AI Agents May Become the Next Major Security Vulnerability in the Crypto Realm
<>agents are increasingly integrated deeply into the the industry (including cryptocurrency), but the industry has yet not the hidden security risksabilities. Currently, AI agents in the cryptocurrency field are widely integrated into wallets, trading bots, and on-chain assistants, used for autoautomating tasks and making real-time decisions.CP can serve as a control layer to manage AI agent behaviors, including tool calls, code execution, and user input responses. However, this flexibility also creates a dangerous attack surface - malicious plugins might override instructions, contaminate input data, or induce agents to execute harmful operations.

Amazon- and Google-backed Anthropic dropped MCP on Nov. 25, 2024, to connect AI assistants to data systems. Source: Anthropic
MCP Attack Vectors Expose AI Agent Security Risks
According to VanE, the 2024the024, number the crypto industry has exceeded ,000an expected toexca million in The security firm SlowMist discovered four major developers should wary of, all implemented through plugins (MCP agents expand capabilities through plugins whether obtaining price data, executing transactions, or handling system tasks):
- DataOning: Inducing users to execute misleading operations. By manipulating user behaviors and creating false dependencies, malicious logic is implanted embedded early in the process.
- JSON Injection Attack: Plugins retrieve information from local (potentially malicious) data sources through JSON. This may lead to data leakage, instruction tampering, or bypassing verification mechanisms by feeding contaminated inputs to the agent.
- Competitive Function Override: Overriding legitimate system functions with malicious code code. This both prevents normal operation execution and embeds obfuscated instructions to disrupt system logic and hide attack traces.
- Cross-MCP Call Attack: By encoding erroneous messages or deceptive prompts, inducing AI agents to interact with unverified external services. By chaining multiple systems, the attack surface is expanded, creating further exploitation opportunities.
- <>
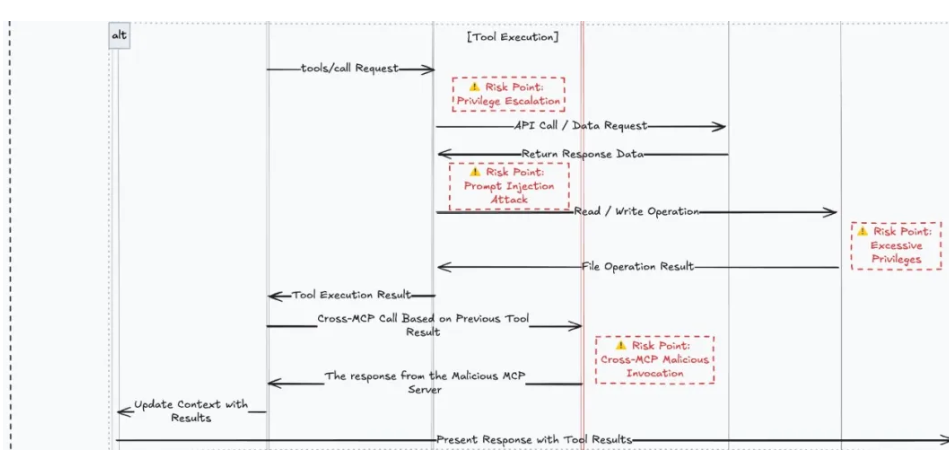
Sequence diagram showing potential cross-MCP attack vectors and risk points. Source: SlowMist
SlowMist co-founder "Monster" explained to Cic oint"poisoning requires injtingectingicious samples embed it in model parameters while agent and Mination occurs during the model stages through additional malicious information. In terms of threat level and permission scope, agentoning more independent AI model poisoning."
Cryptocurrency Faces MCP Security Threats
Although MCP application in the crypto domain is still in its early stages, the attack vectors discoveredowMist found during pre-release project audits have proven these risks are real. Monster recalls a p vulnerability discovered during an audit that could potentially lead to private key exposure - a catastrophic blow to any crypto project or investor.
Fhenix crypto research company Itzhpointedaki out: systems to-means expanding the attack surface beyond controllable ranges.. Plugins often often execute as trusted without sandbox protection, which can trigger privilege escalation, dependency injectionakinjection, and function overoverrides, and the most severe cases, silent data le."p strong Security DefDefenses Strong Urgently strong p Rapid trial-and-and-error iteration - and then encountering a hack" is the real risk faced developers face when leaving security issuesuesto the second version. Secret Foundation executive director Lisa Loud emphasizes: "Building plugin systems in a transparent crypto environments must prioritize security. SlowMist experts recommend developers implement strict plugin validation, input sanit, privilege principles, and regular behavior reviews."
Loud states that implementing implementing such security checks is "not difficult", just "tedious and time-consuming". However, as AI agents continue expand their crypto application in crypto infrastructure, the importance of proactive security protection cannot be overstated.
Munlocks powerful new new capabilities for AI agents, without strict control over plugin and system behaviors, "assistants" may mutate into attack vectors that compromise crypto wallet, fund, and data security.







