Author: Tom Honzik
Source: https://www.unchained.com/blog/collaborative-multisig-quorum-options
Unchained has led the quorum Bitcoin custody service industry for nearly a decade. Our products are specifically designed based on the 2-of-3 quorum, representing the simplest multi-signature wallet structure for holding Bitcoin without worrying about single points of failure. We believe the 2-of-3 quorum is the best choice for most people in most scenarios, while larger quorum requirements introduce unnecessary complexity.
In our article introducing multi-signature wallets , we created a pyramid diagram to illustrate the concept of presence requirements. We pointed out that 2-of-3 presence requirements are generally ideal, while 1-of-N and N-of-N presence requirements fail to eliminate single points of failure; meanwhile, presence requirements exceeding 2-of-3 may be useful for individuals and businesses with specific or sophisticated needs.
Now that Unchaied supports a wider range of multi-signature presence requirements, it's worthwhile to analyze the strengths and weaknesses of the various options in greater depth. This article will delve into the trade-offs of these options, allowing you to make informed choices about your Bitcoin custody security model. We'll start by introducing a few concepts, such as: types of presence requirements, key categories, discretionary access, and proxy insurance.
Presence Requirement Types within the Multi-Signature Pyramid
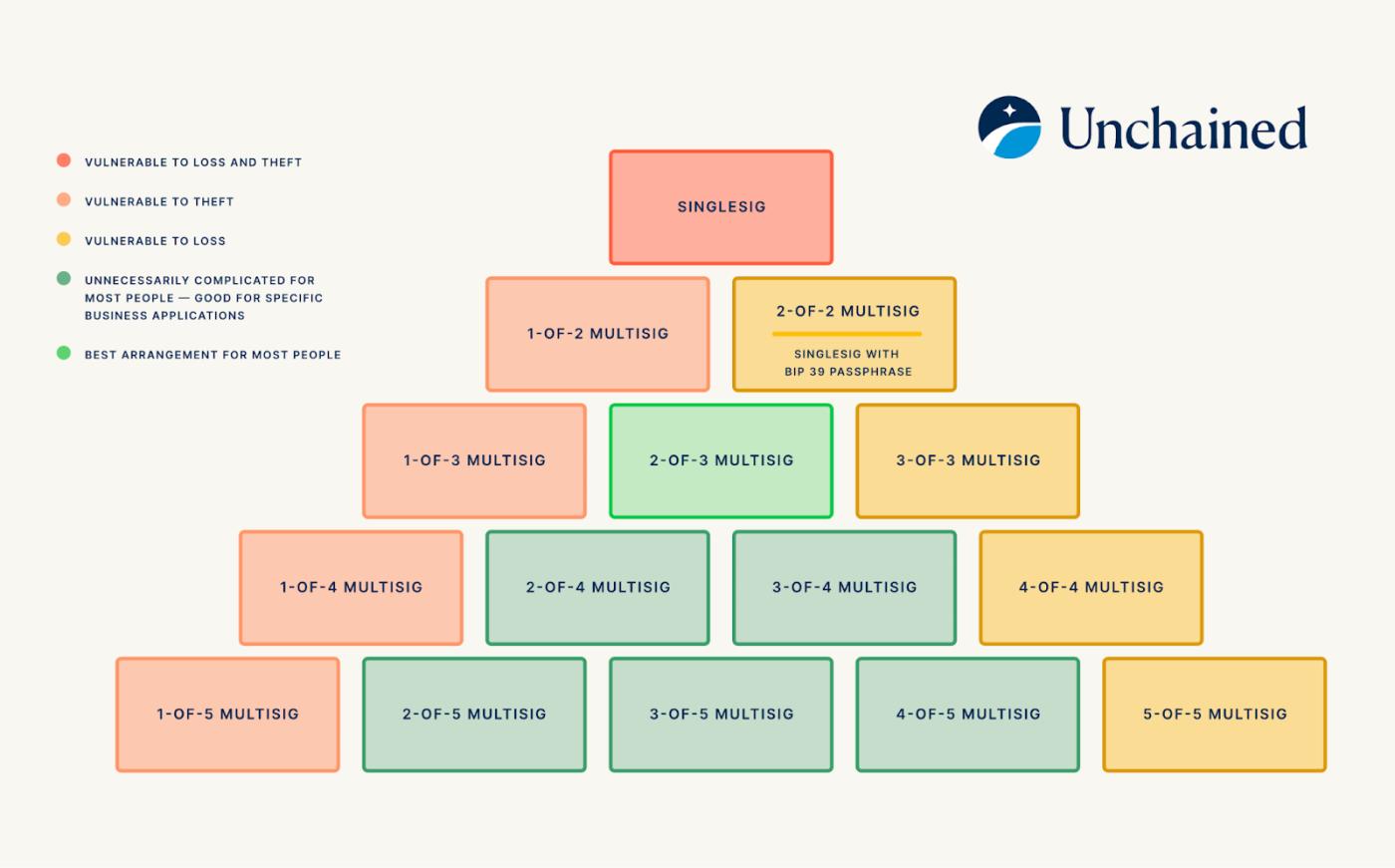
In our analysis of multi-signature presence requirements exceeding 2-of-3, we found that dividing the presence requirements on the pyramid into three types facilitates understanding: median , less than median , and greater than median . Presence requirements within each category share commonalities.
Median Presence Requirement
The median presence requirement is found along the midline of the multi-signature pyramid, including 2-of-3, 3-of-5, 4-of-7, and so on. There is a formula to determine whether a K-of-N presence requirement is a median presence requirement: 2K - 1 = N.
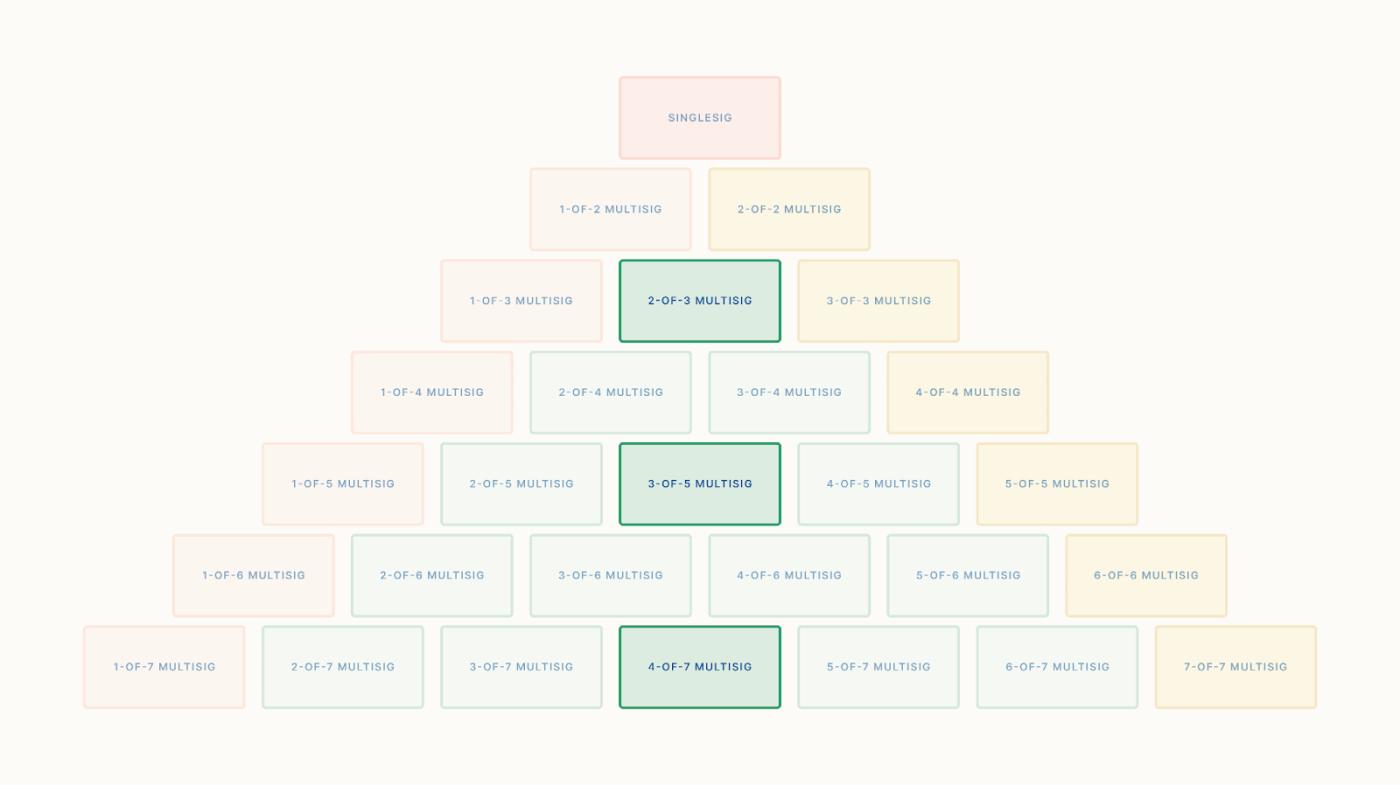
The median presence requirement is perhaps the most popular, likely because it equally addresses the two main threats to your Bitcoin: loss and theft. If a presence requirement is "too left-leaning," such as 1-of-N, it offers relatively little protection against theft; a thief might only need to find one item to access your funds. If a presence requirement is "too right-leaning," such as N-of-N, it offers relatively little protection against loss, as it means that if even one private key is corrupted or forgotten, you lose access to your funds. Therefore, the median presence requirement provides equal protection against these concerns.
Presence requirement less than median
Early-day requirements less than the median are found on the left half of the pyramid, including 2-of-4, 2-of-5, 2-of-6, 3-of-6, and so on. The formula for determining it is: 2K - 1 < N. Note that in this analysis, we discard the 1-of-N requirement because it cannot eliminate single points of failure.
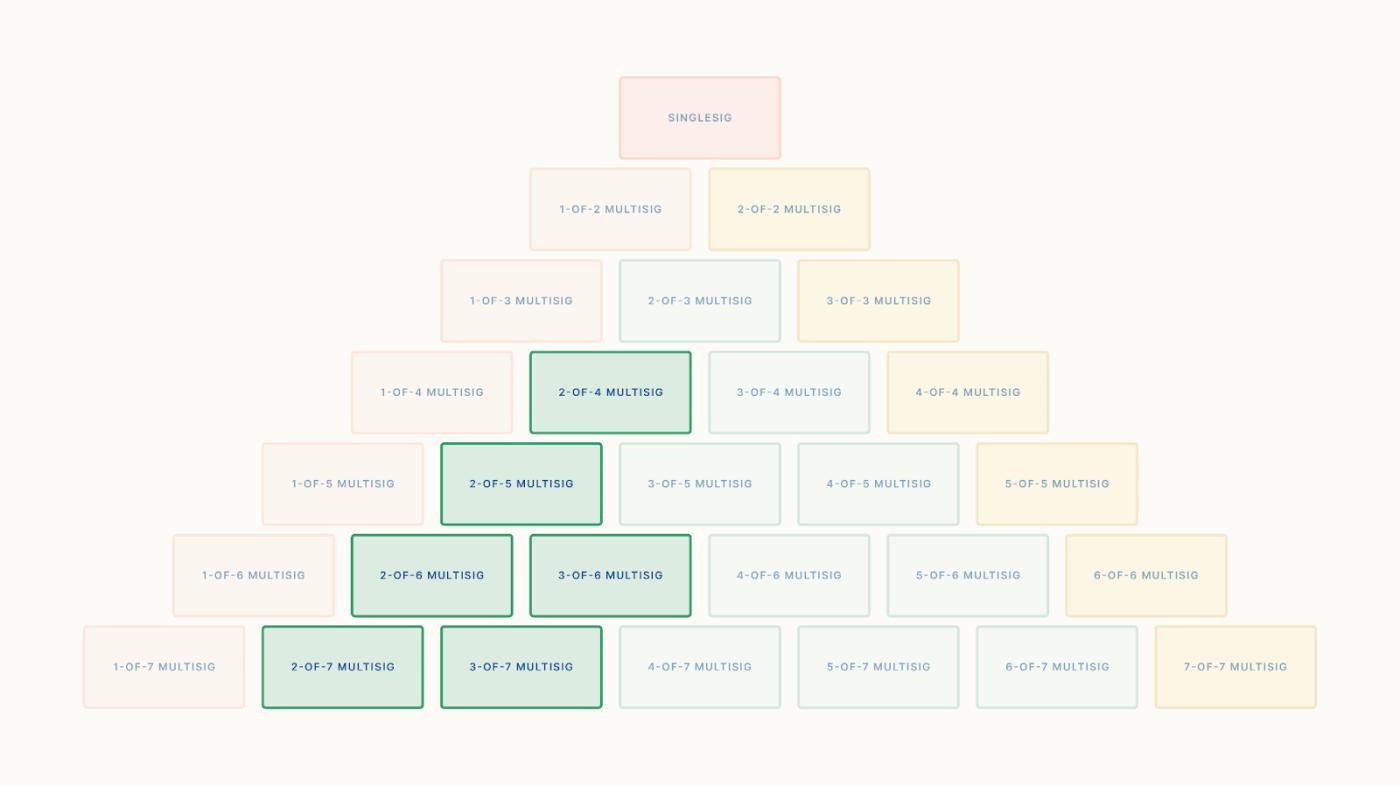
Compared to the median requirement, the presence requirement below the median places a greater emphasis on protection—more protection against lost private keys, but slightly less protection against unauthorized access (i.e., theft). This is not surprising, because if the total number of keys remains the same, a smaller percentage of keys are sufficient to take Bitcoin, making those Bitcoins easier to access.
The presence requirement is greater than the median value.
Early-field requirements greater than the median are found on the right half of the pyramid, including 3-of-4, 4-of-5, 4-of-6, 5-of-6, and so on. The formula for determining this is: 2K - 1 > N. Similarly, in this analysis, we discard the N-of-N presence requirement because it cannot eliminate single points of failure.
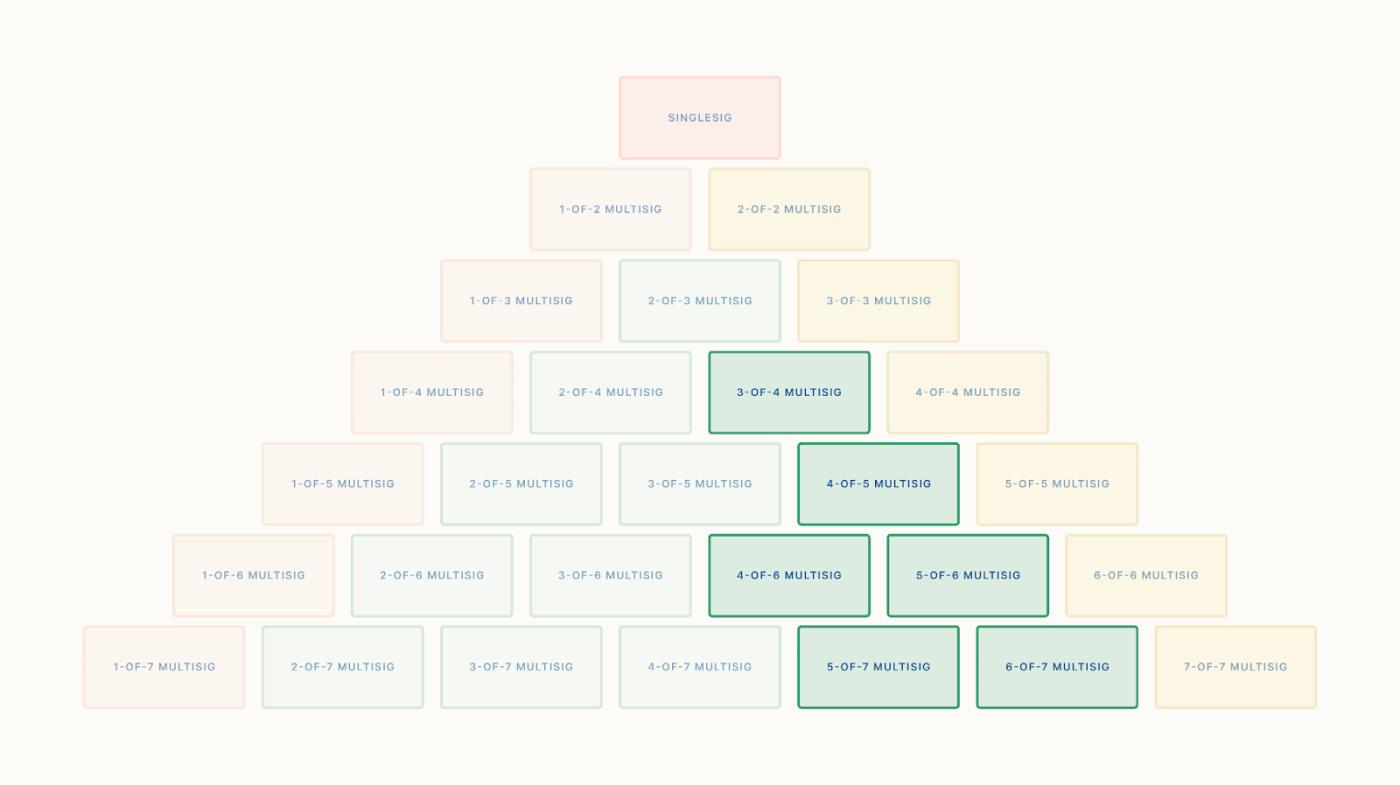
Presence requirements greater than the median are the opposite of early morning requirements less than the median. They offer more protection against theft but relatively less protection against loss. Access is naturally more difficult because a larger proportion of the keys are needed to retrieve Bitcoin.
Key classification: self-management and agent management
Another important element of this analysis is that the keys used in a multi-signature device can also be divided into two main types. Self-managed keys are keys held by yourself; or, in the case of the Bitcoin treasury, keys held by a member of your collective organization. Delegated keys , on the other hand, are held by a key agent —who is not one of the owners of the Bitcoins, but rather someone hired by the owners to safeguard and operate a key within the multi-signature device. This distinction is important because it means that drastically different custody structures can be formed within any given multi-signature presence requirement.
To illustrate, imagine a 2-of-3 presence-required multi-signature custodian that may have four different key type arrangements . Each arrangement produces a unique set of key combinations that authorize withdrawals, which we call " access patterns ":
| Key arrangement (3 keys in total) | Access mode (requires 2 keys) |
|---|---|
| Number of self-managed keys: 3 Number of keys managed by the agent: 0 | 2 self-managed keys |
| Number of self-managed keys: 2 Number of keys managed by the agent: 1 | Two self-managed keys; one self-managed key and one key managed by an agent. |
| Number of self-managed keys: 1 Number of keys managed by the agent: 2 | Two keys managed by agents; one self-managed key and one key managed by an agent. |
| Number of self-managed keys: 0 Number of keys managed by the agent: 3 | Keys managed by 2 agents |
As can be seen from the table above, some arrangements offer more access modes than others, which may be more attractive to those seeking options because they must be physically present when retrieving Bitcoin from cold storage (in these arrangements).
Notation for key arrangement and access mode
In this article, we will use an abbreviation system to more accurately represent key arrangements and access patterns. An arrangement of "2 self-managed keys and 1 agent-managed key" will be abbreviated as "2S/1A" (using a forward slash). An access pattern of "1 self-managed key + 1 agent-managed key" will be abbreviated as "1S + 1A" (using a plus sign).
Furthermore, sometimes, in a multi-signature arrangement, there may be multiple different key combinations that all conform to a certain access mode; this fact is also relevant when comparing different arrangements. A set of different key combinations allowed under an access mode can be represented as "(1S+1A) 2 ", meaning that there are two other different key combinations under this access mode.
Using these notations, the table regarding the 2-of-3 multi-signature presence requirement can be expressed as follows:
| Key Arrangement | Access Mode |
|---|---|
| 3S/0A | (2S) 3 |
| 2S/1A | (2S) <sub>1</sub> , (1S + 1A) <sub>2</sub> |
| 1S/2A | (1S + 1A) ² , (2A) ¹ |
| 0S/3A | (2A) 3 |
Subcategories of agent-managed keys
While each self-managed key can generally be considered similar to others (the main difference being their storage location), keys managed by agents can be further distinguished based on the type of agent. In particular, it's common practice to differentiate between keys held by professional institutions skilled in key management and those held by close friends or family members responsible for managing a particular key. Since the introduction of the " Connections " feature, Unchained has supported both types of agent-managed keys.
It's also useful to differentiate the types of keys managed by these agents. Professional organizations generally have more experience in key management than friends and family because they have carefully designed safeguards and processes. Meanwhile, friends and family have an advantage in situations where institutional processes can be seen as cumbersome obstacles, such as in time-sensitive situations.
Self-access and agent insurance
One of the most important metrics for evaluating a multi-signature presence requirement arrangement is whether it provides users with autonomous access channels and/or a proxy guarantee. Autonomous access means that the Bitcoin in custody can be accessed entirely by self-managed keys, without the assistance of any key proxy. Proxy guarantee, on the other hand, means that even if all self-managed keys are lost, the Bitcoin in custody can still be retrieved because the arrangement has enough proxy-managed keys to authorize the retrieval of Bitcoin.
Self-governing access is useful if you want independent access to your Bitcoin without third-party involvement; however, it may be undesirable if you're worried about attackers extorting your funds. Agent insurance might be a good feature if you're concerned about losing all your self-governing keys; but it's also annoying if you're worried your key broker might collude and steal your Bitcoin.
| Advantages | Disadvantages | |
|---|---|---|
| Autonomous access | Completely independent control of funds, without the need for assistance from a key guarantor. | When faced with personal attacks, money may be even more at risk. |
| Insurance Agent | Even if all your keys are lost or stolen, your funds may still be recoverable. | In theory, key proxies could collude to steal funds. |
It's also worth noting that the disadvantages of both of the aforementioned characteristics can be mitigated through specific technologies. If an arrangement includes autonomous access and the self-managed keys are sufficiently dispersed spatially, then threats to personal safety are less likely to lead to financial loss. If an arrangement includes agent insurance, careful selection of agents can make the probability of collusion extremely low. It's possible to keep key agents unaware of each other's existence. You can divide the responsibility of key agents among professional institutions and relatives, thus requiring various types of betrayal—both institutional/governmental betrayal and personal betrayal.
Assessment median presence requirement
The median presence requirement is interesting because it forces you to choose between autonomous access and agent insurance. In a median presence requirement apparatus, no key arrangement can possess both characteristics simultaneously, nor can any arrangement lack both.
Let’s take a closer look at the simplest examples of median presence requirements, 2-of-3 and 3-of-5.
2-of-3 multi-signature
| Key Arrangement | Access Mode | Autonomous access | Agent insurance |
|---|---|---|---|
| 3S/0A | (2S) 3 | have | none |
| 2S/1A | (2S) <sub>1</sub> , (1S + 1A) <sub>2</sub> | have | none |
| 1S/2A | (1S + 1A) ² , (2A) ¹ | none | have |
| 0S/3A | (2A) 3 | none | have |
The 2-of-3 multi-signature presence requirement is the most widely recommended because it minimizes the total number of keys and management complexity, while successfully resisting single points of failure. It also offers a variety of key arrangement options to meet different objectives. The 3S/0A arrangement can be set up entirely on its own, without using any key brokers; its trade-offs were analyzed in an earlier article . 2S/1A is a good way to establish a joint custody relationship without relinquishing autonomous access. 1S/2A and 0S/3A are methods that minimize your key custody responsibility, and you don't need to trust a single Bitcoin custodian.
3-of-5 multi-signature
| Key Arrangement | Access Mode | Autonomous access | Agent insurance |
|---|---|---|---|
| 5S/0A | (3S) 10 | have | none |
| 4S/1A | (3S) 4 , (2S + 1A) 6 | have | none |
| 3S/2A | (3S) 1 , (2S + 1A) 6 , (1S + 2A) 3 | have | none |
| 2S/3A | (2S + 1A) 3 , (1S+2A) 6 , (3A) 1 | none | have |
| 1S/4A | (1S+2A) 6 , (3A) 4 | none | have |
| 0S/5A | (3A) 10 | none | have |
At the cost of more keys and increased complexity, the 3-of-5 presence requirement eliminates not only single points of failure but also "two points of failure" (i.e., funds can still be recovered even if any two keys are lost). This is the minimum presence requirement to achieve this, just as 4-of-7 is the minimum presence requirement to eliminate "three points of failure," and so on. In reality, most people only need to overcome single points of failure to successfully protect their Bitcoin in the long term.
The 3-of-5 presence requirement includes some interesting key arrangements, such as 3S/2A, which enables self-access but also provides a recovery path in the event of loss of most self-managed keys. 2S/3A, on the other hand, allows for agent insurance through three different agents, and funds can be withdrawn with just one agent and your two self-managed keys.
Assess the presence requirement if it is less than the median.
Presence requirements below the median are unique because they do not require a majority of keys to spend funds. Therefore, this category produces the most access patterns and key combinations with the fewest total keys. It is the only presence requirement that can generate arrangements that allow both autonomous access and agent-insured access.
Let's look at two of the simplest examples of presence requirements less than the median: 2-of-4 and 2-of-5.
2-of-4 multiple signatures
| Key Arrangement | Access Mode | Autonomous access | Agent insurance |
|---|---|---|---|
| 4S/0A | (3S) 6 | have | none |
| 3S/1A | (2S) ³ , (1S + 1A) ³ | have | none |
| 2S/2A | (2S) 1 , (1S + 1A) 4 , (2A) 1 | have | have |
| 1S/3A | (1S + 1A) ³ , (2A) ³ | none | have |
| 0S/3A | (2A) 3 | none | have |
The access modes provided by 2-of-4 multisignatures are not significantly different from those provided by 2-of-3 multisignatures, with one exception: 2S/2A. This arrangement is special because it indicates that the 2-of-4 presence requirement is the minimum multisignature presence requirement capable of generating three access modes. Similarly, 3-of-6 is the minimum requirement capable of generating four access modes, and so on.
The 2S/2A key arrangement is also the simplest way to have both self-governing access and agent insurance. This can be an attractive option if you want to have independent access to your Bitcoin without relying on an agent, but also have the possibility of receiving assistance from an agent in the event of completely losing your self-governing key.
2-of-5 multi-signature
| Key Arrangement | Access Mode | Autonomous access | Agent insurance |
|---|---|---|---|
| 5S/0A | (2S) 10 | have | none |
| 4S/1A | (2S) 6 , (1S + 1A) 4 | have | none |
| 3S/2A | (2S) 3 , (1S + 1A) 6 , (2A) 1 | have | have |
| 2S/3A | (2S) 1 , (1S+1A) 6 , (2A) 3 | have | have |
| 1S/4A | (1S+1A) 4 , (2A) 6 | none | have |
| 0S/5A | (2A) 10 | none | have |
Comparing 2-of-5 and 2-of-4 multisignatures, we find that they do not have a different set of access patterns. The main difference is that there are more possible key combinations when generating any access pattern, which also applies to the requirement of a larger total number of keys for 2-of-6 and 2-of-7. This fact may have its significance if you have a reason to prioritize one access pattern over others.
The required presence is greater than the median.
The uniqueness of presence requirements greater than the median is that an absolute majority of keys are required to spend funds. Therefore, this classification produces the fewest access patterns and key combinations. It is the only presence requirement that can potentially result in arrangements that lack both autonomous access and agent insurance.
Let's look at two of the simplest examples of presence requirements greater than the median: 3-of-4 and 4-of-5.
3-of-4 multi-signature
| Key Arrangement | Access Mode | Autonomous Access | Agent insurance |
|---|---|---|---|
| 4S/0A | (3S) 4 | have | none |
| 3S/1A | (3S) 1 , (2S + 1A) 3 | have | none |
| 2S/2A | (2S + 1A) ² , (1S + 2A) ² | none | none |
| 1S/3A | (1S + 2A) ³ , (3A) ¹ | none | have |
| 0S/3A | (3A) 4 | none | have |
With the same key arrangement, the access patterns offered by 3-of-4 multisignature are essentially the same as those offered by 3-of-5 multisignature, differing only in 2S/2A. It is the simplest key arrangement, offering neither voluntary access nor agent insurance. This may be attractive to those concerned about personal safety and therefore desiring key agent involvement in the withdrawal process, while simultaneously wanting to prevent collusion between key agents. Both concerns relate to the threat of theft, a greater risk than the median presence requirement prioritizes (compared to the danger of lost keys).
4-of-5 multiple signatures
| Key Arrangement | Access Mode | Autonomous access | Agent insurance |
|---|---|---|---|
| 5S/0A | (4S) 5 | have | none |
| 4S/1A | (4S) 1 , (3S + 1A) 4 | have | none |
| 3S/2A | (3S + 1A) ² , (2S + 2A) ³ | none | none |
| 2S/3A | (2S + 2A) ³ , (1S + 3A) ² | none | none |
| 1S/4A | (1S+3A) 4 , (4A) 1 | none | have |
| 0S/5A | (4A) 5 | none | have |
Compared to 3-of-4, 4-of-5 requires an additional key and also an extra key to authorize withdrawals. This makes moving funds more difficult and increases the risk of complete loss of access. If either of the two keys in the device is lost or damaged, the Bitcoin in custody becomes permanently inaccessible. While other presence requirements (such as 2-of-3) also have this issue, the risk of loss and damage is amplified if the total number of keys is higher (e.g., 5). Some presence requirements with values greater than the median (such as 4-of-6) have lower risks because they are further from the edge of the pyramid (closer to the center).
Determine your ideal storage device
As we demonstrated earlier, multi-signature wallets offer a wide range of presence requirements and key arrangements, resulting in highly customizable Bitcoin custody solutions. Some options may seem top-notch, but by understanding all the relevant trade-offs, you can narrow down your choices by prioritizing the features that matter most to you.
| Strengths | Shortcomings | |
|---|---|---|
| The total number of keys is small and the presence requirement is low. | Relatively simple, with fewer variables in analysis and management. | Customization capabilities are also relatively limited. |
| The total number of keys is large and the presence requirement is high. | It can meet more specific and refined needs. | The complexity increases due to the need to manage more key materials and other variables. |
| Median Presence Requirement | Treat the risks of loss and theft equally | No particular concern was given priority. |
| Presence requirement less than median | The risk of losing access is relatively small. | This could increase theft vulnerabilities. |
| Presence requirement greater than median | The risk of losing money due to theft is relatively small. | This could potentially increase the inaccessibility of funds due to vulnerabilities. |
| A larger proportion of self-managed keys | Less reliance on key brokers | Bringing more personal responsibility for managing key materials |
| A larger proportion of agents manage keys | This minimizes individual responsibility for key management. | More reliance on key brokers |
Some questions we can ask ourselves include:
- Are you willing and confident in safeguarding your Bitcoin keys?
- Is discretionary access a good thing or a bad thing for you?
- Is insurance through an agent good or bad for you?
- Does the complex arrangement with more elements bother you, or is it a necessary way to meet the needs of your business or organization?
- Do you have a strong preference for certain protections, such as preventing your Bitcoin from being lost due to loss of access or theft?
When considering these issues, most people might find that a certain key arrangement within the 2-of-3 presence requirement meets their goals. However, some might opt for a 3-of-5 presence requirement to increase customization capabilities, or a 2-of-4 presence requirement to simultaneously obtain autonomous access and agent insurance, or a 3-of-4 presence requirement to lock up funds long-term, or even a 4-of-6 presence requirement to simulate 3-of-4 while adding protection against key loss.
(over)








