Overview of Cross-Chain Bridge Theft Incidents
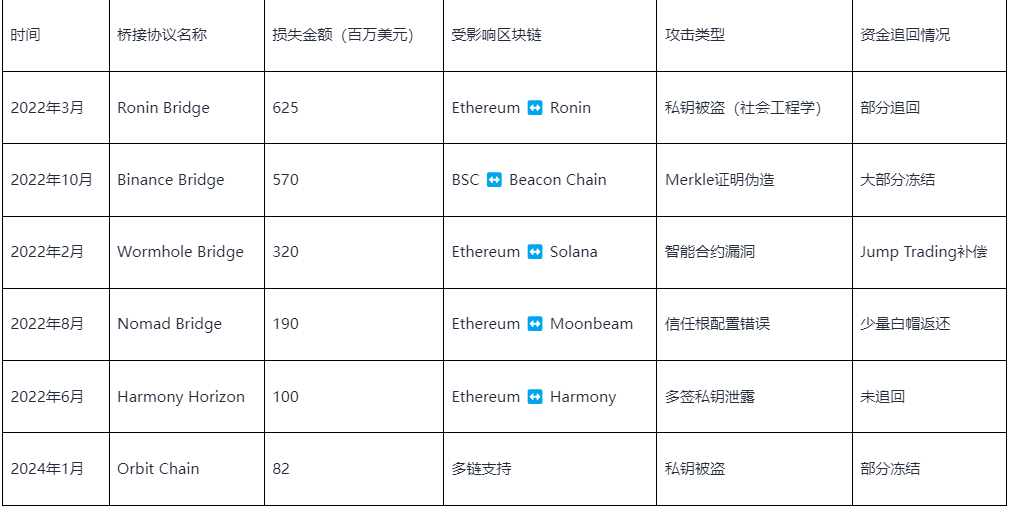
From 2022 to 2024, multiple shocking security incidents occurred in the cross-chain bridge field. The most prominent include: the Ronin Bridge attack in March 2022 with a loss of $625 million, the Binance Bridge attack in October of the same year with a loss of $570 million, the Wormhole Bridge attack in February with a loss of $320 million, the Nomad Bridge attack in August with a loss of $190 million, the Harmony Horizon Bridge attack in June with a loss of $100 million, and the Orbit Chain attack in January 2024 with a loss of $81.5 million.
These data clearly reveal a brutal reality: 2022 became the "darkest moment" for cross-chain bridge security, with annual losses exceeding $1.8 billion. These attacks not only caused massive economic losses but, more importantly, exposed fundamental flaws in the security architecture design of current cross-chain infrastructure.
Ronin Bridge: The Perfect Social Engineering Crime
On March 23, 2022, the Ronin Bridge supporting the world's most popular blockchain game Axie Infinity suffered the most severe cross-chain bridge attack in crypto history. The attackers, through a carefully planned social engineering attack, successfully stole 173,600 ETH and 25.5 million USDC, with a total value of over $625 million. This attack not only set a record for single-incident losses but also demonstrated the vulnerability of traditional multi-signature mechanisms when facing organized and premeditated attacks.
(Translation continues in the same manner for the rest of the text)Step 4: Create Malicious Message After the verification process was compromised, the attacker called the post_vaa function, using the "verified" signature obtained in the previous steps to create a malicious message account, specifying the minting of 120,000 wETH. Specific transaction: https://solscan.io/tx/2SohoVoPDSdzgsGCgKQPByKQkLAXHrYmvtE7EEqwKi3qUBTGDDJ7DcfYS7YJC2f8xwKVVa6SFUpH5MZ5xcyn1BCK
Step 5: Execute Malicious Minting The attacker called the complete_wrapped function, processing the data contained in the malicious message account created in the post_vaa step, ultimately successfully minting 120,000 wETH tokens. Specific transaction: https://solscan.io/tx/2zCz2GgSoSS68eNJENWrYB48dMM1zmH8SZkgYneVDv2G4gRsVfwu5rNXtK5BKFxn7fSqX9BvrBc1rdPAeBEcD6Es
Step 6: Complex Fund Dispersion After minting wETH, the attacker immediately began complex fund transfer operations:
- 16,879.39 ETH converted to 269,356.66 SOL
- 1,866 ETH exchanged for 4.9 million USDC
- 7,504 ETH exchanged for 18 million USDC
- 18,044,852.11 USDC converted to 122,049 SOL
Jump Trading's Unprecedented Rescue
Within 24 hours of the attack being discovered, Jump Trading (Wormhole's parent company) made an astonishing decision: injecting 120,000 ETH into the Wormhole protocol to cover all losses, ensuring the safety of all wETH holders. Jump Trading stated: "We believe in a multi-chain future, and Wormhole is critical infrastructure. That's why we replaced 120,000 ETH to make the community whole and support Wormhole's continued development."
While this action saved user funds, it also exposed the severe dependence of current cross-chain bridge infrastructure on centralized entities. The ultimate solution still relies on fund injection by centralized entities, which starkly contrasts with the decentralization ideology.
Root Causes of the Vulnerability
The core issues exposed by this attack include:
- Code Management Oversight: Continued use of the known risky deprecated function load_current_index
- Insufficient Input Verification: Failure to verify the authenticity of critical account addresses
- Deployment Process Defects: Security patches not timely deployed to production environment
- Architectural Dependency Risk: Excessive reliance on final guarantees from centralized entities
The key to the attacker's success was exploiting functions marked as "deprecated" in the Solana SDK. These functions lack verification of account address authenticity when handling sysvar:instructions accounts, allowing attackers to create fake Sysvar accounts and bypass the entire verification system.
Nomad uses an optimistic verification mechanism to verify cross-chain messages through a "Trusted Root" system. Each valid cross-chain message updates the trusted root, while invalid messages are marked as "untrusted". During a routine protocol upgrade, the development team made a seemingly minor but catastrophically consequential error: setting the "trusted root" value to 0x00. The problem was that 0x00 was also the default value for the "untrusted root", meaning the system could not distinguish between valid and invalid messages, and all messages were automatically marked as "verified".
On August 1, 2022, a user (later confirmed to be an attacker) discovered an anomaly: sending 0.01 WBTC from Moonbeam to the bridge, but receiving 100 WBTC from the Ethereum side. This 1:10000 exchange ratio immediately exposed the system's serious vulnerability. Once the first successful attack transaction was discovered, the situation quickly spiraled out of control. First, technical personnel who understood the vulnerability began manually constructing attack transactions, then other users discovered they could simply copy successful transactions and modify the receiving address to profit, and finally MEV (Maximum Extractable Value) bots joined in, automatically executing similar transactions.
During this approximately 4-hour "attack feast", over 300 addresses participated in thousands of attack transactions, almost completely depleting Nomad bridge's liquidity pool. In this "everyone participates" fund plundering, some white hat hackers also participated, later voluntarily returning about $32 million in funds, receiving a 10% reward. The Nomad team also requested other fund recipients to voluntarily return funds, promising a 10% reward, but with few responses.
The directly exposed issues include configuration value conflicts causing trusted and untrusted roots to use the same default value, insufficient pre-upgrade testing that failed to discover edge cases, and seemingly simple configuration modifications not receiving sufficient code review attention. The deeper problem lies in the optimistic verification mechanism's systemic risk of overly relying on a single trusted root, and the permissionless nature of blockchain that amplifies losses during system failures. This event became a classic case in blockchain security history, illustrating that in complex systems, any seemingly minor error can lead to catastrophic consequences.
- Orbit Chain: Systematic Compromise of Multi-Signature Private Keys
On January 1, 2024, the first day of the new year brought an ominous beginning for cross-chain bridge security. The multi-chain cross-chain bridge protocol Orbit Chain was attacked, with losses reaching $81.5 million, becoming the first major cross-chain bridge security incident in 2024. This attack again exposed the vulnerability of traditional multi-signature mechanisms when facing systematic attacks, with even a seemingly more secure 7-of-10 multi-signature architecture struggling to resist organized attacks.
Orbit Chain uses a 10-node multi-signature architecture requiring 7 nodes to agree to execute transactions. This 7-of-10 design should theoretically provide sufficient security, as attackers would need to control 70% of validation nodes to succeed. However, on the first day of 2024, attackers obtained the private keys of 7 out of 10 validation nodes through undisclosed means, precisely reaching the minimum threshold required to execute arbitrary transactions.
The stolen assets included $48.1 million in USDT, $16.7 million in USDC, $8.3 million in DAI, $5.4 million in WBTC, and $3 million in ETH, among other mainstream cryptocurrencies. The attackers used a money laundering strategy similar to the Harmony bridge attack, first quickly transferring funds to multiple addresses for dispersion, then cleaning the fund trail through mixing services like Tornado Cash, and finally using other cross-chain services to continue transferring funds to avoid tracking.
The key issue in this attack was the simultaneous leakage of 7 private keys, exposing systemic deficiencies in Orbit Chain's private key management. Despite using a multi-signature architecture to distribute risk, private key management still faced centralized single point of failure risks. Insufficient internal security controls allowed attackers to simultaneously obtain private keys from multiple validation nodes, and the lack of real-time monitoring and automatic suspension mechanisms for abnormal transactions provided attackers ample time to complete fund transfers.
This event demonstrates that even a higher-threshold multi-signature architecture cannot effectively resist organized attacks if there are flaws in key management and internal security controls. Traditional multi-signature mechanisms, while dispersing risk to some extent, fundamentally still rely on the assumption that "most validators will not be compromised simultaneously" - an assumption that often does not hold in the face of systematic attacks.
Facing a severe security situation, the industry is exploring various technological solutions. Zero-knowledge proof bridges utilize ZK-SNARKs/STARKs technology to achieve trustless verification, fundamentally eliminating dependence on centralized verification nodes. Multi-Party Computation (MPC) architecture significantly raises the threshold for single-point attacks through private key fragmented storage and distributed signatures. Formal verification uses mathematical methods to prove the correctness of smart contract logic, preventing the possibility of verification bypassing at the code level. Real-time monitoring and automatic suspension systems, driven by AI-powered abnormal transaction detection and automated emergency response mechanisms, greatly reduce the time for attack discovery and response.
Conclusion: Redefining the Future of Cross-Chain Security
Through detailed analysis of six major cross-chain bridge attacks, we can clearly see the fundamental flaws in the security architecture design of current cross-chain infrastructure. The cumulative loss of $2.8 billion is not just a number, but represents real asset losses for tens of thousands of users and reflects systemic security issues in the entire Web3 infrastructure.
The fundamental problem currently facing cross-chain bridges lies in the flaws of the trust model. The vast majority of cross-chain bridges rely on the assumption that "a few verifiers will not act maliciously," which is extremely vulnerable when facing organized and premeditated attacks. The contradiction between complexity and security is increasingly prominent, as cross-chain bridges need to handle the heterogeneity of multiple blockchains, which naturally increases security risks. Meanwhile, the potential gains for attackers far exceed the cost of security protection, creating an asymmetric game relationship that provides strong economic incentives for attacks.
A true solution requires simultaneous action on technical, governance, and economic levels. At the technical level, cryptographic methods must be used to completely eliminate dependence on human trust, ensure the mathematical correctness of code logic through formal verification, and establish a multi-layered defense system rather than relying on a single security mechanism. At the governance level, unified industry security standards and best practices need to be established, promoting regulators to develop targeted compliance frameworks and strengthen cross-project security information sharing and collaboration. At the economic level, more reasonable economic incentive mechanisms should be designed, establishing industry-level security insurance and compensation funds to increase attack costs and reduce attack returns.
The future of cross-chain bridges should not be built on the fragile foundation of "praying for verifier honesty," but on cryptographic guarantees that "even if all participants attempt to act maliciously, they cannot succeed." Only by fundamentally redesigning cross-chain security architecture and breaking free from dependence on centralized trust can we truly achieve secure and reliable multi-chain interoperability. In this challenging era, those who can provide truly decentralized, mathematically provable secure cross-chain solutions will become beacons leading the industry out of the security shadow.
The future of Web3 depends on the security architecture choices we make today. History has told us with the painful cost of $2.8 billion that traditional security models can no longer meet the development needs of decentralized finance. It is time to thoroughly rethink and redesign cross-chain security architecture. Let us work together to build a truly secure and trustworthy multi-chain ecosystem.







