Author | Fourteen Jun
1. Introduction
In the blink of an eye, I've already been working in the wallet industry for four years. Many people think the wallet market is already solidified by 2025, but that's not the case—it's been quietly evolving. This past year:
Coinbase has released a new CDP wallet, built on the underlying TEE technology.
Binance 's MPC wallet introduces key sharding and hosting to the TEE environment;
Bitget just released its social login feature last week, which is hosted on a TEE platform.
OKX Wallet launches smart account functionality based on TEE;
MetaMask and Phantom introduce social login, which is essentially a key-sharded encrypted storage method.
Although no outstanding new players have emerged this year, the existing players have undergone tremendous changes in their ecosystem positioning and underlying technical architecture.
This transformation stems from drastic changes in the upstream ecosystem.
With the complete decline of the BTC and Inscription ecosystem, a large number of wallets have begun to take on the new role of "entry point" and take over emerging tracks such as Perps (perpetual contracts), RWA (stocks), and CeDeFi (a combination of centralized and decentralized finance).
This transformation has actually been brewing for many years. Follow along in this article to gain a deeper understanding of those flowers blooming in the shadows, and their impact on future users.
2. A review of the development stages of the wallet industry
Wallets are a rare essential product in the blockchain industry, and they are also the first entry-level application outside of public chains to break through ten million users.
2.1 Phase 1: The Single-Chain Era (2009–2022)
In the early days of the industry (2009–2017), wallets were extremely difficult to use, and sometimes even required running a local node. We will skip this stage.
Once it reached the usability stage, self-hosting became the preferred choice — after all, in the decentralized world, "default distrust" is the foundation of survival. Well-known products such as MetaMask, Phantom, Trust Wallet, and OKX Wallet were among the best performers during this period.
From 2017 to 2022, the market witnessed a boom in public blockchains/L2 blockchains. Although most chains still use Ethereum's EVM architecture, creating a compatible and good tool is sufficient to meet the needs.
During this period, the core positioning of wallets was "good tools." Although the industry could see the commercial prospects of traffic entry points and DEX entry points, security, ease of use, and stability were the primary requirements.
However, the situation changed between 2023 and 2025. Heterogeneous public chains such as Solana, Aptos, and BTC (during the inscription era) completely dominated the user market. Although Sui itself was developing well, after the hacking incident, large funds hesitated due to the drawbacks of excessive centralization.
Driven by the era of "fat protocols, thin applications" in financing, although VCs have only made little profit, the market landscape is indeed changing.
2.2 Phase Two: The Multi-Chain Era (2022–2024)
Faced with the multi-chain landscape, even established players like MetaMask have had to transform, incorporating built-in support for Solana, BTC, and others. Leading players such as OKX Wallet and Phantom have long since implemented multi-chain compatible architectures.
The core indicators of multi-chain compatibility are the number of chains supported and the origin of transactions—this means the backend handles a significant amount of work, while the client only handles signing. From the user's perspective, it boils down to whether they need to manually find RPC nodes to use the wallet.
Nowadays, multi-chain compatibility has almost become standard. Sticking to a single chain in the long run is easily unsustainable because blockchain trends are constantly changing.
A prime example is the Keplr wallet, which focuses on the Cosmos ecosystem, but this sector has consistently failed to take off. Many application chains quickly built on Cosmos have gradually faded into obscurity after launch. As the barrier to entry for building EVM L2 becomes lower, the situation for single-chain wallets may ease, but their potential is limited.
Once the basic tools are good enough, users begin to realize their business needs in their wallets!
True asset owners not only need to safeguard their assets but also actively drive them—finding the best places to generate returns and choosing the right partners to interact with. However, users are also plagued by the complexity of interacting with various DApps and must constantly be wary of phishing websites. Given this, why not simply use the built-in functions of a wallet?
2.3 Business Competition in the Branch Phase
The focus of competition among wallets has shifted to the business level, typically through aggregating DEXs and cross-chain bridges. Although Coinbase explored integrating social features, this demand was considered too quasi-demand and remained lukewarm.
Returning to basic needs, users require a single wallet entry point to complete multi-chain asset transfers. At this point, coverage, speed, and slippage become the core competitive advantages.
The DEX space can be further extended to derivatives trading: RWAs (such as stock tokenization), Perps (perpetual contracts), and prediction markets (which are expected to be hot in the second half of 2025, given that the World Cup will be held in 2026). Parallel to DEXs is the demand for DeFi yields.
After all, on-chain APY will be higher than that of traditional finance:
Coin-based strategy: ETH staking yields approximately 4% APY, while Solana staking + MEV yields approximately 8% APY (see our lengthy research report: The Evolution and Controversies of MEV on Solana for details). More aggressive strategies include participating in liquidity pools (LPs) and cross-chain bridge LPs (see: Super Intermediary or Business Genius? A Look at LayerZero, the Leading Cross-Chain Bridge, After V1 to V2 in the Past Year).
Stablecoin strategy: Although the returns are relatively low, combining them with cyclical leverage can increase the APY. Therefore, this year (2025), at the peak of business competition, the wallet infrastructure underwent another upgrade. The reason is that the aforementioned transactions are too complex—not only in terms of transaction structure but also in terms of the transaction lifecycle.
To achieve truly high returns, automated trading is necessary: dynamic rebalancing, timed limit orders (rather than just market orders), dollar-cost averaging, stop-loss orders, and other advanced features. However, these features were simply impossible to implement in the era of purely self-managed trading. So, should one prioritize "safety first" or "profit first"? It's not a difficult question, because the market inherently has different needs.
Just like during the Telegram bot boom, many users handed over their private keys in exchange for automated transaction opportunities—a high-risk model of "if you're afraid, don't play; if you play, don't be afraid." In contrast, large service providers must consider brand and reputation when developing wallets. So, is there a solution that can securely hold private keys while relatively guaranteeing that the service provider won't abscond? Of course! This has led to this year's upgrade in underlying custody technology.
3. Hosting underlying technology upgrade period
Returning to the initial point about the industry's underlying technological upgrades, let's analyze them one by one.
3.1 Saying Goodbye to the Era of Fully Self-Managed Services
Firstly, the moves by pure wallet vendors like Metamask and Phantom are relatively lightweight and more experience-driven, as social login only addresses user needs across devices and for account recovery, rather than fully penetrating the specific application layer. However, their shift actually marks a departure from the era of complete self-custody to some extent. Self-custody has varying degrees, but no one can truly define what constitutes complete and incomplete self-custody.
First, self-hosting inherently means that a user's private key can only be stored on the user's device. However, this has had many problems in the past. Locally encrypted private keys are vulnerable to brute-force attacks if the device is compromised, and their strength depends on the user's password. When syncing or backing up across devices, the keys always need to be copied, making the operating system's clipboard permissions a critical threshold.
What I remember most vividly is that a certain wallet vendor only pasted the first few characters of the private key copy page by default, requiring users to manually type the remaining characters. This directly caused a sharp drop of over 90% in private key theft reports during that period. Later hackers learned their lesson and began brute-forcing the remaining characters, effectively ushering in a new era of countermeasures.
Following the Ethereum Prague upgrade, the extremely high permissions of Permit 7702, its obscure signature, and even its potential for chain-wide impact have reignited the high phishing risks associated with Permit 2. Therefore, the root cause of self-custody lies in users' inability to easily adapt to an industry environment where they have complete control over their assets.
Since the private key is with the user, that's naturally fine. However, if an encrypted copy of the private key is stored on the server to prevent the complete loss of assets if the user's local device is lost, can this still be considered self-hosting? Metamask and Phantom answer that it can. But at the same time, it's also necessary to prevent the service provider from acting maliciously.
3.2 Let's start with Metamask.
His approach is simple: users log in to an email address and set a password. The two are combined to form something called TOPRF (Threshold Oblivious Pseudorandom Function), which is used to encrypt the user's private key. The encrypted private key can naturally be backed up.
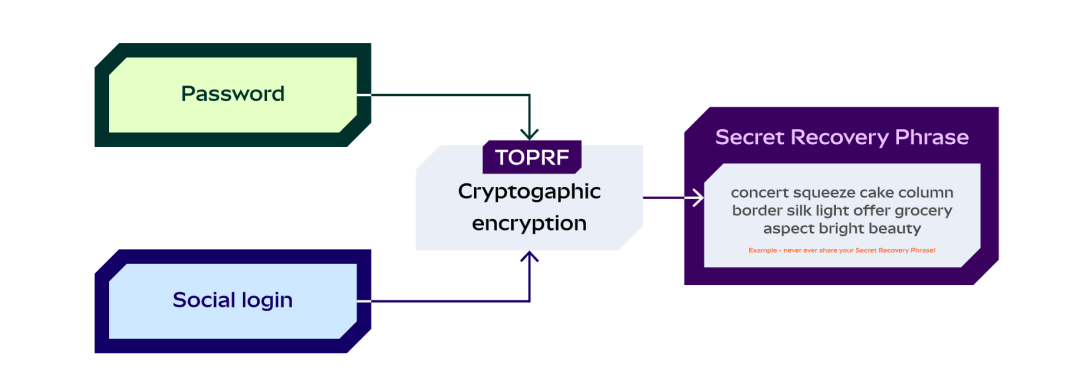
Then, this TOPRF is distributed in fragments using a typical SSS (Shamir Secret Sharing) algorithm. The social login service providers then obtain the encrypted data through social verification and require the user's password to fully decrypt it.
So security risks aren't entirely nonexistent. After all, weak passwords plus email account theft are risky, and if a user forgets their password, it can't be recovered. But the advantage is that it's more convenient, and the experience is basically the same as web2.
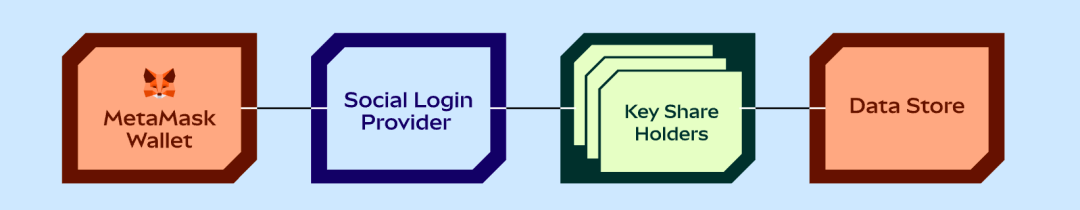
3.3 Watching Phantom
The overall architecture is a bit more complex when viewed in the diagram, but in essence, it still involves storing the encrypted private key on the backend and managing the keys used for encryption and decryption in shards.
The difference between JuiceBox and Metamask is that the encryption key is divided into two parts. JuiceBox introduces another service provider to store one of the parts, and social login and a 4-digit PIN are required to use the shards.
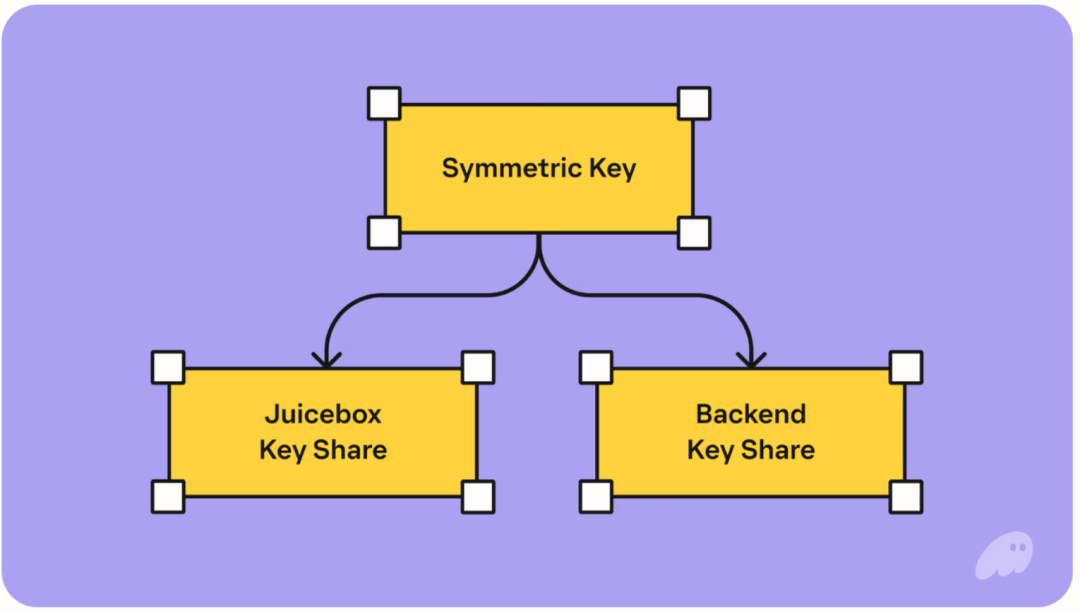
In summary, as long as users' email accounts are not stolen and their PINs are not forgotten, they can recover their accounts at any time. Of course, in extreme cases, if JuiceBox and Phantom collude, they could decrypt the assets, but at least the cost of the hacker's attack changes from a single point to multiple parties. Moreover, since JuiceBox is a network, its security design also distributes the workload among multiple verifiers.
In terms of social media recovery, both companies have made certain compromises while adhering to their bottom lines. However, sacrificing user experience for low-probability events is a positive step. After all, what the blockchain industry needs most is to embrace ordinary users, not force them to become industry experts.
4. Self-hosting of Tee using a trusted technology environment
Social logins can only solve recovery issues, but not automated trading. Therefore, each company has slightly different approaches to addressing this.
First, some background information: Tee stands for Trusted Execution Environments. Essentially, it's still a server, but this server ensures that its memory environment and operation process cannot be read or interfered with, even by the AWS service provider or the server owner. Furthermore, once it starts running, it publishes a file called Attestation. The party interacting with Tee can verify whether this document is consistent with its open-source publication.
Only when the program he runs conforms to the specified open-source version will the two correspond, thus proving trustworthiness. This has already been widely applied in the industry: for example, Avalanche's official cross-chain bridge uses SGX (a certain Tee model) to run the notary validator; for example, on the Ethereum mainnet, 40% of the blockchains are completed through Builder Net, which is also based on TEE, to complete transactions and block production; not to mention various financial banks, which strictly control and prevent insider risks, have also basically introduced Tee. Under the background of compliance in 2025, leading exchanges have also introduced Tee at high prices for cold and hot wallet signature custody.
While using Tee presents several challenges, such as lower machine performance (which can be mitigated with money), the risk of downtime (loss of memory information), and complex upgrades, the remaining question is: how do various exchange providers offer Tee services within their wallets?
4.1 Coinbase and Bitget's solutions
It's hard to imagine at first that a US-listed, compliant exchange like Coinbase actually uses the most centralized version. And Bitget is almost identical in its logical architecture.
In essence, he only uses Tee as a service to generate private keys and drive signatures, but how can Tee verify whether this service is truly the user's intention? Coinbase relies entirely on the user logging in, with backend authentication to forward instructions to Tee, and then complete the transaction.
Bitget is similar. Although information is scarce, it appears there's no on-screen signature page; it simply assigns an EIP-7702 address to the new address, thus enabling gas payment on behalf of the user. The advantage of this approach is that it at least provides the user's private key, which is indeed in the TE (Tepe). However, whether the backend might insert other strange instructions is neither verifiable nor falsifiable.
Fortunately, there is evidence on the blockchain. Therefore, I believe that Coinbase and similar exchanges have essentially enhanced the credibility of exchanges. After all, whether private keys are exported is definitely recorded, which can eliminate the possibility of users committing fraud or other malicious acts. The only risk is that the exchange itself acts maliciously, which is actually consistent with the underlying model of users trusting centralized exchanges.
4.2 Bn and Okx
Comparing the MPC and SA of these two companies, the underlying logic is essentially the same. Regarding driving transactions, OKEx displays an intent authorization signature page. Combined with the intent verification logic within the Tee, this allows for a higher level of user authorization, but also increases the overall user understanding cost.
Binance's MPC is largely due to its existing technical architecture (MPC actually has limitations in multi-chain expansion). After the introduction of Tee, users need to encrypt and transmit a fragment from their local device to Tee. OKX, on the other hand, encrypts and transmits the user's local seed phrase to Tee.
As a user, you don't need to worry too much about security risks. The reliable communication between Tee and the client is currently very mature, theoretically completely eliminating man-in-the-middle attacks. After all, as long as asymmetric encryption is performed using Tee's public key, only the private key can decrypt it. There are some minor differences in user experience, such as MPC, how the private key is passed into Tee, and how to renew it after expiration. These are engineering issues and won't be discussed further.
Analyzing the design motivation, the main benefit of this design lies in reducing migration costs and avoiding the cold start problem of users having to migrate assets to experience new advanced features. For example, CB's system focuses on the payment sector, allowing traditional e-commerce service providers without local private key management experience to complete on-chain operations by calling private keys through APIs. Binance's system, on the other hand, is used in conjunction with other systems to target the CedeFi sector, making it easier for users who usually view stock charts to directly purchase on-chain assets through similar interfaces, while ignoring issues such as gas fees, slippage, and multi-chain compatibility.
5. Summary
How should we evaluate 25 years, and how should we view the future? In my opinion, this year was a year of silence for wallets, but also a year of transformation. They didn't make a big splash, but they were quietly working on significant things. In today's multi-chain environment, simply creating a user-friendly tool is no longer enough to support a large wallet team (and its supporting infrastructure). It inevitably needs various value-added services to sustain itself, and this year also happened to be a year of explosive growth for applications. The perps sector was reborn, and RWA (equity-related), prediction markets, and payments all saw simultaneous improvement.
The market is gradually shifting from memes to meet diverse DEX demands. Furthermore, the apparent size of the meme market is only due to its high transaction speed and turnover; in reality, it's largely the same group of people playing the game. While trends change, user growth is minimal. This is compounded by various tee-based new custody systems from different exchanges, each staking their reputation on them.
Moreover, in the broader trend, AI will become increasingly powerful, including AI trading. Previously, wallets were designed for humans, not AI. Therefore, I foresee a richer explosion in applications next year, as the underlying technology matures further. There will definitely be a gap period, because the Tee platform is still largely operated by large exchanges, and they are unlikely to easily open up external access like Coinbase has.
Furthermore, while some users are using their funds to invest in DEXs, a much larger group simply wants to earn a stable income. They are quite satisfied with the subsidies and airdrops offered during promotional periods, coupled with a certain APY. CedeFi products, which allow users to earn on-chain yields, will be the first avenue for many CeEX users to access the blockchain (note that this mainly refers to CedeFi products with independent addresses; shared addresses like Bitget are not eligible).
Finally, there have actually been many improvements in cryptographic technology for passkeys this year, although these haven't been covered in this article. However, more and more public chains like Ethereum and Solana are gradually integrating the R1 curve (which is supported by default for device passkeys) through pre-compiled contracts. Therefore, wallets combining passkeys are a potential development (although their retrieval and cross-device synchronization are not easy to handle), so there aren't many good applications yet. After all, any product that can streamline high-frequency needs will eventually find its place.








