Author: Aki Wu Blockchain about blockchain
On October 14, 2025, an indictment unsealed in federal court in Brooklyn, New York, revealed that the US Department of Justice recently conducted one of the largest cryptocurrency seizures in history, confiscating approximately 127,000 Bitcoins, valued at over $15 billion. The confiscated Bitcoin assets originated from a scam involving Cambodia's "Prince Group," whose mastermind was none other than Chen Zhi, known as the "pig-killing scam kingpin." The founder of Cambodia's Prince Group was accused of using forced labor to perpetrate a cryptocurrency investment fraud, commonly known as a "pig-killing scam," generating tens of millions of dollars in daily illicit profits. The massive Bitcoin funds are currently in the custody of the US government. This article will examine the details behind this transnational cryptocurrency law enforcement saga, focusing on the prosecution background, asset sources, and enforcement efforts.
The fraud empire under the gilded coat
Chen Zhi is the founder and chairman of Cambodia's Prince Holding Group , a group that claims to operate real estate, finance, and other businesses in over 30 countries. In reality, it's accused of secretly developing into one of Southeast Asia's largest transnational criminal organizations. According to information released by the US Departments of Justice and Treasury, Chen Zhi and others have operated at least 10 fraudulent industrial parks across Cambodia since 2015, luring victims worldwide into fraudulent cryptocurrency investments using the infamous "pig-killing" schemes. US prosecutors allege that Chen Zhi was the mastermind behind this "online fraud empire," condoning employee violence, bribery of foreign officials, and allowing the group to squander the proceeds of the fraud on lavish spending, including yachts, private jets, and even a Picasso painting sold at a New York auction house.
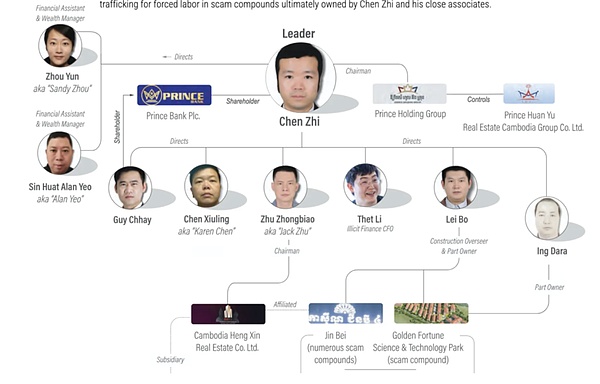
Chen Zhi himself remains at large, and the US has issued a wanted and sanctions notice for him. His dual British and Cambodian citizenship and deep political and business connections complicate his extradition. Such a vast fraud empire naturally involves a systematic money laundering system.
To combat the entire profit chain, OFAC has imposed comprehensive sanctions on 146 targets, including the Prince Group transnational criminal organization. Among them, the Huione Group, controlled by Chen Zhi and other criminal gangs , is a Cambodian financial and e-commerce ecosystem encompassing HuionePay and the Telegram intermediary marketplace. It has been directly identified by the U.S. Financial Crimes Enforcement Network (FinCEN) as a core link in the Prince Group's money laundering activities.
According to the U.S. Treasury Department, at least $4 billion in illicit funds were laundered between August 2021 and January 2025 through the Huiwang network alone. This included virtual assets from North Korean cyber theft, crypto investment scams, and other cybercrimes. In its simultaneous sanctions announcement against the Prince Group transnational criminal organization, the Treasury Department emphasized the complete severance of Huiwang Group's connection to the U.S. financial system. Regulated financial institutions are now prohibited from opening or maintaining correspondent accounts directly or on behalf of Huiwang Group and must take reasonable measures to refrain from processing correspondent account transactions of U.S. foreign banking institutions in transactions involving Huiwang Group, thereby preventing Huiwang Group from indirectly accessing the U.S. financial system.

OKX CEO Star stated in a statement that the Huione Group has had a significant negative impact on the cryptoasset sector. In light of the potential risks , OKX has implemented strict AML controls for transactions involving the group. All deposits and withdrawals of crypto assets related to Huione will be subject to compliance investigations. Based on the results of the investigation, OKX may take measures such as freezing funds or terminating account services.
Source of Assets: Scam Proceeds and Bitcoin Mining
Where did this staggering figure of 127,000 bitcoins (equivalent to approximately $15 billion) come from? According to the U.S. Department of Justice, these funds were the proceeds and tools used by Chen Zhi to conduct a fraud and money laundering scheme. They were previously stored in non-custodial cryptocurrency wallets, for which he personally held the private keys. These massive sums, siphoned from victims, required meticulous laundering to avoid regulatory scrutiny.
The indictment reveals that Chen Zhi and his accomplices invested the proceeds of the fraud in a cryptocurrency mining operation they controlled, thereby "laundering" new Bitcoins free of criminal taint . During the ostensibly legal mining process, the illicit funds were converted into newly mined "clean" Bitcoin assets, thereby attempting to sever the connection between the funds and the crime. This money laundering strategy ensured a steady flow of Bitcoin from the Prince Group's mining operations, becoming a key channel for concealing illicit funds.


The indictment specifically names the Lubian Mining Pool, a mining company linked to Chen Zhi's money laundering scheme. Lubian was once a world-renowned Bitcoin mining pool, headquartered in China and with operations extending to Iran. At its peak, it controlled approximately 6% of the global Bitcoin computing power. As part of Chen Zhi's money laundering network, the Lubian Mining Pool helped convert fraudulent funds into massive amounts of Bitcoin. However, a bizarre "theft" in late 2020 embroiled Lubian in a mystery. In late December 2020, Lubian reported a hacker attack and the theft of a large number of Bitcoins. On-chain data indicates that 127,426 Bitcoins, valued at approximately $3.5 billion at the time, were stolen from Lubian in December 2020. The sheer volume of BTC stolen by the hackers made the incident one of the "largest Bitcoin thefts in history."
Lubian disappeared shortly after the attack, abruptly shutting down its mining pool operations in February 2021. The stolen 120,000 BTC remained unaccounted for for a long time. On-chain analysis indicates that the 127,426 stolen Bitcoins were transferred to a cluster of major wallets. Whether an external hacker stole Chen Zhi's funds or Chen Zhi orchestrated the transfer remains unknown. However, these priceless Bitcoins subsequently disappeared from the blockchain, seemingly vanishing from the face of the earth. Their whereabouts were only revealed years later.
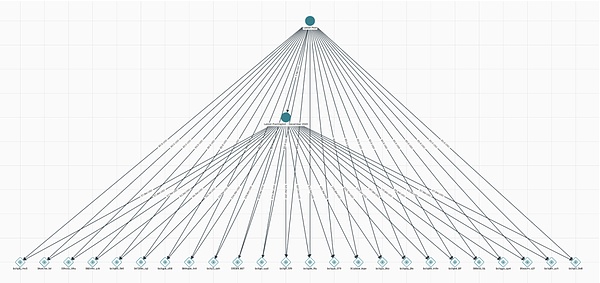
Over 120,000 stolen Bitcoins remained dormant for over three years, with no apparent on-chain movement. On-chain analysis shows that from the time of the theft in late 2020 until mid-2024, these BTC remained in dozens of hacker-controlled wallets. In July 2024, approximately 127,000 BTC underwent a massive centralized transfer. Because these addresses had long been registered within the cryptocurrency community, on-chain intelligence platforms like Arkham quickly identified these massive Bitcoin collections as belonging to the 2020 Lubian mining pool theft. The timing of these BTC's transition from dormancy to movement is intriguing, occurring just as international law enforcement agencies were closing in on the operation.
When the US Department of Justice filed a civil forfeiture lawsuit in October 2025, the document listed 25 Bitcoin addresses indicating that these were the locations of the previously held BTC. These addresses exactly matched the hacker addresses involved in the Lubian mining pool theft. This means that US officials determined that the 127,000 BTC were laundered through Lubian by Chen Zhi and his accomplices, the same funds that were laundered in the fake "theft" in 2020. The lawsuit further stated that the private keys to these BTC were originally held by Chen Zhi himself but are now under US government supervision. This means that the previous Bitcoin collection in July was likely carried out by the US government.
Could America’s core technology be a simple brute force attack?
Due to the publicity surrounding anonymous transactions in early Bitcoin cases, the public has gradually come to interpret Bitcoin's pseudonymity as a strong form of anonymity, fostering the misconception that Bitcoin facilitates money laundering. In reality, the transparency of the blockchain ledger provides law enforcement with an unprecedented view of the flow of funds. Investigators can leverage specialized on-chain analysis tools to connect dispersed transaction addresses into a network, identifying wallets belonging to the same entity and unusual patterns in fund flows. For example, in this case, Arkham had long labeled the wallet addresses of the Lubian mining pool. When a large amount of BTC was stolen and relocated, the analysis system immediately associated the new address with the Lubian tag, effectively pinpointing the whereabouts of the stolen Bitcoin. The blockchain's immutable record also ensures that fraudsters remain undetected even after years of attempting to transfer assets.
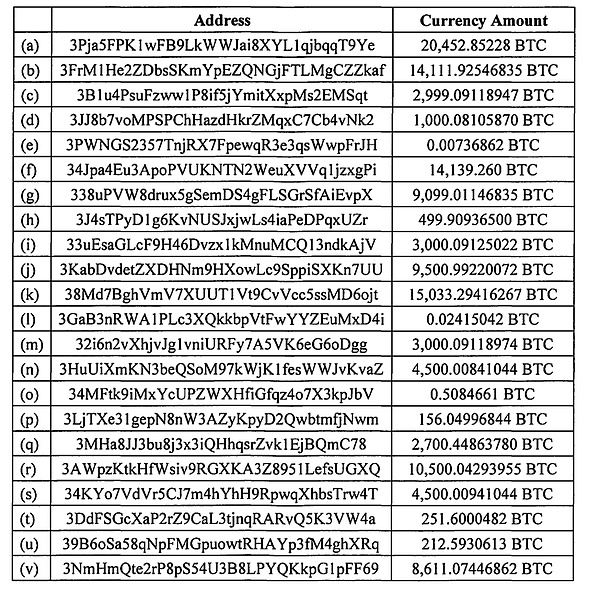
However, obtaining an on-chain address does not guarantee control of the assets; control of the private keys is even more crucial. There's currently no accurate information on how the US government obtained these private keys. According to an Arkham investigation, the Lubian mining pool failed to use a sufficiently secure randomization algorithm for wallet private key generation, resulting in a vulnerability that could be cracked using brute force. However, Cobo co-founder Shenyu stated that law enforcement agencies did not obtain the private keys through brute force or intrusion, but rather discovered a randomness flaw in the keys' generation. According to incomplete statistics, over 220,000 addresses were affected by the vulnerability, and the full list has been made public.
The private keys for these wallets are generated by a flawed pseudo-random number generator (PRNG). Because the PRNG uses a fixed offset and pattern, the private keys are more predictable. Users are still transferring funds to the relevant addresses, indicating that the vulnerability risk has not been completely eliminated. It is speculated that US law enforcement and cyber experts may have similar techniques or clues. However, it is also possible that the US government, through social engineering and forensic investigations, obtained mnemonics or signing rights offline, and gradually gained control of the private keys by infiltrating the fraud ring. In any case, even if Chen Zhi himself has not yet been apprehended, the "digital gold" that the fraud ring boasted has been completely apprehended.

Implications for us and regulators
A fraudster who once eluded justice has now lost his hoard of digital gold. Cryptocurrencies, once considered a valuable tool for money laundering, are now becoming a valuable tool for recovering illicit funds. The incident involving the confiscation of Bitcoin from a Cambodian scam lord offers profound lessons for both the industry and regulators. The inherent security of crypto assets relies on the strength of their cryptography; any technical flaws could be exploited by hackers or law enforcement to determine the ultimate ownership of assets. If you use automated private key wallets like imtoken and Trust Wallet, you're likely at risk of having your wallet hacked. Consequently, more traditional legal authorities are introducing on-chain tracing and encryption cracking technologies, increasingly shattering the illusions of criminals using encryption to evade justice.