The crypto industry experienced a significant escalation in global cryptocurrency thefts in 2025, with total losses exceeding $3.4 billion from January to early December, according to a new report from Chainalysis.
This increase is largely due to hackers linked to North Korea, who were responsible for the majority of the stolen funds during the year.
Inside North Korea's record-breaking $2 billion crypto heist.
In its latest report, blockchain analytics firm Chainalysis stated that while the frequency of attacks from the Democratic People's Republic of Korea (DPRK) has decreased significantly, the amount of cryptocurrency stolen has reached a record high.
North Korean hackers stole at least $2.02 billion worth of digital assets in 2025. This represents a 51% increase compared to the previous year. Compared to 2020, this amount has increased by approximately 570%.
“This year’s record amount comes from far fewer attacks than in previous years. This shift – fewer incidents but greater value – is due to the major Bybit hack in March 2025,” Chainalysis stated.
The report also revealed that groups linked to the DPRK were responsible for a record 76% of all attacks on services this year.
Overall, the 2025 figures push the lowest estimate of the total amount of cryptocurrency stolen by North Korea to $6.75 billion.
“This trend is the continuation of a long-term process. North Korean hackers have consistently demonstrated a high level of sophistication, and their activity in 2025 shows they are constantly changing their tactics and attack targets,” Andrew Fierman, Head of National Security Intelligence at Chainalysis, Chia BeInCrypto.
Based on historical data, Chainalysis determined that DPRK continues to carry out attacks of significantly higher value compared to other hacker groups.
"This pattern suggests that when North Korean hackers strike, they consistently target large services to maximize impact," the report states.
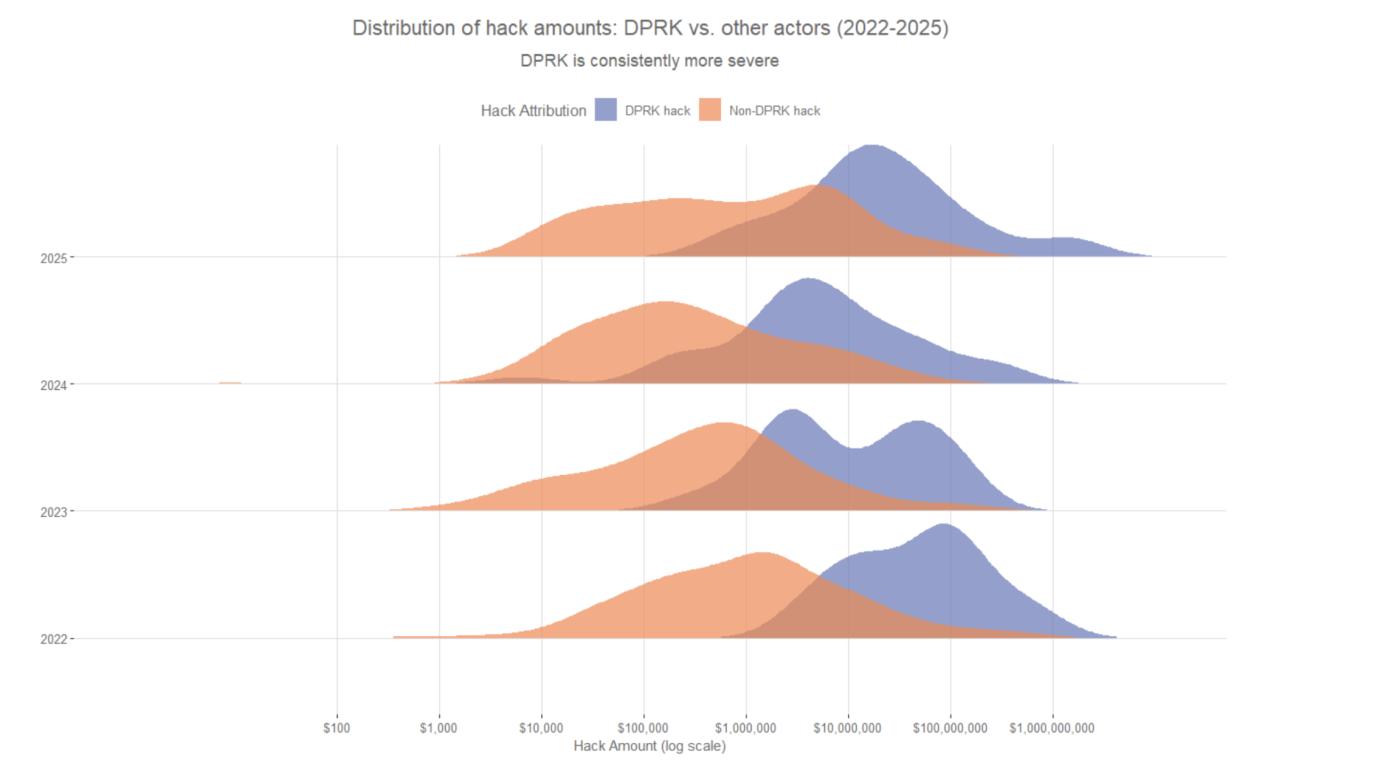 North Korea compared to other hackers. Source: Chainalysis
North Korea compared to other hackers. Source: ChainalysisAccording to Chainalysis, hackers linked to North Korea are increasingly making a significant impact by infiltrating technical positions within crypto companies. This allows them access to insider information and makes it easier to carry out more destructive attacks.
In July, blockchain investigator ZachXBT published an article alleging that individuals linked to North Korea had infiltrated between345 and 920 jobs in the crypto industry.
"Part of the reason for this record number may be North Korea's increased use of IT recruitment tactics at exchanges, custody units, and web3 companies, which helps shorten the time it takes to infiltrate and move data before carrying out large-scale thefts," the report noted.
These hacker groups also employ tactics such as impersonating recruiters and approaching employees working in the industry to scam them.
Furthermore, BeInCrypto recently reported that hackers have been impersonating industry insiders, organizing fake Zoom and Microsoft Teams meetings to steal a total of over $300 million.
“The DPRK is always looking for new attack avenues, exploiting every weakness to steal money. Because the country is limited in its participation in the global economy, North Korea has become a real threat with high motivation, scale, and sophistication. A major reason for the surge in attacks this year is the hijacking of security keys at centralized platforms,” Fierman added.
Chainalysis outlines a 45-day money laundering scenario used by North Korean hackers.
Chainalysis found that North Korean money laundering practices differ significantly from those of other criminal groups. The report indicates that these groups typically Chia funds transferred on the blockchain into smaller amounts, with over 60% of transactions valued at under $500,000.
In contrast, other criminal groups typically send larger amounts of stolen money, with approximately 60% of this amount falling within the range of $1 million to over $10 million. Chainalysis argues that this strategy demonstrates the calculated and sophisticated nature of North Korea's money laundering, even though the total amount stolen is significantly larger.
The company also pointed out a clear difference in how intermediary services are used. North Korean hackers primarily rely on money transfer services, Chinese-language guarantees, as well as bridge and mixing tools to conceal transaction traces. They also utilize specialized platforms like Huione to facilitate money laundering .
Meanwhile, other hacker groups often use decentralized exchanges, centralized platforms, peer-to-peer services , and lending protocols.
“These trends suggest that North Korea operates in an environment and with objectives entirely different from typical cybercrime groups. Their use of numerous professional money laundering services speaking Chinese and OTC traders indicates that the DPRK has close ties to illicit organizations in the Asia-Pacific region, continuing North Korea’s tradition of using networks in China to infiltrate the international financial system,” Chainalysis commented.
Chainalysis also discovered a recurring money laundering pattern that typically occurs over a 45-day period. In the first few days following an attack (days 0-5), individuals linked to North Korea prioritize separating the stolen funds from their original source. The report notes a sharp increase in the use of DeFi (decentralized finance) protocols and money mixing services during this initial phase.
During the second week (October 6-10), activity shifted towards services that allowed for broader integration. Money began flowing to centralized exchanges and platforms with limited KYC (identity verification) requirements.
Money laundering activities still occur through supplemental money mixing services, albeit on a smaller scale. Additionally, cross-chain bridges are also used to conceal asset movements.
"This phase is a critical transitional period as funds begin to move toward conversion or withdrawal services," the unit noted.
In the final stage (days 20-45), interaction with services supporting conversion or withdrawal increases. Exchanges without KYC, secure services, fast swap platforms, and Chinese-language services are prominent during this period. Additionally, criminal funds return to centralized exchanges to be mixed with legitimate transactions.
Chainalysis emphasizes that this recurring 45-day money laundering timeframe provides crucial data for authorities. It also highlights the limitations hackers face and their reliance on certain intermediaries.
“North Korea implements an extremely rapid and effective money laundering strategy. Therefore, the crypto industry needs a coordinated and timely response. Law enforcement agencies and businesses, from exchanges to blockchain analytics firms, must work together to intercept the flow of money whenever an opportunity arises, whether that's when assets pass through stablecoins or when they reach an exchange where the funds can be frozen immediately,” Fierman commented.
While not all stolen assets follow this timeline, it remains a common occurrence on the blockchain. However, the research team also acknowledges potential blind spots, as some activities such as private key transfers or Off-Chain OTC transactions may not be observable through blockchain data unless third-party information is available.
Outlook for 2026
Chainalysis's Head of National Security Intelligence Chia BeInCrypto that North Korea will certainly always look for ways to exploit existing vulnerabilities. Cases like Bybit, BTCTurk, and Upbit this year demonstrate the growing difficulties facing centralized exchanges, and the tactics can change at any time.
The recent attacks on Balancer and Yearn also show that older protocols are also targets for hackers, he said.
"While we don't know what will happen in 2026, we are certain North Korea will want to maximize the benefits of its objectives – meaning that services with large reserves must always prioritize high levels of security to avoid becoming the next victim."
The report also stressed that as North Korea increasingly relies on cryptocurrency theft to fund national priorities and circumvent sanctions, the entire industry needs to understand that this hacking group operates on motivations and constraints that are distinctly different from those of typical cybercriminals.
“This nation’s remarkable performance in 2025 – despite a 74% drop in recorded attacks – suggests we may only be seeing the most visible part of their overall operation,” Chainalysis added.
This unit believes the major challenge in 2026 will be detecting and preventing these large-scale campaigns before the North Korean-linked group can carry out an attack similar in scale to the Bybit hack .







