According to the official website, Jimbos Protocol is an experimental protocol deployed on Arbitrum to "response to centralized liquidity". The main token launched by Jimbos Protocol - 20232023202320232023-0 - aims to periodically rebalance the liquidity of its protocol under different circumstances to improve capital utilization efficiency.
Huang Licheng, the brother of Maji that we are familiar with, spent millions of dollars to buy the tokens of this project a few days ago. After the attack, the related tokens also plummeted. I don’t know how brother Maji feels now.
The Beosin security team analyzed the incident for the first time, and now share the analysis results as follows.
Event related information
attack transaction
0x44a0f5650a038ab522087c02f734b80e6c748afb207995e757ed67ca037a5eda (one of them)
attacker address
0x102be4bccc2696c35fd5f5bfe54c1dfba416a741
attack contract
0xd4002233b59f7edd726fc6f14303980841306973
Attacked contract
0x271944d9D8CA831F7c0dBCb20C4ee482376d6DE7
attack process
There are multiple transactions in this attack, and we use one of them for analysis.
1. The attacker first lends 10,000 WETH in a flash loan.

2. The attacker then uses a large amount of WETH to exchange JIMBO tokens, making it drive up the price of JIMBO.
3. Then the attacker transferred 100 JIMBO tokens to the JimboController contract for the purpose of adding liquidity later (because the price of JIMBO has risen, only a small amount of JIMBO tokens are needed when adding liquidity).

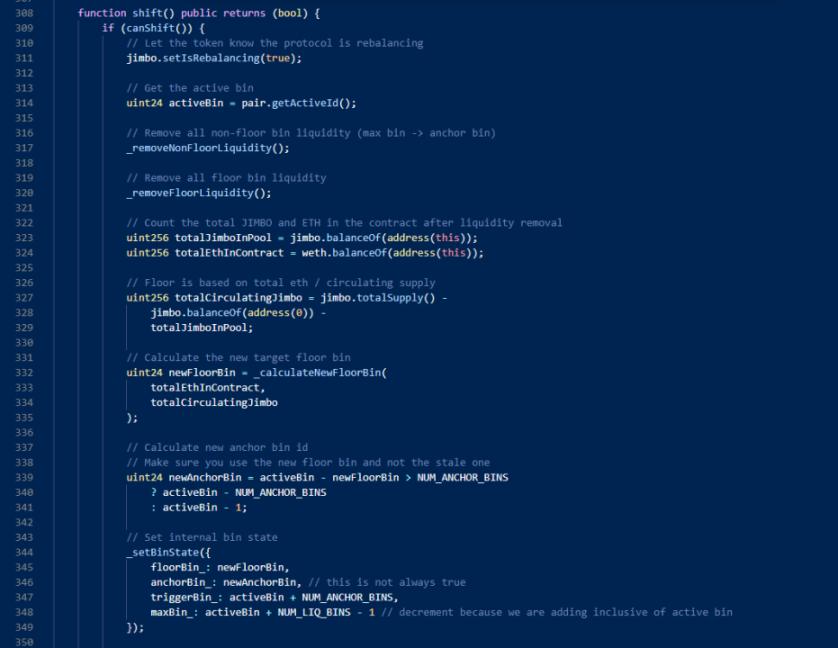
4. Then the attacker calls the shift function, which will remove the original liquidity and add new liquidity. Calling the shift function will take the funds of the contract to add liquidity, so that all WETH of the JimboController contract will be added to liquidity.
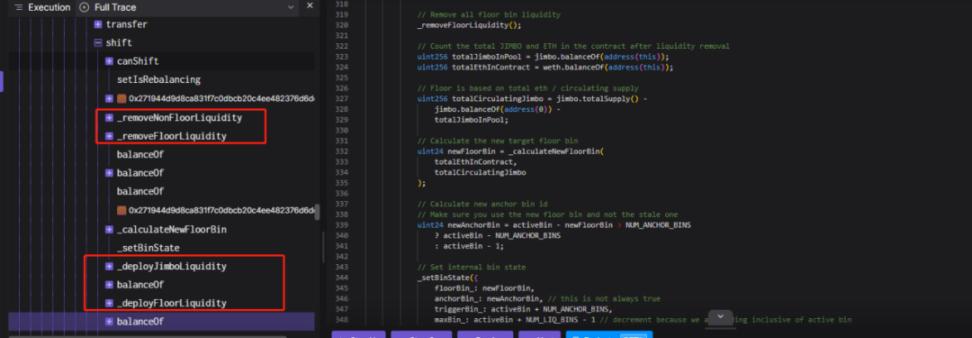
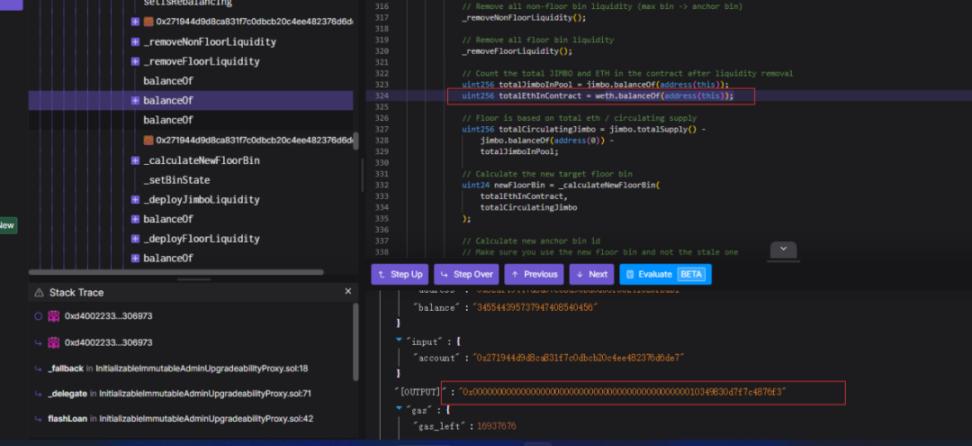
5. At this time, due to the addition of liquidity in an unbalanced state (when adding liquidity, it will rely on the current price as a basis to calculate the number of tokens required, which is equivalent to using a contract to receive orders), so that the attacker can get more WETH, the attacker finally converts JIMBO to WETH to complete the profit.

Vulnerability Analysis
This attack mainly takes advantage of the vulnerability in the JimboController contract, which allows anyone to use the shift function to make the contract perform removal and addition of liquidity operations, making it a high-level order.
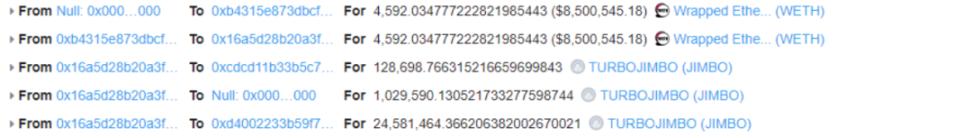
Funds Tracking
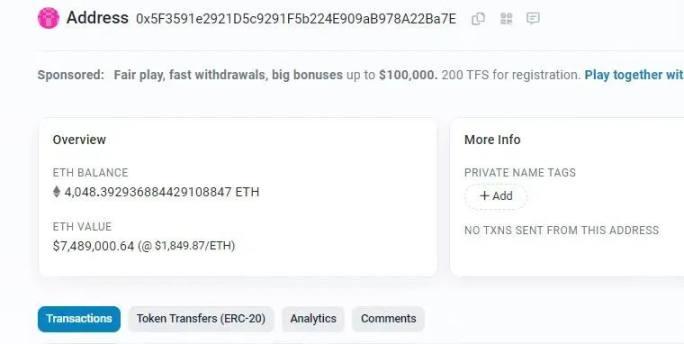
As of the time of writing, the stolen funds have not been transferred out by the attacker, and 4048 ETH are still in the attack address:
(https://etherscan.io/address/0x5f3591e2921d5c9291f5b224e909ab978a22ba7e)
Summarize
In response to this incident, the Beosin security team suggested that: during contract development, investment in the contract should be avoided by external manipulation; before the project goes live, it is recommended to choose a professional security audit company to conduct a comprehensive security audit to avoid security risks.








