This article is based on CertiK's list of the top ten Web3 security incidents of 2025. The total losses from the top ten incidents alone have exceeded $2.5 billion, with the Bybit incident alone accounting for half of them. The security incidents of this year are no longer dominated by logical vulnerabilities in smart contracts, but have evolved into more complex supply chain attacks, social engineering, insider threats, and geopolitical cyber warfare.
Article author: 0x9999in1
Article source: ME
ME Group, in partnership with CoinFoundry, presents its highly anticipated annual column, "Crypto Chronicle 2025: The Era of Convergence | Web3 Annual Rankings and Year-End Review." Five main industry rankings will be launched based on the Chinese-speaking community's interest, highlighting the most influential figures, events, and innovations in the industry.
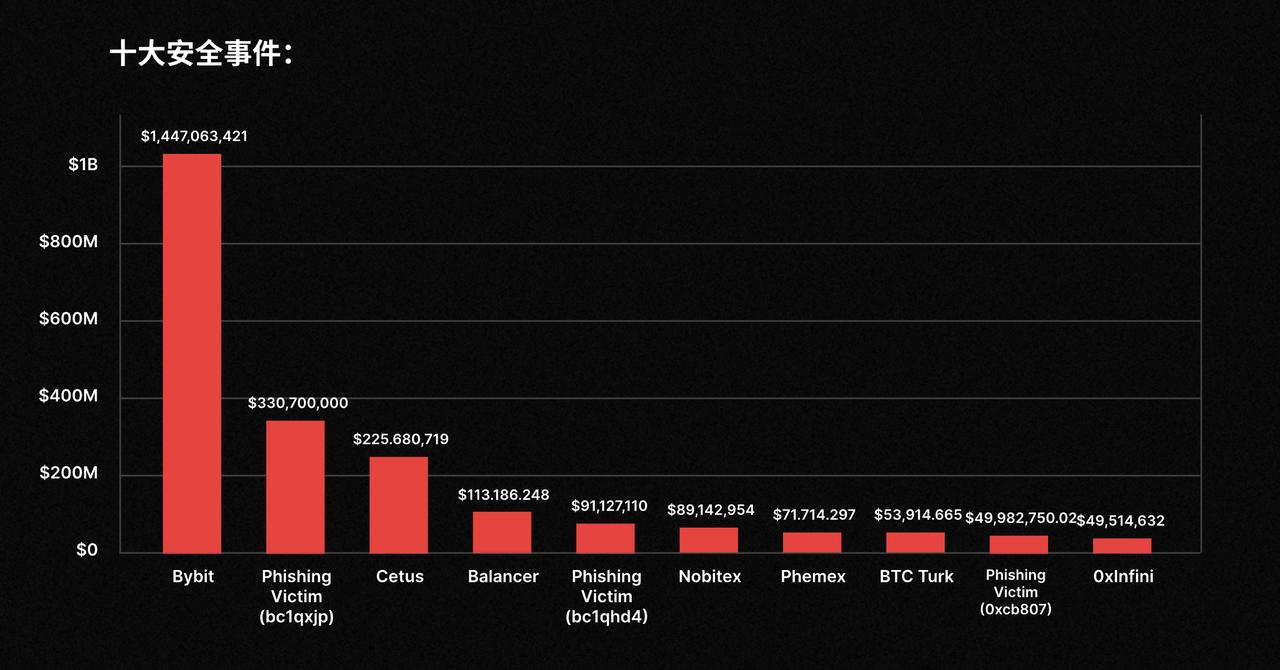
This article is based on CertiK's list of the top ten Web3 security incidents of 2025. The total losses from the top ten incidents alone have exceeded $2.5 billion, with the Bybit incident alone accounting for half of them. The security incidents of this year are no longer dominated by logical vulnerabilities in smart contracts, but have evolved into more complex supply chain attacks, social engineering, insider threats, and geopolitical cyber warfare.
Bybit's massive asset theft incident
Loss amount: $1,447,063,421
The biggest security disaster of 2025 occurred at the top centralized exchange Bybit, resulting in a staggering loss of $1.447 billion. This incident is considered one of the largest single hacks in cryptocurrency history, with the stolen funds primarily concentrated on Ethereum (ETH) and other mainstream assets. The attackers bypassed the exchange's multi-signature security mechanisms using extremely sophisticated methods, directly draining hot wallets and potentially even gaining access to some cold wallets.
The core reason for this attack is most likely a deep penetration of the internal system or a supply chain attack. Hackers (suspected to be nation-state hacking groups such as the Lazarus Group) may have lurked in Bybit's internal network for months, gaining critical private key signing privileges or tampering with the withdrawal interface code. Following the incident, a huge amount of funds was rapidly dispersed to thousands of newly generated wallet addresses and cleaned using mixers, greatly complicating the recovery efforts and serving as a stark warning about asset custody security for the entire centralized exchange (CEX) industry.
Bitcoin whale phishing incident (bc1qxjp)
Amount of damage: $330,700,000
Second on the list is an epic phishing scam targeting a large individual whale, resulting in losses of $330 million. The victim's Bitcoin address was completely emptied in a single transaction, with all funds flowing to a hacker address starting with "bc1qxjp". This case demonstrates that hackers have shifted their focus from breaching exchange defenses to specifically targeting large individuals holding substantial assets, exploiting human weaknesses.
The incident likely involved sophisticated social engineering. Attackers may have posed as trusted wallet software updates, OTC trading counterparties, or legal advisors, tricking victims into downloading backdoored software or tampering with clipboard content when victims copied and pasted addresses. For individuals holding hundreds of millions of dollars, any negligence in their off-chain environment (such as computer malware or private key access to the internet) could lead to irreparable losses, and the irreversible nature of Bitcoin transactions caused this enormous sum to vanish instantly.
Cetus Protocol overflow vulnerability incident
Loss amount: $225,680,719
Cetus, a leading decentralized exchange within the Sui ecosystem, suffered a severe smart contract vulnerability attack, resulting in a loss of approximately $225 million for the protocol. As a star project built on the Move programming language, this theft shattered the common perception that Move is inherently secure. The attackers exploited a logical flaw in the contract's liquidity calculations, manipulating a specific price range (Tick) to extract the vast majority of liquidity from the pool at extremely low cost.
Technical analysis indicates the vulnerability likely stems from integer overflow or missing boundary checks in mathematical operations. In decentralized finance (DeFi) protocols, complex algorithmic logic often presents blind spots for security audits. Attackers precisely crafted anomalous trading parameters, bypassing system risk controls and essentially "printing money out of thin air" to steal users' staked assets. This incident not only severely damaged the Cetus protocol itself but also caused significant short-term fluctuations in the TVL (Total Value Locked) of the entire Sui ecosystem.
Balancer access control failure event
Amount of damages: $113,186,248
In 2025, the established DeFi protocol Balancer suffered a major security setback, losing over $113 million. As one of the infrastructure components of liquidity pools on Ethereum, Balancer's theft affected multiple downstream projects. The attack primarily targeted its V2 or some enhanced liquidity pool smart contracts, with hackers exploiting access control vulnerabilities or reentrancy vectors in the code to forcibly transfer assets from the pools.
The incident stemmed from negligence in contract access control, which allowed unauthorized external callers to execute "flash loan" or "asset rebalancing" operations that should have been restricted. Attackers manipulated the contract by constructing malicious transactions to believe they had legitimate withdrawal rights, or exploited price discrepancies during price oracle updates. Although the Balancer team immediately suspended the protocol after discovering the anomaly, due to the instant settlement nature of blockchain, hundreds of millions of dollars were transferred within minutes.
Bitcoin whale phishing incident (bc1qhd4)
Amount of damages: $91,127,110
This is the second targeted phishing attack on major Bitcoin holders on the list, resulting in losses of $91.12 million. The stolen funds flowed into a hacker address ending in bc1qhd4. Similar to the aforementioned phishing cases, this incident once again exposes the rampant nature of "address poisoning" attacks. Hackers generate highly similar "fake addresses" to the beginning and end of victims' frequently used addresses and send small transfers to them, thereby polluting the victims' transaction history.
When making large transfers, the victim neglected to verify the complete address and habitually copied a forged address from the transaction history, resulting in a huge sum of money being directly transferred to the hacker's account. This attack method exploits blind spots in user vision and operational inertia; it is extremely low-cost but highly destructive. For an account with nearly $100 million in assets, the lack of a strict whitelist mechanism and multi-factor authentication via hardware wallets was the root cause of this tragedy.
Nobitex political hacking incident
Loss amount: $89,142,954
Nobitex, Iran's largest cryptocurrency exchange, was hacked, resulting in a loss of approximately $89.14 million. This incident has strong geopolitical implications; the attackers were not only motivated by economic gain but also aimed to disrupt the region's critical financial infrastructure. The hackers infiltrated the exchange's backend servers, gained control of hot wallets, and illegally transferred large amounts of Bitcoin and stablecoin assets.
This attack exposed the unique risks faced by crypto entities amid geopolitical conflicts. Due to international sanctions, exchanges in the region often lack access to top-tier security services, resulting in relatively weak system defenses. Hackers exploited this weakness, breaching the exchange's internal network through phishing attacks and zero-day exploits, demonstrating that centralized servers remain one of the most vulnerable links in the Web3 world.
Phemex hot wallet private key leak incident
Amount of damages: $71,714,297
The well-known derivatives exchange Phemex suffered a hot wallet private key breach, resulting in the theft of $71.71 million in assets. At the time of the incident, its hot wallets across multiple blockchains, including Ethereum, Bitcoin, and Solana, were emptied almost simultaneously, indicating a single point of failure in the exchange's private key management system (KMS), with core signing permissions completely gained by hackers.
Typically, exchanges store most of their assets in cold wallets, keeping only a small amount in hot wallets for daily withdrawals. However, the loss of over $70 million suggests that the hot wallet's risk control limits may have failed, or that hackers rapidly increased withdrawal limits after breaching the system. This incident not only caused huge financial losses but also severely damaged user trust in the platform, forcing it to suspend deposit and withdrawal services for a comprehensive security architecture overhaul.
BTC Turk Exchange Attack
Loss amount: $53,914,665
Turkish cryptocurrency exchange BTC Turk suffered a cyberattack, resulting in losses of approximately $53.91 million. Attackers targeted several of the exchange's most liquid hot wallets, transferring funds intended for user withdrawals to attacker-controlled accounts in bulk by altering transaction data streams or exploiting API vulnerabilities.
The BTC Turk hack, a leading regional exchange, reflects the mismatch between security investment and asset size among mid-sized exchanges. Hackers used automated scripts to launch a high-frequency withdrawal request overwhelmed the exchange's risk control system. Subsequent analysis revealed that the exchange lacked a real-time on-chain anomaly monitoring mechanism, failing to trigger a circuit breaker in the initial crucial period of the attack, allowing funds to flow out unchecked.
Personal whale fishing incident (0xcb807)
Loss amount: $49,982,750.02
This is a typical signature phishing attack targeting Ethereum (EVM) whale, resulting in losses approaching $50 million. Unlike Bitcoin phishing, victims in the Ethereum ecosystem are often victims of signing malicious Approve or Permit signatures. Hackers lure victims to fake DeFi websites or airdrop claiming pages, tricking them into authorizing unlimited amounts of USDT or ETH.
Once the victim clicked "confirm" in their wallet, the hacker gained access to transfer their assets without requiring further consent. The owner of the victim address 0xcb807... may not have realized the true meaning of that obscure signature data before surrendering control of their assets. This highlights the significant "what you see is not what you get" risk inherent in Web3 interfaces; even experienced crypto users struggle to fully decipher elaborately crafted malicious signatures.
0xInfini Protocol Vulnerability Incident
Loss amount: $49,514,632
The 0xInfini project suffered a smart contract vulnerability, resulting in losses of approximately $49.51 million. As a DeFi protocol involving cross-chain or complex financial logic, 0xInfini's core contract code contained unaudited logical flaws. Attackers may have exploited oracle price manipulation or flash loan attacks to instantly deplete the protocol's liquidity pool.
The attack was extremely swift, with the hacker completing the entire process of lending, attacking, repaying, and withdrawing funds within a single block. The root cause lies in the protocol's design failing to adequately account for boundary conditions under extreme market circumstances, leading to a breakdown in risk control logic. For users, this incident once again demonstrates the inherent high risk of losing all principal when depositing funds into emerging protocols that have not undergone extensive real-world testing.
summary
This $2.5 billion tuition fee in 2025 is costly, yet incredibly valuable. It serves as a reminder to every participant—whether you are a developer, exchange operator, institutional investor, or ordinary holder—that in the world of Web3, security is never the end, but a never-ending arms race. Only by balancing technological rigor with human vigilance, and individual responsibility with industry collaboration, can we navigate this digital realm, brimming with both opportunities and pitfalls, more steadily and further.
May 2026 be a year in which we no longer learn about security at the cost of huge losses, but instead embrace a truly large-scale adoption era with a more mature defense system.
Reference: CertiK's "2025 Skynet Hack3D Web3 Security Report"
Click to enter: Special report on "Crypto Chronicle 2025: The Era of Convergence | Web3 Annual Rankings and Year-End Review"
Click to enter: "Crypto Chronicle 2025: The Era of Convergence | Web3 Annual Rankings and Year-End Review" dedicated webpage








