
The application of Blockchain technology has long surpassed the digital asset industry where it originated, as various organizations are actively exploring the potential and application scenarios of Blockchain in storing and managing different types of data.
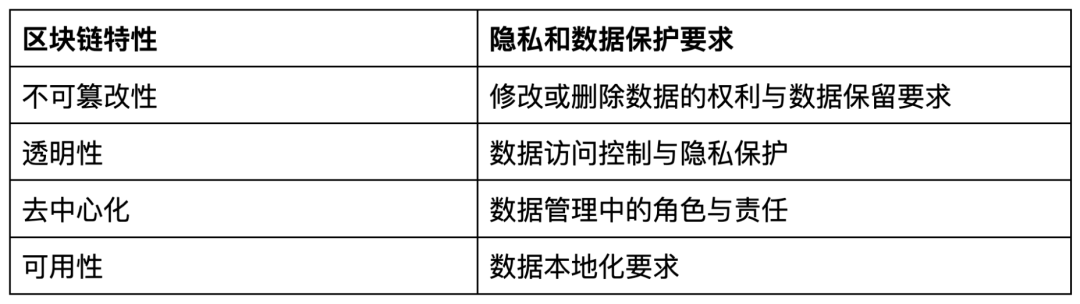
Blockchain has features such as immutability, transparency, decentralized data management, and high availability, which have attracted attention from industries ranging from finance to supply chain management and healthcare. However, these features also pose significant challenges in meeting compliance and regulatory requirements, including:
- Immutability: Once data is recorded on the Blockchain, it cannot be modified or deleted.
- Transparency: All network participants can view and verify the authenticity of the entire data.
- Decentralized management: Data is not controlled by any single entity, nor is it solely responsible for any particular entity.
- High availability: Data is replicated and stored on multiple nodes, making it accessible at all times.
Blockchain compliance is not just for the Web3.0 industry
Depending on the nature of the business and the type of data managed, modern Blockchain applications may be subject to different regulatory rules. In recent years, financial regulators around the world have been continuously issuing and updating relevant regulatory frameworks, which have received widespread media and public attention. However, companies must also comply with other regulations regarding the handling of personal identity data, medical records, business documents, digital credentials, and so on. This article will focus on exploring the impact of privacy and data protection regulatory frameworks on the use of Blockchain technology to manage personal and health data.
Core challenges within the privacy and data protection regulatory framework
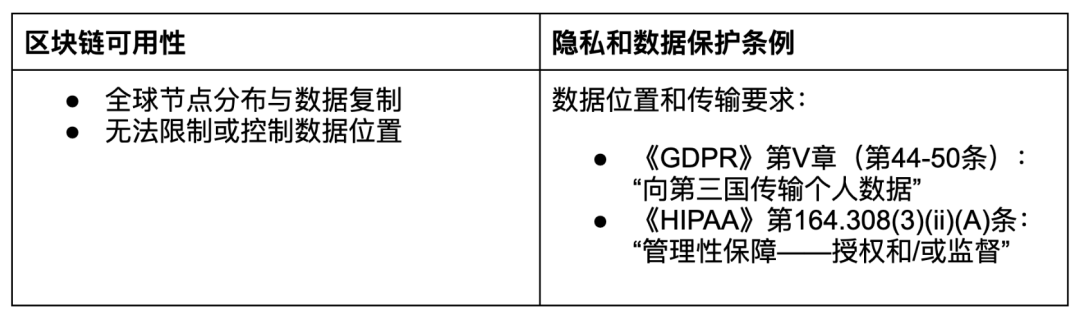
In the regulatory domain, there are many overlapping requirements between privacy and personal data protection (such as GDPR[1], CCPA/CPRA[2], PIPL[3], etc.) and health data protection (such as HIPAA[4]). This overlap is mainly due to the sensitivity of the relevant data, which requires similar requirements for data protection, security, and privacy.
Since these regulations were formulated before the widespread application of Blockchain technology, they do not explicitly mention Blockchain and have not directly addressed Blockchain-related issues. However, these regulations still apply to enterprises that use Blockchain technology to manage personal or health data.
Specifically, the core features of Blockchain pose some challenges in meeting data protection and privacy requirements:
In the following sections, we will delve into each challenge, analyze how enterprises can meet privacy and data protection requirements when using Blockchain, and how CertiK can provide assistance in this context.
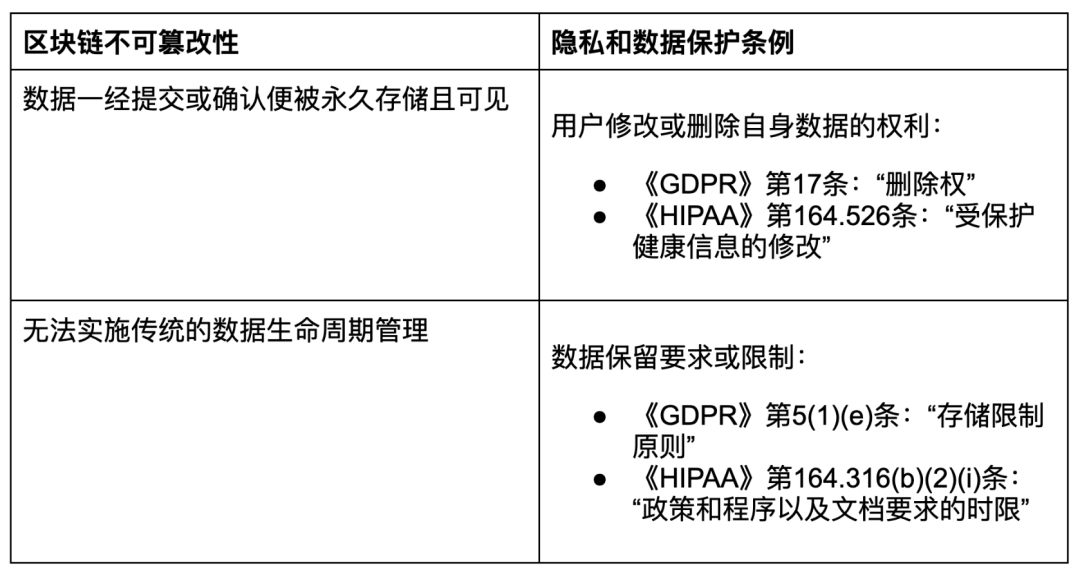
Immutability
The immutability feature of Blockchain poses several major compliance challenges, particularly in terms of limiting users' rights to modify or delete data, as well as related issues such as data storage requirements.
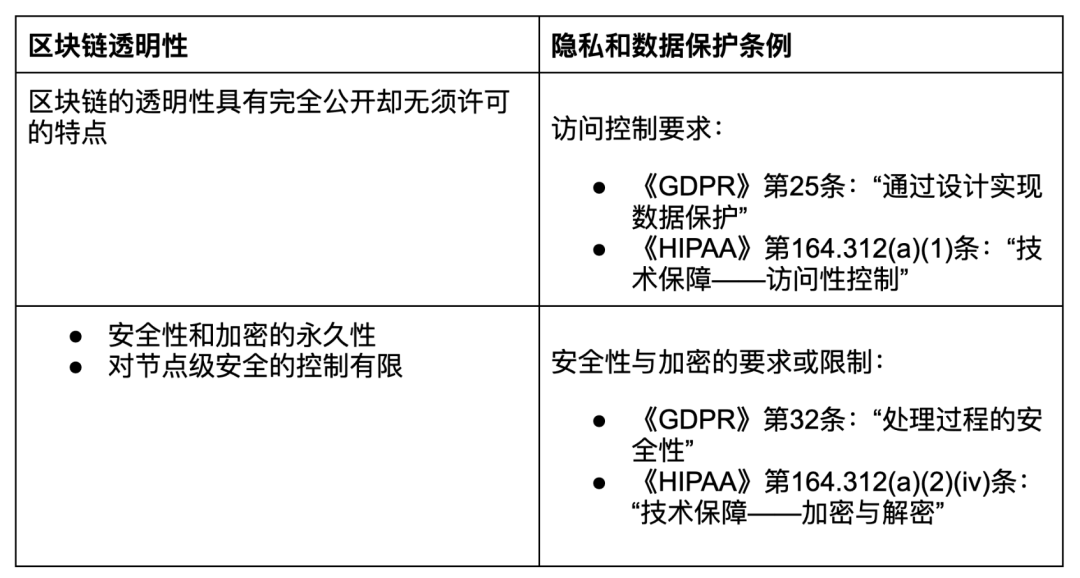
Transparency
The access control requirements aimed at protecting user privacy pose complex challenges in implementing Blockchain solutions.
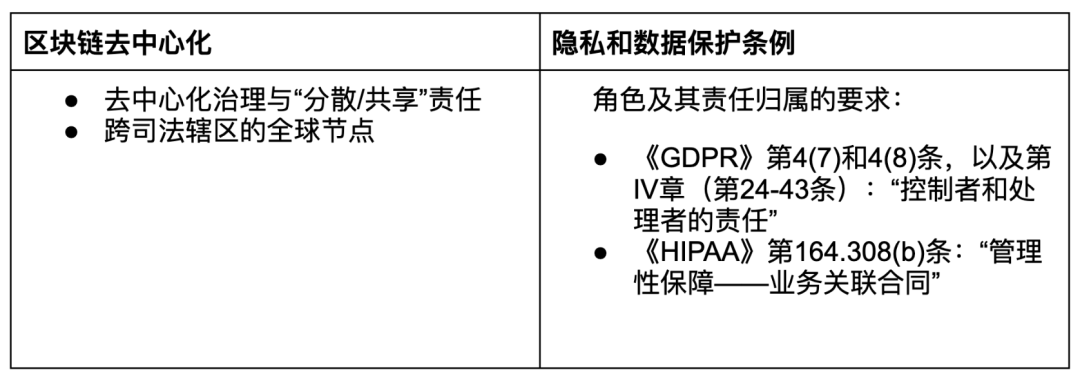
Decentralization
The decentralized nature of Blockchain, particularly in terms of governance, may conflict with regulatory requirements regarding roles and responsibilities.
Availability
The distributed nature of Blockchain nodes, often located in different geographical locations, poses significant challenges for the compliance of data residency and transmission.
Solutions
Hybrid Storage Model
The hybrid storage model is a key solution to balance the advantages of Blockchain and compliance requirements. These models strategically allocate data between on-Chain storage and off-Chain storage:
- Sensitive data is stored in traditional compliant databases.
- The Blockchain only stores references and verification proofs of the data.
- Modifications to sensitive data can be made in the off-Chain storage.
- The Blockchain retains an immutable audit trail.
With the adoption of a hybrid storage model, sensitive data is stored in traditional or off-Chain storage solutions, addressing the following challenges:
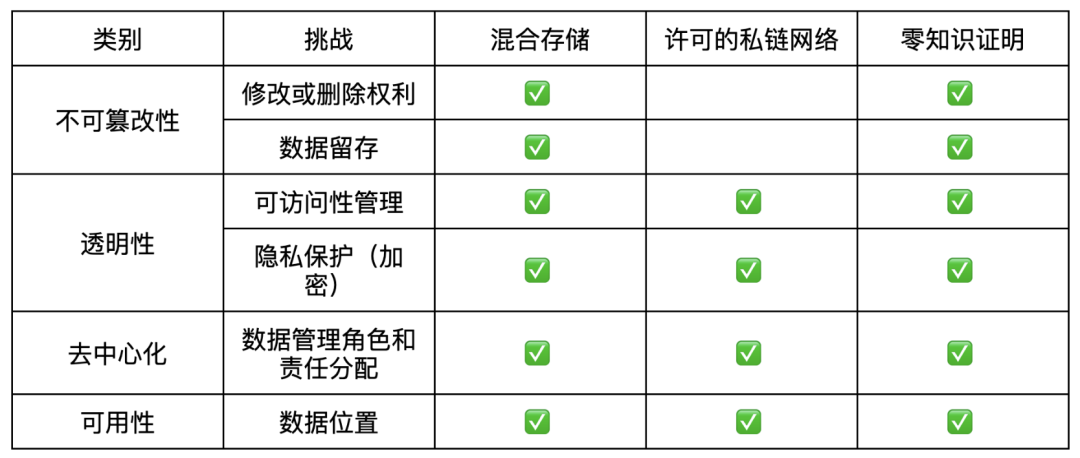
- Immutability: Off-Chain storage enables data to be deletable and modifiable, while maintaining data integrity. Additionally, retention policies can be implemented in the off-Chain data.
- Transparency: Enhanced security, access control, and encryption measures can be implemented and managed in the off-Chain storage for sensitive data.
- Decentralization: Traditional storage solutions can easily delineate roles and responsibilities.
- High availability: The location and jurisdiction of data storage can be effectively controlled.
For example, a healthcare provider can store patient records in a traditional HIPAA-compliant database, while using Blockchain to record access logs and maintain data integrity. This process allows them to modify or delete records as needed, comply with data retention policies, control data storage locations, and maintain an immutable audit trail. The Estonian e-Health[5] system is an application case of this model: patient records are stored in an off-Chain database, while using the KSI Blockchain to protect the access logs and ensure data integrity across the national healthcare network.
Permissioned Private Blockchain Network
Private Blockchain networks provide organizations with control over network participation, permissions, and data governance, while retaining the advantages of a distributed system:
- Authenticate and control network membership through identity verification and permissioning.
- Define data access and node operation rights based on role-based permissions.
- Configurable consensus mechanisms and governance rules.
- Control the geographical distribution of nodes.
This network solution addresses the following issues:
- Transparency: Data access can be granularly controlled to meet security and privacy requirements (further enhanced by the application of cryptographic techniques).
- Decentralization: Roles and responsibilities can be clearly assigned, such as the duties of data controllers/processors.
- High availability: The location and distribution of data can be effectively controlled.
A typical example is that a permissioned private Blockchain network can implement fine-grained access control for health-related data, ensuring patient privacy while supporting secure medical collaboration:
- Healthcare providers maintain control over patient records.
- Each participant can only access the authorized portions of medical records.
- Clinical partners have specific permission levels based on their roles.
- Patients can share records without exposing their full medical history.
For instance, Medicalchain[6] utilizes the permissioned architecture of Hyperledger Fabric to implement different access levels, allowing patients to control who can view their records, what specific information can be viewed, and the time range of access. Additionally, healthcare institutions like the Leeds Teaching Hospital Trust and Queen Elizabeth Hospital can securely exchange patient data while meeting regulatory requirements.
Zero-Knowledge Proofs (ZKP)
Zero-Knowledge Proofs can verify information without revealing the underlying data, providing a powerful solution to maintain privacy while meeting compliance requirements. No sensitive data is stored on the Blockchain, only the proofs used to verify the authenticity of the data. Key features include:
- Mathematical proof of data validity.
- Verify claims without revealing underlying data.
- Implement selective disclosure of information.
- Maintain data confidentiality during the verification process.
Assuming that sensitive data has been properly stored off-chain in accordance with data protection and privacy requirements, the following challenges can be addressed:
- Immutability: Data modification, deletion, and retention policies are handled off-chain, while maintaining the ability to verify the authenticity of data on-chain.
- Transparency: Support on-chain verification of data while protecting the confidentiality of sensitive data off-chain.
- Decentralization: The off-chain storage solution clearly defines the roles and responsibilities for sensitive data.
- High availability: The location and distribution of data depend on off-chain data storage, while the verification function can be implemented on-chain.
Financial institutions can implement the following functionalities through a KYC process based on zero-knowledge proofs:
- Customers can prove their identity requirements without exposing their original personal data.
- Banks can verify compliance without storing sensitive information.
- Identity verification results are stored on-chain while protecting privacy.
- Multiple institutions can verify the customer's status without repeated checks.
For example, Privado ID[7] (formerly Polygon ID) allows organizations to issue verifiable credentials that comply with W3C standards, and users can prove specific claims (such as KYC status) to verifiers without revealing underlying personal data. This process combines blockchain-based verification and zero-knowledge proof technology, addressing both compliance and privacy security.
Conclusion
The intersection of blockchain technology and regulatory compliance poses significant challenges, but emerging solutions provide practical and viable approaches to bridge this gap. The table below matches the key challenges with their corresponding solutions. It is important to note that the solutions mentioned in the table assume that the sensitive data stored off-chain has been managed in accordance with data protection and privacy requirements:
Key Points
- There is currently no single solution that can fully address all compliance challenges while hosting sensitive data on-chain and preserving the original characteristics and ideals of blockchain technology. Combining multiple approaches and considering specific business and operational requirements may be the best approach.
- Incorporating compliance into the development process from the beginning, rather than as an afterthought, can help determine the appropriate blockchain type (e.g., public/private, permissioned/permissionless) and any additional solutions required.
- Given that relevant regulations are still evolving and technical solutions are constantly developing, it is crucial to stay informed about the latest regulatory policy developments.
As blockchain technology and regulatory frameworks mature, organizations that can carefully combine solutions will have an advantage, as they can fully leverage the strengths of blockchain while maintaining compliance.
CertiK can provide solution support for enterprises adopting blockchain at various stages of development, including those with a need to manage personal and sensitive data. The services offered include:
- Analyzing infrastructure and data design or existing environments to identify applicable regulatory frameworks;
- Assessing infrastructure and data design or existing environments to identify information and communication technology (ICT) and regulatory risks;
- Proposing action plans to address ICT and regulatory risks;
- Determining suitable solutions to fully leverage blockchain technology while maintaining compliance.
[1] GDPR: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX:02016R0679-20160504
[2] CCPA/CPRA: https://leginfo.legislature.ca.gov/faces/codes_displayText.xhtml?division=3.&part=4.&lawCode=CIV&title=1.81.5
[3] PIPL: http://en.npc.gov.cn.cdurl.cn/2021-12/29/c_694559.htm
[4] HIPAA: https://www.hhs.gov/hipaa/for-professionals/privacy/laws-regulations/combined-regulation-text/index.html
[5] e-Health: https://e-estonia.com/solutions/e-health/e-health-records/
[6] Medicalchain: https://medicalchain.com/en/whitepaper/
[7] Privado ID: https://www.privado.id/





