In traditional finance, the lending market provides short-term lending opportunities, usually for liquid and low-risk assets, with the aim of providing safe and as high a return as possible. In decentralized finance (DeFi), this concept has evolved, primarily referring to the ability to borrow various digital assets in a decentralized and permissionless environment, without specific time constraints. These platforms allow users to deposit cryptocurrencies into the protocol, and borrowers provide sufficient collateral in exchange, paying interest to the depositors.
The lending market uses dynamic interest rate models, which automatically adjust the lending and borrowing rates based on the liquidity utilization of a particular market or pool. These models ensure efficient capital allocation and incentivize borrowers to return the borrowed assets when liquidity is tight. A key feature of this rate model is the "kink point", where the rate starts to rise significantly when the utilization reaches a critical threshold, in order to control the leverage in the system: as utilization increases, the rate may gradually rise, but once it exceeds the kink point, the rate will spike rapidly, significantly increasing the cost of borrowing.
It is important to note that the lending market is different from unsecured loans: the lending market requires borrowers to provide collateral to secure the loan, ensuring that the loan can be repaid at any time during the loan term; while unsecured loans (typically traditional loans) allow customers to borrow without providing collateral (or only partial collateral or other guarantees), and the repayment of the loan depends on credit scores and legal means to ensure security.
Lending markets: the fundamental "Lego" of the DeFi ecosystem
The importance of lending markets in DeFi is mainly reflected in their ability to help users earn returns on their idle assets without selling them, and unlock liquidity. This function plays a crucial role in the capital efficiency of DeFi. The ability to borrow based on specific tokens is one of the most sought-after features in the industry and is often an important criterion for determining whether a crypto asset is a "blue chip" asset.
This function allows users to access leverage at low cost, helping high-net-worth individuals (HNWIs) incorporate assets into tax planning, and also allows teams with abundant but illiquid assets to borrow against their treasury and holdings to provide operating capital, while earning interest on the collateral (for example, Curve and Maker in the past few years are two typical cases).
In addition, lending markets also serve as the foundation for other DeFi tools, such as collateralized debt positions (CDPs), yield farming strategies (supporting many "delta-neutral" strategies), and on-chain margin trading. Therefore, lending markets are one of the most important building blocks of DeFi, also known as the "money Lego".
To give you a clearer understanding of the scale of these lending markets, the total value locked (TVL) in crypto lending protocols has already exceeded $32.6 billion, as shown in the figure below.
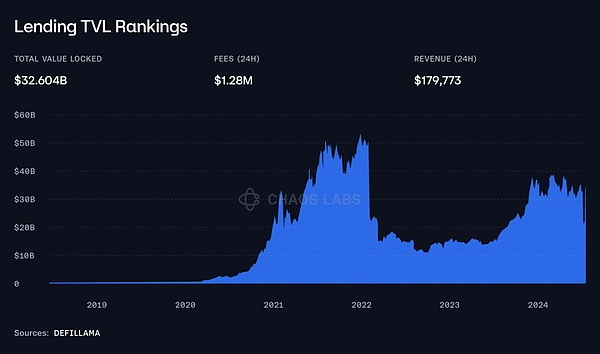
Source: Defillama
Design decisions in crypto lending markets: shared liquidity pools vs. isolated liquidity pools
While crypto lending markets all serve the same basic purpose, there are significant differences in the design of their liquidity structures. The main distinction is between markets that use a single shared liquidity pool (such as @Aave) and those that use isolated liquidity pools (such as Compound v3). Each model has its own trade-offs, with factors such as liquidity depth, asset flexibility, and risk management coming into play.
Isolated liquidity pools: flexibility and risk isolation
In the isolated liquidity pool model, each market or asset operates within its own independent liquidity pool. This approach is adopted by protocols like Compound v3, and even more extreme examples like Rari Capital (before its collapse).
The main advantage of isolated liquidity pools is their flexibility in building sub-markets. This flexibility allows protocols to create markets tailored to specific asset classes or user needs. For example, isolated liquidity pools can be specifically designed to support a particular group of assets, such as meme tokens, or to only allow certain tokens due to their unique risk characteristics or demand.
This customization is one of the key benefits of the isolated liquidity system, as it allows projects to cater to specific communities or niches that may not fit the framework of a more broadly shared liquidity pool. This advantage has been particularly highlighted with the rise of LRTs (liquidity return tokens) and tokenized base trades (such as USDe): many users want to capture high yields, but are unwilling to take on the risks associated with new assets.
In addition to flexibility, isolated liquidity pools also provide better risk isolation. By segregating each market, the risk of any particular asset is contained within its corresponding liquidity pool. This means that if the price of a token experiences a sharp decline or becomes overly volatile, the potential impact is limited to that market and does not spill over to other parts of the protocol.
However, these benefits also come at a cost, as isolated liquidity is a double-edged sword, implying fragmentation of liquidity.
For isolated markets, each market must face the "cold start" problem - this is not just a one-time challenge, but one that must be addressed every time a new market is created. Each market can only rely on its own participants, and liquidity may not be sufficient to support large-scale lending activities.
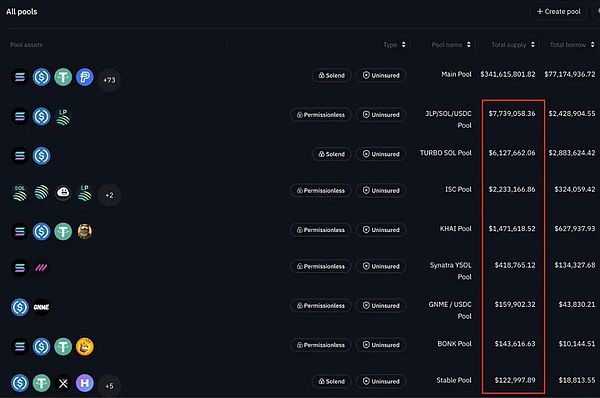
Source: Solend — limited liquidity available on isolated markets
As mentioned earlier, some protocols have taken the concept of isolated lending markets to the extreme, enabling permissionless market creation.
In these cases, such as Rari or @Solendprotocol, users can create permissionless markets themselves, deciding on whitelisted assets, setting risk parameters (such as loan-to-value (LTV) and collateral ratio (CR)), and managing the corresponding incentive mechanisms.
Shared liquidity pools: deep liquidity from day one
On the other hand, a single shared liquidity pool provides deep, ready-to-use liquidity from the start. By aggregating all assets into a unified pool, shared liquidity systems can support large-scale lending activities, with fewer liquidity constraints, and even new assets can be supported.
Borrowers can also benefit from the shared pool: a larger liquidity base attracts more borrowers, generating higher and typically more stable returns, as they are supported by diversified borrowing demand.
This is the main advantage of the shared liquidity model, and while it may be the only advantage, its importance cannot be overstated. In each market, liquidity is king, especially in crypto markets.
However, the main drawback of shared liquidity pools is systemic risk. Since all assets are tied to the same pool, an issue with one asset (such as a sudden devaluation) can trigger a cascade of liquidations, and if bad debts arise, it can impact the entire system.
Therefore, these pools may not be suitable for niche or more experimental assets, especially compared to more liquid and mature tokens.
Finally, the governance and risk monitoring of shared liquidity systems is generally more complex, as the risks involved in any changes to the protocol are greater.
Model Combination: Exploring Hybrid Modes
The trade-offs between isolated liquidity pools and shared liquidity pools are significant, and there is no perfect solution. This is why, as the market matures, the lending market is gradually moving towards a hybrid model (or at least introducing hybrid functionality) to balance the liquidity advantages of the shared pool with the customization and risk isolation provided by the isolated markets.
A typical hybrid example is the customized isolated market introduced by Aave, which collaborates with platforms such as @LidoFinance and @Ether_Fi. Aave's system typically uses a single shared liquidity pool to provide deep liquidity for major assets. However, Aave also recognizes the need for greater flexibility in supporting assets with different risk characteristics or use cases, and has therefore created markets tailored to specific tokens or collaboration projects.
Another key feature of @Aave that is in line with this trend is the eMode design. eMode aims to optimize capital efficiency when trading with related assets. Specifically, eMode allows users to unlock higher leverage and borrowing capacity for assets with higher price correlation (and thus significantly lower liquidation risk) by isolating specific positions, greatly improving capital efficiency.
Other protocols such as @BenqiFinance and @VenusProtocol, traditionally belonging to the shared liquidity category, have also taken an important step by introducing isolated pools for specific sub-sectors. In these cases, the isolated markets are customized for niche areas such as GameFi, real-world assets (RWA) or "ecosystem tokens", without affecting the operation of the mainstream pool.
At the same time, isolated market lending platforms like Compound or Solend typically have a "main pool" as a shared liquidity pool, or in the case of Compound, they have recently started adding more assets to the most liquid pools, effectively also moving towards a hybrid model.
Note: Solend initially adopted a shared liquidity model, but later changed its design.
Business Model of Crypto Lending Markets
The core business model of the crypto lending market revolves around generating revenue through various mechanisms related to lending, borrowing, and collateralized debt positions (CDPs).
1. Interest Rate Spread: The main source of revenue for lending markets is the spread between lending and borrowing rates. Users can earn interest by depositing assets into the protocol, while borrowers must pay interest to access liquidity. The protocol profits from the difference between the borrowing rate paid by borrowers and the deposit rate received by depositors. This spread is typically small, but as more users participate in the protocol, the earnings will gradually accumulate. For example, in the Ethereum market of Aave v3, the deposit rate for $ETH is 1.99%, while the borrowing rate is 2.67%, resulting in a 0.68% spread.
2.Liquidation Fees: Lending markets also generate additional revenue from liquidation fees. When a borrower's collateral falls below the required threshold due to market volatility, the protocol initiates a liquidation process to maintain the system's solvency. Liquidators pay a portion of the borrower's debt in exchange for the collateral at a discounted price. The protocol typically takes a share of this reward, and in some cases, the protocol itself may run liquidation bots to ensure timely liquidation and create additional revenue.
3.CDP-related Fees: Some protocols charge specific fees for their CDP (collateralized debt position) products, which can come from the interest paid on borrowing the CDP assets, and may be charged on a time-based or one-time basis (or both).
4. Flash Loan Fees: Most protocols allow users to take out flash loans and charge a relatively small but highly profitable fee. Flash loans are essentially loans that must be repaid within the same transaction, and they allow users to instantly access the capital needed to execute specific operations (such as liquidation).
5. Treasury Yield: Protocols may also earn yield from their treasuries, typically choosing the safest return options.
These mechanisms make lending markets one of the most profitable protocols.
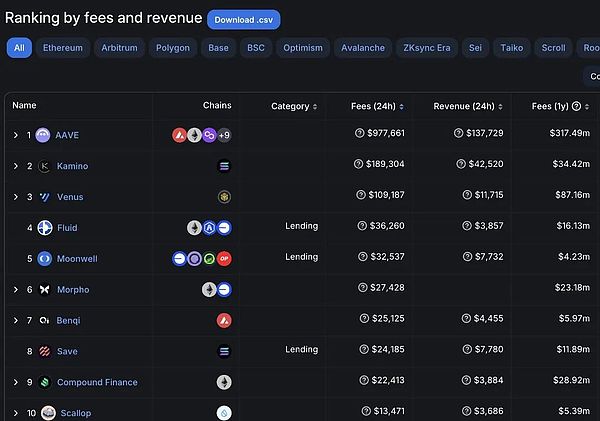
These fees are sometimes shared with governance tokens, or redistributed through incentive mechanisms, or used to cover operational expenses.
Risks <> Lending Markets
As mentioned earlier, operating a crypto lending market can be one of the most profitable businesses, but it is also one of the riskiest.
One of the first challenges faced by emerging lending markets is the "cold start" problem.
The cold start problem refers to the difficulty in bootstrapping liquidity in a new protocol or market. Due to concerns about lack of liquidity, limited borrowing opportunities, and potential security vulnerabilities, early users are often reluctant to commit funds to a pool that has not yet reached sufficient scale. If there are not enough initial deposits, interest rates may be too low to attract borrowers; while borrowers may find it difficult to obtain the required loans, or face excessively volatile rates due to liquidity fluctuations.
Protocols typically solve the cold start problem through liquidity mining incentives, where users are rewarded with native tokens for providing liquidity or borrowing liquidity (with the incentives for one side indirectly affecting the other, especially in the case of circular borrowing). However, if these incentives are not properly managed, they may lead to unsustainable token issuance, which is a trade-off that protocols need to consider when designing their launch strategies.
Timely liquidation is another key element in maintaining the solvency of the protocol. When a borrower's collateral value falls below a certain threshold, the protocol must liquidate it to prevent further losses. This faces two main challenges:
First, the success of this process largely depends on the liquidators - whether operated by the protocol or managed by third parties - who need to monitor the protocol in real-time and execute liquidations swiftly.
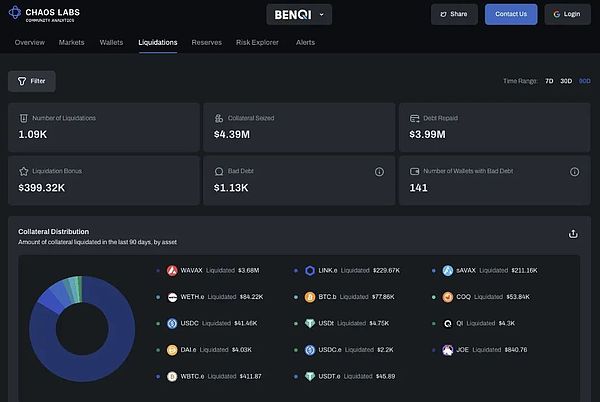
Source: Chaos Labs Benqi Risk Dashboard
To ensure smooth liquidation, the liquidators need to be sufficiently incentivized through liquidation rewards, which must be balanced against the protocol's revenue.
Secondly, the liquidation process must be triggered when it is economically safe to do so: if the value of the seized collateral is close to or almost equal to the outstanding debt, the risk of that position slipping into bad debt increases. In this process, defining safe and up-to-date risk parameters (such as loan-to-value ratio (LTV), collateral ratio (CR), and setting a liquidation buffer between these parameters and the liquidation threshold) is crucial. The asset whitelist on the platform also needs to go through a rigorous selection process.
Furthermore, to ensure the smooth operation of the protocol, timely liquidation, and prevent user abuse of the functionality, lending markets rely heavily on functional oracles that provide real-time valuations of the collateral and indirectly reflect the health and liquidability of loan positions.
Oracle manipulation is an important risk, especially in protocols with low liquidity assets or those relying on a single source oracle, where attackers can distort prices to trigger liquidations or borrow at incorrect collateral levels. There have been multiple incidents of this in the past, the most notable being the Eisenberg exploit of the Mango Markets vulnerability.
Delay and latency are also key factors; during market volatility or network congestion, delays in price updates can lead to inaccurate collateral valuation, resulting in delayed or mispriced liquidations, ultimately causing bad debts. To address this issue, protocols often adopt a multi-oracle strategy, aggregating information from multiple data sources to improve accuracy, or set up backup oracles in case the primary data source fails, and also use time-weighted average pricing to filter out asset value spikes caused by manipulation or abnormal values.
Finally, we also need to consider security risks: in projects that have been attacked, the money market is usually the primary victim, second only to cross-chain bridges.
The code for managing the lending market is highly complex, and only a few protocols can proudly claim to have impeccable backgrounds in this area. At the same time, we have seen many protocols, especially forks of some complex lending products, encounter multiple security vulnerabilities when modifying or handling the original code. To mitigate these risks, protocols often take measures such as bug bounties and regular code audits, and strictly approve protocol modifications through rigorous processes. However, no security measures can be foolproof, and the possibility of vulnerability attacks is a persistent risk factor that a team must be vigilant about.
How to handle losses?
When a protocol suffers losses, whether due to failed liquidations resulting in bad debts or sudden events such as hacker attacks, there is usually a standard mechanism in place to share the losses. The approach of Aave can serve as a typical example.
Aave's Safety Module acts as a reserve mechanism to cover potential funding gaps in the protocol. Users can stake their AAVE tokens in the Safety Module and earn rewards, but if necessary, these staked tokens can be reduced by up to 30% to cover the shortfall. This serves as an insurance mechanism, and has recently been further strengthened by the introduction of stkGHO.
These mechanisms essentially provide users with "high risk, high return" opportunities and align user interests with the overall interests of the protocol.







