 Hacken said Web3 losses are projected to reach nearly $4 billion by 2025, with North Korea accounting for more than half of the losses, and regulators are under pressure to turn security guidelines into mandatory regulations.
Hacken said Web3 losses are projected to reach nearly $4 billion by 2025, with North Korea accounting for more than half of the losses, and regulators are under pressure to turn security guidelines into mandatory regulations.
Hacken's 2025 Annual Security Report estimates total Web3 losses at approximately $3.95 billion, an increase of about $1.1 billion from 2024, with just over half attributed to threats from North Korea.
A report Chia with Cointelegraph showed losses peaked at over $2 billion in the first quarter of the year before falling to around $350 million in the fourth quarter, but Hacken cautioned that this pattern still points to systemic operational risk rather than isolated coding errors.
The report sees 2025 as a year where the numbers get worse, but the underlying story becomes clear. Smart contract flaws are significant, but the biggest and most difficult-to-recover losses still come from weak keys, compromised signers, and sloppy off-boarding processes.
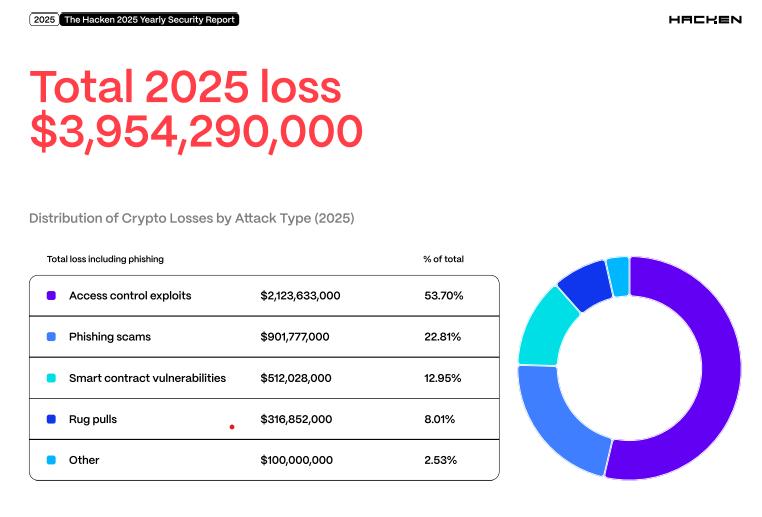
Access control, not the code, is the factor causing the loss.
According to Hacken, access control failures and broader operational security breaches account for approximately $2.12 billion, or nearly 54% of total losses in 2025, compared to about $512 million from smart contract vulnerabilities.
Cryptocurrency losses by type of attack. Source: Hacken Security Report 2025
The Bybit hack alone, worth nearly $1.5 billion, is described as the single largest theft ever recorded and is the main reason why clusters linked to North Korea account for approximately 52% of all stolen funds.
The regulatory agency stated that control measures were in place, but the industry remained slow to implement them.
Yehor Rudystia, head of forensics at Hacken Extractor, told Cointelegraph that regulatory licensing regimes across the US, the European Union, and other major jurisdictions increasingly specify on paper what constitutes “good,” such as Vai based access control, logging, secure reception and identity verification processes, organizational-level custody (hardware-based security models, Multi-Party Computation or Multisignature, and cold storage), as well as continuous monitoring and anomaly detection.
However, “while legal requirements are only just becoming mandatory guidelines, many Web3 companies will continue to pursue insecure practices throughout 2025,” Rudystia said.
He pointed out practices such as not revoking developer access during off-boarding, using a single private key to manage a protocol, and the lack of Endpoint Detection and Response systems.
“Among the most important are regular penetration testing, incident simulations, custodial control reviews, and independent financial and control audits,” Rudystia said, adding that major exchanges and custodians should consider these requirements non-negotiable by 2026.
From soft guidelines to hard requirements
Hacken expects standards to be raised even further as regulatory bodies move from guidance to mandatory requirements.
Yevheniia Broshevan, co-founder and CEO of Hacken, told Cointelegraph: “We see a significant opportunity for the industry to raise its security baseline, particularly in adopting clear processes for the use of dedicated signing hardware and deploying essential monitoring tools.”
He said he expects overall security to improve by 2026, with legal requirements and “the highest safety standards” being imposed to protect users’ money.
Given that clusters linked to North Korea account for approximately half of the total losses in Hacken's allocation, Rudystia argues that regulatory and law enforcement agencies should also consider the country's operational methods as a specific monitoring concern.
He argued that authorities should mandate real-time Chia of threat intelligence on indicators related to North Korea, require specialized risk assessments focused on phishing-driven access attacks, and combine that with “increasing penalties for non-compliance” and safe-harbor protections for platforms that fully participate and maintain specialized defenses against North Korea.







