By Tyler Campbell
Source: https://www.unchained.com/blog/replace-key-multisig-wallet
Using a multi-signature wallet and holding your own keys to secure your bitcoins helps eliminate single points of failure: even if one of the keys that make up your wallet is lost, corrupted, or stolen, you have a fault-tolerant mechanism in place, allowing you to spend your bitcoins. However, if this happens, being able to "spend" your bitcoins is one thing, but maintaining the integrity of your wallet is another. If one of your multi-signature wallet keys becomes compromised for any reason, you should replace it as soon as possible. Attempting to replace an unnecessary key can introduce unnecessary risk.
How do I replace keys in a multi-signature wallet?
Before we consider when it's necessary to replace a key, it's helpful to first look at how to replace it.
Generate a new key — and a new safe
Think of your multi-signature wallet as a digital safe, to which you hold the key. Let's assume you're using a 2-of-3 multi-signature wallet. By analogy, your safe has two keyholes and three compatible keys. Any two of these three keys can open the safe, allowing you to access the bitcoins.
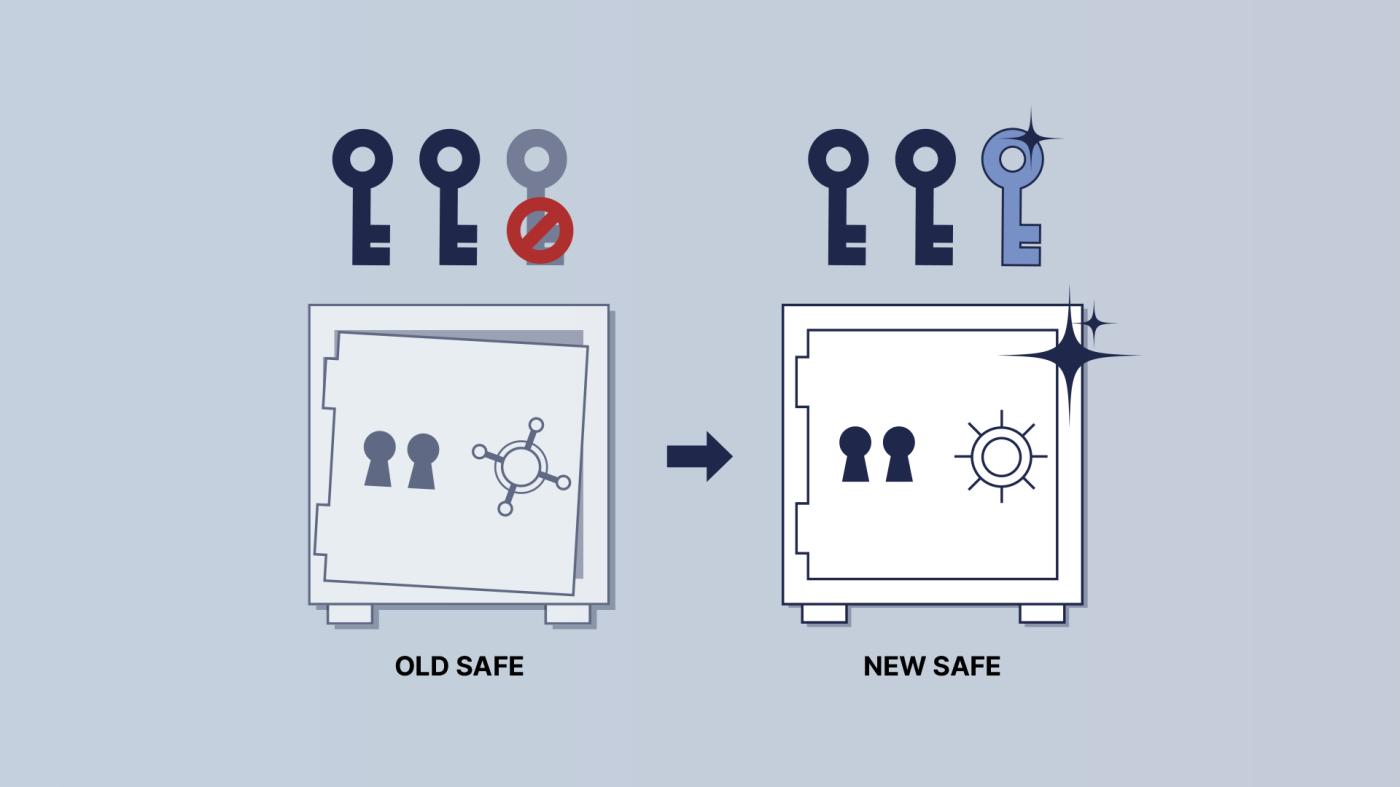
If someone steals one of your keys, or you lose it, you'll want to replace it so things don't get out of hand.
If you lose the key to a physical safe, or you want to replace it, buying a new key won't work because it won't fit your safe! If any key can open your lock, then your lock itself has no meaning, right?
Therefore, the necessary steps are to first open the old safe with your two remaining keys, transfer the contents to a new safe , and ensure that the new safe can be opened with your two original unexposed keys and a brand new key . This is the principle behind multi-signature wallet key replacement.
How to create a new multi-signature wallet installation
Let’s imagine the most common key replacement scenario: a 2-of-3 multi-signature wallet, whose keys are numbered [1], [2], and [3]. Now the key numbered [3] needs to be replaced, and we generate a new key numbered [4]. Now our goal is to replace key [3] with key [4].
In order to completely replace key [3], we first need to create a new multi-signature wallet using keys [1], [2], and [4]. Once this new multi-signature wallet is constructed, funds can be transferred from the old wallet (using signatures from keys [1] and [2]) to the new multi-signature wallet. In other words, you are transferring funds from the old, no longer secure safe to the new, sufficiently secure safe.
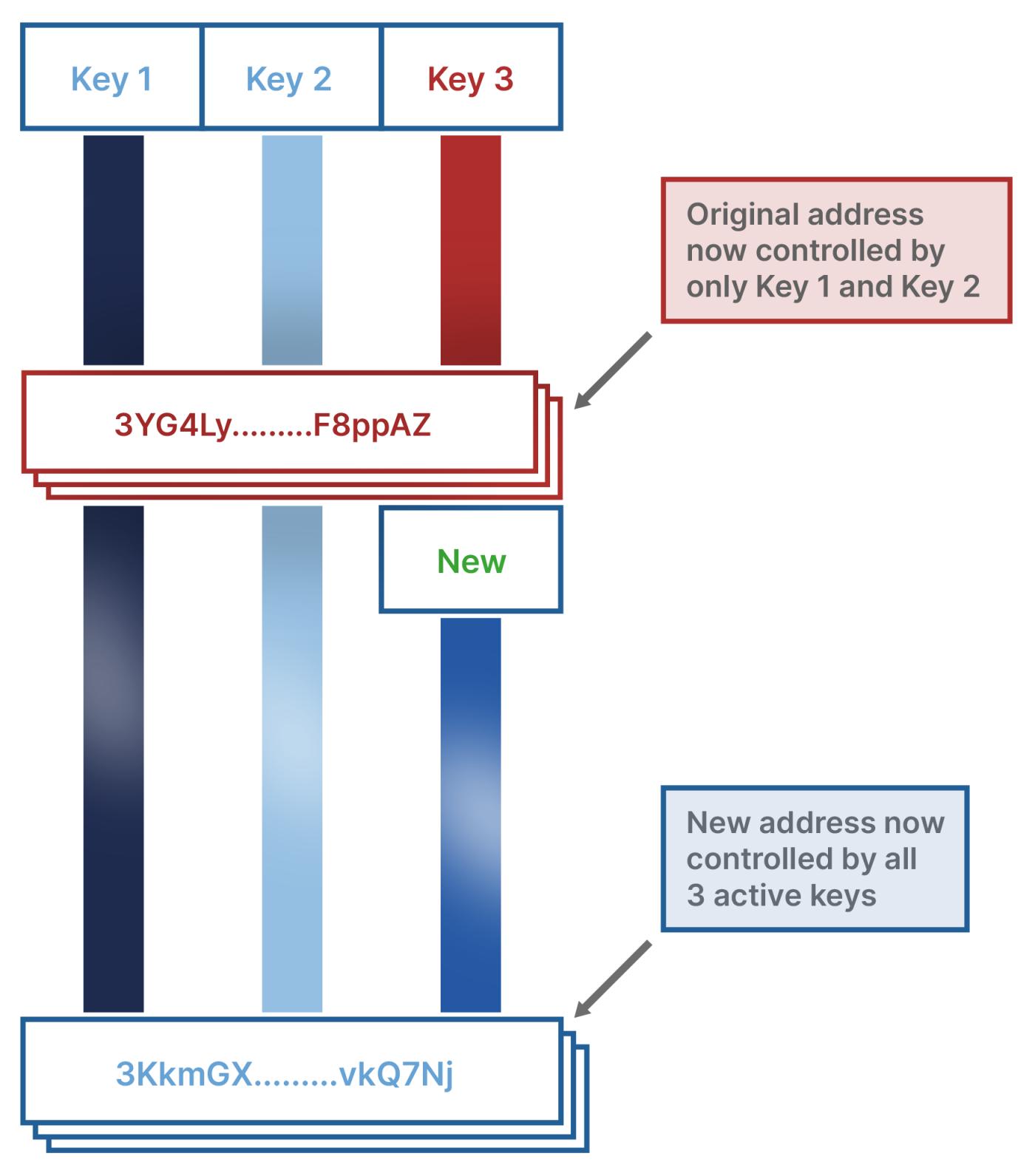
Remember: when you replace one of the keys in a multi-signature wallet setup, you are creating a brand new wallet (with a new key)! This means that any addresses in your old multi-signature wallet are not associated with or protected by this new key.
For this reason (and others), you're best off:
- Replace the key only when it is really necessary; we will explain in detail when it is necessary later.
- If you replace your keys, be sure to transfer all funds from your old wallet to your new one.
- Remember to update the whitelist addresses on exchanges and other platforms.
When do I need to replace my key?
If you think you're in a situation where you might need to replace your keys, take a deep breath. One of the benefits of multi-signature wallets is their fault tolerance. Even if one of the keys that make up your wallet becomes compromised, it's not the end of the world.
Each key in a multi-signature wallet setup consists of two components: a hardware signer and a seed word backup. In our 2-of-3 multi-signature setup , this means a total of six sensitive items—three hardware signers and three seed word backups—that need to be secured, in addition to a file describing the wallet configuration. In a jointly custodial 2-of-3 multi-signature wallet, a total of four sensitive items—two hardware signers and two seed word backups—need to be secured, plus a wallet configuration file (the third key is held by the custodial partner).
Your seed word backup is the most sensitive component of every key, as it's a human-readable representation of your key , which is used to generate all the private keys you use to spend and secure your funds. Hardware signers, while also storing your seed words and allowing you to sign Bitcoin transactions, typically come with a PIN as an additional layer of physical security.
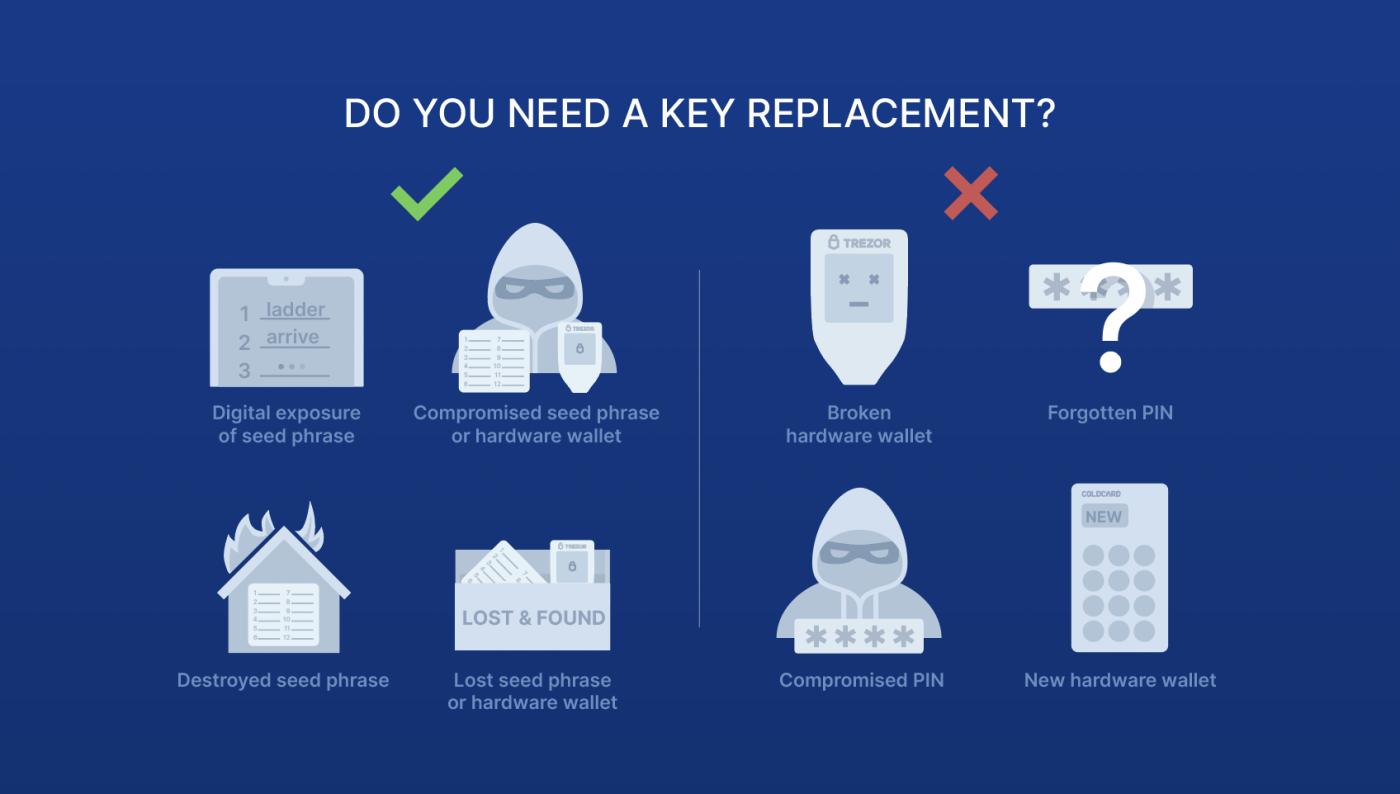
Let's look at the most common scenarios where your keys can become compromised.
Exposed seed words
An "exposed seed word" means it has been exposed to an (unintended) third party. For example, if you store your seed word in a digital file and then transfer it via internet communication, or if you take a photo of your seed word and then transfer it online, or if someone obtains a physical copy of your seed word, all of these situations mean your seed word has become exposed.
Electronic exposure risks
Most hardware signers will encourage you to save a physical backup when generating seed words, but it is very common for new users to ignore this advice and choose to use electronic devices to save seed words.
Hardware signers are specifically designed to generate seed words in a secure environment , isolated from less secure internet-connected devices. Generating seed words and then immediately storing them on a non-specific device exposes them to the potential failure of electronic storage media and the risk of malware (such as keyloggers). Even worse, you might not discover the exposure until after you've already deposited a significant amount of funds into the wallet generated by the key.
If you use electronic storage media to store your seed key, you should assume that the key has been exposed and therefore need to replace it.
Lost the seed word
Losing your seed means that you either can't determine its whereabouts or you can no longer use it. Maybe you checked your safe at home and found that your seed was not there; or maybe you lost something while traveling.
In either case, you have to assume that the seed word has been exposed, so the key needs to be replaced.
Seed word stolen
Fortunately, if you use a proper multi-signature, a single stolen seed word will not result in a loss of funds. Of course, if stolen, it must be considered lost and exposed.
You need to replace this key because a thief only needs to steal one more of your keys to get your Bitcoin (assuming they also have your multi-signature wallet key configuration file or your login credentials at a federated custodian).
Hardware signature device hijacked
Similar to seed word exposure, if your hardware signer is lost or stolen, you must also replace the key stored in it in your multi-signature wallet. Even if the signer has a PIN that prevents immediate access to the key, you should still assume that the key is exposed, especially since there have been cases where certain devices allow attackers to completely bypass the PIN protection.
Lost hardware signer
If you can’t pinpoint the whereabouts of your device, you won’t know if any of its seed words have been exposed or will be exposed in the future.
At this point, you should assume that the seed key has been exposed, so you need to replace the key for your multi-signature wallet installation.
Hardware signature device stolen
If your device disappears from your safekeeping location, is discovered during your regular inspections (we always recommend quarterly inspections), or disappears from your personal belongings while you are traveling, your hardware signature device may have been stolen.
At this point, you should assume that the seed key has been exposed, so you need to replace the key for your multi-signature wallet installation.
When is it not necessary to replace the key?
The physical copy of your seed is the most sensitive part of a key. If you have reason to believe your seed has been lost or exposed, you should replace the key. However, there are often situations where replacing the key is unnecessary. In fact, in these situations, replacing the key may be more risky than not replacing it.
Some of the risks and costs of replacing keys unnecessarily include:
- Transaction fees : Replacing the key means that you have to move all funds from the old multi-signature wallet address to the new multi-signature wallet address. This requires the blockchain network to confirm your transaction, so you have to pay the block confirmation fee.
- Moving large amounts of Bitcoin : There is always the possibility of errors when transferring Bitcoin, and switching to a new wallet may require moving large amounts of Bitcoin.
- Wallet configuration file : Your multi-signature wallet configuration file should also be kept somewhere safe, and replacing the key means replacing it as well (i.e. accessing this safe location).
- Whitelisted Addresses : Any whitelisted or “fixed” addresses (belonging to your old wallet) that you may be using on an exchange or other service must be updated to addresses from your new wallet.
For these reasons, you should understand when it is not necessary to replace your key. The commonality in all of these situations is that they only affect your signer and do not affect your seed word backups.
Hardware or software failure
If your hardware signer is completely destroyed (e.g., in a fire or flood), or becomes bricked due to an unidentified software or hardware failure (e.g., an error during a firmware update, a malfunctioning USB port, or a non-functional display), you can import your seed words into a new device. As long as your backup is secure, there's no need to replace your key.
If only your signer device is damaged, and your seed key backup is still intact and not exposed, then you can safely assume that your seed key has not been exposed and your hardware signer has not been hijacked, so there is no need to replace this key in the multi-signature wallet.
Lost or forgotten PIN
Similarly, if you simply forget the PIN you set on a device, you can restore the device to factory settings and re-import the seed words, or you can buy a new device and import the seed words. (Translator's note: Note that the security of these two methods is not equivalent. If you are replacing a new hardware signer, you should make sure to clear the old signer (i.e., restore it to factory settings)).
As long as your seed key backup is intact and not exposed, you can safely assume that your seed key has not been exposed and your hardware signer has not been hijacked, so there is no need to replace this key in the multi-signature wallet.
PIN code exposed
If your PIN is exposed, but no one has access to your signer, you don't need to assume the device is lost or stolen. (Translator's note: But you should update your PIN to prevent someone from getting access to the signer in the future and exposing your seed words.)
You can safely assume that neither the seed nor the signer are exposed, so there is no need to replace this key.
Update device
Another common scenario where you don't need to replace your keys is when switching to a new hardware signer. The BIP39 seed standard is supported on all reputable Bitcoin hardware signers, so you can import the seed for a given key into the new device. It's best to confirm that the key has been imported correctly by confirming your multisig wallet address and performing a small spend on the new device.
As long as your seed word backup is kept intact and not exposed, you do not need to replace this key in the multi-signature wallet.
How do I replace the key?
If you need to replace a key on your self-custody multi-signature device for the reasons explained above, there is a standard process to follow, regardless of the Bitcoin wallet software you use. Using a 2-of-3 multi-signature wallet as an example, you will need to follow these general steps:
- Generate a new replacement key on a new hardware signer
- Make a safe copy of the new seed word (on paper or metal)
- Create a new multi-signature wallet (in your wallet software) using this new key and the two original, unexposed keys
- Perform a test: deposit a small amount of funds into the multi-signature wallet and spend these funds to confirm that the multi-signature wallet has been built
- Using the original two unexposed keys, transfer the funds from the old wallet to the new multi-signature wallet address.
- Make sure to download the wallet configuration information of this new multi-signature wallet from your wallet software and back it up; finally, update the whitelist of the old wallet address you use on the exchange or other service providers
After completing the above steps, the two unexposed keys and the exposed key only control the old wallet that no longer has funds; while the two unexposed keys and the newly generated key control the new wallet.
How can I avoid the need to rekey in the future?
The best case scenario, of course, is to always ensure that key replacement methods are never needed. The specifics of your security model depend on many variables and trade-offs, but in general, you should ensure that your seed word backups are securely stored in decentralized locations, and that only people you know and trust have access to your signer device.
To learn how to store your seed word backups and hardware signers, see our Ultimate Guide to Storing Seed Words and our Guide to Paper, Metal Plates, and Other Seed Word Storage Methods . If you are an Unchained customer, please see our Operational Security Guide for seed word and signer storage recommendations .
(over)








