Event Background
On February 22, 2025, Bybit, the world's second-largest cryptocurrency exchange, announced that its offline Ethereum cold wallet was hacked, resulting in the theft of approximately $1.5 billion worth of Ether (ETH) and related assets. This incident has been viewed by blockchain security experts as the largest cryptocurrency theft in history, and possibly one of the largest single thefts in global financial history.

According to data from blockchain security firm Arkham Intelligence, approximately 400,000 ETH (around $1.12 billion), 90,000 stETH (around $253 million), and other ETH derivatives were stolen, with some of the assets already being transferred and liquidated. This attack caused the price of Ether to drop by 6.7% at one point, while Bitcoin fell by around 3%.

Hacker Techniques and Attack Process
This hacker attack demonstrated an extremely high level of technical capability and meticulous planning. Bybit CEO Ben Zhou stated on X (Twitter) that the hackers manipulated the smart contract logic of the ETH cold wallet, causing the exchange's multi-signature cold wallet (Cold Wallet) to lose its original protection function, ultimately transferring all assets to unknown addresses.

Specifically, the attack process was as follows:
- Infiltrating the cold wallet management system: The hackers may have obtained the multi-signature signing permissions through internal vulnerabilities or social engineering attacks (such as phishing attacks).
- Manipulating the smart contract logic: The hackers modified the smart contract of the cold wallet, allowing the assets in the wallet to be withdrawn by unauthorized addresses.
- Transferring the assets: Once they controlled the cold wallet, the hackers quickly transferred the funds to multiple unknown addresses and liquidated them through decentralized exchanges (DEXs).
- Money laundering: Some of the funds were transferred through mixing services (such as Tornado Cash) or cross-chain bridges in an attempt to obscure the flow of funds.
Security experts believe that this may have been the work of the North Korean hacker group Lazarus Group, as they have previously attacked cryptocurrency exchanges multiple times and used similar methods to steal funds.
Bybit's Response and Community Reaction
After the hacker attack occurred, Bybit CEO Ben Zhou immediately went live on X to explain the incident to the community. His transparency and responsible attitude were widely praised by users.

However, despite Bybit's assurance of customer fund safety, a large number of users chose to withdraw their assets. According to the data, Bybit processed 350,000 withdrawals within 24 hours, resulting in a net outflow of $2.485 billion. The market was once concerned that a bank run might occur.
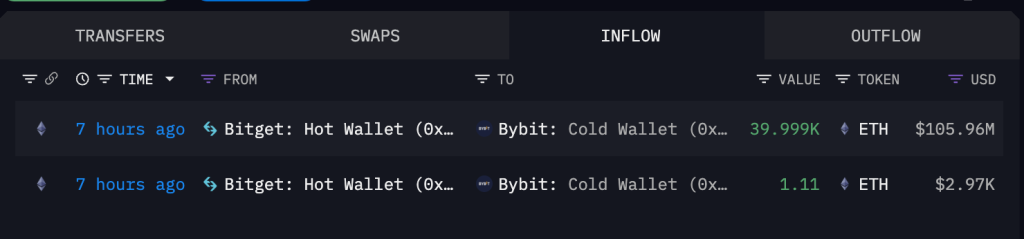
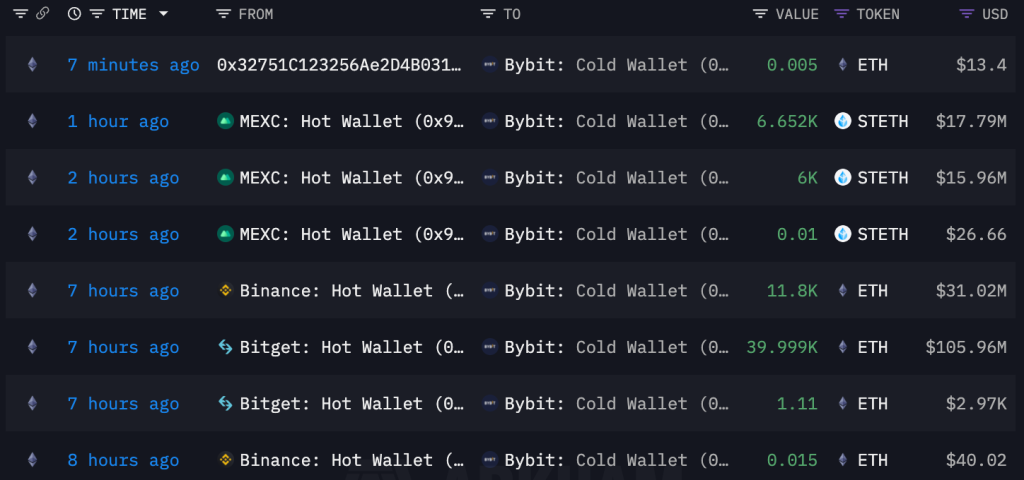
To address the liquidity pressure, Bybit quickly mobilized funds and received financial support from exchanges such as Bitget, Binance, and MEXC. Bitget even unconditionally provided 40,000 ETH (about $106 million) to help Bybit stabilize its liquidity.
Impact on the Market
Ethereum Market Volatility
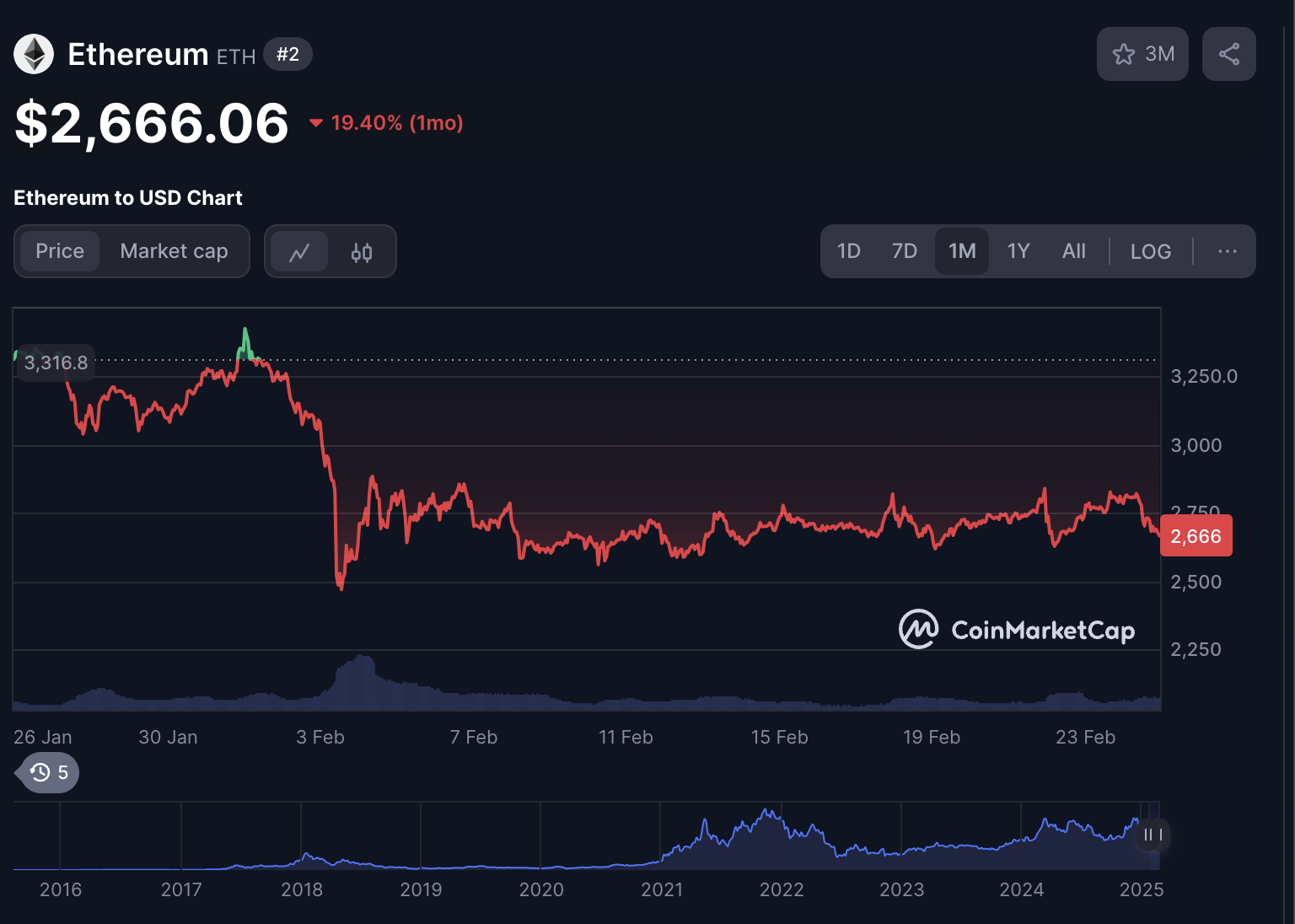
The main assets stolen were Ether, so the market price of ETH was directly affected. After the incident, the price of Ether fell by about 6.7% in the short term, but as Bybit and other institutions mobilized funds, the price quickly rebounded to around $2,800. However, as the hackers are still liquidating ETH, ETH may face some selling pressure in the short term.
Impact on the Altcoin Market
The overall cryptocurrency market is still in a bull market cycle, but this incident has had a certain negative impact on the Altcoin market. As ETH is still the core asset of the DeFi and Altcoin markets, market sentiment may remain depressed in the short term.
Impact on Exchange Reputation and Regulation
Although this incident has dealt a severe blow to Bybit, unlike the FTX collapse, Bybit still has sufficient capital reserves to bear the loss. Therefore, while the market's trust in Bybit has been shaken, it has not reached an irreversible stage.
On the other hand, this incident may accelerate the regulatory authorities' efforts to strengthen the supervision of centralized exchanges (CEXs), requiring them to improve their security protection measures. Some exchanges under strong regulation, such as Coinbase, may gain more market share as a result.
Security Recommendations for Cryptocurrency Users
Private Key Management and Decentralized Wallets
This incident once again reminds us: "Not Your Key, Not Your Coin" - if your assets are stored on an exchange, then you do not truly own them. Users are advised to:
- Use hardware wallets (such as Ledger, Trezor) to store large amounts of funds.
- Preferably use decentralized wallets (such as MetaMask, Trust Wallet).
- Do not store all your funds on exchanges, and should manage your risks accordingly.

Exchange Selection and Security Checks
- Prioritize exchanges with good security mechanisms, such as multi-signature wallets and proof-of-reserve (PoR) mechanisms.
- Regularly check if the exchange has any suspicious transaction records, and immediately withdraw your funds if you find any suspicious activities.
- When a security incident occurs on an exchange, do not panic and sell off your assets, but focus on the official announcements and make rational judgments.
Conclusion
Bybit's $1.5 billion hacker attack incident has become the largest theft in the history of cryptocurrency. The hackers' attack methods were extremely sophisticated, using vulnerabilities in the multi-signature wallet and manipulating the smart contract to successfully steal a large amount of assets.
However, Bybit's rapid response after the incident, including the CEO's transparent communication, the smooth handling of the massive withdrawals, and the support from other exchanges, have gradually stabilized market confidence.
Although this incident has had a certain impact on ETH and the overall market, it has not triggered a liquidity crisis similar to the FTX collapse. Cryptocurrency investors should learn from this incident, strengthen their own security awareness, ensure the safety of their assets, and appropriately diversify their risks to cope with potential future security challenges.