elsewhere.
Also note that better privacy can be achieved by developing protocols on Bitcoin, such as the Lightning Network:
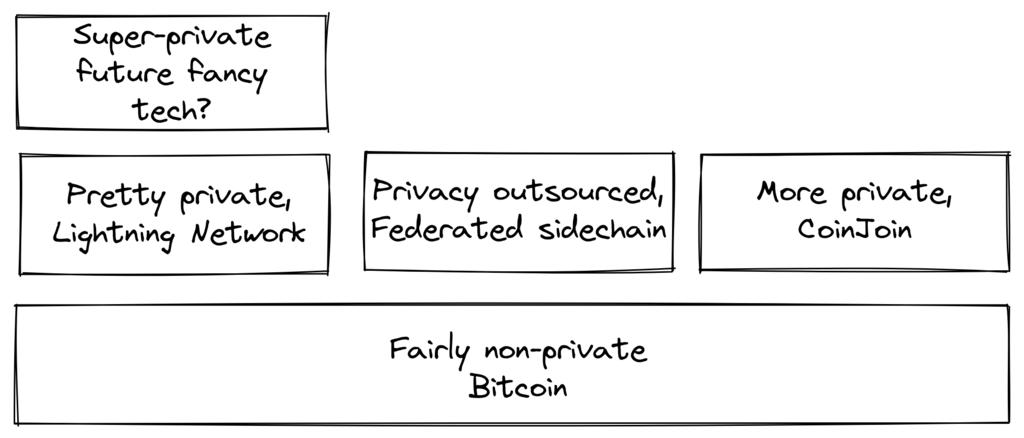
- Figure 4. Layers above Bitcoin can add privacy -
As we pointed out in Chapter 2 ( Chinese translation ), as technological layers stack up, the need for trust only increases, but privacy seems to be an exception; it can either be enhanced or deteriorated. Why? Because (as explained in Section 8.2.4 of this book ), layers implemented on top of Bitcoin must occasionally use transactions within the blockchain, otherwise they are not "Bitcoin-based." Layers that enhance privacy typically try to use the base layer as little as possible to reduce the information leaked at the base layer (the Bitcoin blockchain).
The image above illustrates techniques that can improve your privacy to some extent. But there are other methods. As mentioned at the beginning of this chapter, Bitcoin is a pseudonymous system. This means that Bitcoin users do not directly reveal their real names and other personal data, but only their public keys. A public key is a pseudonym, and a user can have many pseudonyms. In an ideal world, your personal identity and your Bitcoin pseudonym are separate. Unfortunately, due to the privacy issues mentioned earlier in this chapter, this separation often deteriorates over time.
To mitigate the risk of your personal data being leaked, you shouldn't give it up in the first place, nor should you entrust it to centralized services—they build massive databases that themselves can be compromised (see Section 3.5). A Bitcoin Q+A article explains KYC and the dangers it entails. The article also suggests a few steps you can take to improve your situation.
Fortunately, there are some options that allow you to buy Bitcoin from non-KYC sources. These are all peer-to-peer exchanges, meaning you trade directly with another individual without using a centralized third party. However, some people sell other currencies besides Bitcoin, so we urge you to be careful.
—— Bitcoin Q+A, bitcoiner.guide
This article suggests that you avoid using exchanges that require KYC/AML and instead try private trading or use decentralized exchanges (such as BISQ ).
For more in-depth information on privacy measures, please refer to the aforementioned privacy wiki page , starting with the heading "Methods for improving privacy (non-blockchain)".
3.8 Conclusion
Privacy is extremely important, but it's difficult to achieve completely. There's no one-size-fits-all solution for privacy. To ensure good privacy for your Bitcoin, you must take proactive measures, some of which are expensive and time-consuming.








