※This article is automatically translated. Please refer to the original text for accurate content.
Key Points of Cryptocurrency Crime in the First Half of 2025
Stolen Funds
- In 2025, the amount stolen from cryptocurrency services exceeded $2.17 billion, surpassing the annual damage of 2024. The main reason is the $1.5 billion hacking of Bybit by North Korea, which became the largest hacking incident in cryptocurrency history.
- By the end of June 2025, the year-to-date theft amount was 17% higher than the worst year, 2022. If the current trend continues, service theft funds may exceed $4 billion by the end of the year.
- The proportion of personal wallet breaches in the total ecosystem theft has increased, with attackers increasingly targeting individual users. They account for 23.35% of the total stolen funds year-to-date in 2025.
- Physical violence and threats against cryptocurrency holders, known as "wrench attacks", are suggested to correlate with Bitcoin price fluctuations, with attacks more targeted during periods of high prices.
Regional Characteristics
- Looking at the location of stolen funds, 2025 shows concentration in the United States, Germany, Russia, Canada, Japan, Indonesia, and South Korea.
- The total number of victims in Eastern Europe, MENA, and CSAO regions increased most rapidly from the first half of 2024 to the first half of 2025.
- The types of stolen assets vary significantly by region, likely reflecting the cryptocurrency adoption patterns in each area.
Money Laundering Trends
- Differences are observed in money laundering methods between cyber attacks targeting services and those targeting individuals. Service attackers generally tend to use more sophisticated techniques.
- Money launderers are spending significantly more on fund transfers, with the average premium increasing from 2.58 times in 2021 to 14.5 times year-to-date in 2025.
- Despite decreasing blockchain transaction costs, the markup for moving stolen funds on-chain has increased.
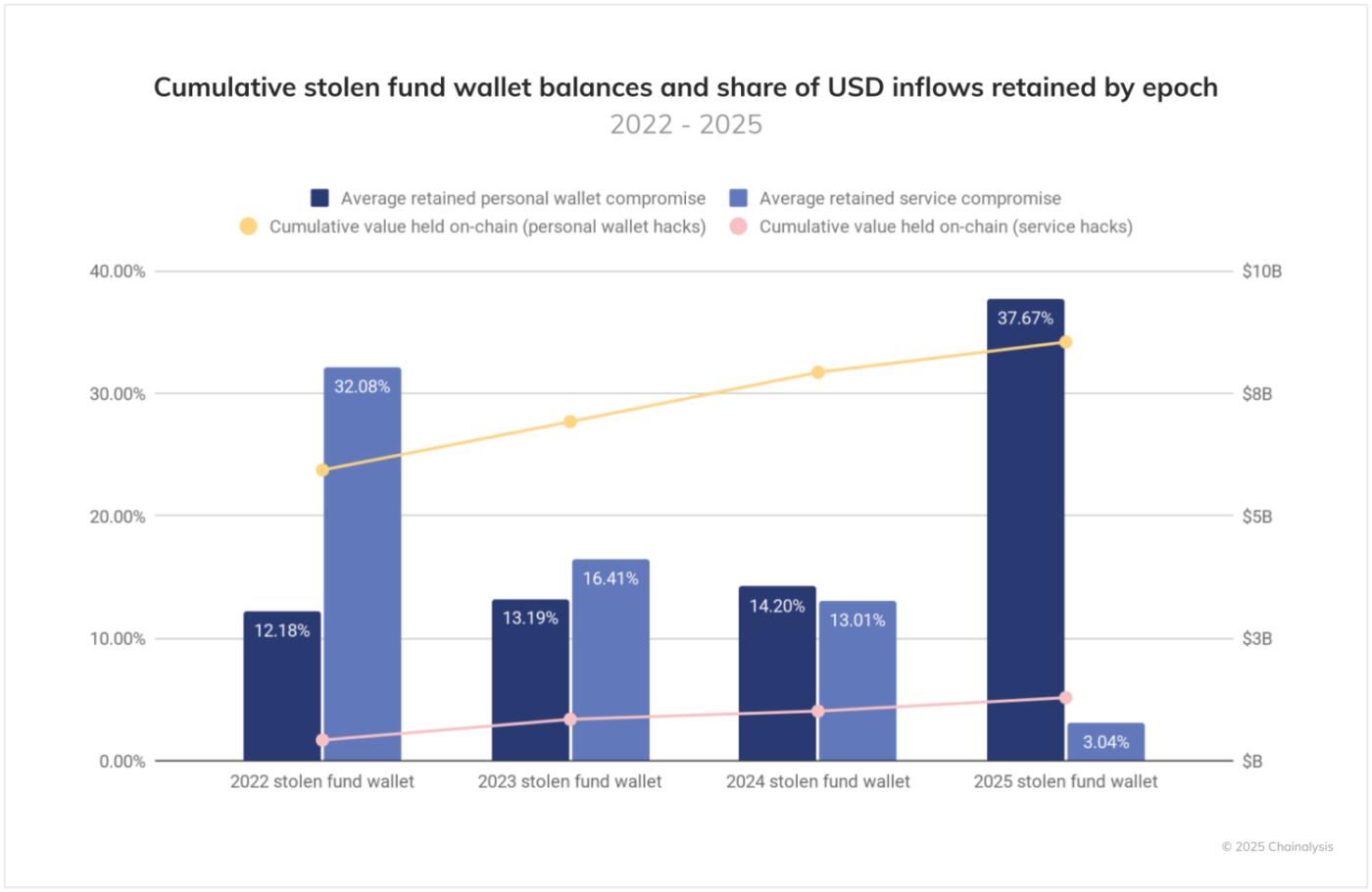
- Cyber attackers targeting personal wallets are increasingly leaving large amounts of stolen assets on-chain without immediate laundering. Currently, $8.5 billion in cryptocurrency stolen from personal wallets remains on-chain, compared to $1.28 billion stolen from services.
Changing Illegal Trading Environment
In 2025, illegal trading is proceeding at an unprecedented pace, with total amounts matching or exceeding last year's estimated $51 billion. This occurs amid significant changes in illegal actors' activities, such as the closure of the Russian cryptocurrency exchange Garantex and potential FinCEN special measures against the Huione Group. These changes are impacting how criminals move funds through the ecosystem.
In this context, stolen fund transactions have emerged as the most critical issue in 2025. While other illegal activities show diverse trends compared to the previous year, the surge in cryptocurrency theft represents an immediate threat to ecosystem participants and a long-term challenge for the industry's security infrastructure.
Service Fund Outflow Proceeding at Unprecedented Pace
Cryptocurrency theft from services (platforms) in 2025 vividly illustrates the escalating threat. The orange line showing year-to-date trends broke through $2 billion by June, an unprecedented increase for the first half of the year.
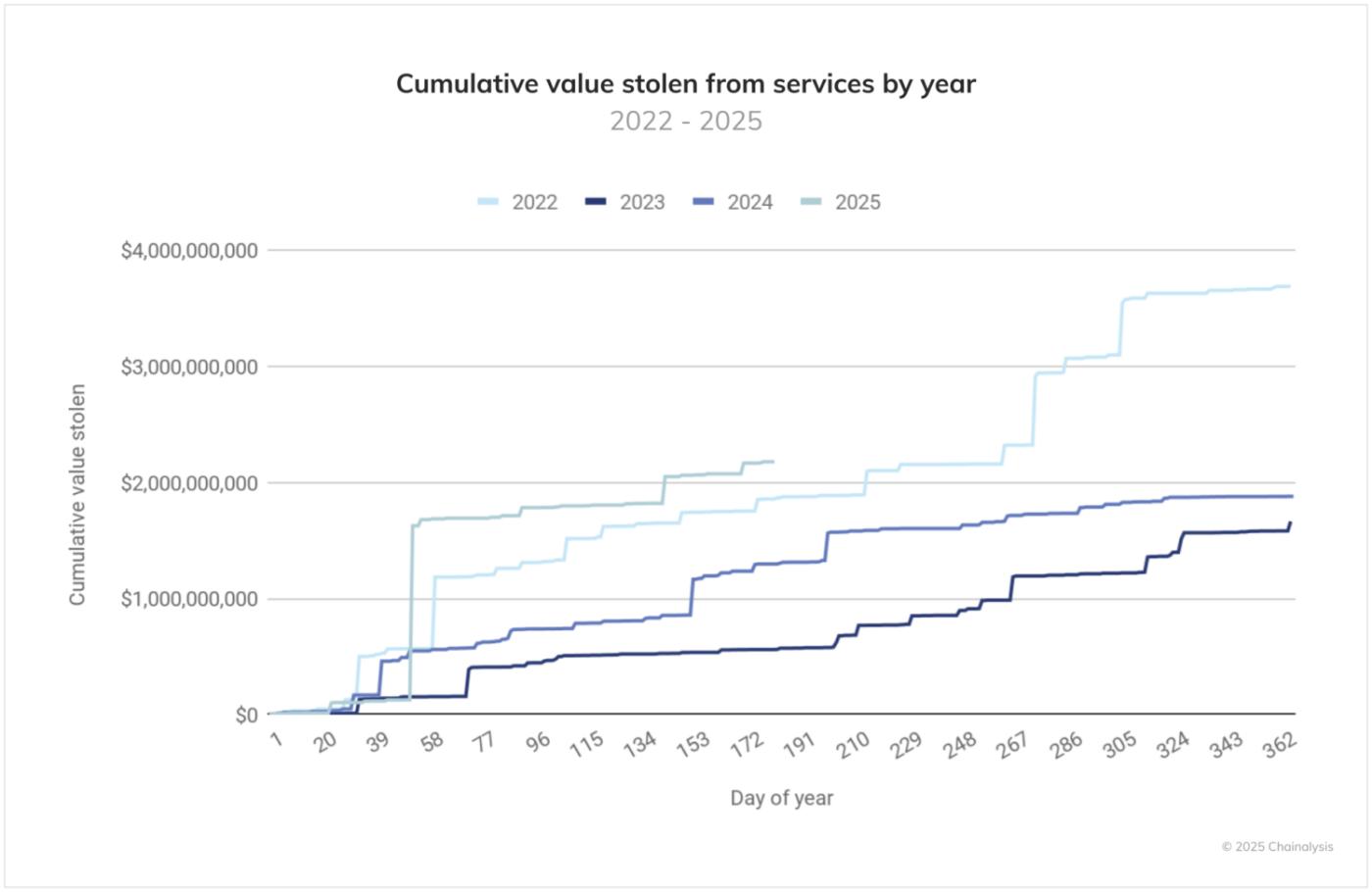
According to our data, service theft amounts continue to rise, particularly notably in 2025. In the worst year of 2022, it took 214 days to reach $2 billion in damages, while in 2025, the same scale was reached in just 142 days, significantly accelerating the damage expansion rate.
While 2023 and 2024 showed relatively moderate increases, 2025 has already worsened by 17.27% compared to 2022 by the end of June. If this trend continues, service-related theft damages could exceed $4.3 billion by the end of 2025.
Bybit Hacking Incident: A New Cyber Crime Threat
The North Korean hacking of Bybit has had a significant impact on the entire cryptocurrency industry. In the February 2025 incident, damages reached $1.5 billion, accounting for approximately 69% of cryptocurrency theft this year and becoming the largest in history. This reveals a phase shift from the temporary reduction in hacking damages seen in the latter half of 2024 to the emergence of a new threat from state-sponsored attackers.
This large-scale breach is seen as part of North Korea's efforts to strengthen sanction evasion strategies using cryptocurrency. North Korea-related cryptocurrency losses reached $1.3 billion in 2024, which was the worst at the time, but 2025 is already surpassing that.
The attack is believed to have used sophisticated social engineering methods similar to those previously employed by North Korea, such as hijacking IT personnel to infiltrate cryptocurrency-related services. The effectiveness of this approach is supported by a recent UN report about Western technology companies.
Personal Wallets: A New Target in Crypto Asset Crimes
Chainalysis has developed a new method to identify and track theft originating from personal wallets, which has been insufficiently reported but is increasing in importance. This improved visibility reveals a concerning trend where attackers are diversifying their targets and methods over time.
As shown in the graph below, the proportion of attacks on personal wallets in the overall ecosystem's theft amount is gradually increasing, with several factors potentially contributing to this trend.
- Enhanced Security of Major Services: Attackers are shifting their focus to individuals who are easier to attack.
- Increase in Individual Crypto Asset Holders: The number of individuals holding crypto assets is increasing.
- Increased Asset Value in Personal Wallets: As major asset crypto prices continue to rise, the value of crypto assets stored in personal wallets is also increasing over time.
- Development of Advanced Targeted Attack Methods: The proliferation of easily deployable LLM AI tools may lead to the development of more sophisticated attacks targeting individuals.
The Philippine National Police (PNP) claims that the gaming companies 9 Dynasty Group and White Horse Club conducted sophisticated money laundering after kidnapping, using electronic wallets, dummy accounts, and digital assets to convert ransom paid in Philippine pesos and US dollars into crypto assets to conceal the source of funds.
Our Global Services team utilized Chainalysis Reactor and collaborated with PNP investigators to track the ransom flow. Blockchain analysis revealed that multiple ransom payments were collected through a series of intermediate addresses and further laundered through additional intermediate addresses. Chainalysis successfully worked with PNP to contact Tether and freeze some funds held in USDT.
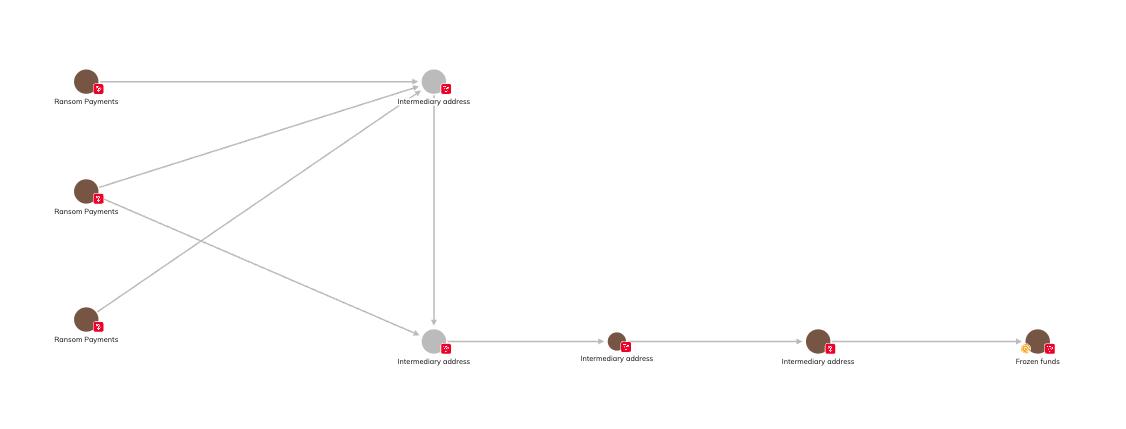
The adopted laundering method was relatively simple, matching patterns seen in many organized crime groups using crypto assets without advanced technical expertise. While traditional financial investigations often have evidence scattered across multiple institutions, blockchain provides a single, reliable, and immutable ledger. This allows investigators to track fund movements in real-time, visualize networks, and obtain international leads.
The tragic deaths of Anson Que and Armani Pavillo remind us of the human lives lost behind these crimes. However, their case also demonstrates how blockchain technology's immutability is a powerful tool for achieving justice, making it impossible for exploiters to easily hide in digital darkness.
Victim Situations by Country and Region
Chainalysis estimates global theft spread by cross-referencing reliable geolocation data with reported individual wallet theft cases. This study is limited to theft incidents where definitive geographic information can be identified and does not comprehensively cover global theft fund activities in 2025.
According to 2025 data, countries with the most individual wallet theft cases include the United States, Germany, Russia, Canada, Japan, Indonesia, and South Korea. The regions with the highest theft case increase rates from the first half of 2024 to the first half of 2025 were Eastern Europe, MENA (Middle East and North Africa), and CSAO (Central, South Asia, and Oceania).
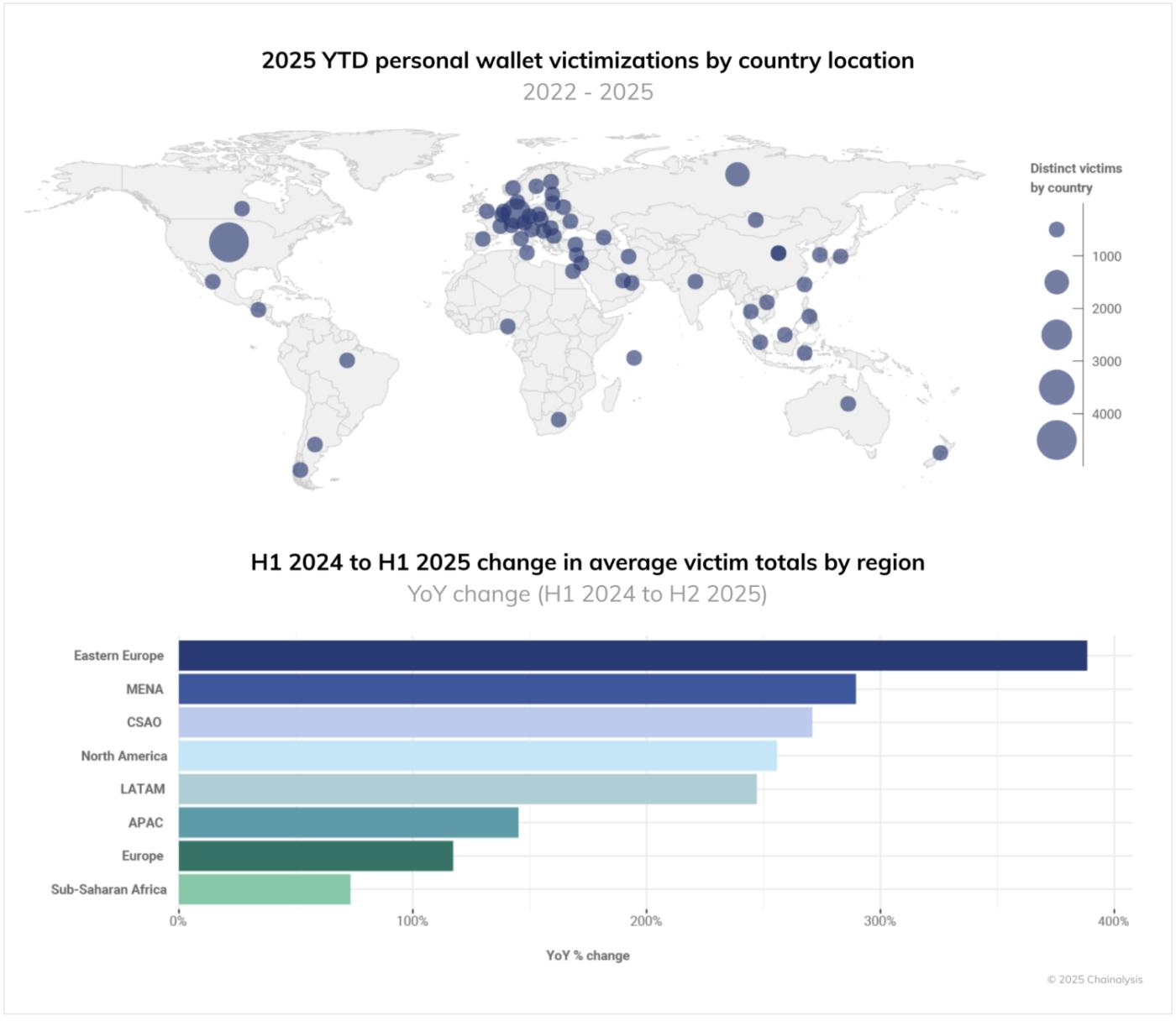
The 2025 analysis revealed significant differences in theft amounts per victim across countries. While the United States, Japan, and Germany remain at high levels, countries like the United Arab Emirates, Chile, India, Lithuania, Iran, Israel, and Norway have newly ranked high, highlighting a globally serious victim situation.

When moving illegally obtained proceeds, perpetrators always pay high fees, which vary significantly depending on the period. Interestingly, despite the overall decline in transaction costs due to the popularity of Solana and Layer2, theft fund perpetrators continue to pay higher average fees during the same period.
Specifically, from 2022 to early 2025, while the overall average fee decreased by 89%, the premium paid by theft fund perpetrators (additional charges on top of the base fee) increased by 108% during the same period. Moreover, cyber attackers targeting cryptocurrency exchanges tend to pay higher premiums compared to those targeting individual wallets. This is likely due to the need to quickly move large funds before they can be detected and frozen.
Most cryptocurrency theft incidents are motivated by financial gain. However, a notable recent exception is the approximately $90 million asset outflow incident at Nobitex, Iran's largest cryptocurrency exchange, in June 2025. This incident is considered an attack with geopolitical intentions by a pro-Israeli group. According to Chainalysis analysis, the perpetrators' wallets were temporary "burner addresses" with no access to private keys, suggesting that this outflow was driven by political motives rather than traditional financial objectives.
Furthermore, many theft fund perpetrators do not prioritize optimizing on-chain transaction costs (fees), but instead focus primarily on the speed of fund movement and transaction finality. This is because it is crucial for perpetrators to have transactions quickly confirmed to reduce the risk of tracking or interception.
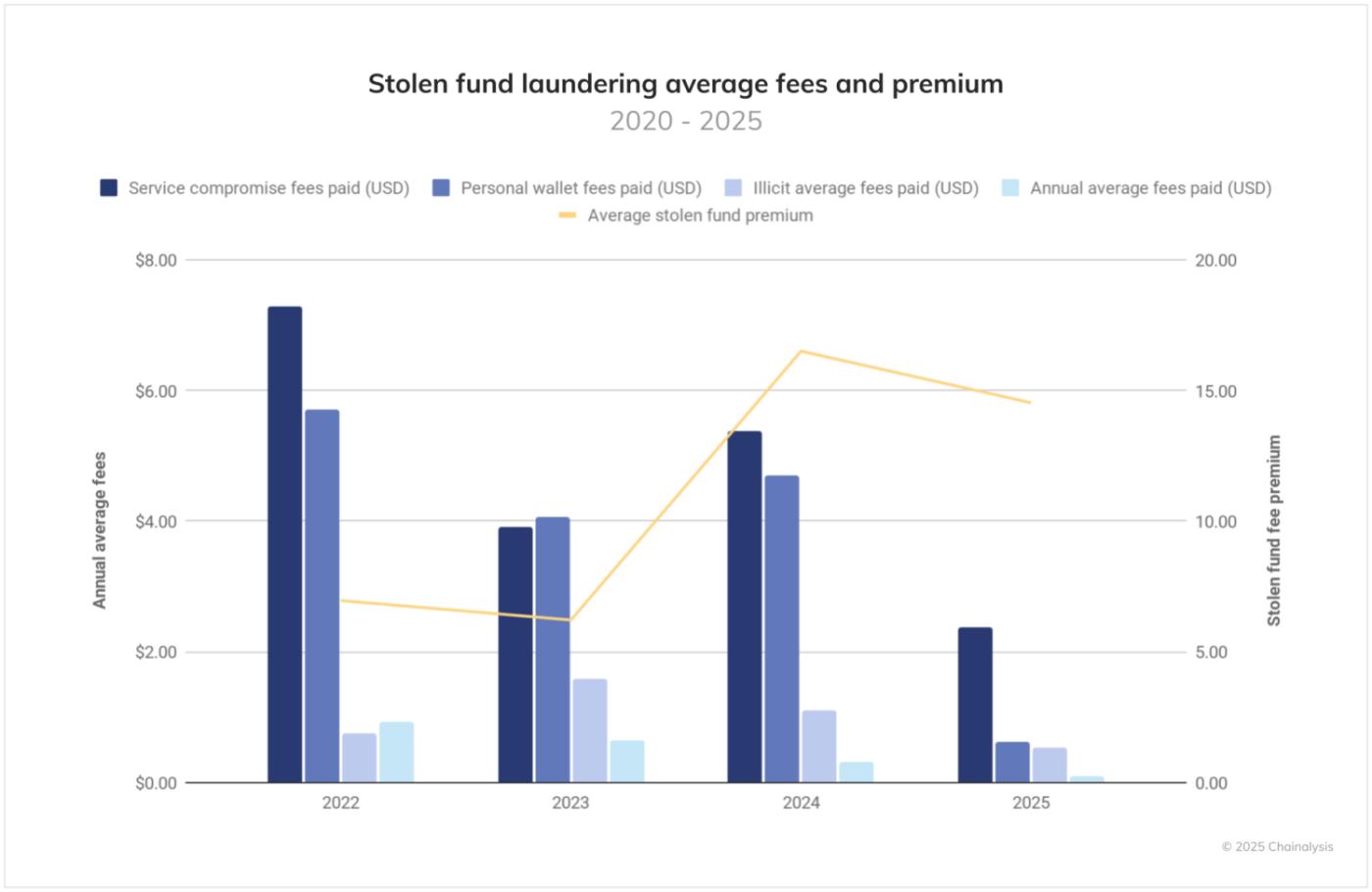
Not all stolen funds immediately enter the laundering cycle. Particularly in cases of personal wallet hacking, there is an increasing trend of theft funds remaining on-chain, with significant balances held in addresses controlled by attackers. These funds are not immediately laundered on-chain or converted to fiat currency. Such "HODLing" behavior by criminals suggests either confidence in their operational security or the possibility of treating stolen funds as an investment.
Prevention and Risk Reduction Strategies to Prevent Victimization
Security Measures for Service Providers
- Fostering a robust security culture
- Conducting regular security audits
- Introducing employee screening processes that can detect social engineering attempts
- Code audits are becoming increasingly important as smart contract vulnerabilities are a major attack vector
- Improving wallet technical infrastructure, particularly introducing multi-signature hot wallet addresses, is crucial for enhancing institutional investor security. This allows risks to be minimized through layered security, even if one private key is compromised
Security Measures for Individual Users
- Operational Security: There is a correlation between violent attacks and crypto asset (e.g., Bitcoin) price fluctuations, making operational considerations like not disclosing asset holdings externally important. Additionally, technical measures such as exchanging to privacy coins and utilizing cold storage wallets are effective.
- Physical Security: In countries with increasing incidents, extreme caution is necessary regarding digital footprints and real-world safety. Crypto asset-related kidnappings and violent crimes are increasing, making personal physical security an urgent issue.
- Incidents targeting famous holders and their families have been reported, and digital asset holders must actively implement traditional physical crime prevention measures. These include:
- Not publicly displaying assets or wealth
- Not posting about crypto asset ownership or trading on social media
- Deliberately changing daily behavior patterns
- Being attentive to suspicious surveillance








