*This article has been automatically translated. Please refer to the original article for accurate content.
On August 27, 2025, the U.S. Treasury Department's Office of Foreign Assets Control (OFAC) announced sanctions against a rogue IT worker network linked to North Korea (DPRK) . Vitaliy Sergeyevich Andreyev (a Russian national) was facilitating payments to Chinyong Information Technology Cooperation Company (Chinyong, also known as Jinyong IT Cooperation Company), and the cryptocurrency addresses used for this purpose were also included in the sanctions. Chinyong was sanctioned by OFAC and the South Korean Ministry of Foreign Affairs (MOFA) in May 2023.
The sanctions also include Kim Ung Sun, Shenyang Geumpungri Network Technology Co., Ltd., and Korea Sinjin Trading Corporation, who are alleged to have been involved in diverting revenues earned by North Korean IT workers to fund North Korea's weapons of mass destruction and ballistic missile programs.
North Korean IT Worker Network: A Source of Funding for Weapons of Mass Destruction
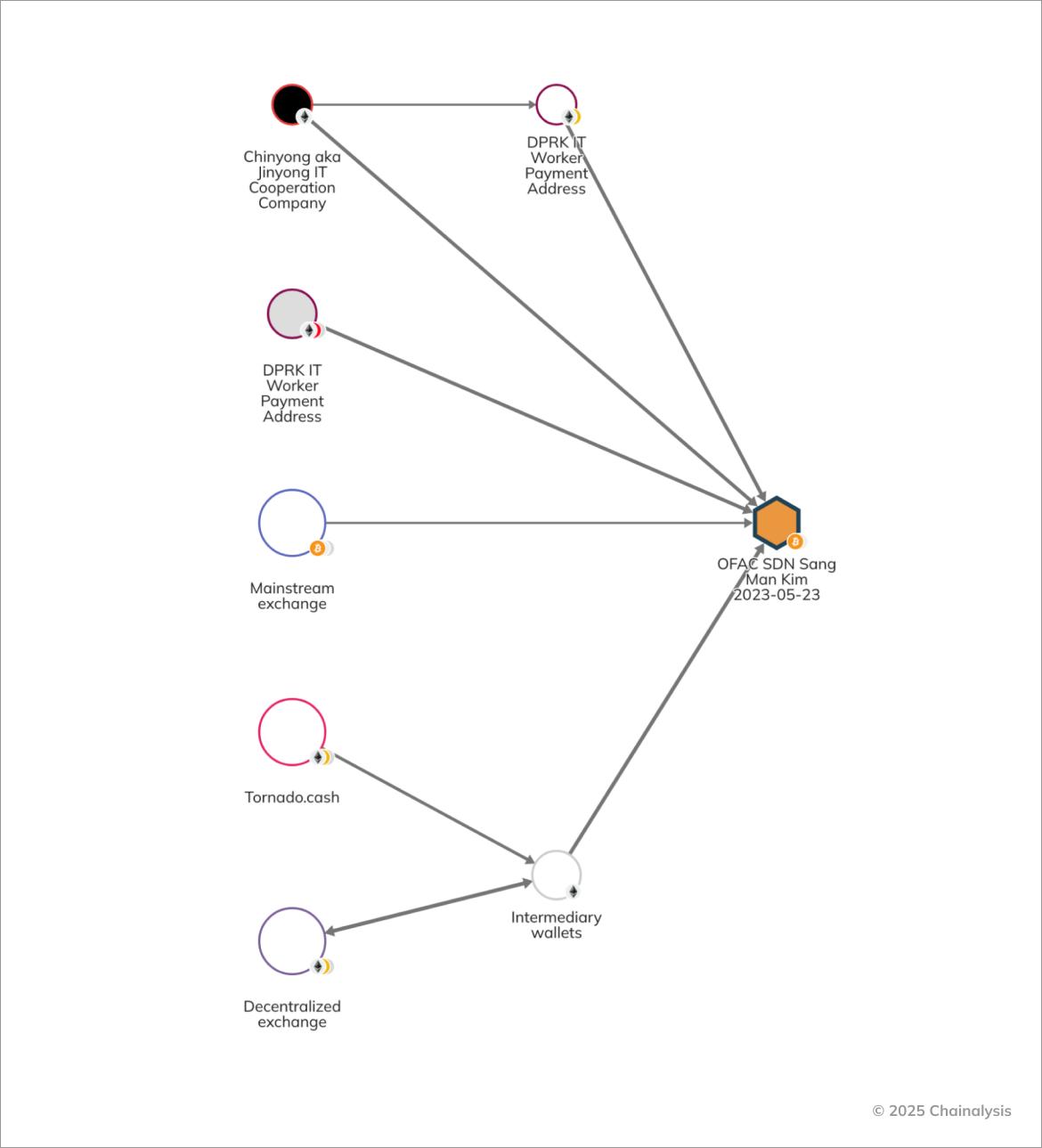
These sanctions continue OFAC's previous actions against North Korean IT worker networks. In May 2023, OFAC designated Chinyong Information Technology Cooperation Company and its employee, Sang Man Kim, as targets of sanctions, and at the same time disclosed their cryptocurrency addresses.
In this network, North Korean IT workers are sent overseas to infiltrate ordinary companies under false names, stealing confidential information and launching ransomware attacks. They are then paid in cryptocurrency. The funds are then sent back to North Korea, where they are used to fund the development of weapons of mass destruction.
Analysis using the investigative tool Reactor revealed that Chinyong and Kim laundered funds by combining mainstream services, decentralized finance (DeFi), mixers, etc. It was also confirmed that funds were transferred directly from the wallets of Chinyong and North Korean IT workers to the deposit addresses of services operated by Kim.
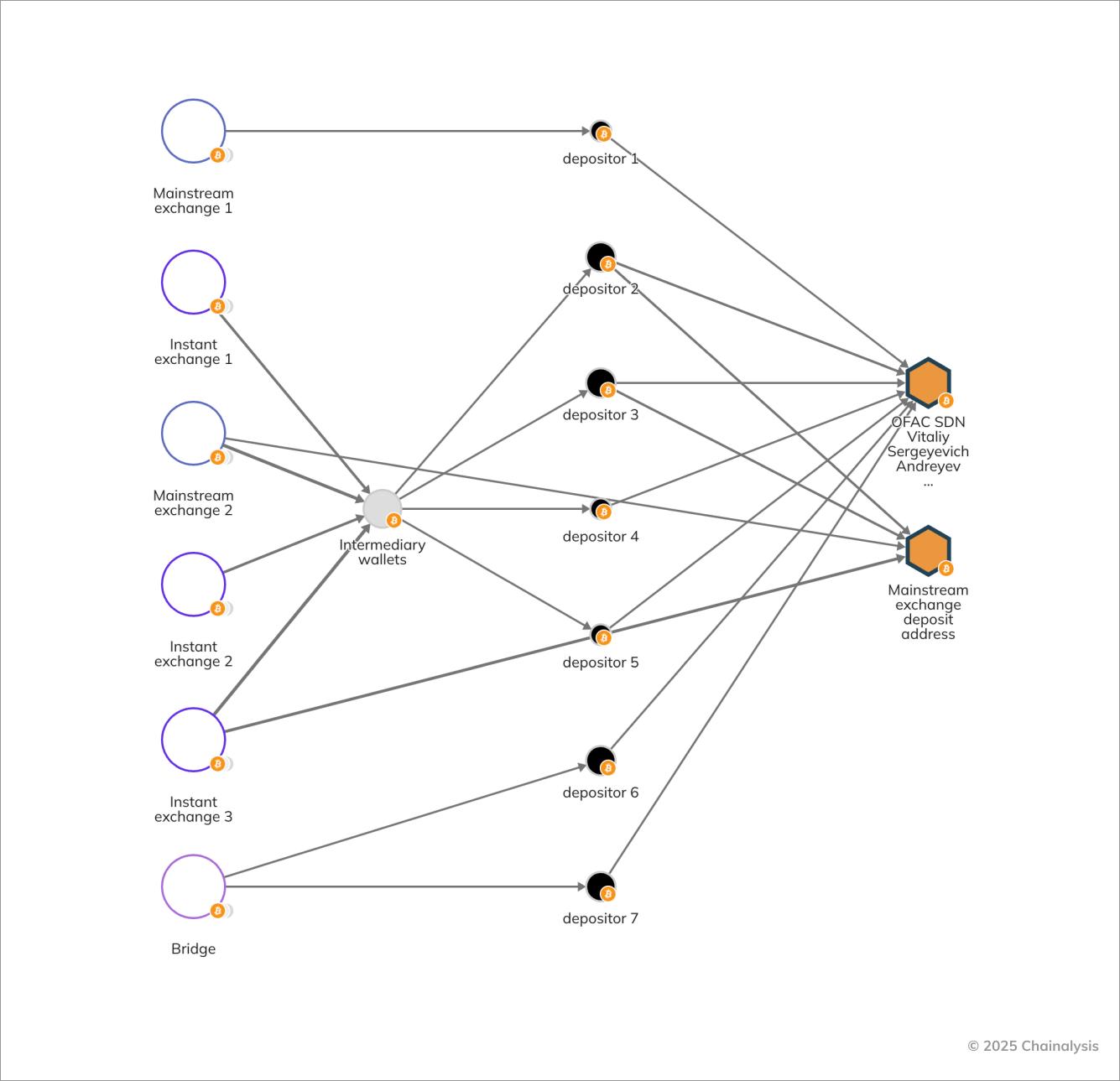
The sanctions include Andreyev's bitcoin address, which he allegedly used to facilitate transfers to Chinyong. Andreyev, working with Kim Ung Sun, North Korea's economic and trade consul in Russia, transferred over $600,000 in total by converting crypto assets into cash.
As illustrated in the reactor graph, Andreyev's address is a deposit address for a common exchange (centralized exchange: CEX), which has been repeatedly used for money laundering by North Korean IT workers. Multiple money laundering operations using this address are supported by its usage history for exchanges, bridges, and decentralized finance (DeFi) protocols , and according to OFAC documents, more than $600,000 has been confirmed to have been deposited into Andreyev's address.
Strategic Countermeasures Against State-Sponsored Cryptocurrency Fraud
By imposing sanctions on Andreyev, Kim Ung Sun, and their associated front companies, OFAC seeks to disrupt North Korea's illicit revenue streams. These sanctions further shed light on the growing network of North Korean IT workers overseas, their fraud targeting of U.S. companies, and the funding of their weapons programs.
These sanctions, along with other recent actions targeting North Korean IT worker networks, indicate that the infrastructure and financial intermediaries that support the regime through cryptocurrency will continue to be a key focus of regulatory enforcement.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient's use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claims attributable to errors, omissions, or other inaccuracies of any part of such material.
The post North Korean IT workers, cryptocurrency money laundering, and weapons financing: New OFAC sanctions designations appeared first on Chainalysis .








