Bybit was hacked for $1.5 billion, which may be the largest crypto theft in history, surpassing the Axie Infinity hack in 2022. The theft has caused a lot of panic in the market, with ETH prices fluctuating sharply in the short term, but there has not yet been a bank run like the FTX collapse.
Ironically, many investors had just recovered some of their losses from the FTX bankruptcy. "After 2.5 years, I finally received the FTX payout and deposited it into Bybit, and the next day Bybit's hot wallet was hacked," is the most widely circulated hell joke today, but the joke casts a shadow over the crypto industry.
Midnight Theft
On February 21 at 11 pm, crypto KOL Finish reported that according to on-chain data, a Bybit multi-signature address had transferred $1.5 billion worth of ETH to a new address.
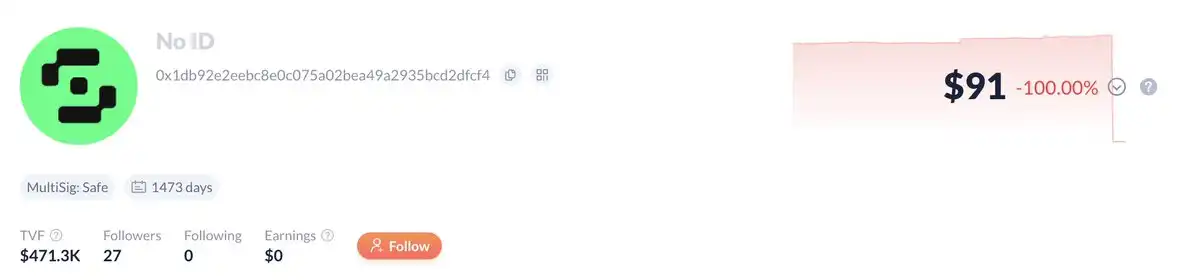
The funds reached the new address 0x47666fab8bd0ac7003bce3f5c3585383f09486e2, and then were transferred to 0xa4b2fd68593b6f34e51cb9edb66e71c1b4ab449e, where 0xa4 is currently selling stETH and mETH to exchange for ETH.
"The address is currently using 4 different DEXs, if they just swap LSD for native ETH, the trade execution will be very poor (high slippage). This scale is usually done through OTC, so it's very unusual."
Half an hour later, Bybit CEO Ben Zhou said that the ETH multi-signature cold wallet was attacked by impersonation, the smart contract logic was tampered with, causing the hacker to control the specific wallet and transfer all the ETH. He said that other cold wallets are safe, withdrawals are normal, and they are seeking assistance to track the stolen funds, and said "we will start a live broadcast soon to answer all questions!! Please continue to follow."
Related reading: Timeline | Bybit loses over 500,000 ETH, a loss of $1.5 billion
The Largest Theft in History?
According to EmberCN's monitoring, Bybit's ETH multi-signature cold wallet was hacked for 514,000 ETH, worth $1.429 billion. The hacker has already dispersed 490,000 ETH to 49 addresses (10,000 ETH per address). "There are also 15,000 cmETH being unstaked by the hacker (with an 8-hour waiting period, not sure if this can be intercepted)."
According to CoinMarketCap data, Bybit had $16.2B in reserve assets before the hack, and the $1.4B stolen assets accounted for 8.64%. This may be the largest crypto theft in history, accounting for 16% of all previous crypto hacks. The previous largest crypto theft was the Ronin Network (Axie Infinity) hack on March 29, 2022, where hackers stole about $620-625 million in cryptocurrencies, including 173,600 ETH and $25.5 million in USDC.
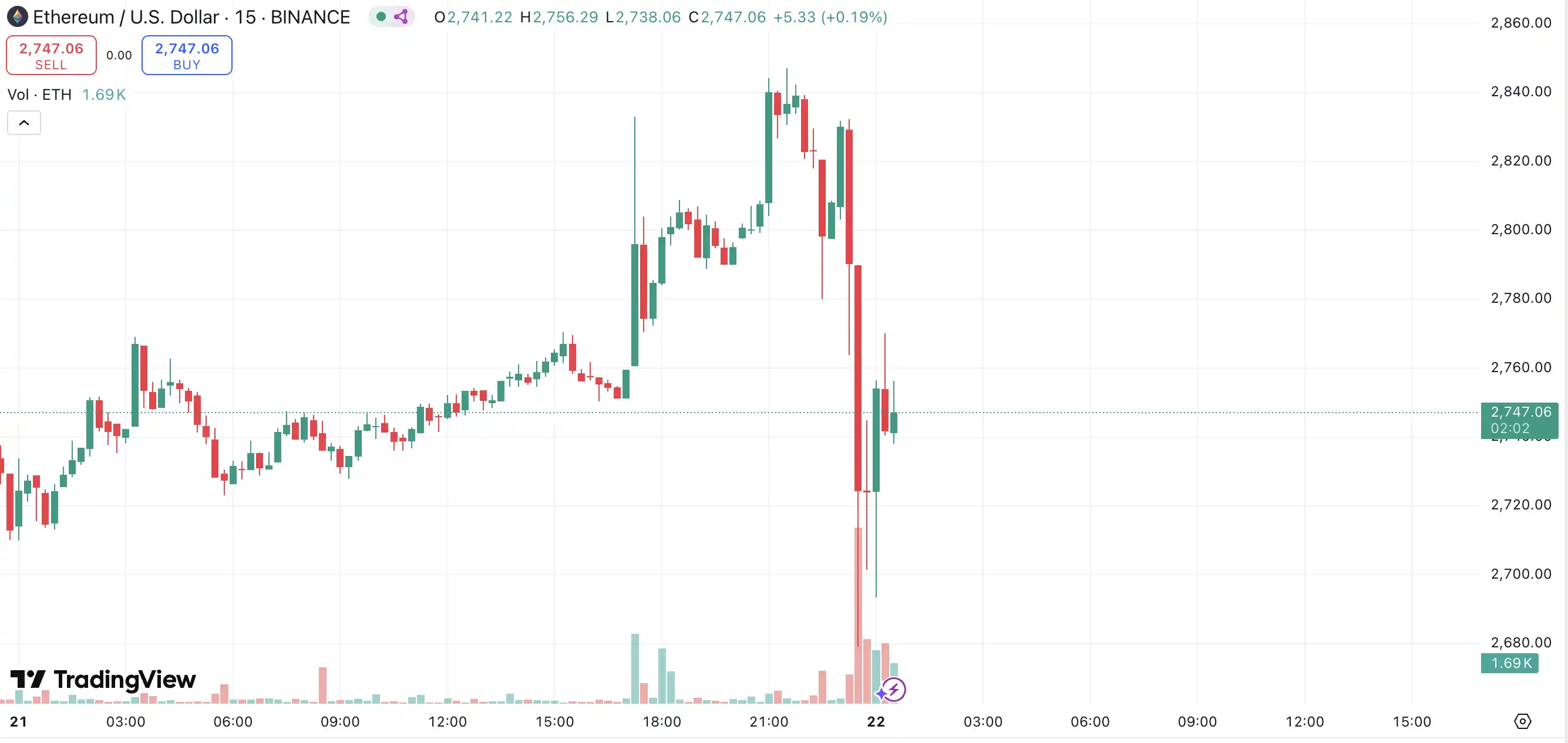
After the news of the Bybit hack broke, ETH briefly fell to around $2,600.
The only thing hacked was the ETH cold wallet, Bybit's hot wallet, warm wallet and all other cold wallets were not affected. According to community feedback, all withdrawals can be made normally, with withdrawal times within 20 minutes.
Some community members also asked ChatGPT and Grok about Bybit's annual revenue and profit estimates. Both gave similar calculation results: annual revenue of about $2 billion and annual profit of about $600 million.
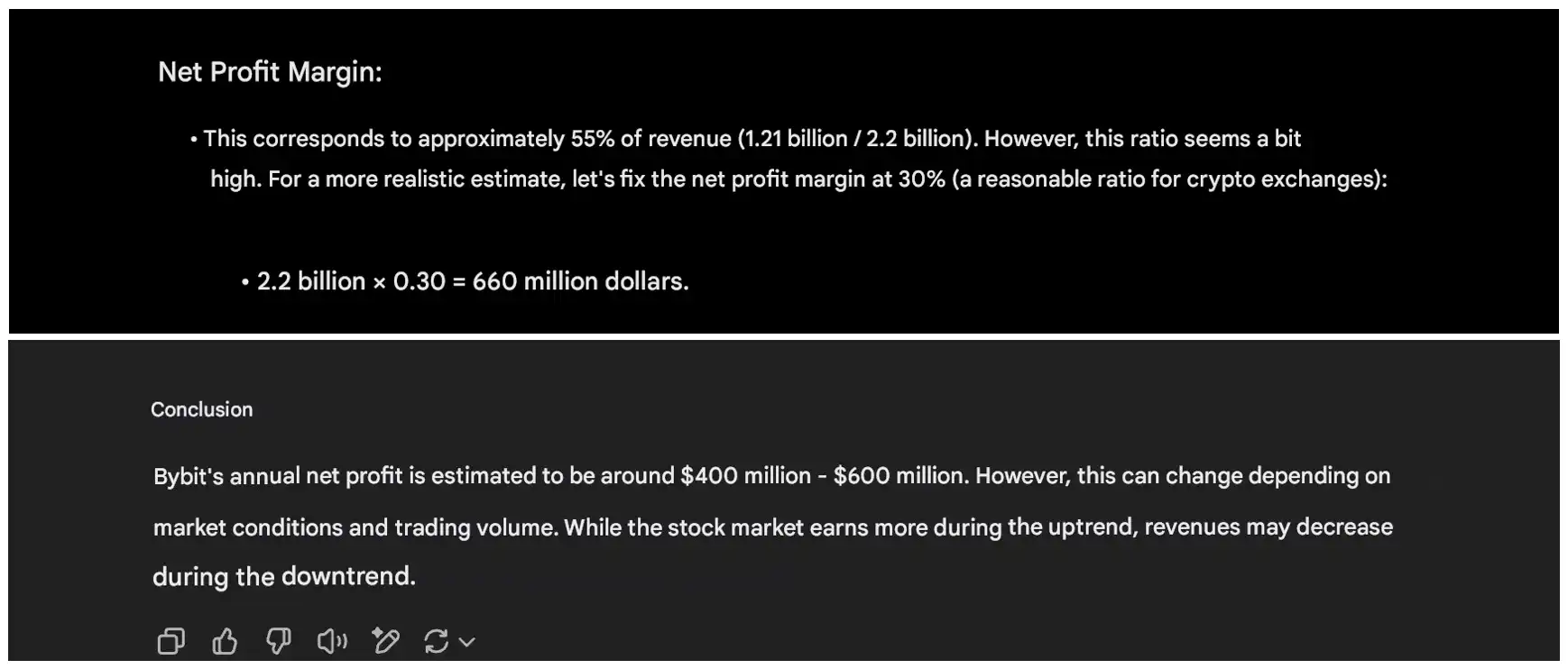
"Bybit still has the ability to pay, even if the losses from this hacking attack cannot be recovered, all customer assets are still maintained at a 1:1 ratio, and we can bear this loss," the words of Bybit's co-founder also gained more credibility.
Was the Multi-Signature Wallet Not Safe?
On February 22, Slowmist founder Yu Xian said that the Bybit hacking method is similar to that of North Korean hackers, "although there is no clear evidence yet, but from the way of doing Safe multi-signature and the current money laundering method, it looks like North Korean hackers."
At the same time, the founder of DefiLlama pointed out that the attack vector is similar to the hacking of WazirX, which is related to North Korea. Stay vigilant.
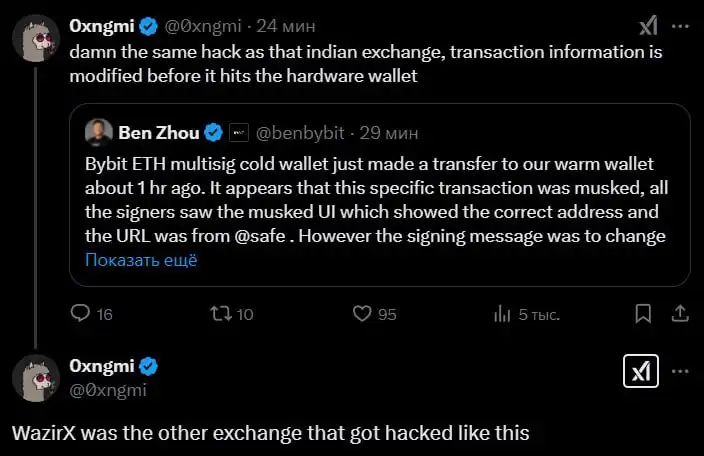
At 11:44 pm, in the announcement of Bybit's co-founder and CEO Ben Zhou, it showed: "Bybit's ETH multi-signature cold wallet was transferred to our hot wallet about 1 hour ago. It seems that this transaction was impersonated, all signatories saw the impersonated interface, showing the correct address, and the URL came from Safe."
But the signature information was to modify the smart contract logic of their ETH cold wallet. This allowed the hacker to take control of the specific ETH cold wallet they signed, and transfer all the ETH in the wallet to this unconfirmed address.
Further investigation by Slowmist found more details about the vulnerability:
1) A malicious implementation contract was deployed at UTC 2025-02-19 7:15:23:
https://etherscan.io/address/0xbdd077f651ebe7f7b3ce16fe5f2b025be2969516…
2) At UTC 2025-02-21 14:13:35, the attacker used the signatures of the three owners to replace the implementation contract of Safe with the malicious contract:
https://etherscan.io/tx/0x46deef0f52e3a983b67abf4714448a41dd7ffd6d32d32da69d62081c68ad7882…
3) The attacker then used the backdoor functions "sweepETH" and "sweepERC20" in the malicious contract to steal the hot wallet.
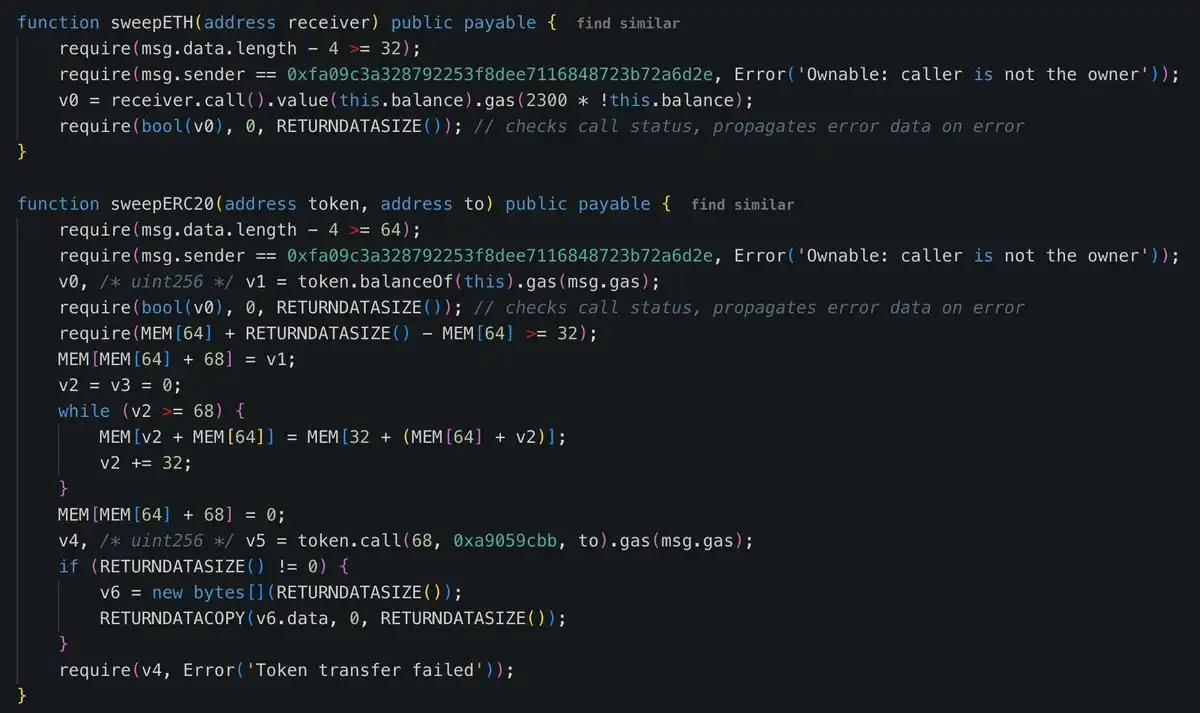
This method is similar to the Radiant Capital theft in October 2024:
At that time, the security vulnerability at Radiant Capital led to the theft of about $50 million. The attacker used malware to infect the devices of at least three core developers who were long-trusted DAO contributors and used hardware wallets for transactions. The hacker manipulated the front-end of Gnosis Safe, causing the victims to unknowingly approve the malicious transactions when signing.
The attack process was that the developer's device was implanted with highly sophisticated malware, causing them to inadvertently approve the hacker's malicious operations when signing transactions. The Gnosis Safe front-end did not show any abnormalities, so the victims could not detect the tampered transactions. The hacker took advantage of the common phenomenon of failed transactions (such as Gas fee fluctuations, synchronization delays, etc.) to induce the developers to re-sign multiple times, thereby obtaining multiple valid malicious signatures. Although the transactions were simulated and reviewed by tools like Tenderly, the malware manipulation of the developer's device led to all the check results still showing normal, causing the attack to go undetected.
Related reading: Radiant Capital Autopsy
All the fingers seem to be pointing to the Safe multi-signature wallet.
Safe is the most widely used multi-signature wallet in the Ethereum ecosystem, and is the wallet of choice for large holders. When Safe issued tokens this year, the top 100 airdrop addresses were almost all project parties or institutions, including OP, Polymarket, Drukula, Worldcoin, Lido and others. Related reading: Safe is about to trade, a look at its token economics and ecosystem
Initially, Safe's audience was more DAO and crypto project parties. But as the crypto industry entered the next stage, traditional finance, traditional institutions, family funds, and old money gradually entered the market, and more and more traditional institutions began to use the multi-signature wallet Safe, such as the Trump family.
The design of Safe has greatly improved the security of fund management. Through the multi-signature mechanism, funds are stored in the smart contract address, and transactions can only be executed when the preset number of signatures (such as 3/10) is met. This mechanism effectively reduces the risk of single-point failure, and even if the private key of one signature address is leaked, the attacker will find it difficult to obtain enough signatures to complete the transaction.
Currently, the Safe security team states: "There is no evidence that the official Safe frontend has been compromised. But out of caution, Safe{Wallet} has temporarily suspended certain functions." They are working closely with Bybit to conduct ongoing investigations.
Some community members have launched mockery of Safe: multi-signature is just a "covering one's ears to steal a bell" decoration. At the same time, there are also many industry practitioners who have reflected and expressed concerns about the industry: "If even multi-signature wallets are not secure, then who will take this industry seriously?"
The investigation of the current incident is still ongoing, and Mars Finance will continue to follow up.








