Author: Bankless / Source: https://www.bankless.com/10-projects-i-want-someone-to-build
Translation: vernacular blockchain

1. What is EigenLayer?
EigenLayer is very simple. It creates a job market for more than 900,000 Ethereum operating nodes and others (i.e., computers running Ethereum software around the world) to perform more decentralized tasks to earn additional rewards. If they run new tasks maliciously, they will be punished and slashed.Rehypothecation occurs when mortgagees entrust their shares to these operators to provide financial security such that the total reducible shares are greater than the operator's corrupt interests.
From this perspective, any protocol that requires a group of decentralized computers to perform tasks can hire EigenLayer operators (Ethereum operators and computers selected through EigenLayer to run more tasks), quickly launch their own group to Centralized network.
The term "Rollup Service", as the name suggests, refers to the services provided for Rollup. Many early and immediate EigenLayer applications fall into this category of services.
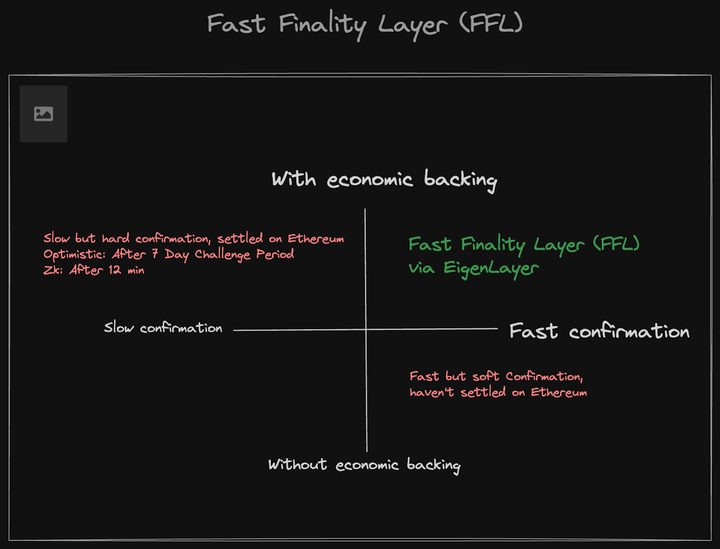
2. Quick settlement
For fast settlement aspects of optimistic and zero-knowledge (zk) RollupCurrently, Rollup only supports slow mode. For optimistic rollups, transactions take seven days to settle, while for zk rollups, it takes 12 minutes. That's fine, but what if you want to do some fast and atomic transactions or operations that require instant settlement and confirmation?
Quick Finalization is a system that enables any Rollup and L2 to declare that a specific block's transactions can lead to a specific state of commitment. This basically means that a transaction that you thought was completed on the blockchain actually is, and can be completed almost instantly (otherwise, there would be a lot of money and collateral being slashed).
With Quick Terminator, Rollup now has the option to run in Fast Mode and Slow Mode.
In "Quick Mode," nodes at this layer can verify confirmations instantly, ensuring economic certainty in the event of majority agreement . Confirmation goes through a challenge period when switching to "slow mode", used in cases where malicious behavior is suspected.
You can leverage EigenLayer operators to build many cryptographic primitives and networks, such as Zero-Knowledge Proofs (ZK), Multi-Party Computation (MPC), Trusted Execution Environments (TEEs), Fully Homomorphic Encryption (FHE), and more.
3. Shamir secret sharing
Get the reorganization-resistant properties of chains and networks with EigenLayer economic securityShamir secret sharing is a method of splitting a secret into multiple parts and releasing them only when certain conditions are met. This is possible through EigenLayer node operators who commit to storing secrets and may have their funds deducted if the secrets are not released when conditions are met.
4. TEE Committee
The system will only be affected if a large number of TEE nodes are compromised, which significantly reduces the trust assumption.Currently, some protocols are exploring the use of TEEs ( Trusted Execution Environments ) as an alternative way to guarantee certain computations, such as running private auctions or ensuring that certain data cannot be tampered with.
A protocol can enhance its security by leveraging TEE and building a distributed TEE network, called a TEE committee.
Combining TEE with committees greatly enhances the reliability of committees. This means that unless a majority of committee members collude and violate the TEE's security model, no threat can be posed to the system. In the TEE committee, multiple TEE models may be used, such as Intel SGX, ARM TrustZone, and Amazon Nitro, and signature confirmation is required for each model.
EigenLayer provides trust in decentralization while lending economic trust when it can be cut.
The TEE committee also provides privacy protection, making it suitable for scenarios that require both program integrity and privacy.
5. Optimistic zero-knowledge proof and negative proof
Stay optimistic most of the time and only run zero-knowledge proofs when fraud is detected.Negative Proof introduces an innovative way of handling on-chain proofs, prioritizing efficiency and cost-effectiveness. In this system, the proof is initially accepted by the OP and is not immediately verified on-chain, assuming that actors such as "naysayers" will only interact with the proof if they find an error . The disadvantage of fraud proof is that it must operate under a stronger model, as it requires assumptions, synchronicity, censorship resistance, and the existence of at least one honest party.
However, fraud proofs are particularly suitable for proof systems with repeated structures or multi-round applications, and play a role in open proofs of FRI polynomial commitments, post-quantum secure digital signature schemes, and verifiable shuffling. Finally, they differ from fraud proofs in that they focus on identifying disagreements in the evaluation of the validator circuit, making them significantly more efficient.
You can launch any general decentralized network through EigenLayer to build a decentralized off-chain infrastructure.
6. Circuit breaker
A network of nodes that monitors and takes action against malicious transactions. Most applications have a built-in circuit breaker , the exact name depends on the protocol, but in principle it is capable of suspending the entire protocol or disabling specific functions. When thinking about this concept, imagine if this responsibility could be shifted to Ethereum’s validators. The network of nodes will monitor this circuit breaker function, and if the protocol misbehaves—pausing too late or at an inappropriate time—it may be curtailed.Leveraging Ethereum’s trust network to oversee the protocol encourages good behavior and discourages bad behavior.
7. Decentralized RPC (remote procedure call)
To ensure that the RPC system is not compromised and prevents erroneous data from being sent, a decentralized network of nodes can be created that not only manages RPC services but also appends signatures to their responses, which are guaranteed by economic security.Decentralized RPC is an AVS (Decentralized Application Service) design that not only manages these services, but also validates signatures, adding an additional layer of responsibility. It reinforces trust by identifying any discrepancies or data errors and holds relevant parties accountable. For RPC services like Alchemy and Infura, people usually assume that the data they provide is accurate and trustworthy. However, these services are not infallible and there is a small risk of being tampered with or providing erroneous data. Decentralized RPC aims to solve these problems.
MEV (miner tie-in value) management basically describes a situation where Ethereum proposers make additional commitments on how blocks are constructed, generated, and ordered. In addition to Ethereum proposers, any individual participating in the MEV pipeline can make these additional commitments.
8. Slot auction
The slot auction allows the next 32 public validators to auction their verification slots in advance.Slots play a key role in enhancing the security and efficiency of Ethereum’s PoS system. They help prevent attacks, reduce validators’ data storage needs, and ensure the security and stability of Ethereum’s history. The "slot auction" is a concept where the next batch of upcoming validators can auction their verification slots in advance.
During each checkpoint, information about the next upcoming batch of validators is released to the public, and each of these validators can auction their own validation slots in advance, eliminating the need to be in a proposer slot. The necessity of MEV to maximize value.
This approach will provide traders with the opportunity to improve execution over a variety of time periods and help manage execution risk more effectively. Implementing this approach requires commitment from validators, both off-chain and on-chain, and may risk funding cuts.
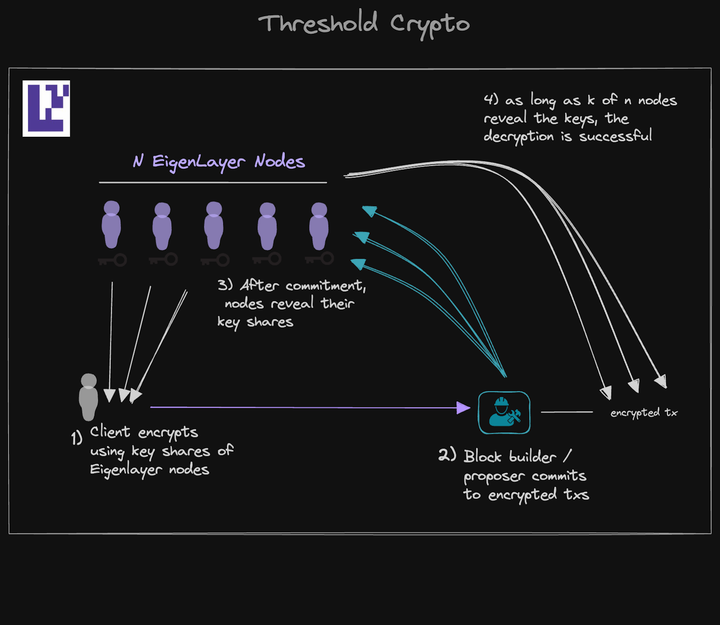
9. Threshold encryption
Threshold encryption is an encryption technique in which data is divided into parts and distributed to multiple participants, and only when a certain threshold is reached, the parts can be reconstructed into the original data.Threshold cryptography offers a potential solution for applications that need to protect against targeted front-running transactions and enhance on-chain privacy. The core concept involves using an encrypted message as an example that can be decrypted by at least k out of n signers, but not by less than k.
This requires k to be large enough and a decentralized set of signers to mitigate the effects of collusion and liveness attacks. This decentralized collection of nodes can be inherited from EigenLayer .
Coprocessors are operations that can be computed and executed off-chain, extending the range of what primary computers (like Ethereum) can operate on and running these tasks in a more efficient manner, but still in a provable, trust-minimized manner .
10. Implement program integrity and session privacy for AI inference
In the current field of artificial intelligence, only a few centralized entities are running AI inference engines. Therefore, there is a strong incentive to leverage EigenLayer for on-chain AI inference:Leveraging zero-knowledge ( ZK ) technology for machine learning ( ML ) improves the cost-effectiveness and computational integrity of artificial intelligence operations by providing an alternative to centralized servers such as AWS .
Privacy is enhanced through a mechanism that allows operators running AI engines to decrypt consumer queries only if many operators collude. This approach is consistent with the decentralization principles inherited from the Ethereum network of trust .
11. Summary
This article touches on some of the big categories you can build on EigenLayer: Rollup services, threshold encryption, decentralized off-chain infrastructure, MEV management and co-processors, etc.You can go beyond these basic categories and think about more interesting and bold ideas - like decentralized power grids, data tagging (e.g., token-based CAPTCHAs), decentralized front ends - for anything you need multiple computers to run and Tasks with certain credibility guarantees can be completed through EigenLayer.








