In the rapidly evolving blockchain landscape, privacy and security have become important areas of research for practitioners, and the Threshold Network's Threshold encryption service can empower blockchain users' sovereignty, allowing users to effectively protect their information security and digital asset privacy while experiencing the public blockchain. How does Threshold achieve all this, and what is the core of its operation? If we want to invest in it, how do we buy its tokens? Let's take a closer look at this article.
I. What is Threshold Network?
Threshold Network (T) was launched in January 2022 and is the first on-chain merger between two existing decentralized networks (Keep Network and Nucypher). Both technologies involve building sustainable, blockchain-based privacy solutions for users. While these two networks already have their own native tokens, the goal of the Threshold network is to allow smart contracts to access the Threshold Network, which is designed to guarantee users' sovereignty over their digital assets, including simple wallets and cryptocurrencies, as well as user data, smart contracts and information contained in decentralized applications (DApps), non-fungible tokens (NFTs) and other digital assets. Its launch is also to address data and privacy issues, to cope with various hacker attacks on the blockchain and to make the decentralized digital finance industry more mainstream. As Threshold Network is a product of the merger of Nucypher and Keep Networks, it also has the following features: 1. Keep Network: The structural elements of the Threshold Network are derived from the Keep Network, which uses off-chain containers to encrypt, store and transmit private data. These containers, called "keeps", can be accessed by smart contract developers without compromising user privacy or network transparency. This technology has previously been positively tested for use in tBTC, which is considered one of the most trusted Bitcoin (BTC) bridges in DeFi, connecting BTC to Ethereum. 2. Nucypher: Nucypher's privacy tools are built on top of the "keeps", including its management of confidential or sensitive information, so that the processed and encrypted data will not be leaked. The network can also grant and revoke access permissions to sensitive information, thereby protecting it in the event of any abnormal activity. In addition, the Threshold Network also utilizes Nucypher's proxy re-encryption tool, which can securely and reliably delegate decryption permissions.
II. How does Threshold Network operate
While the blockchain revolution has unleashed the power of decentralized Apps, the Web3 platforms built on public blockchains may pose great risks to user privacy. Through the use of threshold cryptography, the Threshold Network provides an exclusive solution to the privacy challenges of Web3 platforms. Relying on the decentralized network nodes and threshold cryptography, in the Threshold ecosystem, sensitive operations are distributed among multiple independent entities (such as network nodes). To successfully execute these operations, a certain minimum threshold or number of collaborating entities is required. This mechanism ensures that even if there are a few malicious actors, the system can continue to operate safely and correctly.
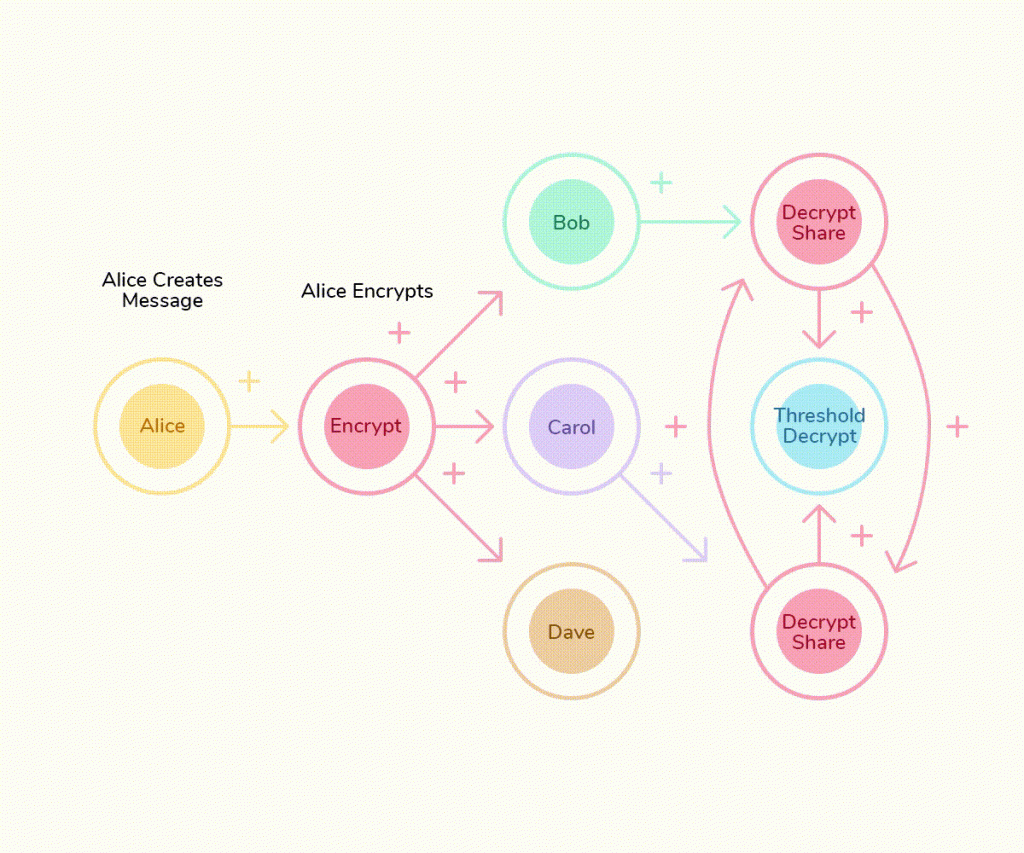
Within the Threshold framework, sensitive operations no longer depend on a single trusted party, effectively reducing the risk of system disruption. Even if there are a few malicious actors or bad actors, as long as the minimum number of participants continue to follow the rules, the system can still run securely and correctly. This distributed collaboration mechanism has brought revolutionary changes to the field of information security. Take centralized custodians as an example, in the traditional model, if there are bad actors among the custodians, user funds may face great risks. However, under the protection of the Threshold cryptographic system, this single point of failure has been effectively prevented. Even if a node or entity has a problem, the other nodes can still work together to ensure the overall security and stability of the system.
III. What is the technical core of Threshold Network?
The Threshold Network ecosystem combines the advantages of Threshold cryptography, PRE privacy protection services, and the decentralized Bitcoin to Ethereum bridge tBTCv2. It aims to enhance user privacy, control and accessibility in the web3 environment. By providing a set of encryption services to web3 applications through a decentralized node network, the services on this network include confidential management and proxy re-encryption (PRE) services with user-controlled access control, as well as tBTCv2 (a decentralized and permissionless Bitcoin to Ethereum asset bridge). Threshold Network's proxy re-encryption (PRE) is an encryption middleware that can support privacy-preserving applications. It uses a scalable end-to-end encryption protocol, where the nodes on the network act as proxy entities. These nodes securely and collaboratively re-encrypt data for the recipient based on the access conditions defined by the data owner. PRE is particularly useful for maintaining data ownership while enabling data sharing, such as paid subscriptions for encrypted content or encrypted Non-Fungible Token (NFT) transfers. Data remains private and encrypted, and data owners can enforce access control through encryption.

Another component of the Threshold ecosystem is tBTCv2, a decentralized and permissionless Bitcoin to Ethereum asset bridge. Unlike existing centralized solutions, tBTCv2 allows Bitcoin holders to access DeFi and the web3 universe without relying on intermediaries. It replaces the centralized intermediary with a randomly selected set of operators running nodes on the Threshold network. These operators collectively use Threshold cryptographic technology to protect the Bitcoin deposited by users. User funds are controlled by the consensus of the majority of these operators, preventing individual or group control. tBTCv2 is permissionless, ensuring that everyone can access it.
IV. Threshold DAO
The DAO (Decentralized Autonomous Organization) of the Threshold Network is the core of its decentralization mechanism, providing a platform for community-driven projects and a framework for democratic and decentralized voting, which is crucial for the entire network's operation. This goal is achieved through the dual-track governance system of the Threshold DAO, which mainly includes the following two aspects:
- StakerDAO:
- The DAO holds the core decision-making power in the Threshold network, as it represents the stakers who run the decentralized nodes. These nodes are responsible for verifying transactions, ensuring the continuous operation of the network.
- Each member of the StakerDAO must hold a stake in the Threshold network, and their voting power is proportional to the size of their stake.
- This ensures that those who directly contribute to the network (by running nodes) have a greater say.
- TokenHolderDAO:
- The DAO members manage the finances, token issuance and network governance through decentralized voting and community-driven decision-making.
- To maintain accountability, the TokenHolderDAO has the power to veto proposals from the StakerDAO. This provides a system of checks and balances to ensure that no single group can unilaterally control the network.
- Each member of the TokenHolderDAO must hold the Threshold network's tokens (assumed to be T tokens here), ensuring that only those with an economic stake in the network can participate in this layer of decision-making.
- Keep and Nucypher Representative Council: This elected member committee decides the staker rewards to incentivize token holders to become network stakers. The committee also has the power to veto proposals to ensure the network's trajectory remains decentralized, aligned with the Threshold network's ethos, and maintains accountability.
V. Threshold Token Economics
$T is the native token of the Threshold Network, which can be used as both a utility token for the network and a governance token for the Threshold DAO. $T enables the operation of the network, with the following functions and uses:
Staking rewards: Like all proof-of-stake (PoS) consensus algorithms, users must stake their tokens to become validator nodes and receive rewards. Rewards are given for honest behavior, and penalties are imposed for dishonest behavior. The amount of $T staked by each node affects the rewards they will receive as well as their voting power in the DAO. The more $T staked, the more likely they are to be selected to validate blocks.
Liquidity pools (LP): The Keep Network proposes to provide incentives for users to move their liquidity from the available KEEP-ETH pool on Uniswap to the T-ETH pool. This will increase the available yield rewards, potentially increasing the number of Threshold token holders and strengthening the network DAO's connection with new community members.
$T holders can help run the Threshold network by staking and running decentralized nodes to verify activity on the network, and they are incentivized to do so without the use of any centralized institutions. Additionally, by becoming active members of the DAO and participating in voting and discussions, $T token holders can ensure the network, maintain community engagement, and decentralize the total supply of $T, which is 10 billion, with 90% of the initial token supply exclusively held by the initial owners of NU and KEEP tokens, and the remaining 10% of the total supply held by the Treasury.
VI. Analysis of the Future Value of Threshold
As an innovative cryptocurrency and blockchain technology, the Threshold Network has significant advantages in terms of security and privacy protection, while also supporting scalability and decentralization. However, its complexity and cost issues may limit the widespread adoption and application of the technology. Additionally, challenges in performance need to be properly addressed to ensure the network's competitiveness and user satisfaction. With the continuous progress of technology and the development of the market, the Threshold Network is expected to play a greater role in the future, but it also needs to overcome its existing shortcomings and challenges. The Threshold Network has a truly promising product and the structure and tools to achieve this goal. Furthermore, its incorporation of the Keep and Nucypher network communities should mean it has a healthy DAO community and a large number of staking nodes to ensure decentralization and activity. This means that $T has a very promising future as a cryptocurrency. In the long run, as more and more applications are built around its functionality, Threshold has tremendous upside potential.






