*This article has been automatically translated. Please refer to the original article for accurate content.
summary
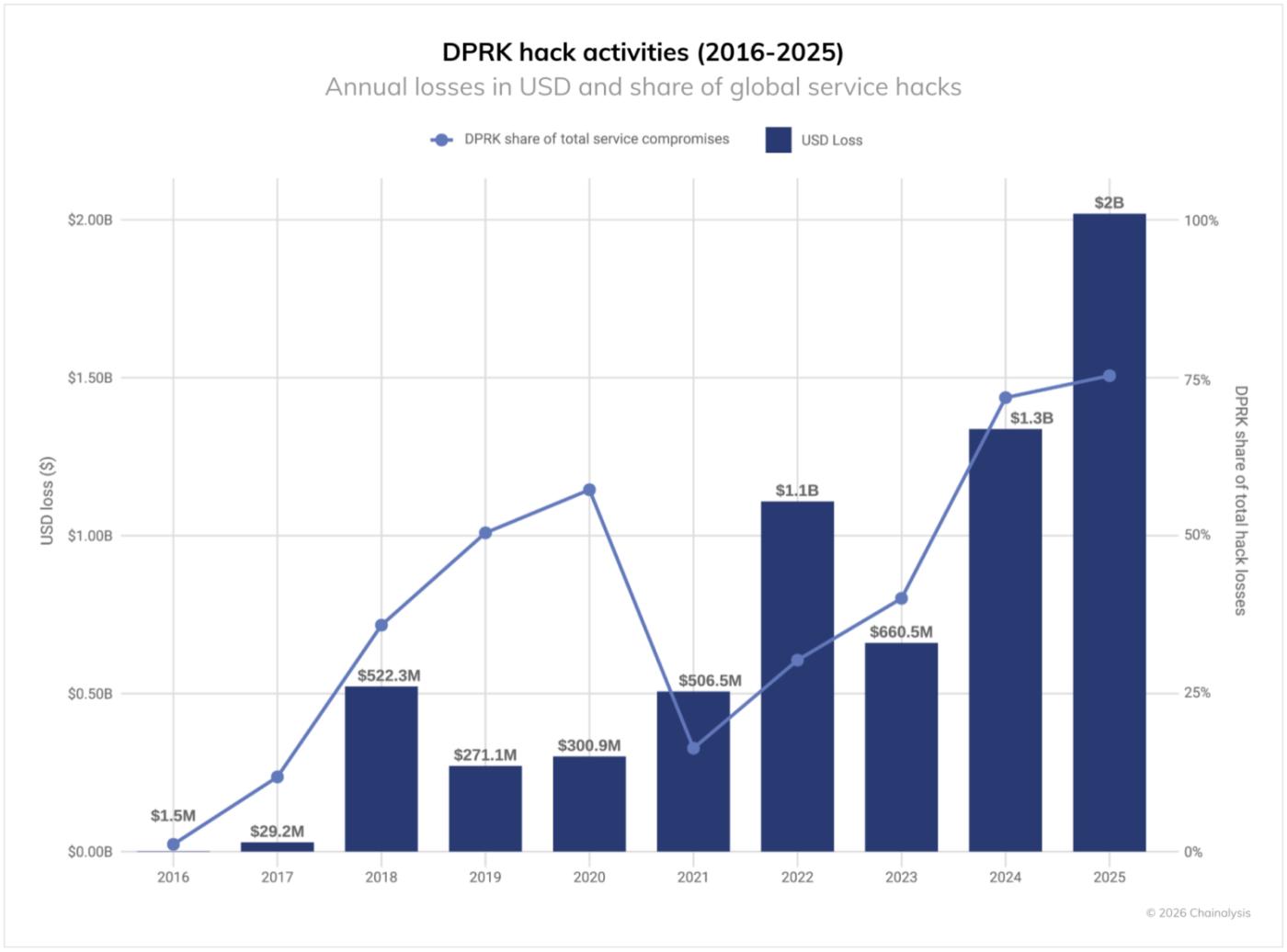
- North Korean hackers will steal $2.02 billion in crypto assets in 2025, a 51% increase from the previous year, bringing the total damage to $6.75 billion. The number of attacks is on the decline.
- North Korea has managed to steal huge sums of money from a small number of cryptocurrency services by placing IT workers within the services and using sophisticated impersonation techniques to target management.
- North Korea favors Chinese-language money laundering services, bridging services, and mixing protocols, and tends to complete its laundering of funds in about 45 days after large-scale thefts.
- In 2025, breaches of personal wallets surged to 158,000, with 80,000 victims, but the total losses ($713 million) were down from 2024.
- Although the total value of assets held (TVL) in decentralized finance (DeFi) has increased, the amount of damage caused by hacking in 2024-2025 has been contained, suggesting that strengthened security measures may be having an effect.
2025 was another challenging year for the cryptocurrency ecosystem, with the amount of theft continuing to rise. Our analysis reveals a shift in cryptocurrency theft patterns, with four key changes: North Korea (DPRK) remains the biggest threat, targeted attacks on centralized services are becoming more severe, consumer wallets are increasingly being compromised, and decentralized finance (DeFi) hacking trends are showing signs of diverging.
These trends are clearly visible in the data, highlighting the dramatic shift in the cryptocurrency theft landscape across different platforms and victim demographics. As digital assets continue to grow in popularity and reach new heights in value, understanding evolving security threats becomes increasingly important.
The big picture: Over $3.4 billion stolen in 2025
Between January and early December 2025, the cryptocurrency industry saw over $3.4 billion stolen, with the February attack on Bybit alone accounting for $1.5 billion of that.
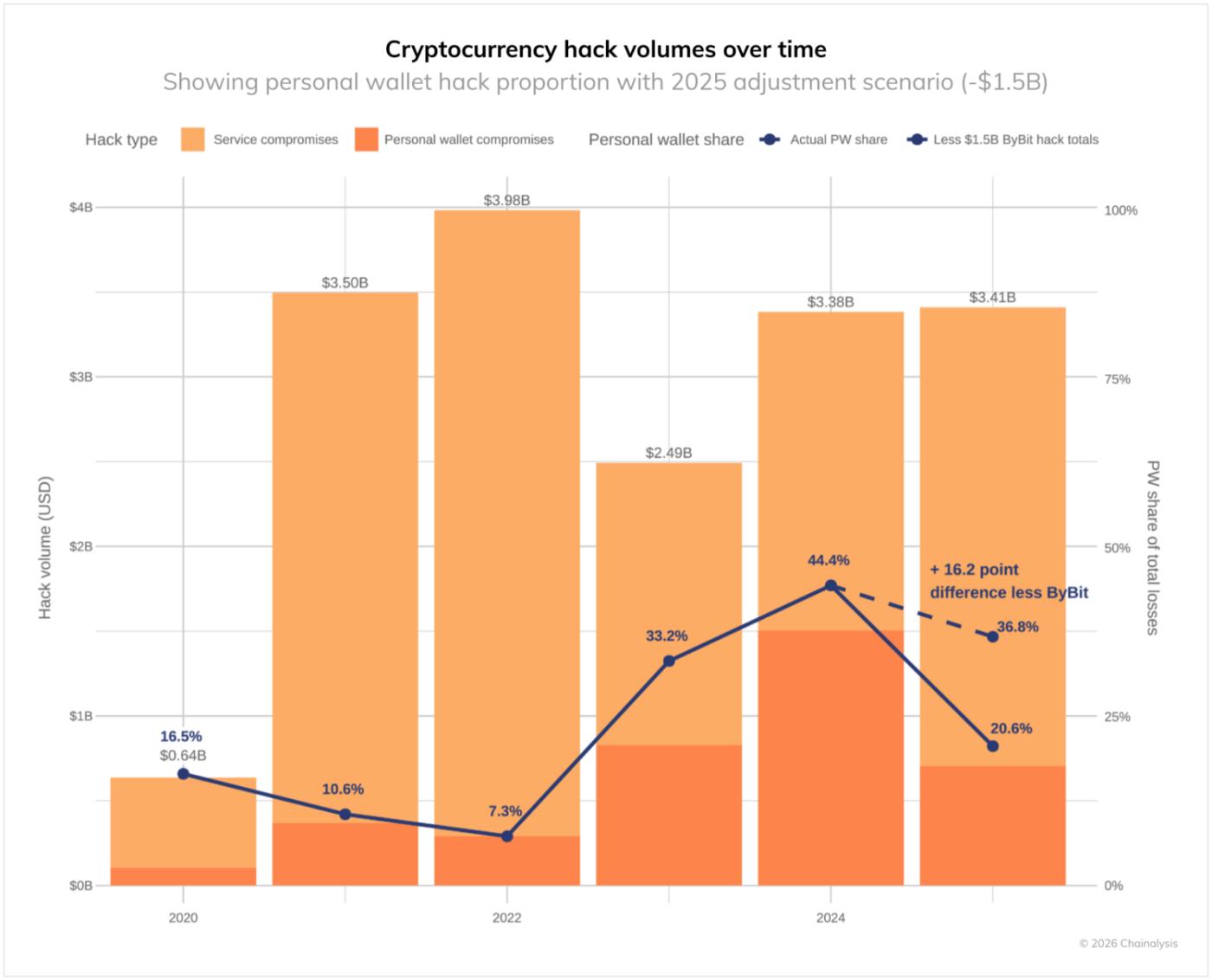
Behind this total, there is also an important shift in the composition of thefts: the proportion of losses due to compromised personal wallets will increase significantly, from 7.3% of the total in 2022 to 44% in 2024, and would have been 37% in 2025 if the Bybit incident had not had a significant impact.
Meanwhile, centralized services have experienced massive losses due to private key hacks. While these platforms have extensive resources and dedicated security teams, they remain vulnerable due to fundamental security challenges. While these incidents are rare (see chart below), when they do occur, they are extremely severe, accounting for 88% of losses in Q1 2025.
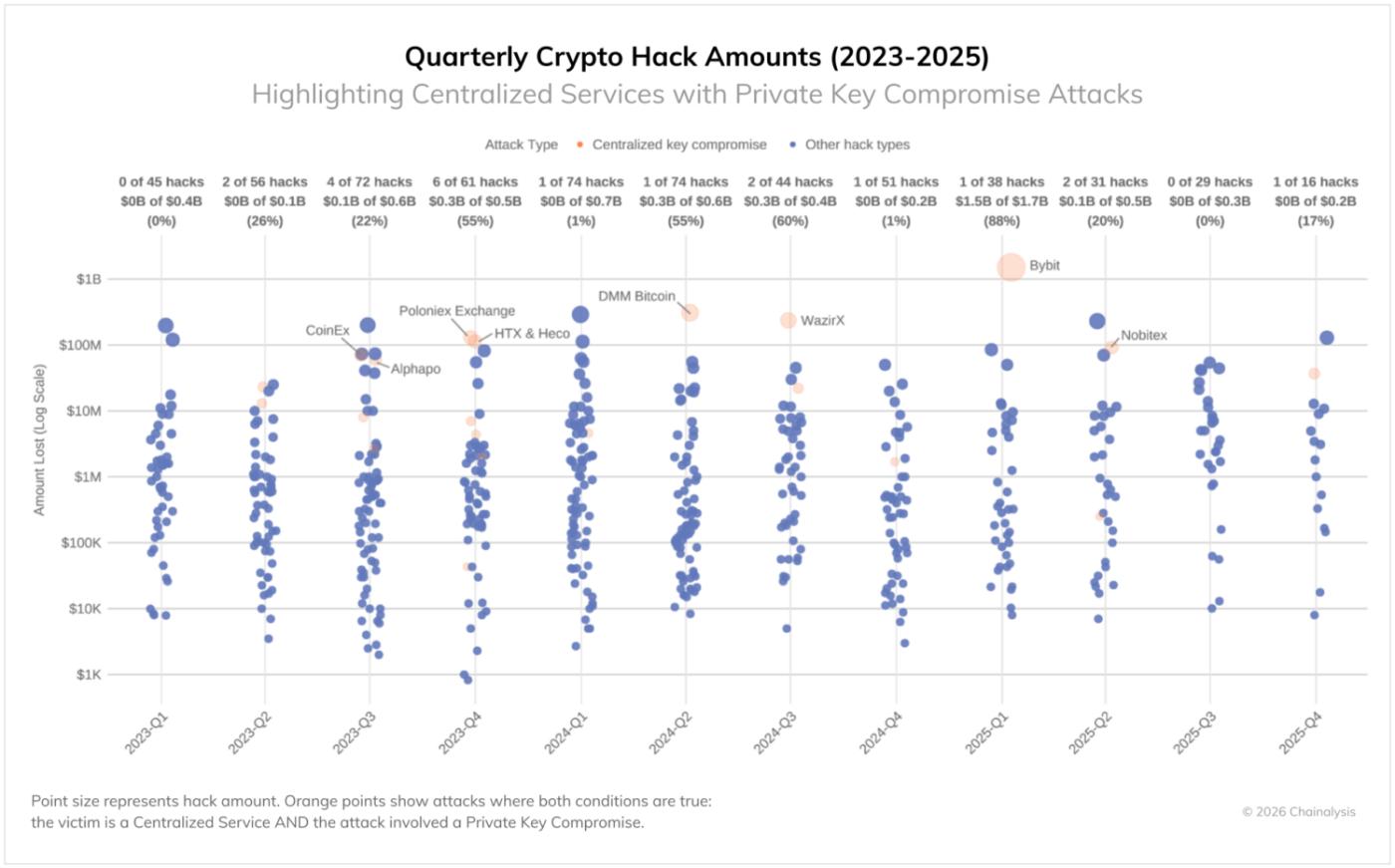
The persistently high value of thefts indicates that while cryptocurrency security has improved in some areas, attackers continue to have success through multiple methods.
The top three hacking incidents accounted for 69% of total losses, with the damage disparity expanding by more than 1,000 times
While the movement of stolen funds has traditionally been driven by exceptionally large incidents, this trend has grown even more in 2025. For the first time, the ratio of the largest hack to the overall median exceeded 1,000x. The largest incidents have stolen 1,000x more funds than typical incidents, even surpassing the peak of the 2021 bull market (in USD terms at the time of the incident).
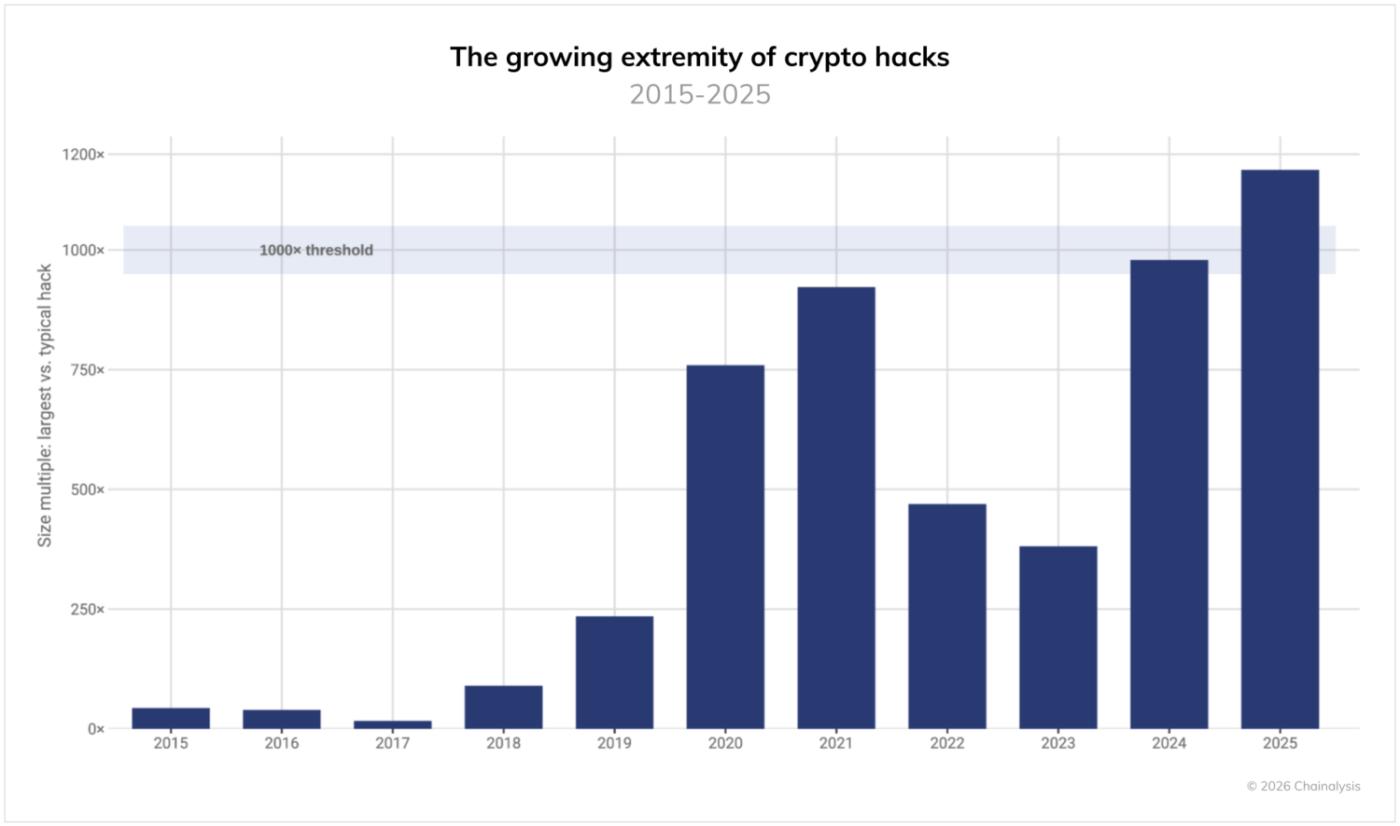
This widening disparity has dramatically increased the concentration of losses. The top three hacks in 2025 accounted for 69% of all service losses, with individual incidents having a disproportionate impact on the annual total. While the number of incidents is volatile and median losses increase with rising asset prices, the risk of catastrophic damage is accelerating.
North Korea remains the biggest cryptocurrency threat despite declining numbers
The Democratic People's Republic of Korea (North Korea) remains the largest nation-state threat to cryptocurrency security, achieving record-breaking thefts even as analysis shows a significant decrease in attack frequency. In 2025, North Korean hackers stole at least $2.02 billion in cryptocurrency, a 51% increase from the previous year (and an increase of $681 million from 2024). This was the worst year on record in terms of value, with North Korean attacks accounting for a record 76% of all service breaches. This brings the cumulative total of North Korean cryptocurrency thefts to a lower bound of $6.75 billion.
North Korean attackers primarily deploy IT workers within cryptocurrency services to gain privileged access and carry out large-scale attacks. The record-breaking losses in 2025 are likely the result of strengthening initial access and lateral movement through IT workers at exchanges, custodians, and Web3 companies.
More recently, the IT worker model has evolved, moving beyond simple employee infiltration to increasingly posing as recruiters from prominent Web3 and AI companies to obtain victim credentials, source code, and VPN/SSO access through a fake recruitment process. Targeting executives, social engineering techniques derived from the IT worker scam are expanding, including fake approaches posing as strategic investors or acquiring companies to seek access to system information and infrastructure through pitches and simulated due diligence.
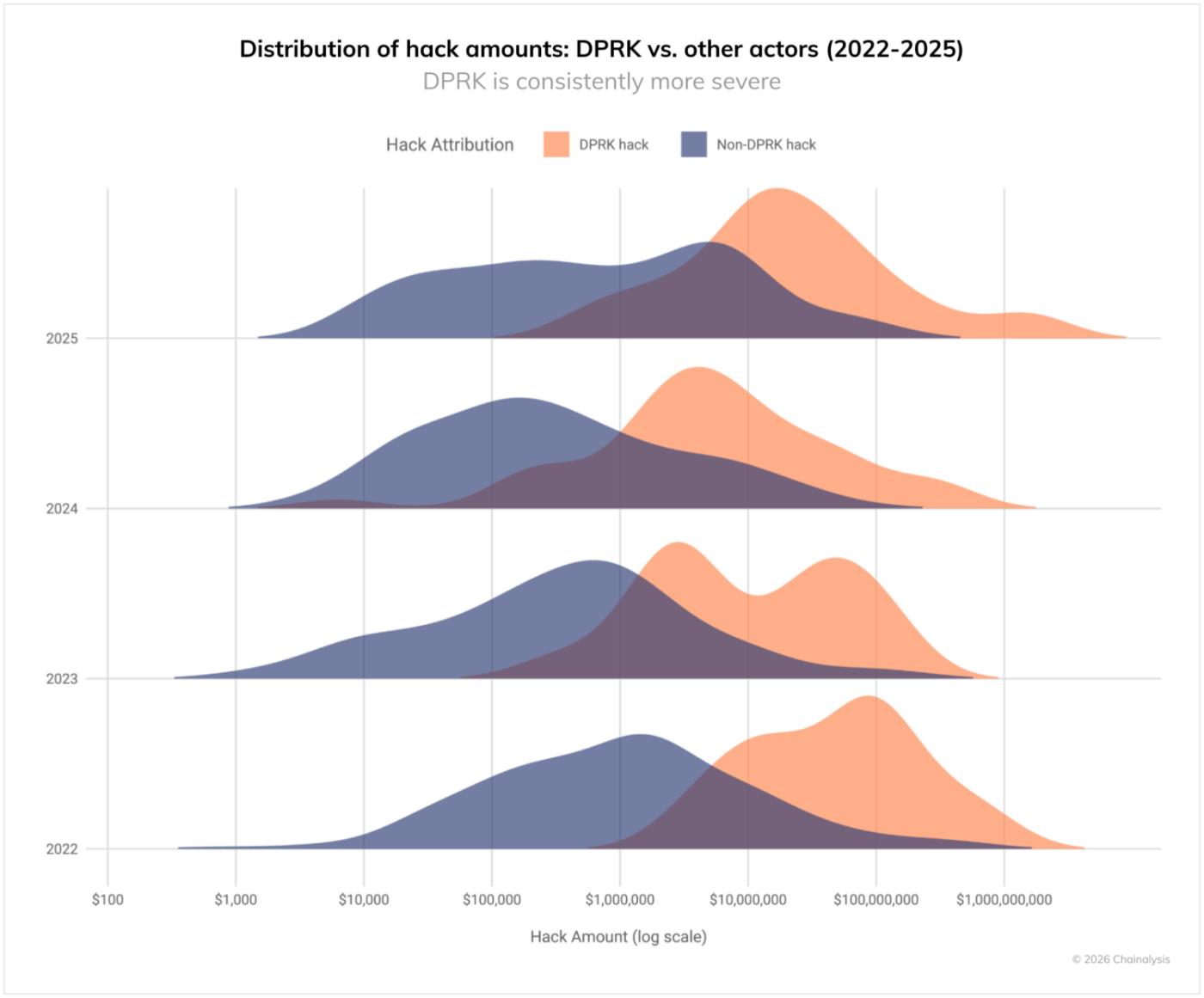
As usual, North Korea is committing significantly higher thefts than other attackers. As the graph below shows, North Korea-related hacks from 2022 to 2025 are concentrated in the largest volume range, while non-North Korean attacks are more evenly distributed. North Korean attacks are targeting large-scale services to maximize impact.
The record-breaking damage in 2025 occurred despite a significant decrease in the number of confirmed cases, which is thought to be largely due to the Bybit incident in February.
North Korea's unique money laundering pattern
The massive influx in early 2025 has shed unprecedented light on how North Korean actors are laundering crypto assets on a large scale, revealing their distinctive methods and operational preferences and weaknesses that set them apart from other cybercriminals.
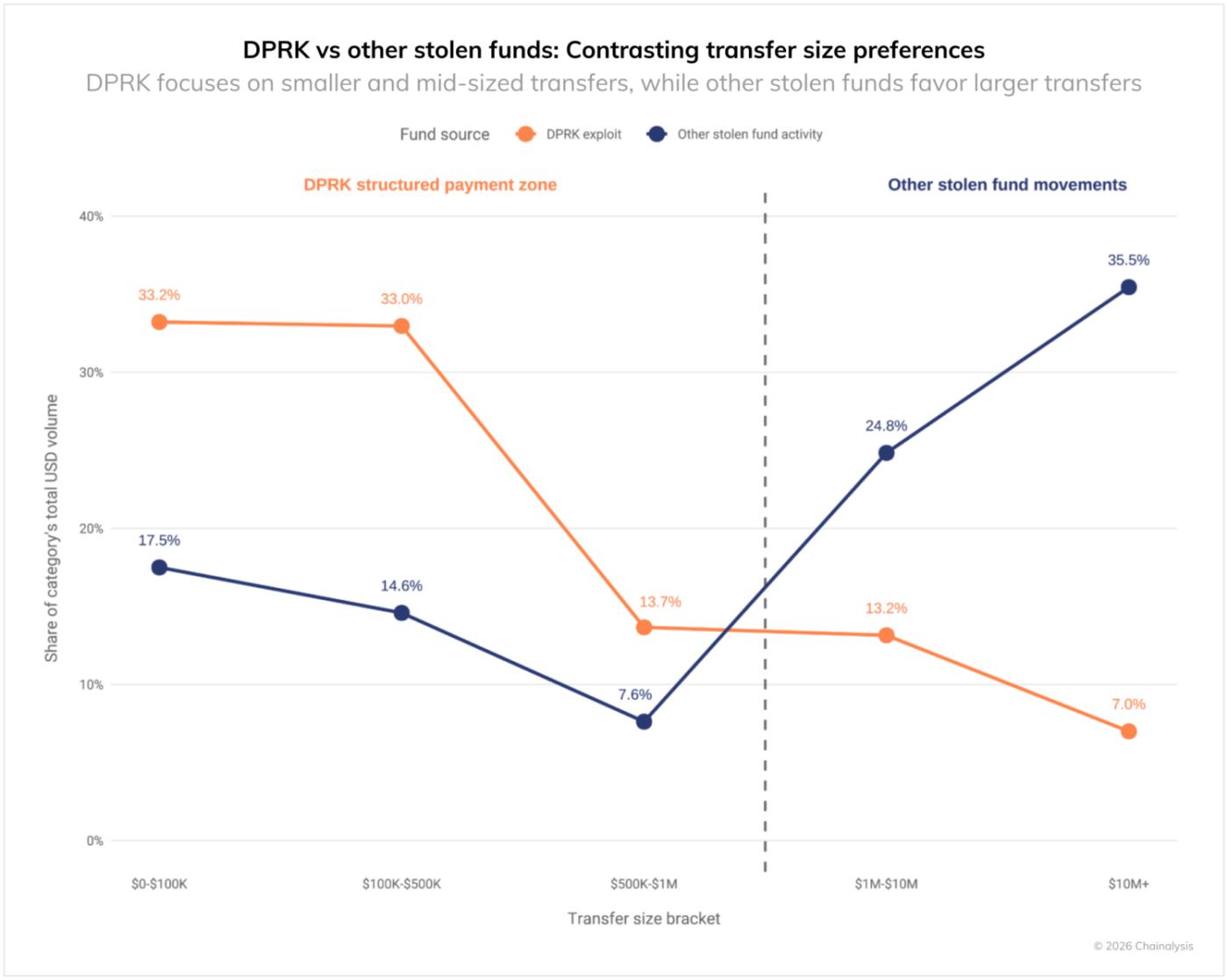
North Korea's money laundering is characterized by a unique blanket pattern, with over 60% of funds concentrated in transfers of less than $500,000. In contrast, other criminals mainly transfer large amounts of over $1 million to $10 million. While North Korea steals large amounts, it divides its on-chain transfers into smaller amounts, demonstrating the sophistication of its money laundering operations.
Compared to other criminals, North Korea has a strong preference for the following methods of laundering money:
- Chinese-language money transfer and collateral services (+355% to +1,000% or more): These are the most distinctive, relying on Chinese-speaking money laundering networks with numerous launderers, often with weak compliance controls.
- Bridging services (+97%): Leveraging asset transfers between blockchains, complicating tracking.
- Mixing services (+100% difference): Often used to hide the flow of funds.
- Specialized services like Huione (+356%): Strategic use of specific services to facilitate cleaning.
Other criminals focus on:
- Lending Protocols (-80% difference): North Korea has little use for these decentralized financial services.
- No KYC exchanges (-75% difference): Surprisingly, no KYC exchanges are more commonly used by other criminals than by North Koreans.
- P2P Exchanges (-64% difference): North Korea has little interest in P2P platforms.
- Centralized Exchanges (-25% difference): Other criminals interact more with traditional exchanges.
- Decentralized Exchanges (DEX) (-42% difference): Other criminals value the liquidity and anonymity of DEXs.
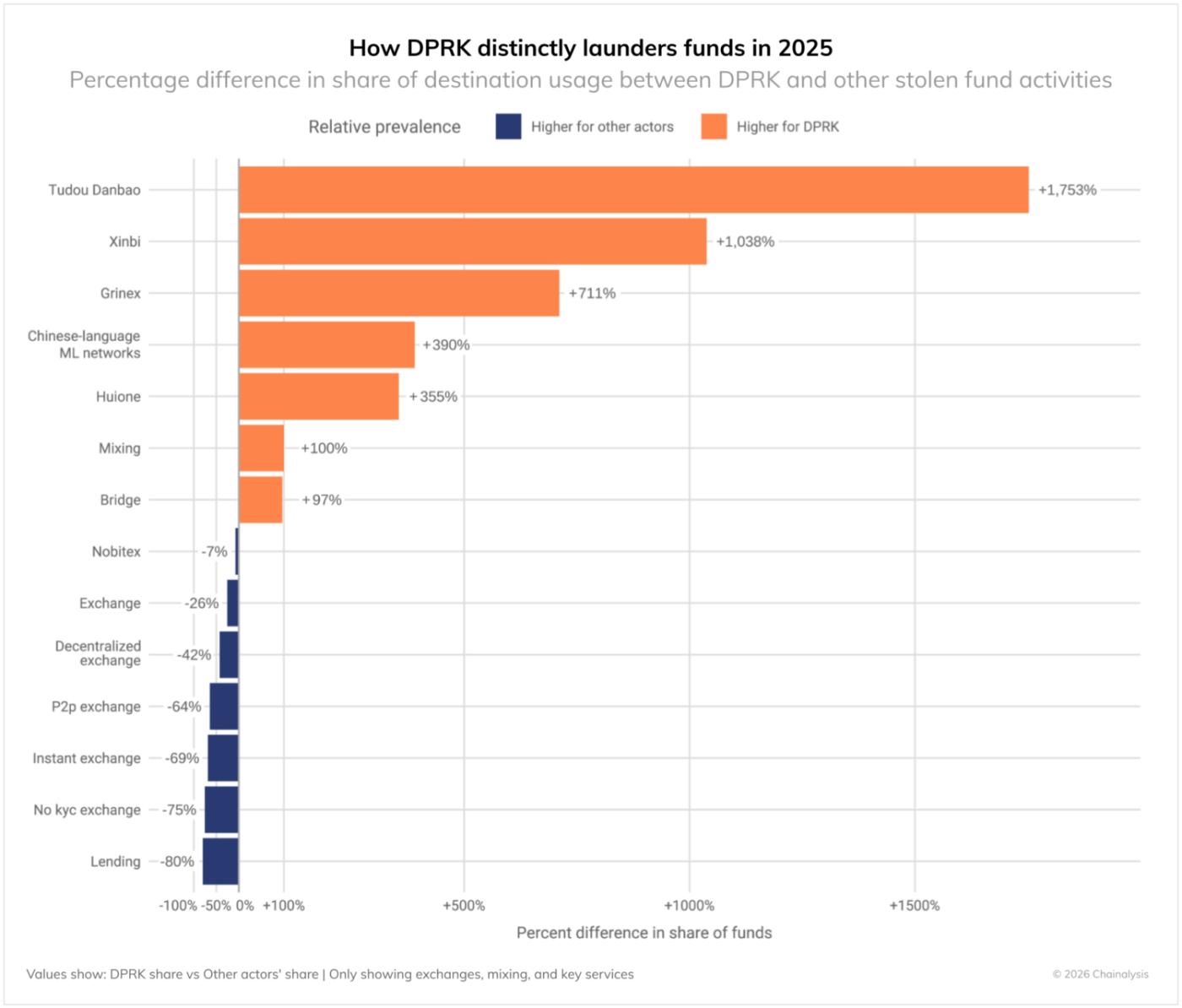
These patterns suggest that North Korea operates with different constraints and objectives than typical cybercriminals. The use of Chinese-language money laundering services and OTC traders is consistent with North Korean actors' close collaboration with illicit networks in the Asia-Pacific region and their historical use of China-based networks as a means to access the international financial system.
Timeline of money laundering after North Korea hack
Analyzing on-chain activity following North Korea-related hacks consistently reveals a multi-wave laundering chain in which stolen funds are deployed over a period of approximately 45 days:
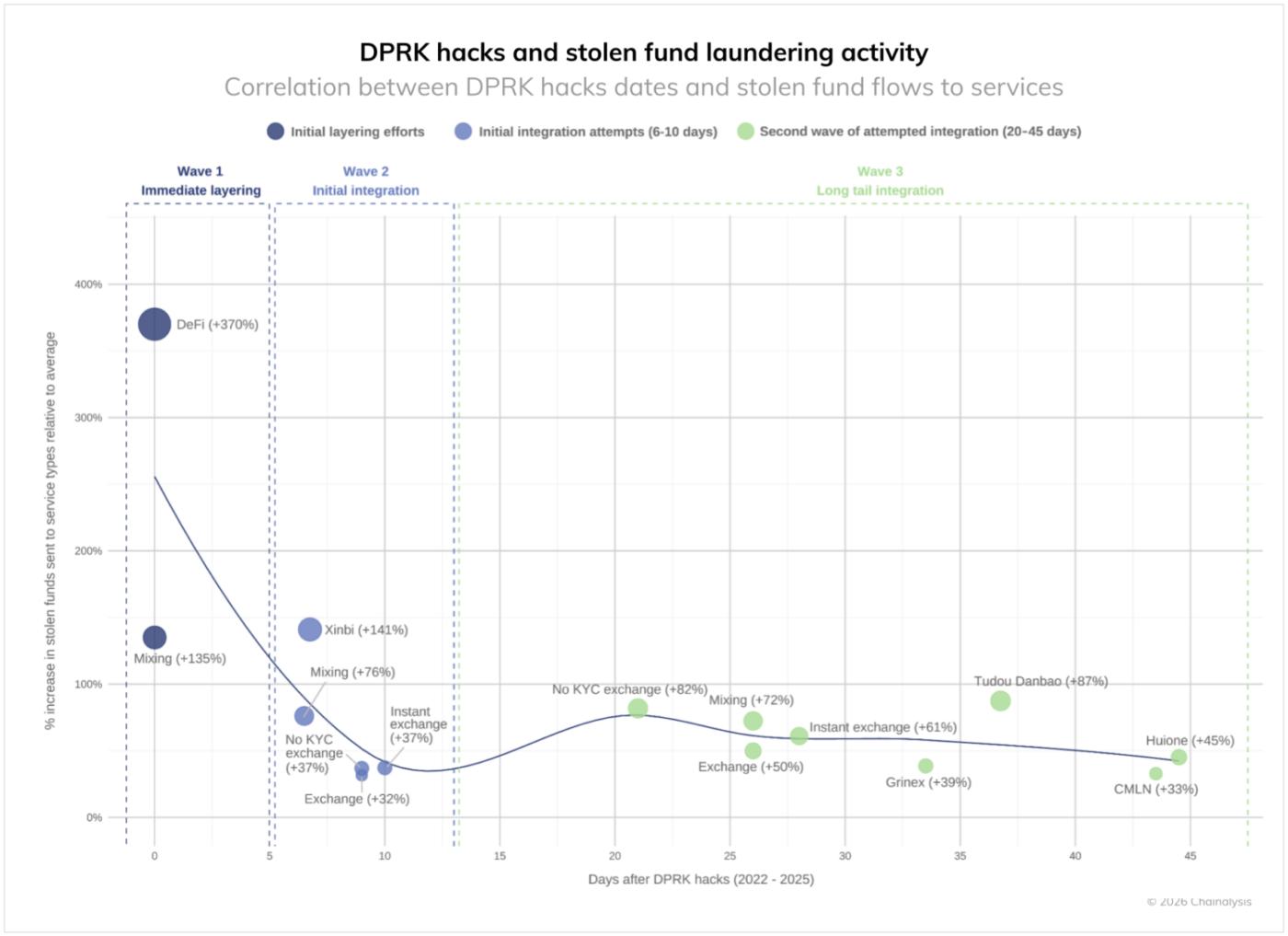
Wave 1: Immediate layering (days 0-5)
Immediately after the hack, there will be a rapid movement to distance yourself from the source of your funds:
- Decentralized finance (DeFi) protocols saw the most significant inflows (+370%).
- Mixing services also saw a significant increase (+135-150%), forming a first-time obscuration layer.
- The purpose of this phase is to separate funds through the "initial action."
Wave 2: Early Consolidation (Days 6-10)
As we enter week two, we shift to tactics to integrate funds across the ecosystem:
- Inflows to exchanges with KYC restrictions (+37%) and centralized exchanges (+32%) will begin.
- Secondary mixing services (+76%) continue to be used for money laundering, but at a reduced intensity.
- Cross-chain bridges (e.g., XMRt, +141%) decentralize and obfuscate funds.
- This phase is an important transition period towards the exit of funds.
Wave 3: Long-tail consolidation (days 20-45)
In the final phase, services that help convert to fiat or other assets are preferred:
- KYC-free exchanges (+82%) and collateral services such as Tudou Danbao (+87%) surged.
- Instant exchanges (+61%) and Chinese platforms such as Huione (+45%) will be the final point of redemption.
- Centralized exchanges (+50%) are also becoming destinations for inflows, with some seeking to mix them with legitimate funds.
- Platforms from less regulated regions such as Chinese Money Laundering Network (+33%) and Grinex (+39%) complete the pattern.
This 45-day cleaning window provides useful insight for law enforcement and compliance officers: the continuity of this pattern over multiple years suggests that North Korean-linked actors have limited access to financial infrastructure and need to work with specific collaborators.
While not all stolen funds necessarily follow this timeline, and there are cases where they are left for months or even years, this is typical of on-chain behavior during active laundering. It is also important to note that activities that do not appear on-chain, such as private key transfers and OTC legal tender transactions, can be blind spots in analysis without additional information.
Personal Wallet Compromise: A Growing Threat to Individual Users
The scale of retail wallet breaches is becoming clearer through on-chain pattern analysis and reports from victims and industry partners. While the actual number of breaches may be higher than estimates, a low-end estimate suggests that retail wallet breaches will account for 20% of all breaches in 2025, down from 44% in 2024. The number of incidents will be 158,000, nearly triple the 54,000 in 2022. The number of victims will also double, from 40,000 in 2022 to at least 80,000 in 2025. This increase is also driven by the growing adoption of cryptocurrencies. Solana, for example, is one of the blockchains with the most active retail wallets and the highest number of victims (approximately 26,500).
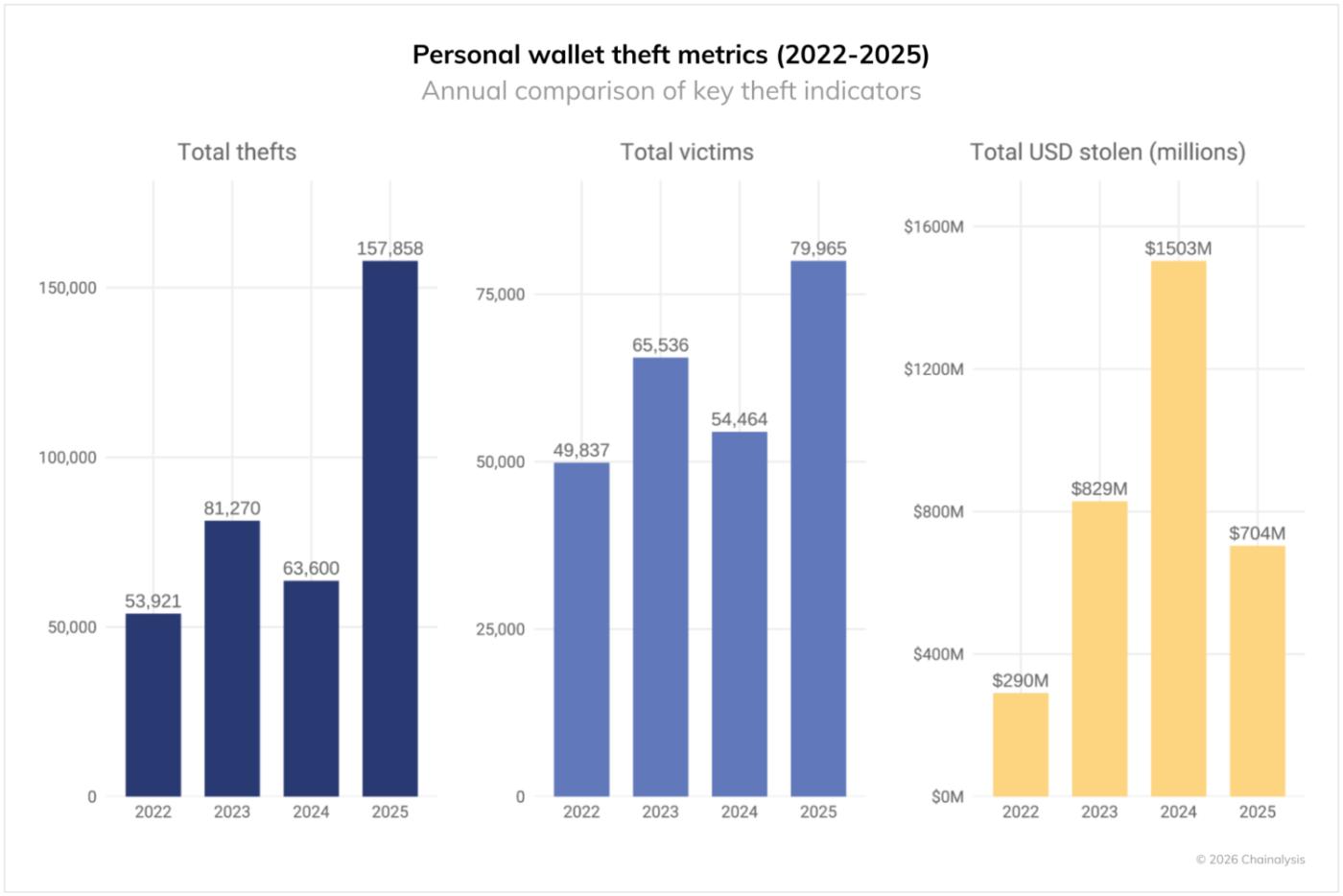
While the number of incidents and victims is increasing, the total amount of damage to individuals is expected to decrease from $1.5 billion in 2024 to $713 million in 2025. While attackers are targeting more users, the amount of damage per person is on a downward trend.
Damage data by network also reveals which areas are at high risk. The graph below shows the damage rate adjusted for the number of active individual wallets for each blockchain. In 2025, Ethereum and Tron recorded the highest theft rates. Ethereum had a high number of cases and victims, and Tron also had a high damage rate despite having a small number of active wallets. On the other hand, Base and Solana had low damage rates despite having a large number of users.
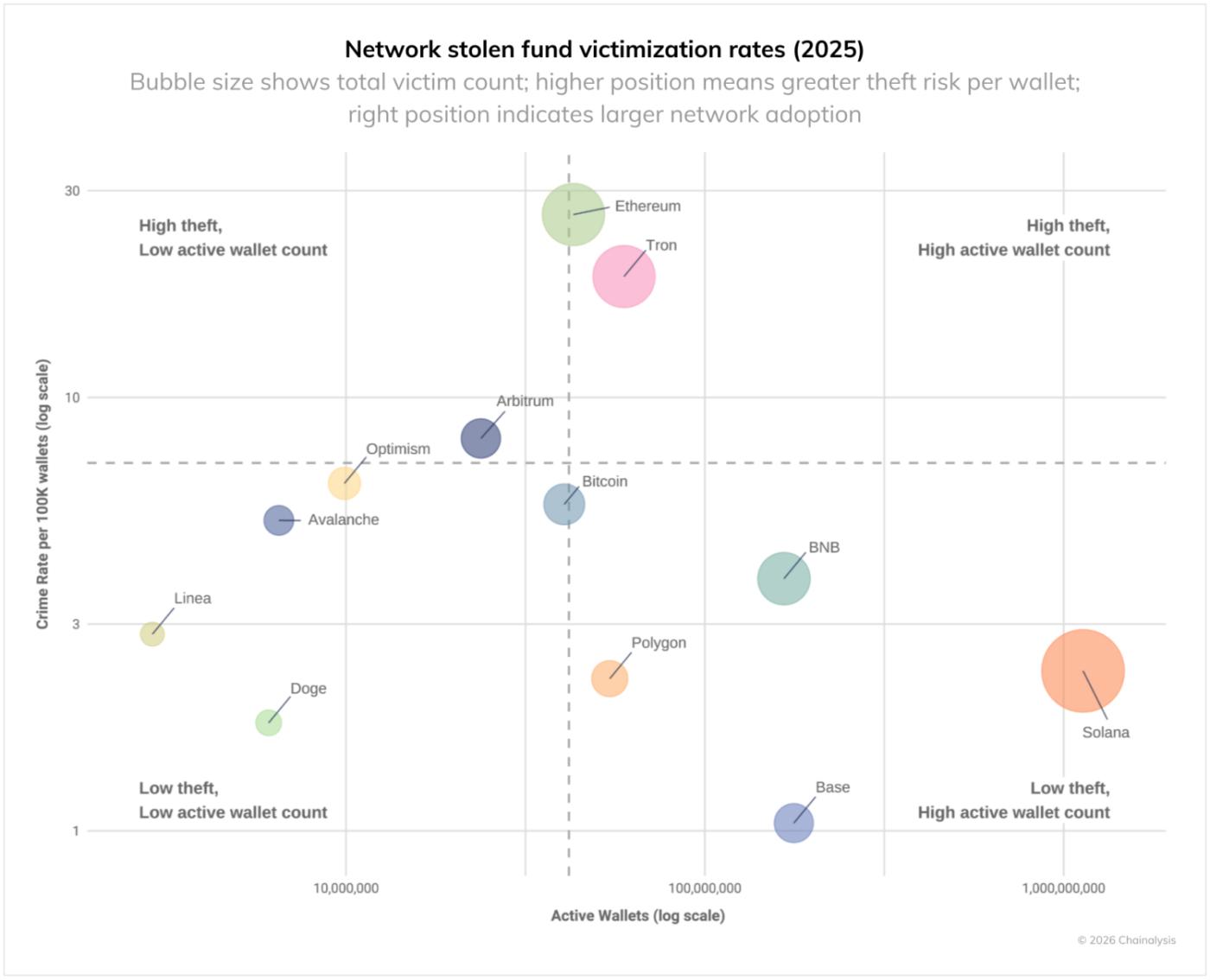
These differences demonstrate that the security risks to personal wallets are not uniform across the cryptocurrency ecosystem. The difference in victim rates between chains with similar technical infrastructure is due to factors other than technology, such as user demographics, popular apps, and criminal infrastructure.
DeFi Hacking: A Different Market Trend than Previous Years
In the decentralized finance (DeFi) space, 2025 crime data shows clear patterns that diverge from historical trends.
Three phases emerge from the data:
- Phase 1 (2020-2021): DeFi TVL (total assets held) and hacking losses increase in parallel.
- Phase 2 (2022-2023): Both indicators decrease.
- Phase 3 (2024-2025): TVL recovers, but hacking losses remain contained.
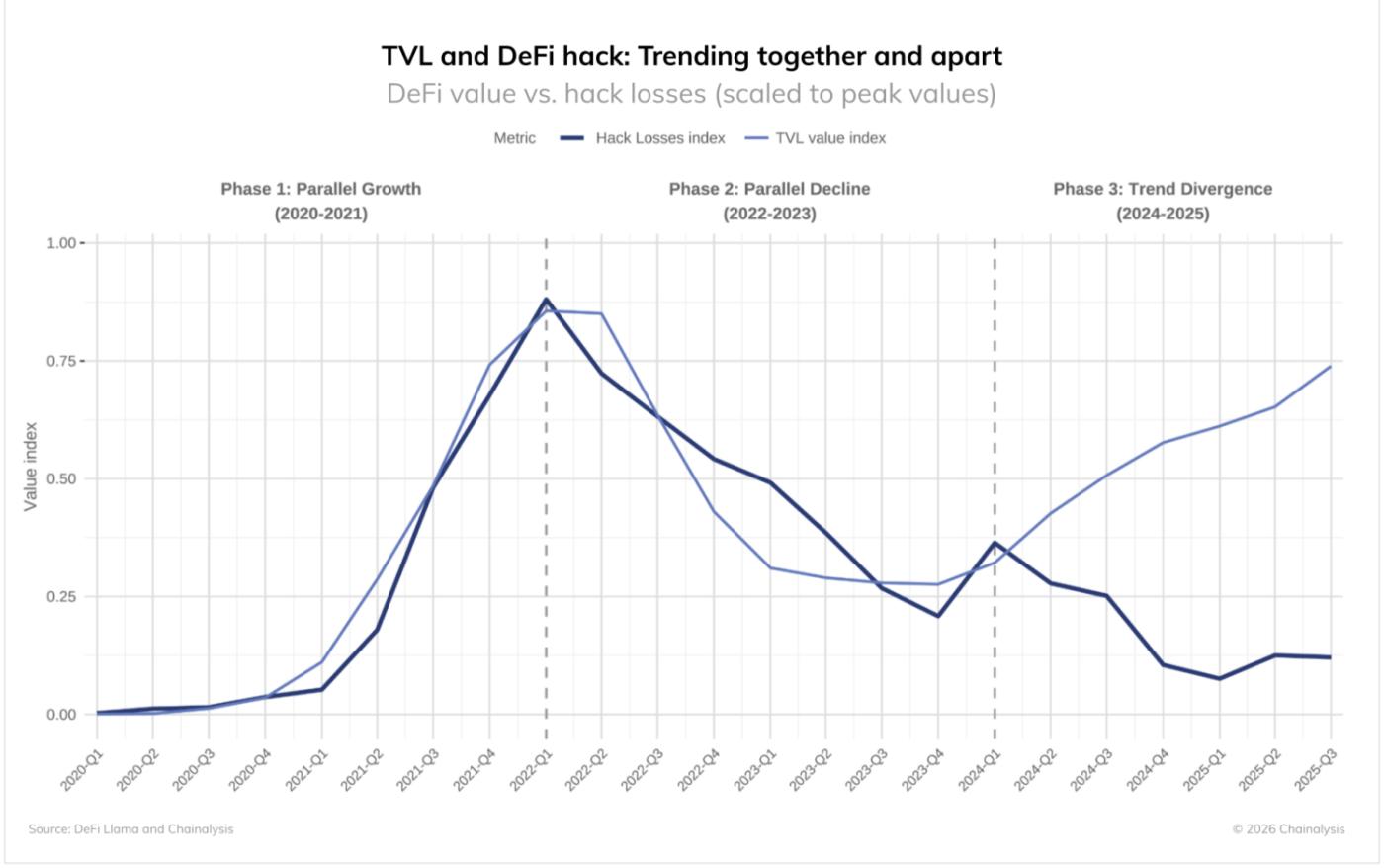
The first two phases are intuitive: the more risky assets, the more targets criminals have and the more attacks they face. However, in 2024-2025, even as TVL recovers significantly, there is no increase in hacking losses, creating an unusual divergence.
There are two possible reasons for this discrepancy:
- Evolving Security : Consistently low hacking rates despite increasing TVL likely indicate that DeFi protocols are adopting effective security measures.
- Shift in targets : With the increase in theft of personal wallets and attacks on centralized services, attackers may be shifting their attention to other areas.
Case study: Venus Protocol security measures
The Venus Protocol incident in September 2025 is emblematic of the evolution of security measures. Attackers used a compromised Zoom client to infiltrate the system and trick victims into granting delegation authority to a $13 million account. While this would normally have been fatal, Venus had deployed the Hexagate security monitoring platform a month earlier.
The platform detected suspicious activity 18 hours before the attack and immediately alerted the user when a malicious transaction occurred. Within 20 minutes, Venus had paused the protocol and prevented the funds from leaking. The response process was as follows:
- Within 5 hours: Partial functionality restored after security check
- Within 7 hours: Attacker's wallet is forcibly liquidated
- Within 12 hours: Full recovery of damages and service resumption
Notably, Venus passed a governance proposal to freeze $3 million in assets held by the attackers, resulting in losses rather than profits for the attackers.
This case shows that the DeFi field is seeing the establishment of a new security system that can minimize or reverse damage even after an attack has occurred, unlike the early DeFi era, by combining proactive monitoring, rapid response, and governance functions.
Implications for 2026 and beyond
The 2025 data paints a complex picture of North Korea's evolution as a cryptocurrency threat actor. Its ability to cause significant damage with a small number of attacks indicates increasing sophistication and persistence. In the wake of the Bybit incident, North Korea appears to be slowing down its attack pace after large-scale thefts, focusing on money laundering.
The cryptocurrency industry needs to be vigilant in detecting large-value targets and strengthen its detection of North Korean money laundering patterns. Their consistent preferences in service types and amounts sent provide opportunities for detection, helping to distinguish them from other criminals and identify their on-chain behavior.
As North Korea continues to steal crypto assets to fund national priorities and evade international sanctions, the industry must recognize that these actors play by different rules than typical cybercriminals. 2025's record losses came amid a 74% decline in known attacks, and we may only be seeing the tip of the iceberg. The challenge for 2026 will be to uncover and disrupt these high-impact operations before a Bybit-level incident occurs again.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient's use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claims attributable to errors, omissions, or other inaccuracies of any part of such material.
The postNorth Korea's cryptocurrency theft hits record high of $2 billion in one year appeared first on Chainalysis .