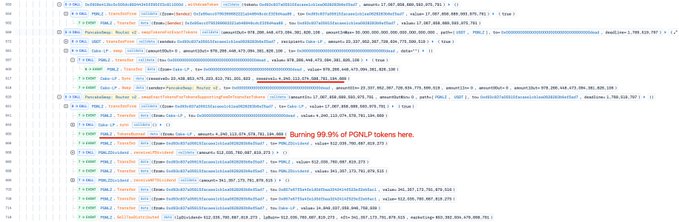
ALERT! Our system just detected a suspicious transaction targeting an unknown contract on #BSC, resulting in ~$100K in losses. The root cause appears to be a "burn pair" design flaw. Exploitation via two reverse swaps: 1. Swap 1: drained 99.56% PGNLZ tokens from the pool, leaving roughly the amount later sold. 2. Swap 2: sold PGNLZ; transferFrom triggered burns (99.9% PGNLP) + sync, pumping PGNLP price, then used the manipulated position to drain almost all USDT from the pool. 🟦 Found by #PhalconSecurity, 🟦 Analyzed via #PhalconExplorer.
Sector:
From Twitter
Disclaimer: The content above is only the author's opinion which does not represent any position of Followin, and is not intended as, and shall not be understood or construed as, investment advice from Followin.
Like
Add to Favorites
Comments
Share
Relevant content







