What?
Vyper is a programming language designed for creating smart contracts on blockchain platforms. Inspired by Python, Vyper adopts a user-friendly and easily readable syntax, making it accessible to developers of all levels.
Curve Pool is a decentralized finance (DeFi) protocol that revolutionizes stablecoin swapping on blockchain networks. As an automated market maker (AMM) optimized exclusively for stablecoins, Curve Pool ensures seamless and cost-effective exchanges between stable assets with minimal slippage and fees. Its unique algorithm is designed to minimize price impact during trades and maximize capital efficiency, making it a preferred choice for traders and liquidity providers seeking stablecoin liquidity.
Thanks for reading Verichains! Subscribe for free to receive new posts and support my work.
How?
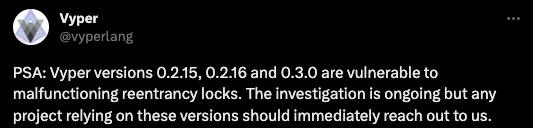
“A number of stablepools (alETH/msETH/pETH) using Vyper 0.2.15 have been exploited as a result of a malfunctioning reentrancy lock. We are assessing the situation and will update the community as things develop.” - @CurveFinance
The attacks have occurred across various blockchain chains, resulting in a total loss of over $59 million. These losses are attributed to pools that use vulnerable versions of Vyper and contain ETH. Pools Hacked:
CRV/ETH pool
alETH/ETH pool
msETH/ETH pool
pETH/ETH pool
…
According to Curve Finance, there are still pools on Arbitrum that may be vulnerable. They advise users to remove liquidity as soon as possible for precautionary reasons.
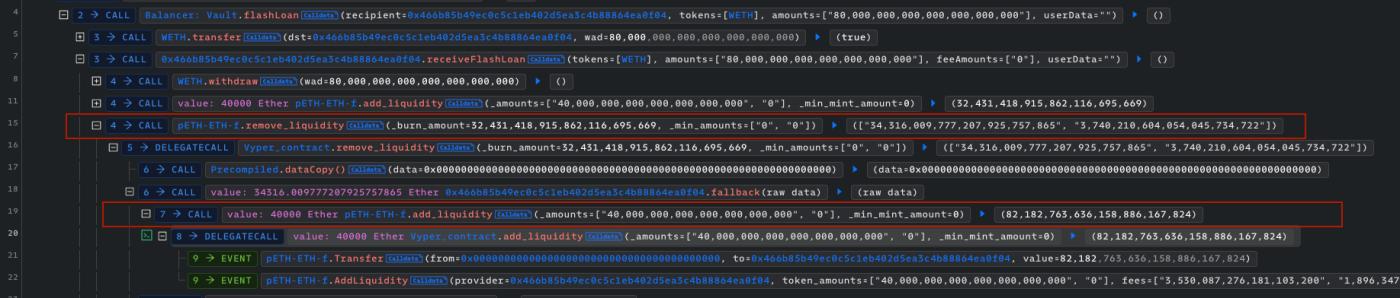
In attacks, the attacker reentered the add_liquidity function after calling the remove_liquidity function. The states do not fully update before reentering the add_liquidity function, resulting in lp_price calculation error.
Why?
Curve Pools are developed using the Vyper programming language, and this vulnerability exists within the Vyper compiler.
The vulnerability allows the attacker to perform reentrancy despite the function being protected by the built-in nonreentrant decorator in Vyper.
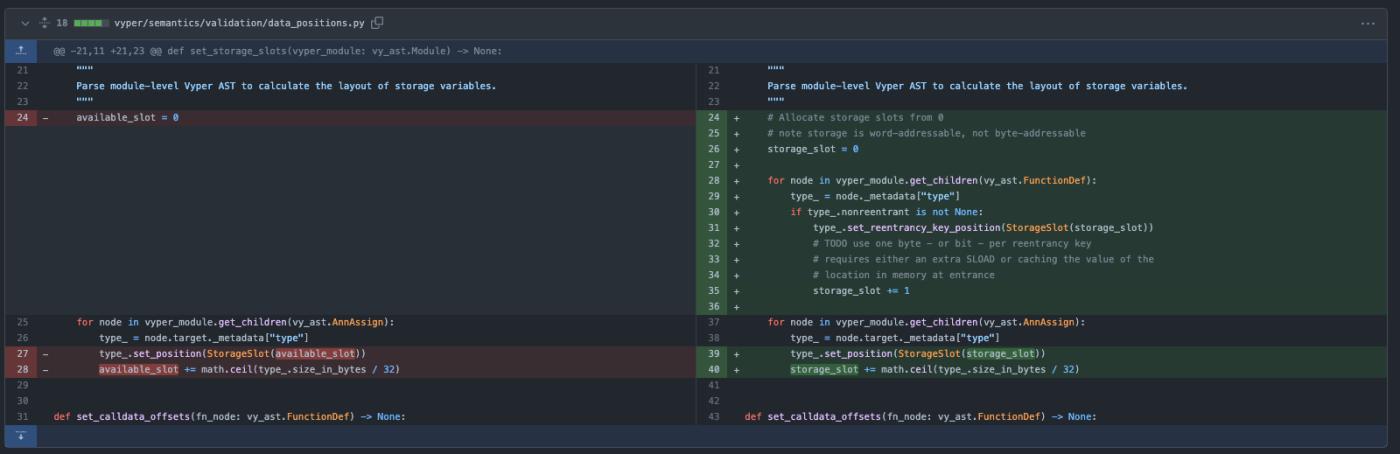
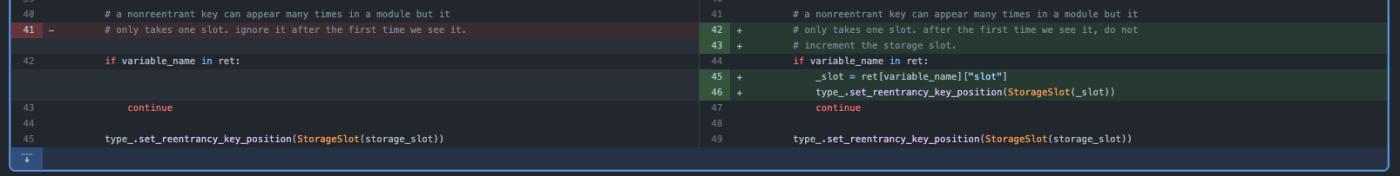
The vulnerability's root cause can be traced back to a commit made between versions 0.2.15 to 0.3.0 of the Vyper compiler, written in Python. During compilation, the Vyper code loads reentrancy decorator and stores it into a storage slot. However, the important check to verify if the reentrancy already exists before storage and slot increment is missing in the code. Consequently, each function gets its separate reentrancy lock slot, which is independent and fails to provide protection against reentrancy attacks.
Affected Vyper version:
0.2.15
0.2.16
0.3.0
Conclusion
The attacker carefully examined Vyper's bug fixes and targeted contracts using vulnerable versions, resulting in significant losses for Curve.
The important lesson learned is that vendors must promptly inform the developer community about critical bug fixes. It is encouraged to utilize open-source technologies, including security features developed and reviewed by the community. Conducting thorough security reviews before releasing new versions or making significant changes to essential features is crucial. By adopting these practices, we can enhance system security and provide a safer environment for all users.
Thanks for reading Verichains! Subscribe for free to receive new posts and support my work.