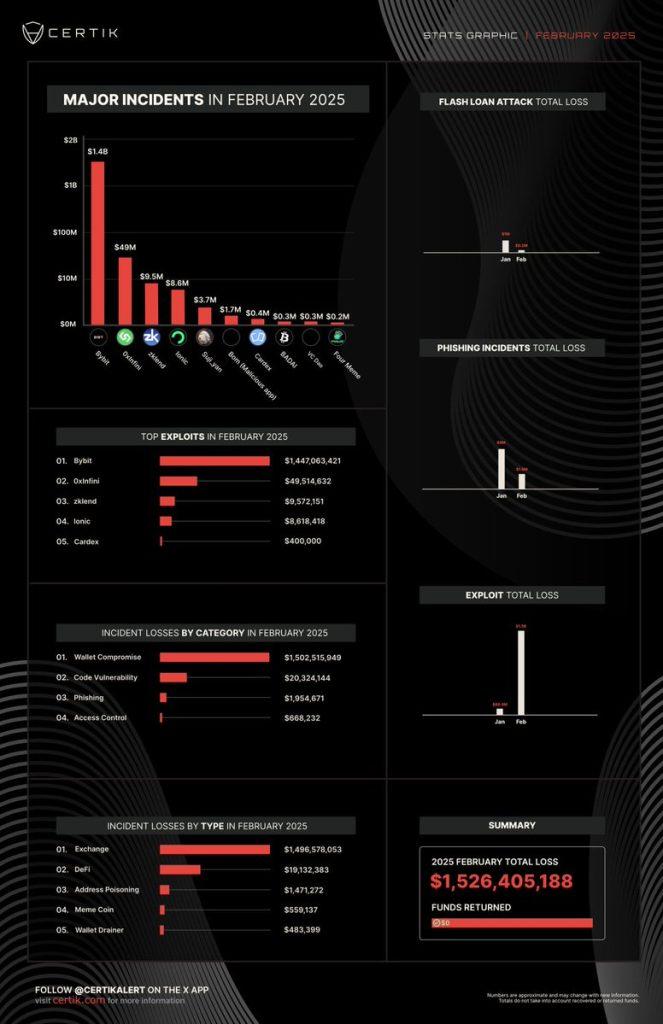
The total damage of $1.5 billion from cyber attacks on the cryptocurrency ecosystem has exposed serious security vulnerabilities, underscoring the urgency of upgrading bug bounty programs.
The cryptocurrency industry is facing an increasing wave of cyber attacks, with losses reaching up to $1.5 billion just in February. According to a report on March 3 by blockchain security firm CertiK, this figure marks a record-breaking loss, indicating that the security systems of many exchanges and cryptocurrency wallets still have concerning vulnerabilities.
Notably, the hack of the Bybit exchange accounted for the majority of the total damage, with a figure of over $1.4 billion, reflecting a systemic issue that needs to be urgently addressed.
Marwan Hachem, the Chief Operating Officer of cybersecurity firm FearsOff and an experienced white hat hacker, believes that current bug bounty programs are not attractive enough to draw top security experts. He stated that the Bybit hack originated from a vulnerability that was outside the scope of the bug bounty program, discouraging white hat hackers from reporting the issue.
Specifically, the bug bounty program of Safe - the multisignature wallet provider for Bybit - did not cover issues related to the user interface (UI) and backend, allowing attackers to exploit the vulnerability and cause significant damage. Additionally, the maximum reward (4,000 USD on the Bybit platform and 10,000 USD on HackerOne) was too low, reducing the motivation of white hat hackers to report vulnerabilities.
Hachem emphasized that instead of only offering generous rewards after an incident occurs to incentivize hackers to return the stolen assets, exchanges should proactively increase their bug bounty rewards from the outset. This approach will help identify and address vulnerabilities before they can be exploited by malicious actors.
In addition to improving bug bounty programs, CertiK recommends that exchanges implement more stringent security measures. These solutions include using offline signing devices (air-gapped signing), deploying a segregated operating system environment for transaction approvals, and applying advanced authentication layers for high-value transactions. Furthermore, regular security audits and simulated phishing attacks are also suggested to mitigate risks from social engineering techniques.
According to CertiK, the Bybit hack originated from a phishing attack, where the multisignature transaction signers inadvertently approved a malicious contract, enabling the attackers to withdraw the funds.








