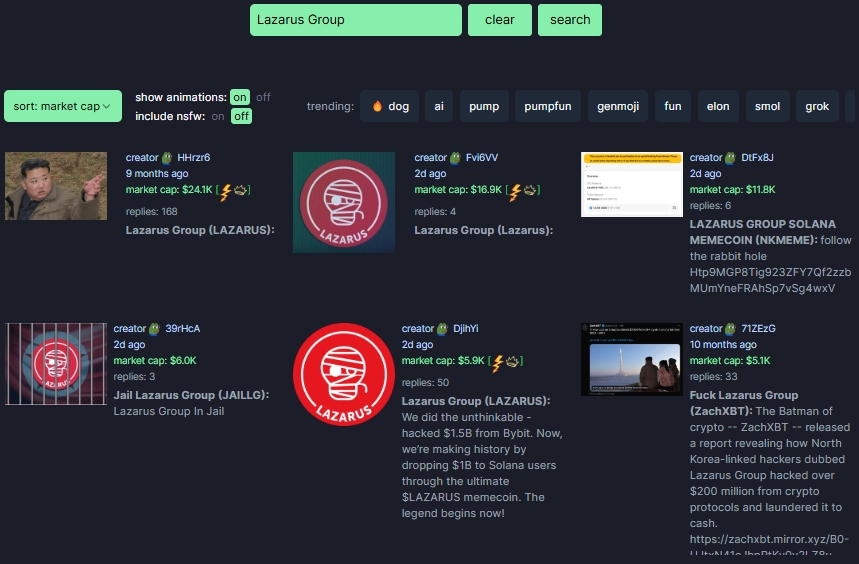
After a weekend of settling, the money laundering methods of the attackers on the cryptocurrency exchange BlockTempo have also attracted strong attention from the cryptocurrency community. According to Solscan monitoring, the Bybit hackers seem to be using the pump.fun platform to issue MEME coins for money laundering.
The data shows that the hackers transferred about 60 SOL funds to the address 9Gu8v6…aAdqWS, which subsequently issued a MEME coin called "QinShihuang". The trading volume of this token has now exceeded $26 million, with a market capitalization of $2.2 million, but its liquidity is only $200,000.
After being discovered as a suspected money laundering method for the attackers, pump.fun has removed MEME coins that may be related to the North Korean hacker group Lazarus Group from the front end, to prevent more assets from being laundered. However, this also exposes the control issue of the pump.fun platform. Although the platform claims to be decentralized, it actually has the right to manage the listed assets and decide which tokens appear on the platform, which is inconsistent with its self-proclaimed fully decentralized spirit.
But from the perspective of the victims of BlockTempo, we also hope that these stolen assets can be frozen or even recovered. How to balance this is also an area that the cryptocurrency industry needs to have more discussions in the future.
Bybit Hacker Fund Flow and Cross-Chain Laundering
According to the tracking by BeosinTrace, the Bybit hackers started transferring large amounts of funds to multiple settlement addresses from February 23, 2025, involving 115 addresses, totaling 11,693.48 ETH (about $160 million). These funds flowed to platforms including OKX Dex and THORChain: Router, with the specific details as follows:
- From February 22 to 23, the contract address 0xf3de (OKX Dex. Aggregation Router) received 6,624.25 ETH;
- The contract address 0xd37 (THORChain: Router) received 7,662.8 ETH;
- The address 0xf1da (Exch exchange) received 3,570.62 ETH;
- The contract address 0xfc9 (OKX Dex. Xbridge) received 2,541.56 ETH.
The flow of these funds shows that the Bybit hackers are actively using decentralized exchanges and bridge protocols to disperse the funds, trying to obscure the source of the funds and increase the difficulty of tracking.
Hackers Still Hold Over 460,000 ETH
According to the on-chain analyst Yu Jin's observation, after the incident broke out, the Bybit hackers have used multiple cross-chain platforms such as Chainflip, THORChain, and LiFi to convert about 37,900 ETH (worth over $106 million) into other assets, including BTC. Currently, their address still holds about 461,491 ETH (worth about $1.29 billion), and the total amount of ETH stolen and transferred from Bybit has reached 499,395 ETH (worth about $1.4 billion).