Authors: Lisa&Liz
Editor: Liz
Background
Recently, the U.S. Treasury's Office of Foreign Assets Control (OFAC) announced sanctions against Aeza Group and its affiliated entities, headquartered in Russia, for providing hosting services to ransomware and information theft tools.
(https://home.treasury.gov/news/press-releases/sb0185)
The sanctions cover Aeza Group and its UK front company Aeza International Ltd., two Russian subsidiaries (Aeza Logistic LLC and Cloud Solutions LLC), four executives (CEO Arsenii Penzev, Director Yurii Bozoyan, Technical Director Vladimir Gast, and Manager Igor Knyazev), and a crypto wallet (TU4tDFRvcKhAZ1jdihojmBWZqvJhQCnJ4F).
"Cybercriminals continue to heavily rely on bulletproof hosting service providers like Aeza Group to launch destructive ransomware attacks, steal U.S. technology, and sell black market drugs," said Bradley T. Smith, Acting Deputy Assistant Secretary for Terrorist Financing and Financial Crimes at the Treasury Department. "The Treasury will continue to work closely with the UK and other international partners to resolutely expose the key nodes, infrastructure, and related personnel supporting this criminal ecosystem."
This sanction marks a shift by international law enforcement from targeting attackers to focusing on their underlying technical infrastructure and service providers. This article will analyze Aeza Group's background and operational model, and use the on-chain anti-money laundering and tracking tool MistTrack to restore its role in the criminal ecosystem.
Who is Aeza Group?
(https://www.pcmag.com/news/us-sanctions-russian-web-hosting-provider-aeza-for-fueling-malware)
Aeza Group is a Bulletproof Hosting (BPH) service provider headquartered in St. Petersburg, Russia, long providing dedicated servers and anonymous hosting services for ransomware gangs, infostealer operators, and online criminal groups such as illegal drug trading platforms.
Its clients include notorious infostealer operators like Lumma and Meduza, which have attacked the U.S. defense industrial base and global tech companies; ransomware and data theft groups BianLian and RedLine; and the famous Russian Dark Web drug market Blacksprut. Aeza not only provided hosting services for Blacksprut but also participated in its technical architecture. According to OFAC disclosure, Blacksprut is widely used for global distribution of fentanyl and other synthetic drugs, seriously threatening public safety.
MistTrack Analysis
According to the on-chain anti-money laundering and tracking platform MistTrack, the sanctioned address (TU4tDFRvcKhAZ1jdihojmBWZqvJhQCnJ4F) has been active since 2023 and has accumulated over $350,000 in USDT.
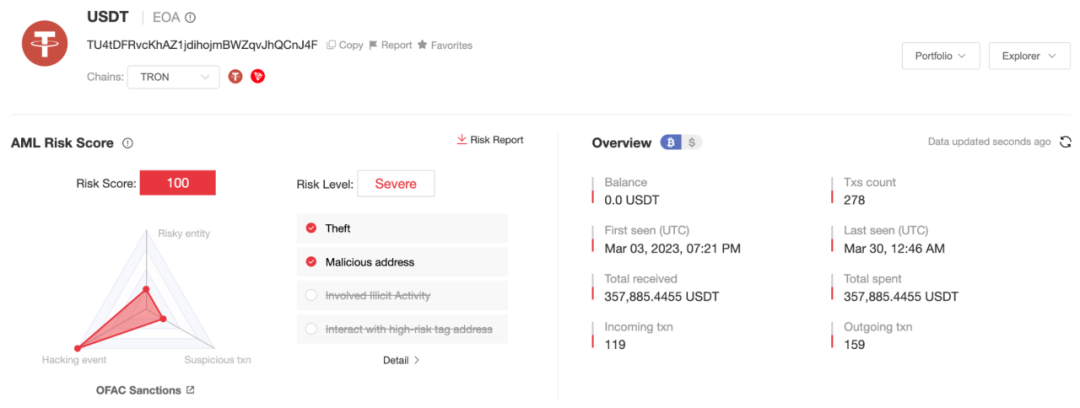
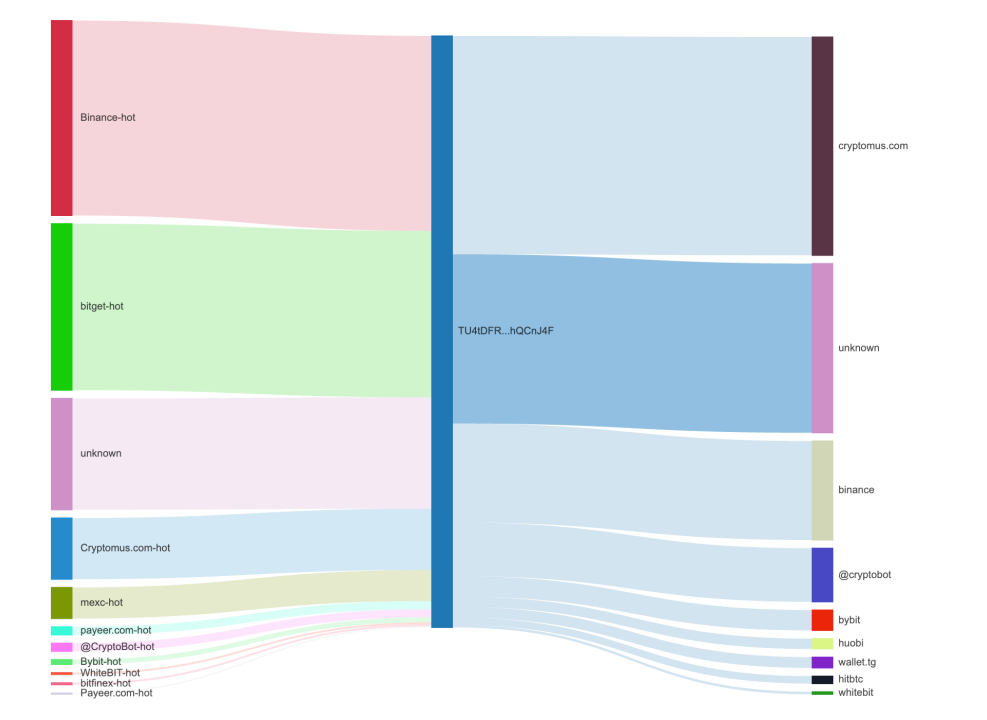
According to MistTrack analysis, this address interacts with the following entities:
Transferred assets to multiple known trading platforms/OTC services like Cryptomus, WhiteBIT, etc., for money laundering;
Associated with sanctioned entities such as Garantex and Lumma;
Associated with Stealer-as-a-Service platforms promoted on Telegram;
Associated with addresses related to the Dark Web drug market Blacksprut.
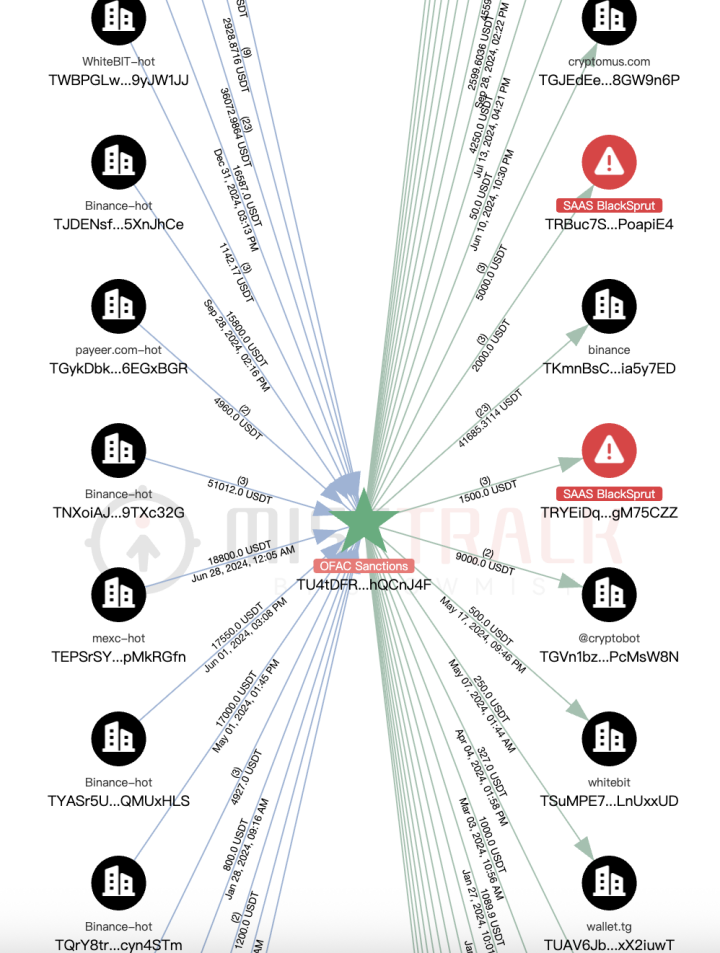
According to MistTrack's counterparty analysis, the address's interaction objects are distributed as follows:
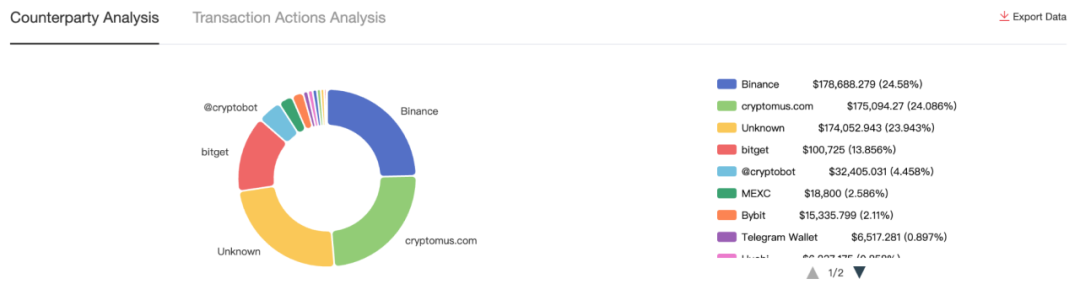
Additionally, we found that on July 2nd, Aeza was still active on Telegram, with administrators posting backup website addresses in case users couldn't access the main site:
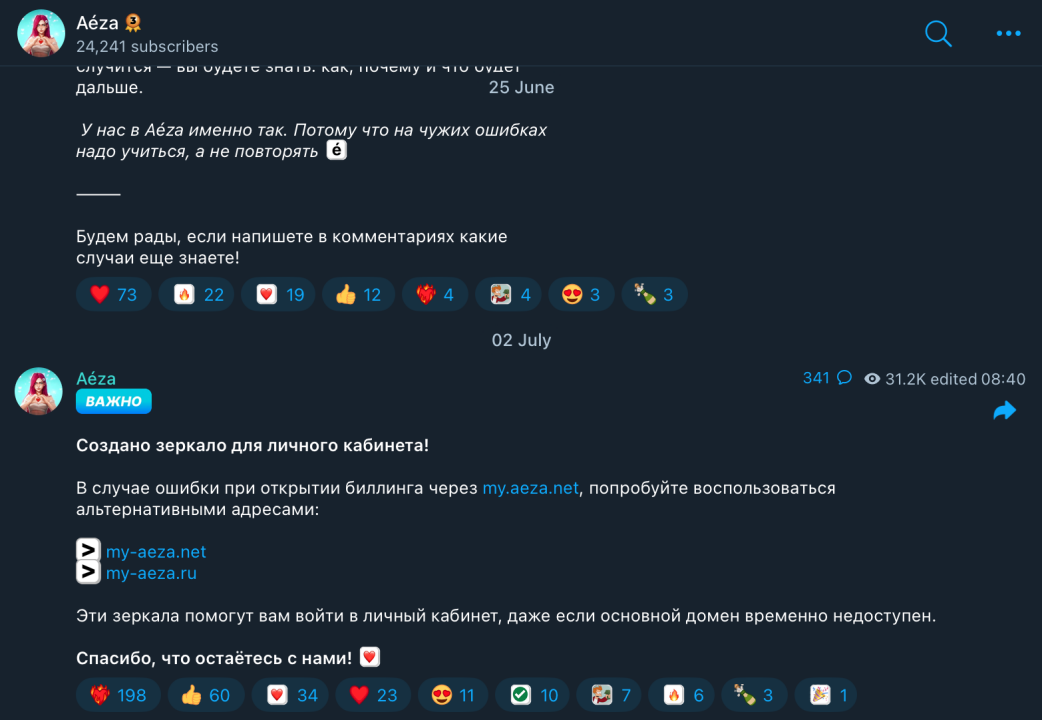
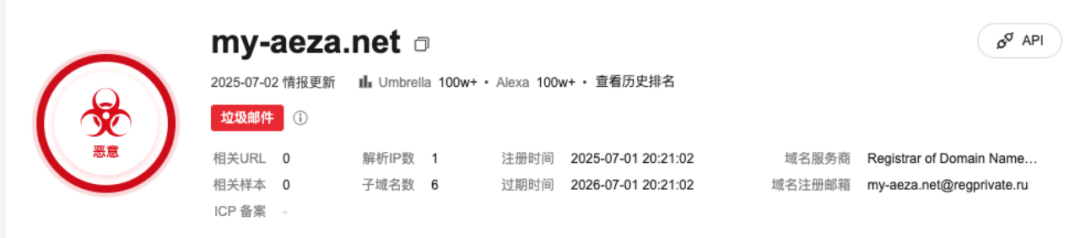
Upon investigation, these two backup website addresses were created exactly on the day OFAC announced sanctions against Aeza.
Conclusion
The sanctions against Aeza Group indicate that global regulation is extending its focus from attackers to their underlying technical service networks. Hosting providers, anonymous communication tools, and payment channels are becoming new focal points for compliance efforts. For businesses, exchanges, and service providers, KYC/KYT is no longer optional, and inadvertent business associations with high-risk entities may lead to potential collateral sanctions.








