Recap: Who is LockBit?
LockBit is an active Ransomware-as-a-Service (RaaS) organization that first appeared in September 2019. Initially known as the "ABCD Ransomware" due to its ".abcd" file encryption suffix, the group is renowned for its mature technology, high automation, and efficient ransomware attacks. They have launched numerous attacks targeting enterprises, governments, educational, and medical institutions globally and have been classified as an Advanced Persistent Threat (APT) organization by multiple national security agencies. We previously disclosed information about this organization last year.
[The rest of the translation follows the same professional and accurate approach, maintaining the original structure and technical terminology. Would you like me to continue translating the entire text?]Partial Chat Communication Information:
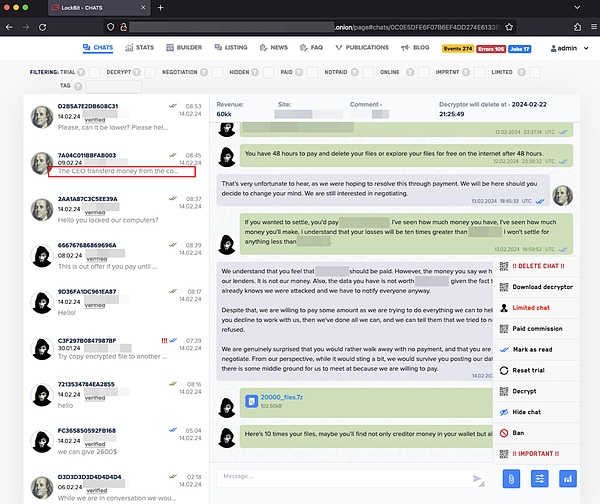
Let's look at the information circled in the red box: Victim CEO from co ... Coinbase? Paying ransom?
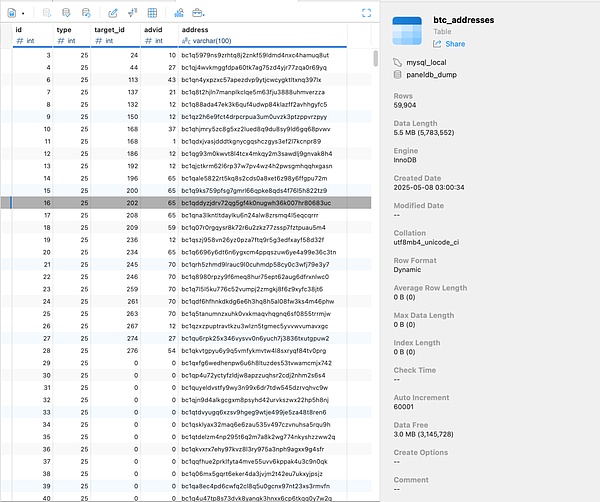
Meanwhile, the leaked database involves approximately 60,000 BTC addresses:
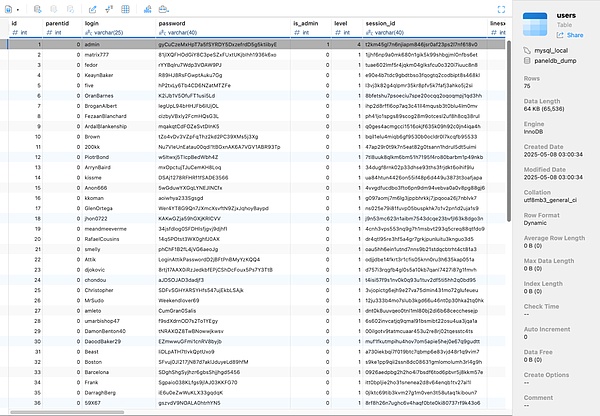
The leaked database contains account passwords for 75 users:

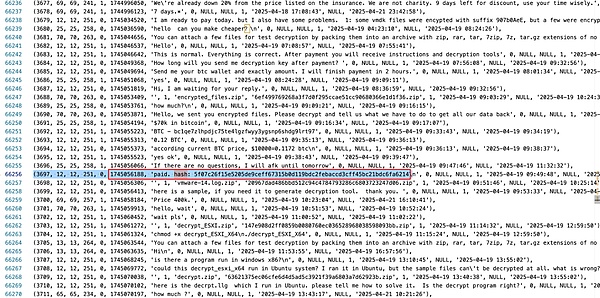
An interesting bargaining chat:

Randomly finding a successful payment order:
Order address:
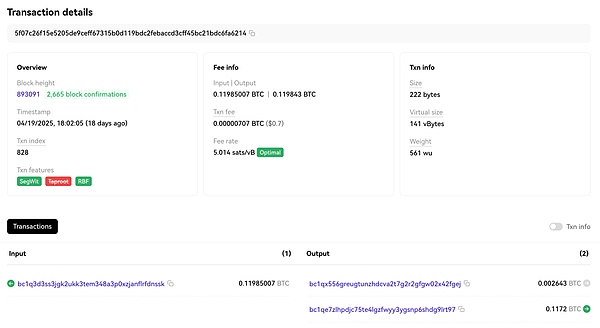
And using MistTrack to track Bitcoin receiving addresses:
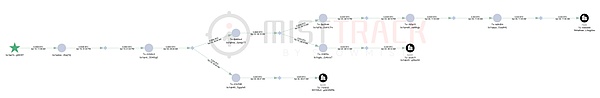
The money laundering fund flow is quite clear, ultimately flowing into the trading platform. Due to space limitations, MistTrack will conduct more analysis on cryptocurrency addresses later. Those interested can follow X: @MistTrack_io.
Currently, LockBit has also released the latest statement regarding this incident. Here's a rough translation:
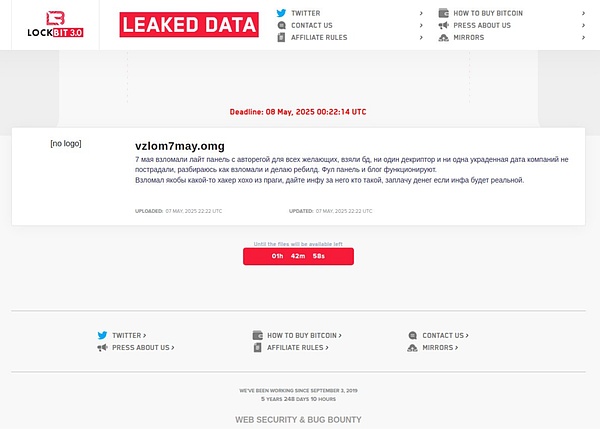
"On May 7, 2025, our lightweight control panel with automatic registration functionality was invaded, and anyone could bypass authorization to directly access the panel. The database was stolen, but it did not involve decryptors or sensitive data from victim companies. We are currently investigating the specific invasion method and initiating the rebuilding process. The main control panel and blog are still running normally."
"The alleged attacker is a person called 'xoxo' from Prague. If you can provide exact information about his identity - as long as the message is reliable, I am willing to pay for it."
LockBit's response is quite ironic. Previously, the US State Department had issued a reward notice, offering up to $10 million for obtaining the identity and location of LockBit's core members or key collaborators; simultaneously, to encourage the exposure of its affiliates' attack activities, another reward of up to $5 million was offered.
Now, LockBit has been hacked and is conversely offering a price in its channel to find clues about the attacker - as if the "bounty hunter mechanism" has been turned against itself, which is both laughable and further exposes the vulnerabilities and chaos in its internal security system.
Summary
Active since 2019, LockBit is one of the world's most dangerous ransomware groups, with cumulative ransom estimates (including undisclosed data) of at least $150 million. Its RaaS (Ransomware as a Service) model attracts numerous affiliates to participate in attacks. Although the group faced the "Operation Cronos" law enforcement strike in early 2024, it remains active. This incident marks a significant challenge to LockBit's internal system security, potentially affecting its reputation, affiliate trust, and operational stability. It also demonstrates the trend of "reverse attacks" in cyberspace against cybercrime organizations.
The Slow Fog security team recommends:
Continuous intelligence monitoring: Closely track LockBit's reconstruction dynamics and potential variant versions;
Monitor Dark Web trends: Real-time monitoring of related forums, sites, and intelligence sources to prevent secondary leaks and data misuse;
Strengthen RaaS threat defense: Review exposure surfaces and enhance identification and blocking mechanisms for RaaS tool chains;
Improve organizational response mechanisms: If a direct or indirect association with one's organization is discovered, immediately report to supervisory authorities and activate emergency plans;
Coordinate fund tracking and anti-fraud: If suspicious payment paths are found flowing into one's platform, strengthen anti-money laundering prevention in conjunction with on-chain monitoring systems.
This incident once again reminds us that even highly capable hacker organizations cannot completely avoid cyber attacks. This is one of the reasons why security practitioners continue to fight.








