It's too late to mend the fence after the sheep are lost.
Article by Eric
Article source: Foresight News
"Hacking" is a staple of the Web3 industry, and it gets more exciting every year.
According to the "2025 Skynet Hack3D Web3 Security Report" released by security company CertiK at the end of December 2025, there were 630 security incidents in the Web3 industry in 2025, resulting in a total loss of approximately $3.353 billion, with the amount of stolen funds increasing by 37.06% year-on-year.
US$3.353 billion, equivalent to approximately RMB 23.37 billion, is roughly the GDP of Liyang City, Jiangsu Province in 2024. This figure, enough to wipe out a year's worth of hard work for everyone in a county, is truly alarming.
Over the past year, everyone has felt that the Web3 industry is gradually maturing, but it's clear that our investment in security is far from sufficient. The fact that the amount of money stolen has been increasing year by year serves as another wake-up call for this decentralized industry.
"Fishing" has become a major target of attacks.
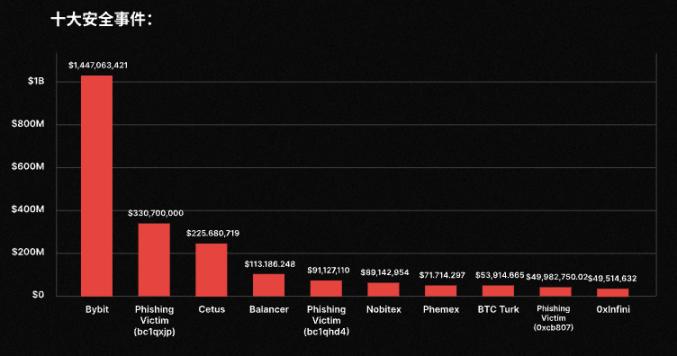
Although the total losses in 2025 increased by more than 30% compared to 2024, the Bybit incident alone resulted in losses of approximately $1.4 billion. Compared to 2024, the number of hacking incidents decreased by 137 in 2025, and the median loss decreased by 35.75% to $104,000.
Regarding these changes in detailed data, CertiK stated in its report that while the frequency of small-scale attacks will remain high in 2025, attackers are gradually concentrating their resources on fewer but more impactful high-value attacks. The Bybit incident is a prime example, demonstrating the escalating activity of well-organized hacking groups in the Web3 space.
The Bybit incident was later proven to be the work of the notorious North Korean "state-owned hacking group" Lazarus Group. Compared to its earlier attacks targeting vulnerabilities in protocol code logic, Lazarus's style in recent years has shifted to sophisticated supply chain attacks. Lazarus members impersonate hackers within their organization to apply for development positions at various Web3 companies, using their positions to learn about the companies' fund transfer processes, and then launching sophisticated attacks from within after discovering vulnerabilities.
In the Bybit incident, hackers compromised Safe developer devices and implanted malicious code in the wallet management interface to tamper with multi-signature transactions approved by Bybit employees, changing the destination of funds to their own accounts. Such organized and premeditated attacks are difficult to prevent; any small oversight can be exploited by hackers.
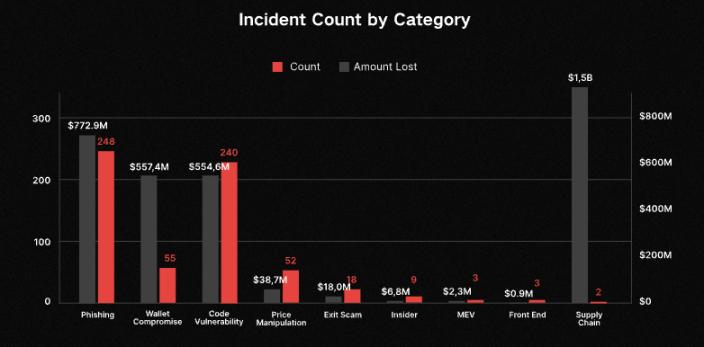
Excluding Bybit as an exception, phishing attacks were the most prevalent and costly attack method in 2025, with 248 incidents resulting in approximately $773 million in losses. Wallet theft ranked second in terms of financial loss, with 55 incidents causing approximately $557 million in losses. From my perspective, many of my friends experienced theft of funds and the unexplained transfer of all their assets from their wallets in 2025 due to accidentally clicking on links. Therefore, the actual losses caused by these two attack methods likely exceed the report's statistics, and similar attacks may become increasingly pervasive in the future.
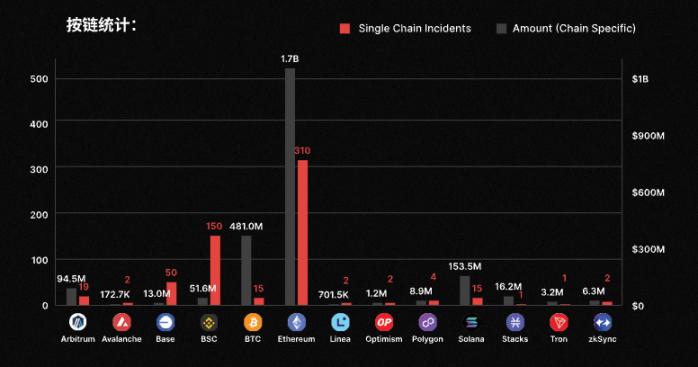
Ethereum saw the largest amount of stolen funds due to Bybit; however, excluding the $1.4 billion stolen, Bitcoin became the blockchain with the highest amount of stolen funds. Bitcoin, which does not support smart contracts, saw its wallets emptied primarily due to private key leaks, phishing attacks, and other reasons.
Regarding the attack methods mentioned earlier, we can only analyze the causes in hindsight, reminding ourselves to be more vigilant while praying that hackers won't target us. However, there is one type of "attack" that can be prevented in advance: the "Exit Scam" that caused $18 million in damages, mentioned earlier. This type of attack isn't actually a proactive attack; in most cases, the token issuer has reserved permissions to manipulate token parameters, deceiving unsuspecting investors.
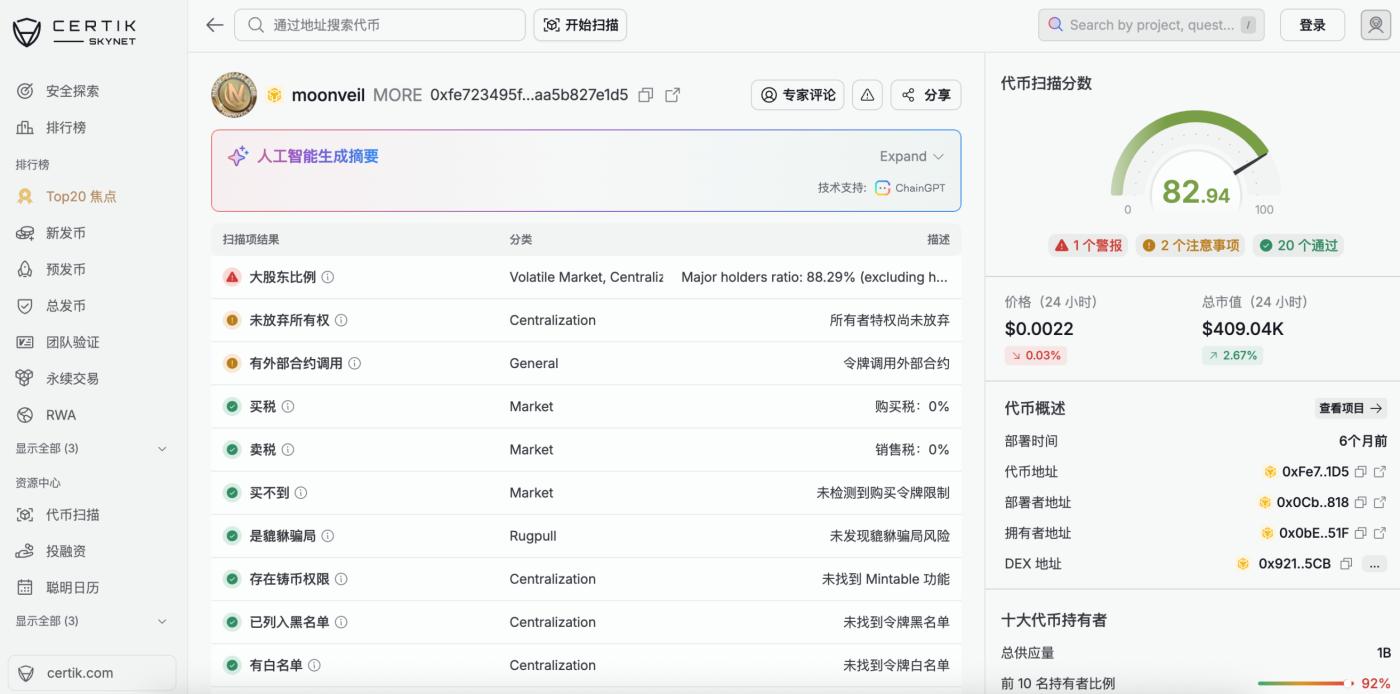
CertiK's Skynet can help with attacks like Exit Scams by assessing the overall security of Web3 projects across six dimensions: code security, project structure, operational resilience, governance, market dynamics, and community reputation. Checking with Skynet before investing can effectively filter out many risks. Furthermore, users can use token scanning tools to understand basic information such as the percentage of token holders, whether they have the authority to adjust token parameters, whether there are transaction taxes, and whether it's a Crypto honeypot. In addition, CertiK's Skynet series reports and Skynet Top 20 list provide authoritative security assessment references through data-driven security analysis and transparent quantitative evaluation standards, helping to identify foreseeable risks.
From post-event tracking to pre-event prevention
On the evening of January 6th, Beijing time, CertiK announced a strategic partnership with YZi Labs. Under the agreement, CertiK will allocate $1 million in dedicated security audit funding for its EASY Residency program and provide security services such as formal verification, Skynet Boosting, and AI scanning. YZi Labs will assist in facilitating connections between CertiK and its incubated projects, helping project teams gain a deeper understanding of CertiK's products and services.
CertiK stated that as countries and regions such as the United States and the European Union continue to improve their Web3-related laws and regulations, the supervision of projects will inevitably become increasingly stringent. In the future, projects may no longer be able to remain unaffected by security incidents, which places higher demands on the introduction of security checks and mechanisms from the early stages of project development. The security fund established by CertiK in partnership with YZi Labs is essentially aimed at strengthening proactive security measures for Web3 projects.
CertiK hopes that this collaboration will set a benchmark for the industry, encouraging more projects to prioritize safety from the outset, thereby boosting overall confidence and reputation within the industry.
CertiK stated that over the past year, the company has accumulated significant experience in proactive risk prevention, including identifying high-risk vulnerabilities in a well-known meme platform and hardware wallet products. Furthermore, after the disclosure of the React2Shell (CVE-2025-55182) remote code execution vulnerability, the CertiK team immediately assessed its exploitability and assisted over 40 React/Next.js projects in completing rapid fixes. In addition to risk identification, CertiK has also launched Skylens, a product that helps projects monitor suspicious transactions, issuing alerts immediately when risks occur to minimize potential losses.
But these achievements raise a sobering question: why are the losses caused by hackers still increasing year by year?
The answer to this question is largely related to the "Web3" and "security" industries. Unlike the internet industry, where there are deep battles against hackers, due to the decentralized nature of blockchain, once a hacker identifies a vulnerability, they will almost always succeed in the attack, with very little chance of recovering losses. Web3 projects also generally lack the capacity to implement 24/7 monitoring, and in the absence of regulatory oversight, they lack sufficient motivation to invest time and resources in security. This makes the possibility of risk exposure extremely high when the code is open source.
When security agencies compile statistics, they only show us the amount stolen, while the "potential losses recovered due to security measures" are an unquantifiable figure. This means that, thanks to the efforts of multiple security companies in the industry, the annual growth rate of recovered assets may far exceed the growth rate of losses. Furthermore, projects benefiting from security companies don't actively publicize the fact that they have vulnerabilities, so our perception of the actual impact of security companies isn't as strongly influenced by concrete figures like the amount stolen.
Regarding the subjective reasons, CertiK stated that organized and premeditated crimes like those of the Lazarus Group, which involve state investment, are difficult to prevent in advance. Taking the Bybit incident as an example, Bybit's security procedures for transferring funds were not flawed, but the act of implanting malicious code by hacking into the security vendor's developer's device to achieve the attack's purpose was something that security companies could not predict in advance.
To give an imperfect example, you can use a high-security door to keep thieves away, but you can't stop a thief from simply breaking the door down.
The double-edged sword of technological development
Security companies and hackers are always in a dynamic game of cat and mouse, with each side constantly outmaneuvering the other. Every time a hacker uses a new method to launch an attack, it provides security companies with a new defense template, which in turn prompts hackers to research new attack methods, creating a vicious cycle.
The development of AI has also brought more uncertainty to security. CertiK, a security company, has widely applied AI in its vulnerability discovery and auditing processes. By analyzing on-chain alert data, it helps identify the causes of vulnerabilities and attack paths; simultaneously, it uses AI technology to scan known vulnerability patterns, analyze code logic, and generate reports, significantly improving efficiency. Skynet, mentioned earlier, also has tools that use AI to provide overall analysis conclusions.
During the 2026 World Economic Forum (WEF) Annual Meeting, Professor Ronghui Gu, founder of CertiK, gave an exclusive interview to CBS in Davos. He stated that CertiK has achieved a deep integration of AI technology and formal verification. Based on its self-developed Spoq engine architecture, CertiK significantly improves the scalability and execution efficiency of the formal verification process by integrating AI automation capabilities. This AI-powered security solution provides institutional clients with high-standard mathematical-level security.
On the other hand, a large number of phishing attacks and address poisoning attacks using fake addresses with identical beginnings and endings can now be mass-produced using AI, increasing hackers' attack efficiency. What used to require selective targeting now only needs to fool one out of ten thousand people to be profitable for a hacker. This is one reason why, by 2025, attacks will no longer be limited to whale, unregistered internet users).
According to data from authoritative research firm Gartner, global end-user spending on cybersecurity was approximately $193 billion (about RMB 1.4 trillion) in 2024, while internet giants invest between $1 billion and $5 billion annually in cybersecurity. In the Web3 industry, which has even higher security requirements, such security investments are a drop in the ocean compared to those of internet giants.
A lack of awareness, talent, funding, and resources are hindering the development of security capabilities in the Web3 industry. The fact that most security companies primarily focus on B2B business also highlights the imbalance between supply and demand. How to find a reasonable profit model for B2C security tools, and whether insurance can cover the Web3 industry, are questions that require joint exploration by all participants, including security companies.







