Written by Daii
TL;DR
Blue Hook "Deputy Editor of CoinDesk" invited me to record a podcast → I almost installed a phishing app → I hesitated for 5 seconds to save my wallet.
The real 0-Day lies in human nature: authority worship + time pressure = infinitely reusable vulnerabilities; 40%+ of global encryption losses are caused by script fishing.
Minimum defense line = "5-4-3-2-1" countdown: stop for 5 seconds, raise 1 question, check the source once - no matter how skilled you are, you have to rely on this second to be awake.
I was going to talk to you about the third part of the Decentralization Trilogy today, but I’m sorry, it has to be postponed for a while. Because in the past few days, I encountered a major event that almost changed my destiny——
I was almost scammed, and almost without even realizing it.
Last Friday morning, I turned on my computer as usual. X (formerly Twitter) prompted me that I had received a private message. I clicked on it and saw the identity of the other party that immediately attracted me:
The profile picture is formal, with a blue check mark, and the ID is: Dionysios Markou, who claims to be the deputy editor-in-chief of CoinDesk.
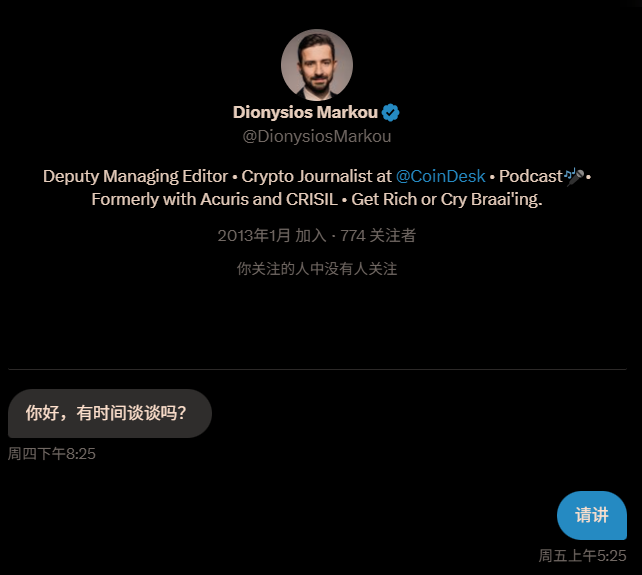
During the conversation, he told me:
I work at @CoinDesk and we'd like to do a series of interviews with different members of the web3 community about the crypto community in Asia. If you don't mind, we'd like to invite you to be our guest.
We plan to record a podcast and publish it on our website, Spotify, and other platforms.
This episode will delve into topics such as the future market of Bitcoin/Ethereum/Solcoin, MEME market, DeFi and web3 Asian projects.
Could you please let us know if you have time?
The content was concise and professional, and the format was completely in line with the common external invitations in the crypto media circle. I thought: CoinDesk? It's a veteran media in the industry, I'm very familiar with it.
I agreed almost without hesitation. Isn’t it the most ideal scenario for me to be a guest interviewer and talk about Bitcoin, Ethereum, Web3 and MEME projects?
We have agreed to connect online this Monday (May 12th) at 10pm.
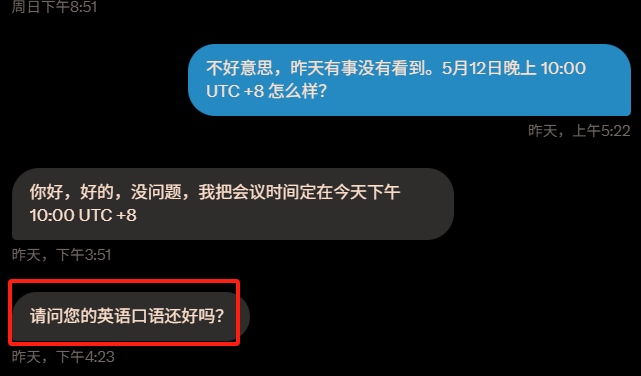
Please pay attention to the picture above. The other party sent a sentence: "Excuse me, how is your spoken English?" This sentence will become an important premise for me to be deceived.
At 9:42 pm on Monday, the other party greeted me at X and was ready to start the video call.
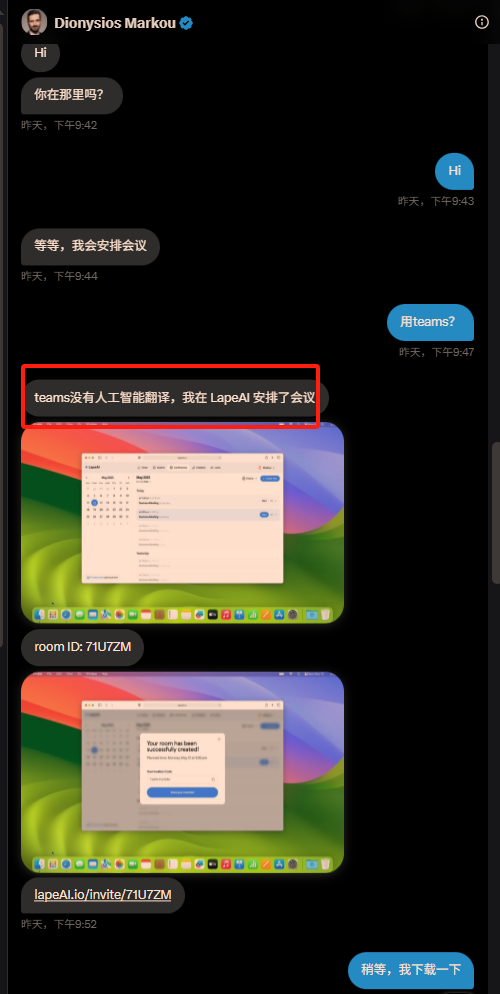
I suggested using Teams, but the other party said that Teams did not have artificial intelligence translation and suggested using LapeAI, which would allow for barrier-free Chinese-English conversations. They also took a screenshot to tell me that it was ready and sent me the room number and invitation link, as shown above.
Although I have never used LapeAI, the other party's reason is also reasonable. For safety reasons, I did not click on the link given by the other party, but went directly to Google to search for LapeAI and found the following website.
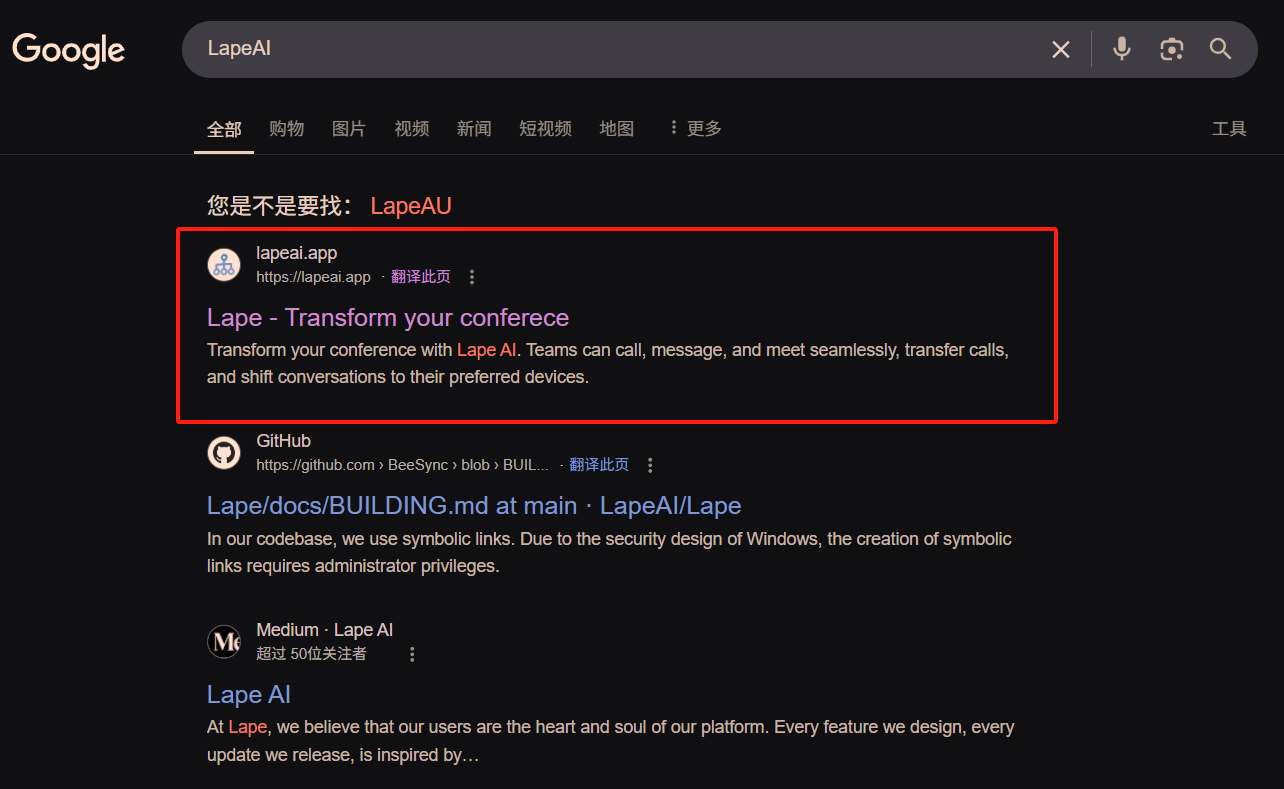
I was shocked when I opened it. The Chrome browser immediately reported an alarm, saying that this was a phishing website.
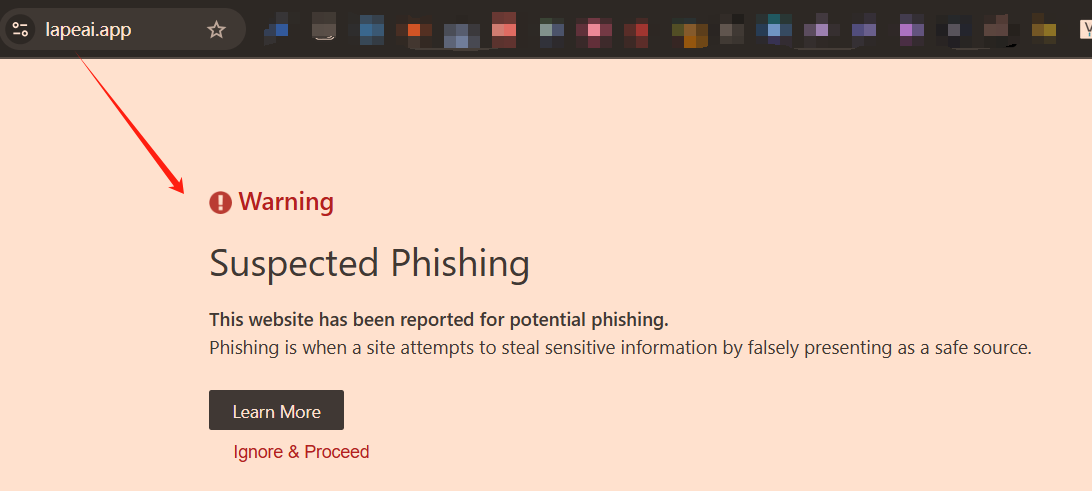
But after looking at the domain name carefully, the other party gave me LapeAI.io, and the result of Google search was Lapeai.app. The suffixes are different, and they are two different websites. I directly entered Lapeai.io in the address bar, and sure enough, there was no alarm, as shown below.
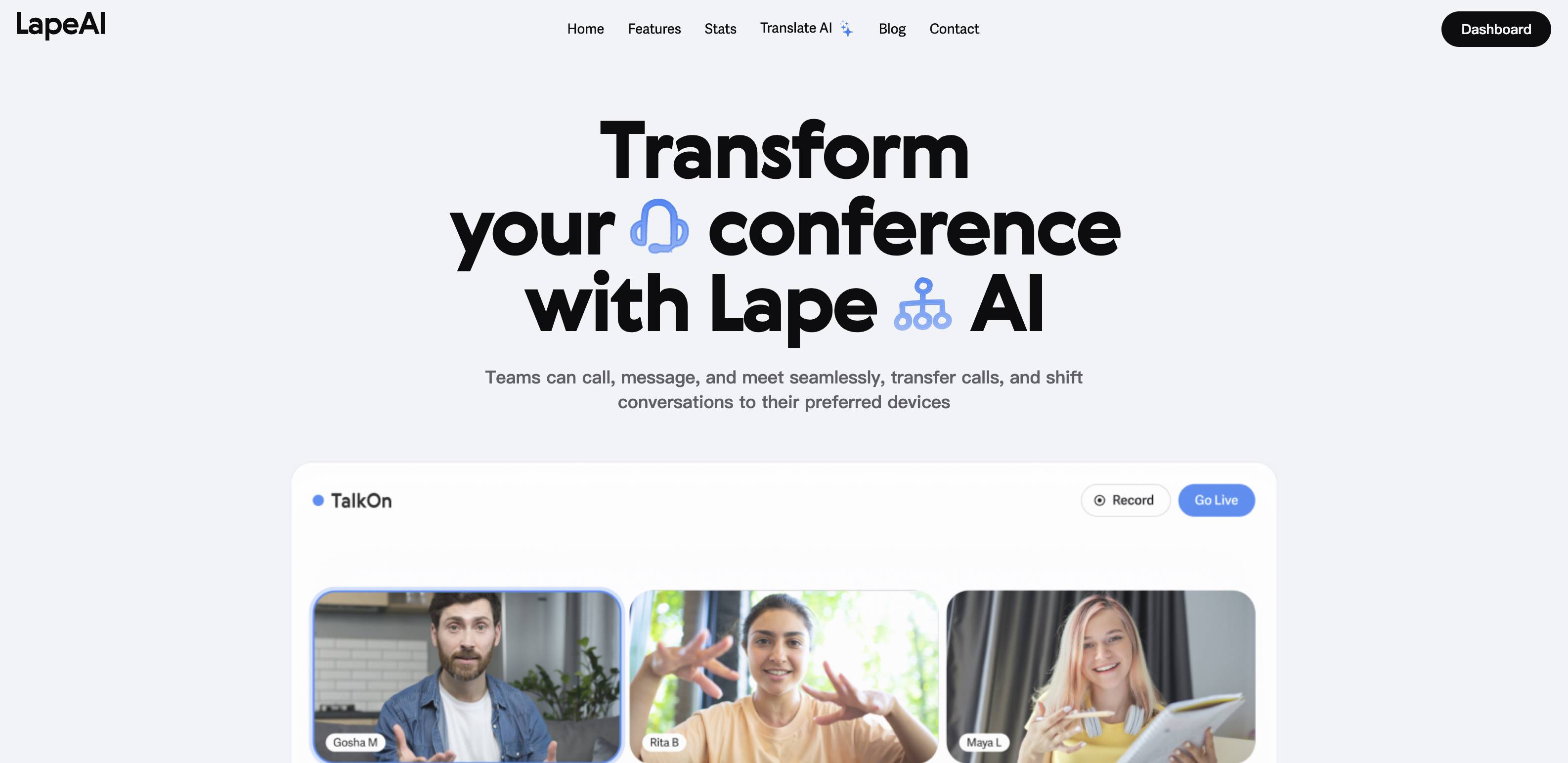
Everything seemed normal, so I registered an account and filled in the other party's invitation code. Note that LapeAI.app and LapeAI.io are actually the same website. It's just that the .app one was discovered, so they applied for a new .io. You will understand it if you read on.
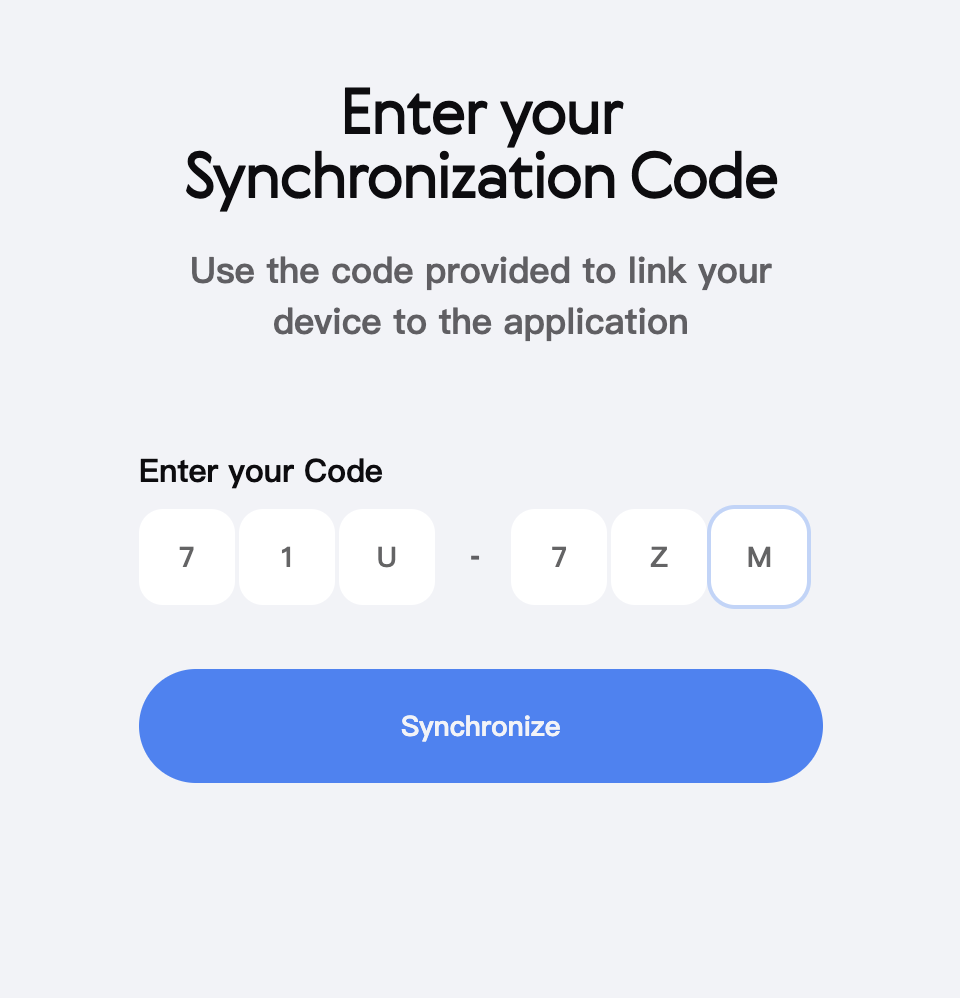
After clicking the Synchronize button in the above picture, the following page appears instead of a dialog window.
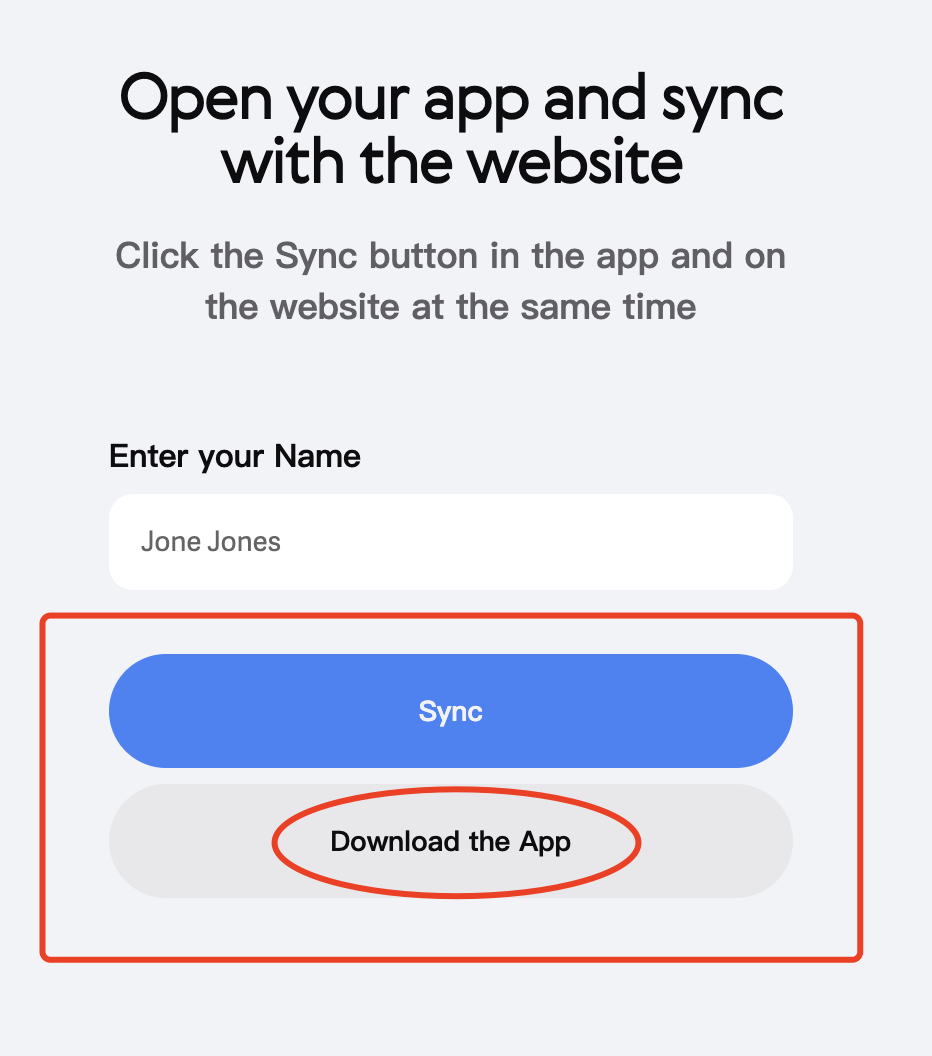
Note the content in the red box in the above picture. Although the other party did not ask me to click to download the App, the text above clearly stated that I needed to click the Sync button on both the website and the App.
Why do I need to download the app? Isn't there a web version?
Although I was a little hesitant, I still downloaded it. However, when I entered the installation page below, I hesitated.
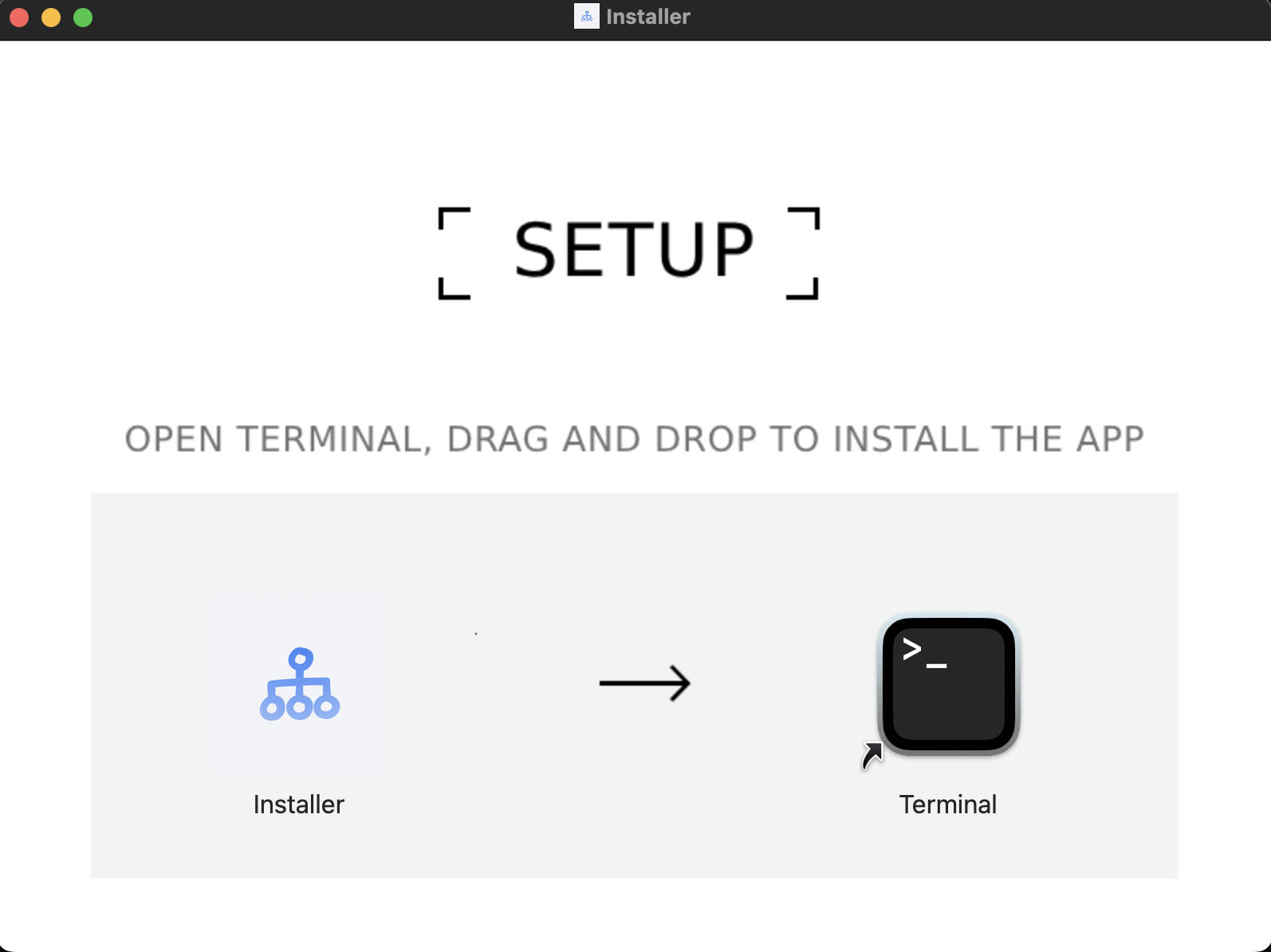
The reason for my hesitation was that this app cannot be installed directly, but needs to be run through the terminal, which I had never encountered before. So I stopped and wanted ChatGPT o3 to help me identify it. The result was shocking, as shown in the picture below.
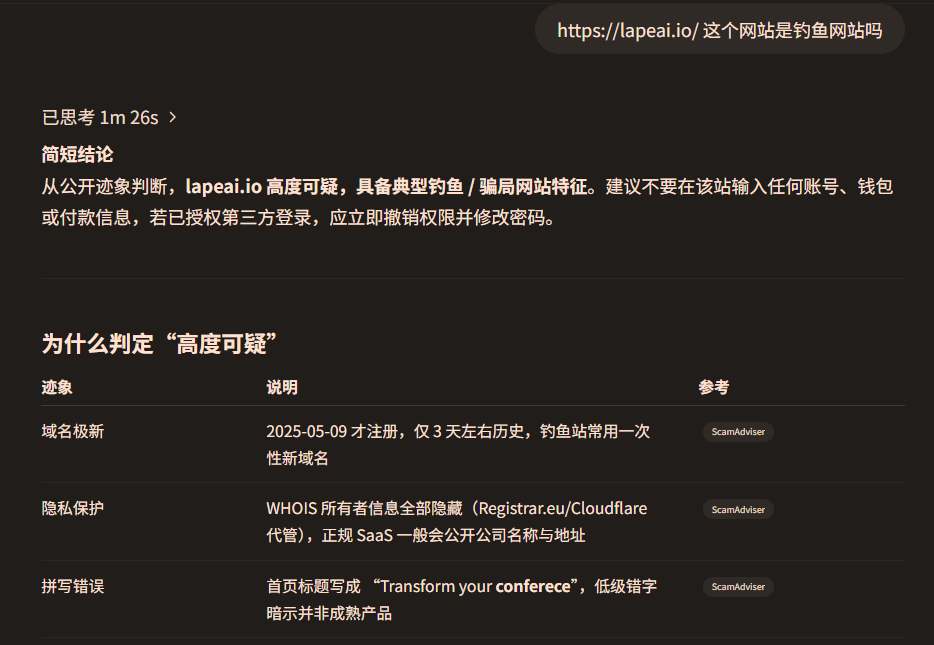
This check really made me realize how close I was to danger.
The domain name lapeAI.io was registered on May 9, 2025, just three days ago;
The owner information of this domain is hidden;
There is even an obvious spelling error in the page title: "Transform your conferece" (the correct title should be conference). Note that this is the same as the page title of LapeAI.app, which has been marked as a phishing website.
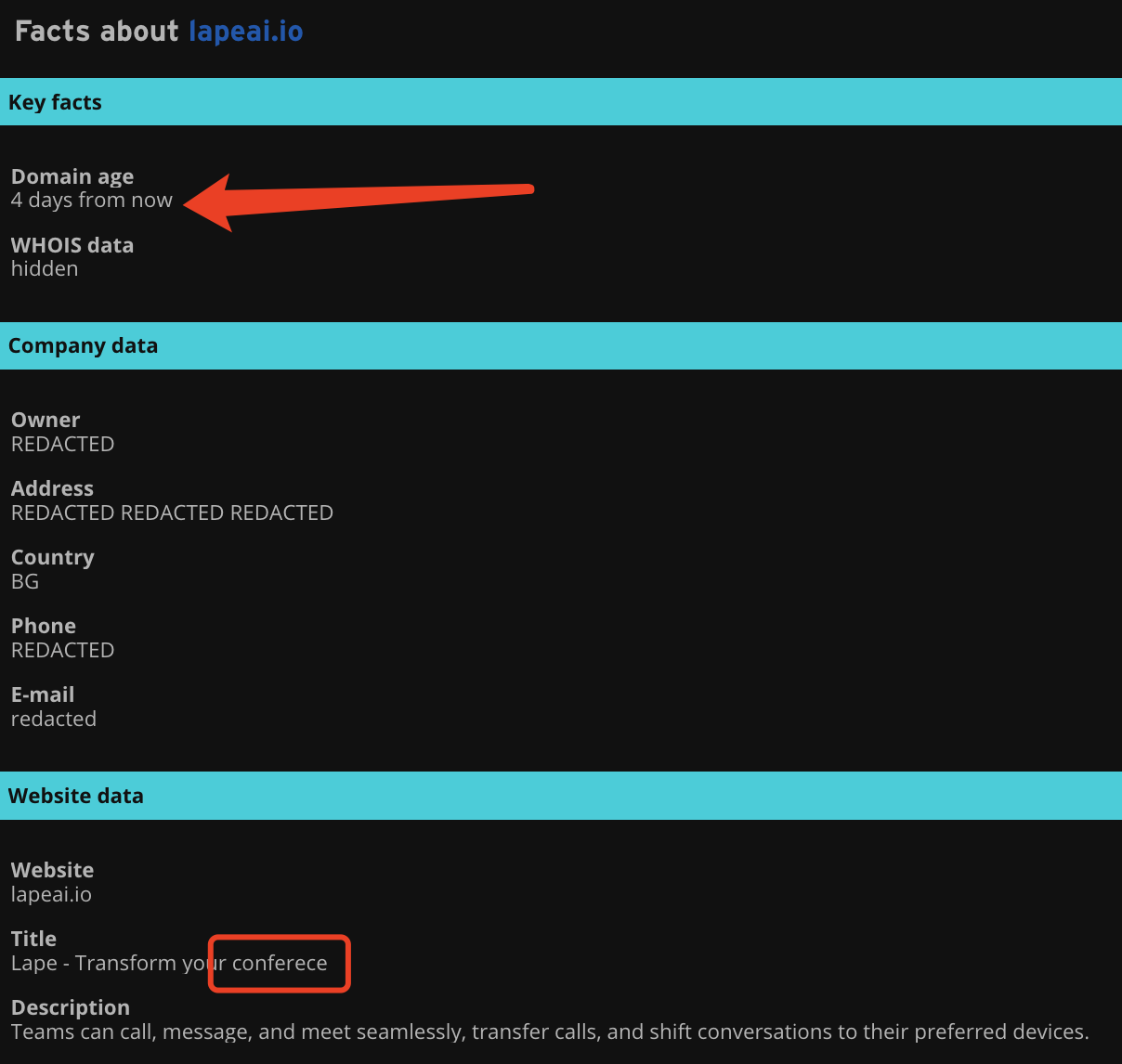
Any of the above 3 points would be enough to stop me from installing that suspicious program.
1. I'm sure I've encountered a scammer
I realized that this was not an interview invitation from CoinDesk, but a carefully packaged social engineering attack.
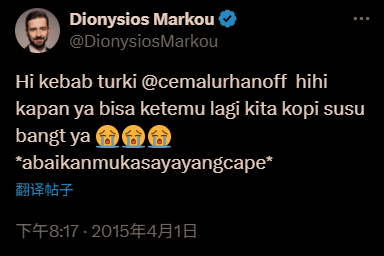
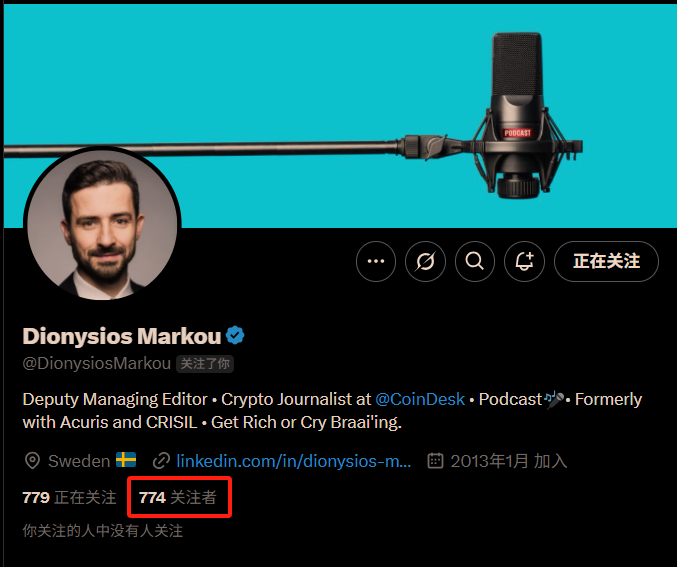
Looking back at the X (Twitter) account, although it has a blue certification, after careful observation, it was found that the account was originally in Indonesian (see the picture above), and recently it suddenly changed its identity to become a Swedish crypto media editor. Moreover, its number of followers is suspiciously small, only 774 people - which is completely inconsistent with the number of followers of the real CoinDesk editors, who often have tens of thousands of fans.
I realized that the other party was not a journalist, but a liar. Thinking back on the communication process, it is terrifying.
From the initial private message response, confirming the time, registering an account, to almost clicking to run the installation package, you are only one step away from being deceived.
The other party knew that I spoke Chinese and took the initiative to mention AI translation; he knew that I wrote about Web3 and specifically emphasized that this podcast episode talked about Bitcoin, MEME, and Asian projects; he certainly knew the influence of CoinDesk in this circle - he used it as bait.
I was tailor-made to be deceived.
I began to realize that this was not a "random scam" but a precise social engineering attack.
It didn't use any hacking techniques, didn't write a line of code, and didn't send virus links. It attacked my trust, my professional identity, and my desire to be interviewed.
At that moment, a word came to my mind - 0-day vulnerability.

2. Humanity 0-Day: Vulnerabilities that never expire, attacks that are always online
You may have heard of the term “0-Day vulnerability” — it represents the highest level of threat in the field of cybersecurity.
"0-Day" was originally a technical term. It first appeared in underground BBSs in the 1980s and 1990s: hackers used "zero-day software" to refer to "a brand new program that has been released 0 days ago, has not been made public, and no one has a patch to apply."
Because developers don't know about the vulnerability yet, hackers can use it to invade first on "day 0"; later, the term simply evolved into "zero-day vulnerability" itself, and "zero-day attack" against it. The common collocation of 0-day is:
0-day vulnerability: The vendor is completely unaware of it and has no patch yet.
0-day exploit: An attack code written for the vulnerability.
Zero-day attack: An intrusion operation carried out by exploiting the vulnerability.
Because there are no patches and no rules to block them, zero-day attacks have always been regarded as the "highest level of threat."
But you may never have thought that humans themselves also have "0-Day vulnerabilities".
It is not hidden in a certain section of server code, but buried deep in the instinctive reactions of human beings evolved over thousands of years. You think you are surfing the Internet, working, and getting information, but in fact you have already been exposed to countless psychological loopholes that are enabled by default.
for example:
When you see a blue check mark account, do you assume it is “official”?
Do you get nervous as soon as you hear "limited places" or "the event is about to end"?
When you encounter "abnormal account login" or "frozen assets", can't help but click to check?
This is not stupidity or negligence, but a survival mechanism evolved by humans. More precisely, this is the weaponized 0-Day of human nature after being repeatedly verified and refined by scammers and hackers.
2.1 What is Humanity 0-Day?
We can understand this concept like this:
Human 0-Day refers to those human psychological loopholes that can be repeatedly exploited by social engineering attacks but cannot be completely repaired by technical means.
A 0-Day vulnerability at the technical level can be blocked with just one patch. But a 0-Day vulnerability in human nature is almost impossible to cure. It is written in our desire for a sense of security, in our natural trust in authority, and in our instinctive impulse to "take advantage" and "not lag behind others."
It doesn't require complex technology or code, just a phrase, a familiar icon, and an email that "looks like the real thing." It doesn't need to hack into your device, it just needs to bypass your brain - to be precise, bypass the time you think.
Moreover, it has no "update" mechanism, and no anti-virus software can block it. Everyone online is exposed to the attack range by default.

2.2 Three characteristics of human nature 0-Day
The reason why "Humanity 0-Day" is so scary is that it has three core characteristics that go beyond technical vulnerabilities.
First, it transcends time. These psychological response mechanisms are almost written into human evolutionary genes. In the era of eating raw meat and drinking blood, our instinctive reaction of fear (such as seeing fire and snakes) was necessary for survival; absolute obedience to the "leader" in the tribe was the basis of group cohesion. Thousands of years have passed, and these mechanisms are still retained in your and my decision-making loops.
Secondly, it transcends culture. It doesn’t matter what country you are from, what school you went to, or whether you have a technical background. North Korea’s famous Lazarus hacker group can use English to hook Bybit employees, use Korean to deceive North Korean defectors, and use Chinese to fool encrypted KOLs on Telegram. Languages can be translated, but human nature does not need to be translated.
Finally, it can be reused in batches. You may still be wondering if you are being "targeted". In fact, attackers no longer need to "target" anyone. A script, a paragraph of speech, can be sent to tens of thousands of people by copying and pasting. In the fraud parks in Cambodia and northern Myanmar, fraudsters can "take up their posts" after receiving 8 hours of "speech training", with a "output value" of millions of dollars per month - with almost no cost, but a success rate far exceeding traditional phishing emails.
This is not a loophole, this is an industry.
2.3 Your brain is running a "social interface" that is open by default
If we compare the human brain to an operating system, then many of human thinking reactions are actually a set of APIs that are always running - psychological interface functions.
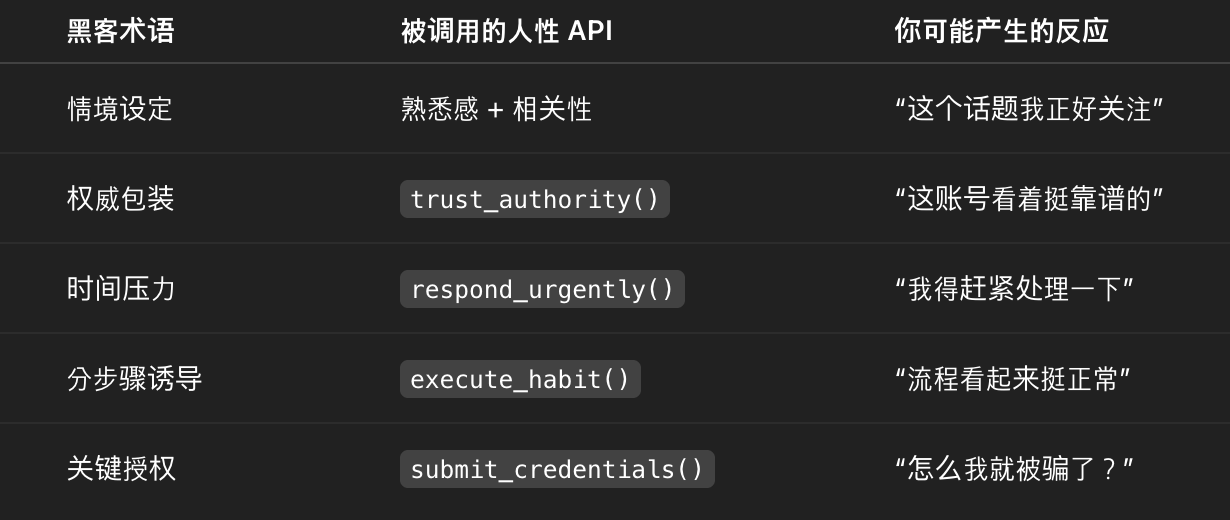
These APIs have no code and cannot be turned off. As long as you are a human, they are open by default. For example:
Sending a private message to a blue-tick account can trigger your trust mechanism in "authority";
Using "there may be abnormal operations in your account" as an opening statement can trigger your fearful reaction to asset risks;
Add a sentence like "300,000 people have participated" and you will feel "I can't miss it";
If you are told "time limit, only 20 minutes left", your rational judgment will be compressed to the minimum.
During the whole process, they don't need to hold you down, scare you, or even lie. They just need to tell you a script that meets your expectations, and you can click on the link, register on the platform, and download the app by yourself - just like every step I took in the experience of being deceived, all voluntary and active.
So, what is really scary is:
You think you are "operating the software", but in fact you are the one being called by the "program".
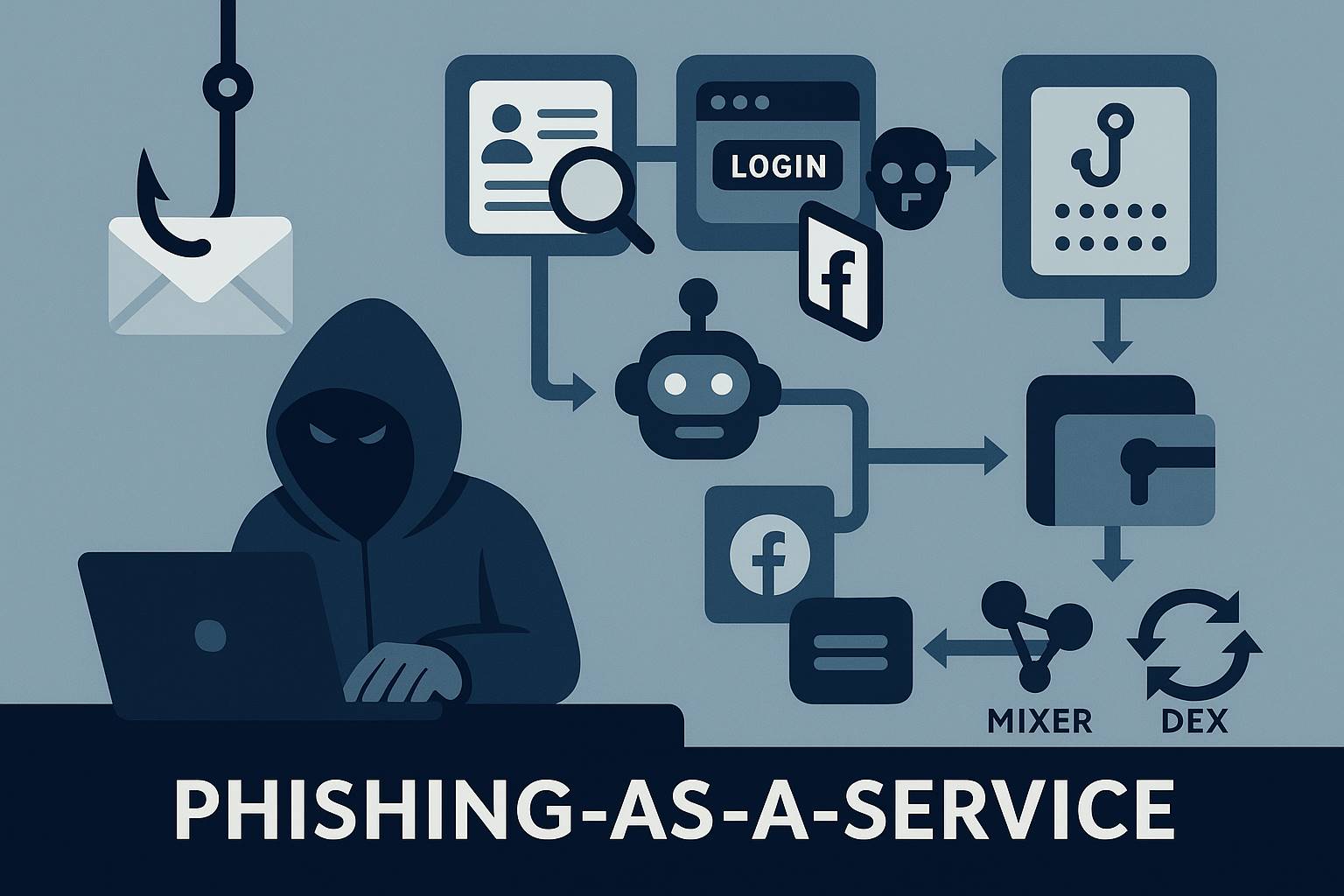
This is no longer a scammer "fishing", but a phishing-as-a-service network consisting of an entire script factory, customer service system, and money laundering process.
There are no "fixable" vulnerabilities in this type of attack, only "forever exploitable" human nature.
3. This is not a crisis just for you, but a global cognitive war
After understanding the concept of "0-Day of Humanity", I deeply realized that I am not an isolated case, nor a special case.
I am just a pawn in this precisely targeted global psychological attack - like millions of ordinary people, I am being manipulated in batches using the same "social engineering script".
The weapons of hackers are no longer keyboards and codes, but "scenario design, authority disguise and trust scripts"; and the entire attack ecosystem has long evolved from "individual crimes" to an industrialized model of "content factory + script assembly line".
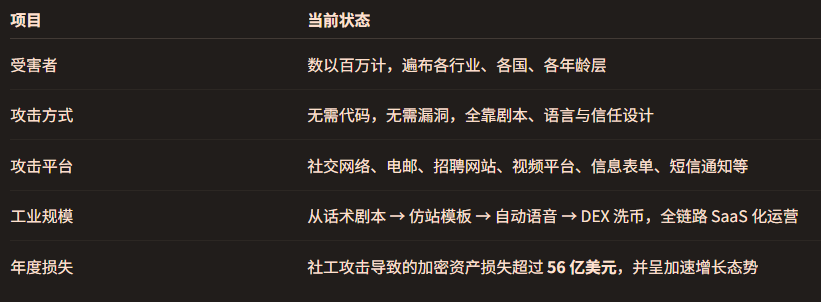
3.1 The “black hole” of crypto assets: 43% of losses are not caused by hacking, but by fraud
According to the "Crypto Crime Report 2025" released by Chainalysis: In 2024, the global direct losses caused by the theft of crypto assets will reach 2.2 billion US dollars, and private key leakage (usually triggered by phishing, social engineering, etc.) will account for 43.8%, about 960 million US dollars.
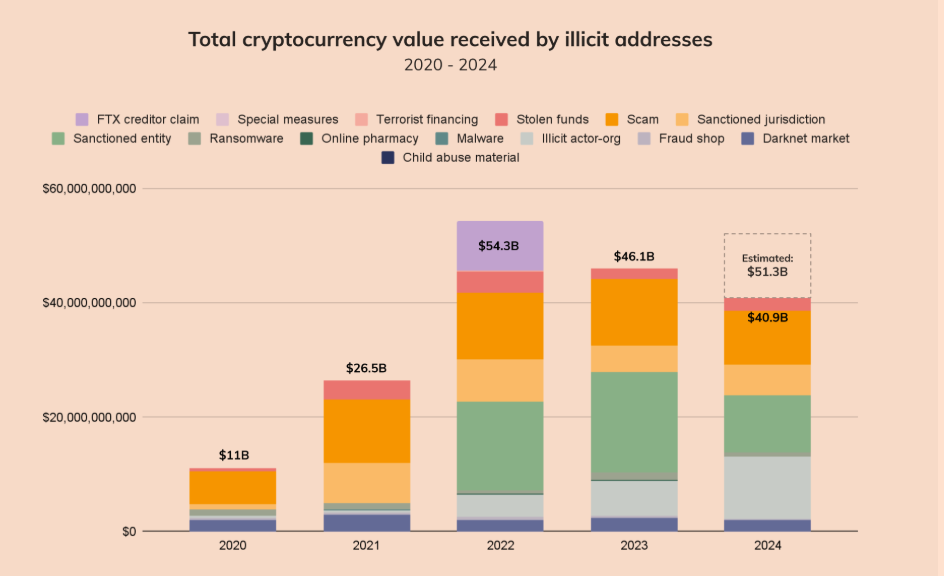
This means that out of every $5, nearly $2 is lost not because of technical loopholes or attack scripts, but because human nature is precisely manipulated and users voluntarily "hand over the keys."
These attacks do not invade wallets, crack contracts, or hijack nodes. They only require sending an email, a private message, a fake identity, and a "tailor-made inducement speech".
Losses often occur the moment you click on a link or enter a seed phrase.
This is not a system collapse, but each of us, under the cognitive mode of "default trust", has opened the backdoor again and again.
3.2 Hacker Script Factory: Lazarus Group’s $1.3 billion cognitive theft
If you think these attacks are sporadic and unsystematic, then you need to get to know the world's "most professional" social engineering team - Lazarus Group, which comes from North Korea, has state-level support, and operates globally.
According to data tracked by several security companies:
In 2024, Lazarus launched more than 20 major social engineering attacks;
Attack targets include: Bybit, Stake.com, Atomic Wallet and other mainstream crypto platforms;
The methods of committing the crime include: fake recruitment (resume + interview software), supplier disguise, cooperation emails, podcast invitations, etc.;
Annual stolen assets exceeded $1.34 billion, accounting for nearly 61% of the total global encryption attacks.
What’s even more shocking is that these attacks hardly exploit any system-level vulnerabilities and rely entirely on “script + packaging + psychological phishing”.
You are not their technical target, but their cognitive interface.
They study your language, habits, and identity information; they imitate the companies, friends, and platforms you are familiar with; they are not hackers, but more like a psychological manipulation content team.

3.3 Hackers don’t attack wallets, but take over your brain’s “trust system”
Let's restore the essential picture of the whole situation:
All of this is not ultimately a disaster at the system level, but a collapse of default trust at the user level.
The attacker did not crack your wallet password, but they broke through the few seconds of hesitation in your cognitive system.
It's not the virus that kills you, but you yourself, in a well-packaged script, step by step towards the wrong "confirm" button.
Maybe you are thinking: "I am not an exchange employee, I am not a KOL, and I don't have many coins in my wallet, so no one should be watching me, right?"
But the reality is:
The attack is no longer "designed specifically for you", but "as long as you fit the template, the script will hit you accurately."
Have you published your address publicly? They will recommend tools.
Have you submitted your resume? They will send you an interview link.
Have you written an article? They will invite you to collaborate.
You said in the group chat that there was an error with your wallet? They came immediately to "help fix it."
They don't look at whether you have money, but whether you enter the script trigger conditions.
You are not a special case, you just happened to "trigger the automatic delivery system."
You are not naive, you just haven't realized that human nature is the most central battlefield of this era.
Next, I will disassemble the most core tactical weapon in this war - the attack script itself. You will see how they are polished step by step, and each move is aimed at the "default operating system" deep in your heart.

4. Scripted attack: calling your "human API" step by step
In 99% of social engineering attacks, it’s not that you accidentally clicked the wrong button, but that you were “guided to click the right button” step by step.
This may sound like a fantasy, but the fact is -
While you thought you were "just replying to a message" or "just registering on a platform", you had actually already fallen into the psychological script carefully arranged by the other party. Each step was not violent control, but cleverly designed to make you willingly walk towards the end of being attacked.
4.1 The attack process is a cognitive manipulation chain
Don’t think you were “cheated” because you clicked a link or downloaded an app. A true social engineering attack is never a matter of action, but a matter of psychological processes.
Every click, every input, and every confirmation is actually the other party calling the "behavior shortcuts" that have already been written in your brain.
Let's restore the five most common attack scripts of hackers:
[Step 1] Context Priming
Hackers first design a scenario that you are "willing to believe".
Are you a journalist? They will invite you to an interview by claiming to be CoinDesk editors.
Do you work in a business? They said you were selected for "advanced testing";
Are you a Web3 developer? They pretend to be a project owner and invite you to collaborate.
Are you an ordinary user? They scare you with "account abnormality" or "transaction freeze".
These scenes are not rigid, but highly consistent with your identity, role, and daily needs. They allow you to naturally immerse yourself in them without thinking. They are hooks and anchors.
▶ The case of a journalist being scammed, which I have analyzed in depth, is a classic example. He just asked for help from Ledger customer service on Twitter, but that "reasonable" message became the entry point for hackers to precisely target him.

【Step 2】Authority Framing
Once there is an entrance, we also need to build trust.
Attackers will use visual symbols that you are familiar with - blue check marks, brand logos, official tone of voice.
They will even clone the official website domain name (for example, replacing coindesk.com with coindesk.press), and add authentic podcast topics, screenshots or samples to make the whole plot look "just like the real thing."
▶ In my case, the other party wrote about a CoinDesk position in the profile, and the topics covered Web3, MEME, and the Asian market—perfectly hitting the psychological bull’s eye for me as a content creator.
This trick is to activate the "trust_authority()" function in your mind - you think you are judging the information, but in fact you are just trusting the authority by default.
【Step 3】Time Pressure (Scarcity & Urgency)
Before you can completely calm down, the other party will immediately speed up the pace.
"The meeting will start soon."
"Link will expire soon"
"Account will be frozen if not processed within 24 hours"
——This kind of wording has only one purpose: to prevent you from having time to verify and forcing you to do as it says.
▶ In the classic case of Lazarus hacking into Bybit, they deliberately sent out "interview materials" through LinkedIn before employees got off work, creating the double psychological pressure of "rushing for time + high temptation" and accurately hitting the opponent's weak moment.
【Step 4】Action Step
This step is crucial. Hackers will not ask for all permissions at once, but will guide you through each key action step by step:
Click the link → Register an account → Install the client → Authorize access → Enter the seed phrase.
Every step seems to be "normal operation", but this is the rhythm design of the script itself.
▶ In my experience, the other party did not send the compressed package directly, but used the method of "invitation code registration + synchronous installation" to disperse the vigilance to multiple links, giving you the illusion that "there should be no problem" at every step.
【Step 5】Key Authorization (Extraction)
By the time you realize something is wrong, it's often too late.
At this stage, the attacker will either trick you into entering a seed phrase or private key, or silently obtain your session, cookies, or wallet cache files through a software backdoor.
Once the operation is completed, they will transfer the assets immediately and complete the mixing, extraction and laundering processes in the shortest possible time.
▶ In Bybit’s $1.5 billion theft, the entire process of obtaining permissions, splitting transfers, and mixing coins was completed in a very short period of time, leaving almost no chance for recovery.

4.2 Why does this process almost never fail?
The key is: it does not defeat your technical system, but makes you actively "go offline" your own defense system.
From the first step "Who are you", to the second step "Who do you believe", to the third step "You don't have time to think", to the final step "You pressed the execute button yourself" - this process is not violent, but precise at every level, and each step is aimed at an "automatic reactor" in your mind.
In psychology, this state is called Fast Thinking. It means that when a person is anxious, excited or in a hurry, the brain will skip logical analysis and make decisions directly based on emotions and experience. To understand the principles and mechanisms behind this, I recommend reading the book Thinking, Fast and Slow.
What hackers are best at is creating an environment that puts you in fast thinking mode.
So remember this most important sentence:
Social engineering attacks do not break through your defenses, but invite you to "open the door actively" step by step.
It did not break your blockchain encryption algorithm, but it perfectly bypassed the most critical "user-level firewall" - yourself.
So, if "Humanity 0-Day" cannot be repaired by technology, is there still a habit, an iron rule that allows you to press the pause button before the script is triggered?
The answer is: Yes.
It's called the "5-second rule."

5. The 5-second rule: the minimum action plan to crack the 0-day of human nature
We can see it clearly here:
The target of social engineering attacks is never your wallet or your mobile phone - its real target is your brain response system.
It is not a violent attack that smashes through the defense line with a hammer, but a cognitive manipulation game of boiling a frog in warm water: a private message, a link, a seemingly professional conversation, leading you to "voluntarily" walk into the trap step by step.
So, if the attacker is "tuning your program", how do you interrupt this automatic process?
The answer is actually very simple, you only need to do one thing:
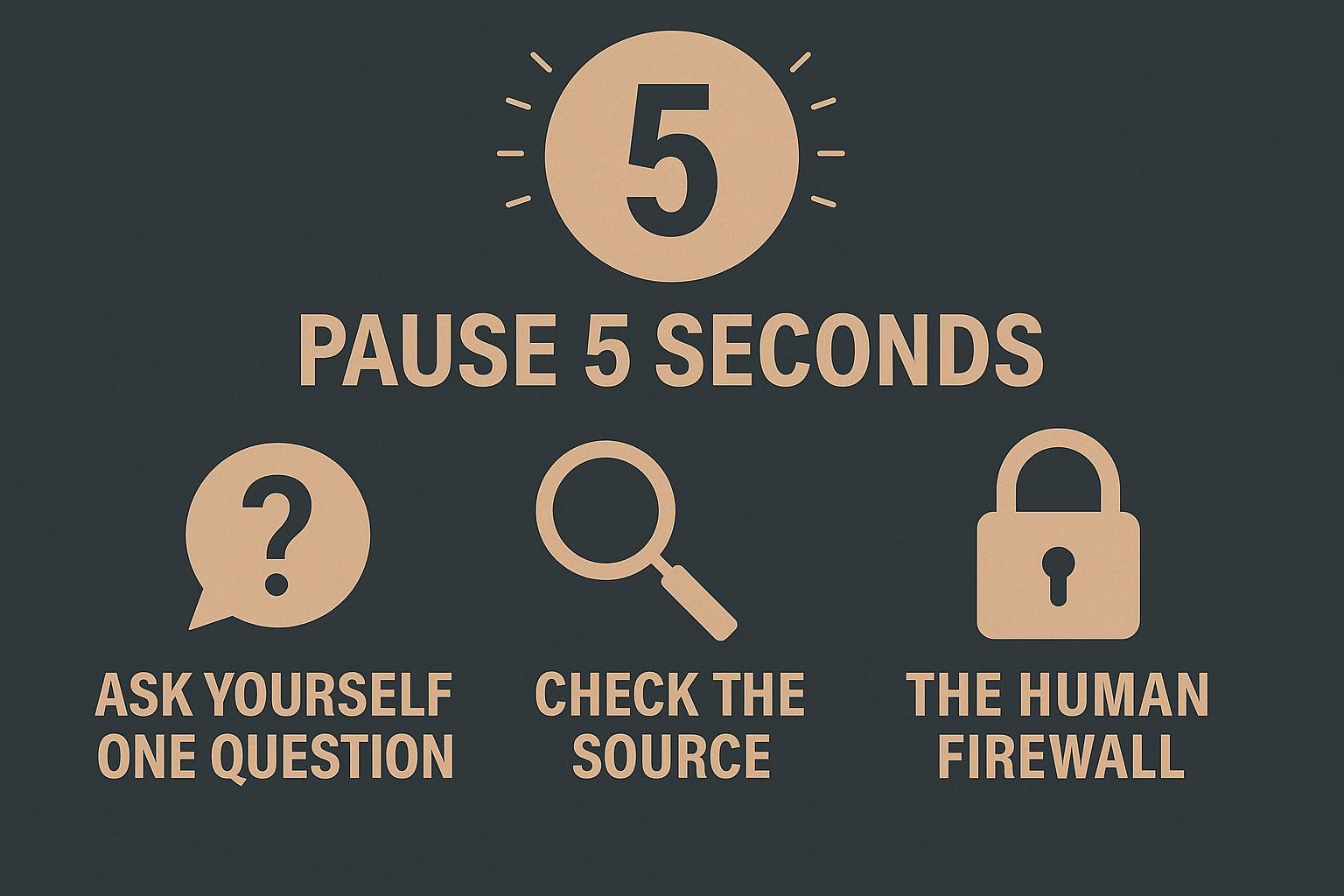
Whenever someone asks you to enter a seed phrase, click a link, download software, or claim to be an authority - you must stop and count to 5 seconds.
This rule may sound trivial, but when implemented, it is:
The "humanity patch" with minimal cost and highest benefit.

5.1 No matter how strong the technical defense is, it can’t stop your quick hands
You may ask: "I am not a newbie. I also use cold wallets, multi-signatures, and two-factor authentication. Why do I still need the '5-second rule'?"
Indeed, today’s Web3 world has built a complete set of progressive security technology stacks:
Log in to your account using Passkey;
Sign transactions offline with Ledger or Trezor;
Open suspicious links with Chrome sandbox;
Verify each installation package with macOS Gatekeeper;
Use a SIEM system to monitor device connection behavior.
These tools are powerful, but the biggest problem is: you often don't have time to use them.
Did you check the signature when you downloaded the app?
Did you check the domain name spelling before entering the seed phrase?
When you click on the private message "System abnormality, please repair", have you ever thought of checking the account history first?
Most people are not incapable of defense, but simply do not have the time to activate defense.
That’s why we need the “5-second rule”. It is not against technology, but it buys time for technology.
It won't kill the enemy for you, but it can call you back before you "put your hands down".
Let you think for a second: "Is this link reliable?"
Check: "Who sent this?"
Pause: Why should I rush?
These short 5 seconds are the time it takes for your cognitive system to go online, and are also the prerequisite for all your technical defenses to take effect.
5.2 The behavioral science logic behind the “5-second rule”
Why is it 5 seconds, and not 3 seconds or 10 seconds?
This comes from the experimental evidence and neuroscience explanation presented by behavioral writer Mel Robbins in his book The 5 Second Rule and TEDx talk.

Robbins found that:
When you count down 5-4-3-2-1 within the first 5 seconds of the urge to act and immediately take the first step, the prefrontal cortex of the brain will be forcibly activated, thereby "occupying" the procrastination and escape circuits of the emotional brain, allowing rational thinking to temporarily take over the decision-making.
The countdown is essentially a metacognition (“metacognition starter”):
Interrupt inertia - a countdown of several seconds is equivalent to pressing the "pause button" for the brain, interrupting automatic procrastination or impulsive behavior;
Activate rationality - Countdown forces you to focus on the present, awakens the prefrontal cortex, and puts you into "slow thinking" mode;
Trigger micro-actions - Move or say something as soon as the countdown ends. The brain will regard this step as a fait accompli, and the resistance to subsequent actions will drop sharply.
Psychological experiments have shown that with just this simple technique, subjects' success rates in self-control, overcoming procrastination, and social anxiety scenarios have significantly increased; Robbins' own cases and those of millions of readers have repeatedly confirmed this.
The 5-second countdown is not to make you wait, but to let your rationality "cut in line".
In social engineering scams, these 5 seconds are enough for you to switch from "automatically clicking" to "questioning and verifying", thereby breaking the time pressure of the other party's script.
Therefore, the "5-second rule" is not metaphysics, but a "cognitive emergency brake" supported by neuroscience and metacognition research.
It has almost zero cost, but can bring all subsequent technical means (two-factor authentication, cold wallets, browser sandboxes, etc.) to the forefront at the most critical behavioral entrance.
5.3 High-risk scenarios: Stop in all three situations without hesitation
I have summarized the scenarios where more than 80% of social engineering attacks occur. If you encounter any of the following three situations in real life, please immediately follow the 5-second rule:

Scenario 1: “You have a problem with your wallet, let me fix it for you”
You ask for help on a social platform, and a few minutes later, a blue-checked account claiming to be "official customer service" sends you a private message and kindly attaches a "repair link" or "synchronization tool."
Stop: don’t reply, don’t click.
Think about it: What is the history of this account? Has the profile picture been changed?
Check it out: Go to the official website to check the customer service channels, or Google this domain name.
Many scams start with this "timely help". You think the other party is helping you in times of need, but it is actually a preset script.
Scene 2: "Congratulations on being selected for internal testing/interview/interview"
You receive a fully formatted invitation email from someone who appears to be a major industry player. The tone is formal and there is a PDF or software download link attached.
Stop: Don’t click on the file in a hurry, check the sender domain name first.
Think about it: Does Coinbase really use zip attachments? Why does CoinDesk have to use LapeAI?
Take a look: When was this website registered? Is there a typo?
▶ My case is a typical example of this scenario. The other party did not use low-quality fraud, but rather sophisticated disguise. He did not come to defraud you of a meal, but to take over your wallet.
Scenario 3: "Your account login is abnormal, please verify your identity"
This type of scam is the most common. It involves a "warning email" or text message with a sensational title, an urgent link attached, and an oppressive tone that suggests "if not handled, your account will be frozen."
Stop: Do not click on the SMS link, directly open the official website to log in and verify.
Think about it: Why would the official notice be so urgent? Does the tone sound like a template?
Check: Does the sender's email address end with google.com or g00gle.co?
These kinds of scenarios hit your fears and sense of responsibility, and once you click, the consequences are immediate.
5.4 Why is this iron rule applicable to everyone?
You don’t need to be a hacker hunter, you don’t need to learn cold signatures and cold wallets, and you don’t need to install a bunch of blockers and plug-ins. You only need to:
Countdown 5 seconds
Ask yourself a question
Check the source (Google / domain name / tweet record)
This is the “behavioral patch” you put on “Humanity 0-Day”.
This iron rule has no threshold, no cost, and does not rely on technology updates. The only thing it relies on is whether you are willing to stop and think at the critical juncture.
This is the simplest, most practical and most universal "human firewall" to crack script attacks.
Conclusion: Be cautious for 5 seconds, and you will be free for a lifetime
At first, I just wanted to record an experience of "almost being cheated".
When I saw the copied fraudulent website, the same misspelled webpage title, and the phishing domain name that was just registered three days ago... I realized:
This is not an individual misjudgment, but an entire script assembly line that is harvesting trust in batches around the world.
It does not rely on technical attacks, but on the second of hesitation when you "click".
You thought your cold wallet was invincible, but you ended up handing over seed phrase yourself; you thought the blue check mark was trustworthy, but it turned out to be just a disguise for $8; you thought you were unimportant, but you just happened to fall into their script.
Social engineering attacks do not break into the system, but hijack your cognition step by step.
You don’t need to master cold signatures or study address authorization, you just need a small habit:
At critical moments, force yourself to stop for 5 seconds.
Go and see if this account, this link, and this reason are worthy of your trust.
These 5 seconds are not slow, but clear-headed; they are not suspicious, but dignified.
When cognition becomes a battlefield, every click of yours is a vote.
Be cautious for 5 seconds and you will be free for a lifetime.
I hope you are not the next victim, and I hope you will forward this message to the next person who may not have time to hesitate.








