*This article has been automatically translated. Please refer to the original article for accurate content.
summary
- Cryptocurrency fraud and scams will cost an estimated $17 billion in losses in 2025. Identity theft fraud will surge 1,400% year-over-year, and AI-powered scams will be approximately 4.5 times more profitable than traditional scams.
- Large-scale fraud organizations have become more industrialized, building sophisticated infrastructures including phishing-as-a-service, AI-generated deepfakes, and professional money laundering networks.
- Strong ties to Southeast Asian criminal networks have been identified, particularly in forced labor camps in countries such as Cambodia and Myanmar, and there have been numerous cases where victims have been coerced into committing fraud.
- The largest law enforcement seizures to date, including the recovery of 61,000 bitcoins in the UK and the seizure of $15 billion in assets linked to the Prince Group criminal organisation , demonstrate growing capabilities in combating cryptocurrency fraud.
In 2025, cryptocurrency fraud will receive at least $14 billion on-chain, a significant increase from the $9.9 billion we first reported in 2024 (recalculated to $1.2 billion at the time of writing). This is roughly in line with our original 2024 forecast ($12.4 billion). Based on historical trends, annual estimates have increased by an average of 24% between reports, so losses are expected to reach over $17 billion in 2025 as more fraudulent wallet addresses are identified.
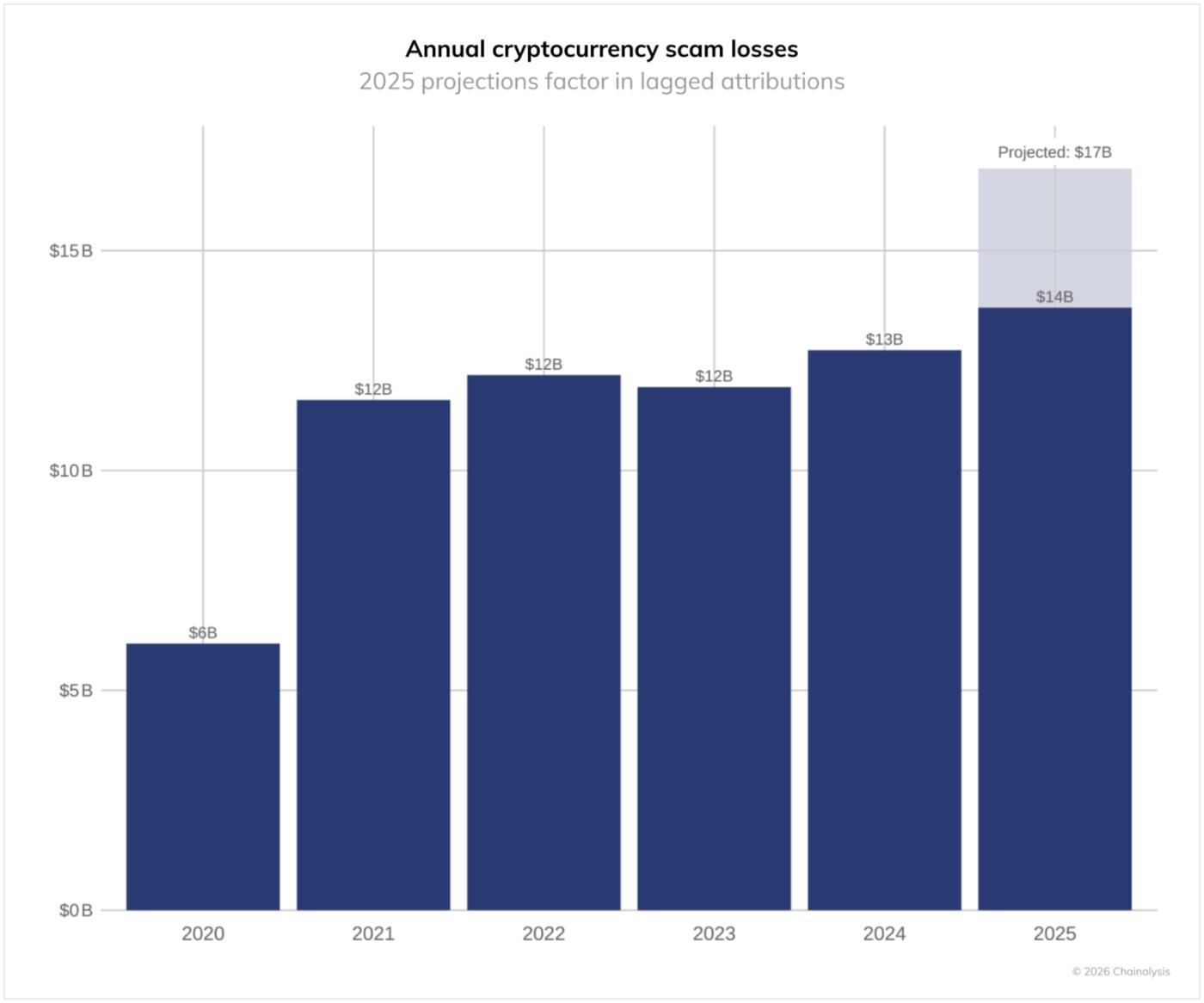
This year's data shows that scammers continue to evolve their methods, with the average fraudulent transfer amount increasing 253%, from $782 in 2024 to $2,764 in 2025. Overall fraud traffic also increased significantly, with impersonation schemes growing by a staggering 1,400% year-on-year. While high-yield investment programs (HYIPs) and romance scams (Pig Butchering) remain the leading categories, we are seeing a fusion of tactics that combine the use of AI , advanced SMS phishing services, and complex money laundering networks to target victims more effectively than ever before.
Traditional classifications of fraud are becoming blurred, with an increasing number of techniques being combined (impersonation, social engineering, technical and wallet fraud).
Identity theft fraud is on the rise
Impersonation fraud is a particularly worrying trend, increasing by over 1,400% since 2024, with the average amount sent to these clusters also increasing by over 600%. In this technique, fraudsters impersonate legitimate organizations or authority figures to trick victims into sending them money.
Government Impersonation: E-ZPass Fraud Network
Government impersonation has become a highly effective tactic, taking advantage of trust in official communications. In 2025, a widespread "E-ZPass" phishing campaign targeted millions of E-ZPass (automated toll collection) users in the United States.
The scheme has been attributed to a Chinese-speaking cybercrime group known as "Darcula" (also known as " Smishing Triad "). This China-based criminal network used phishing-as-a-service tools to send mass SMS messages to primarily target E-ZPass users in at least eight states, posing as a collection agency. This group has also previously spoofed the United States Postal Service .
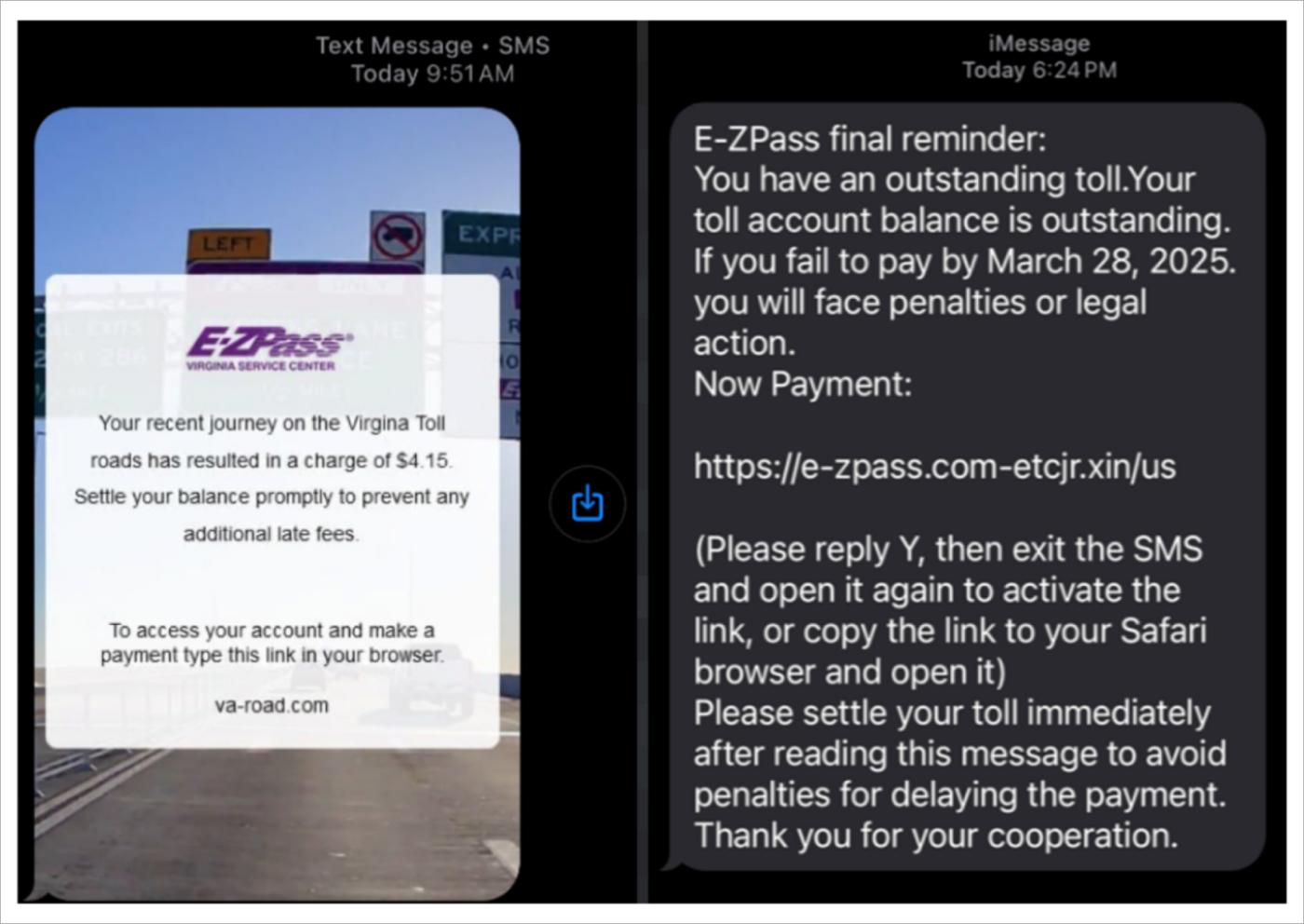
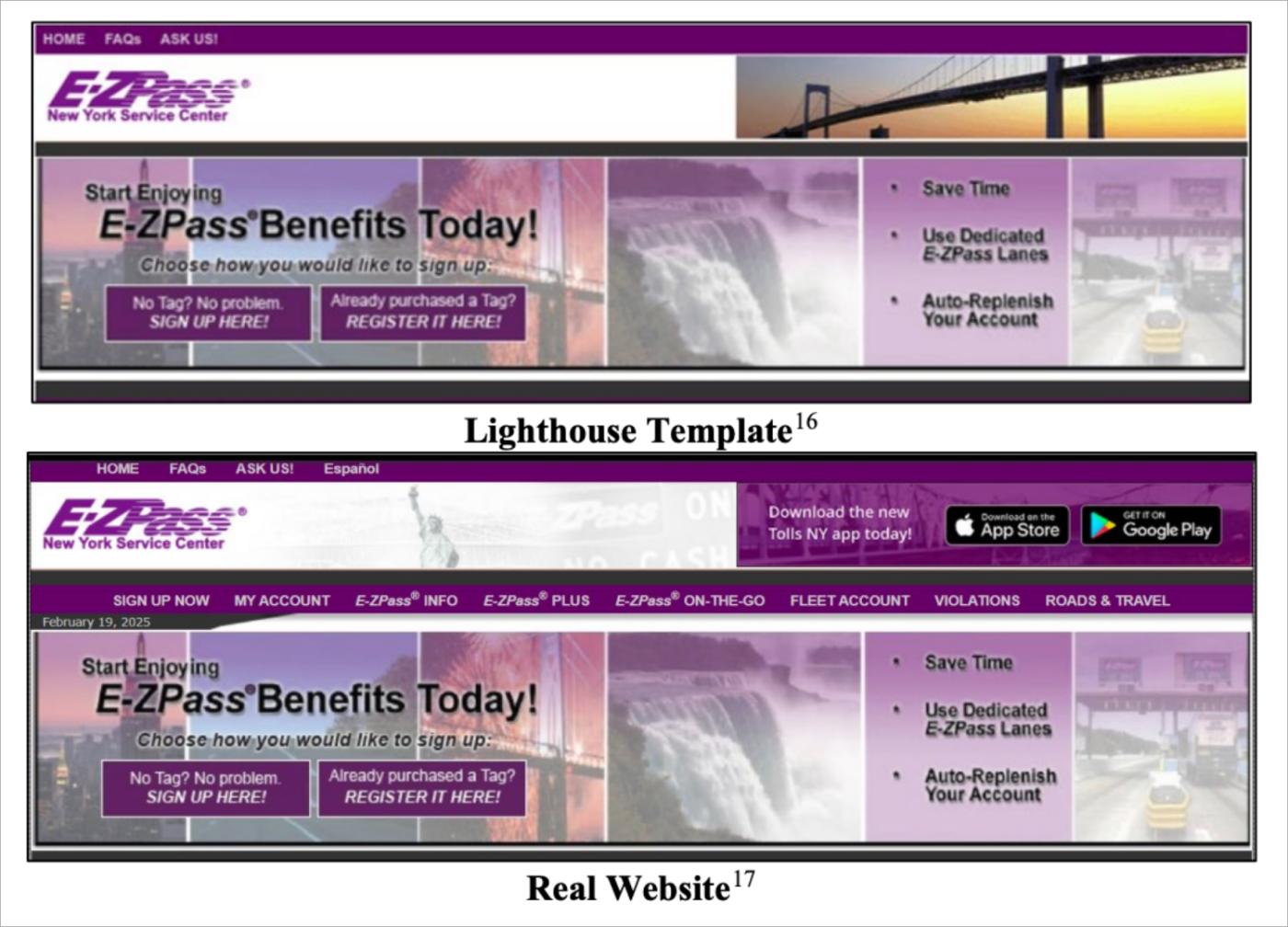
According to a lawsuit filed by Google in November 2025, Smishing Triad used software from a Chinese vendor called "Lighthouse" to provide criminals with a "beginner's phishing kit" that included hundreds of fake site templates, domain configuration tools, and detection evasion features.
The group created fraudulent websites that imitated government websites such as the official New York City website (nyc.gov) and New York E-ZPass (e-zpassny.com), disguising them so well that they were indistinguishable from the legitimate sites.
In addition to illustrating the modus operandi of cybercriminals using cryptocurrency to purchase infrastructure and carry out their crimes, this case also highlights the on-chain traces they leave behind that present real opportunities for countermeasures. As shown in the graph below, multiple Chinese underground criminal organizations, including the Taihe Gong fraud group, purchased the Lighthouse phishing kit and received funds from multiple Chinese-language money laundering networks (CMLNs) and fraud shops. Taihe Gong is comprised of Chinese-speaking operators suspected of engaging in fraudulent cybercrime activities, including the sale of phishing kits, and its operational structure suggests an established supply chain distributing malicious tools to facilitate online fraud, credential theft, and other illicit activities.
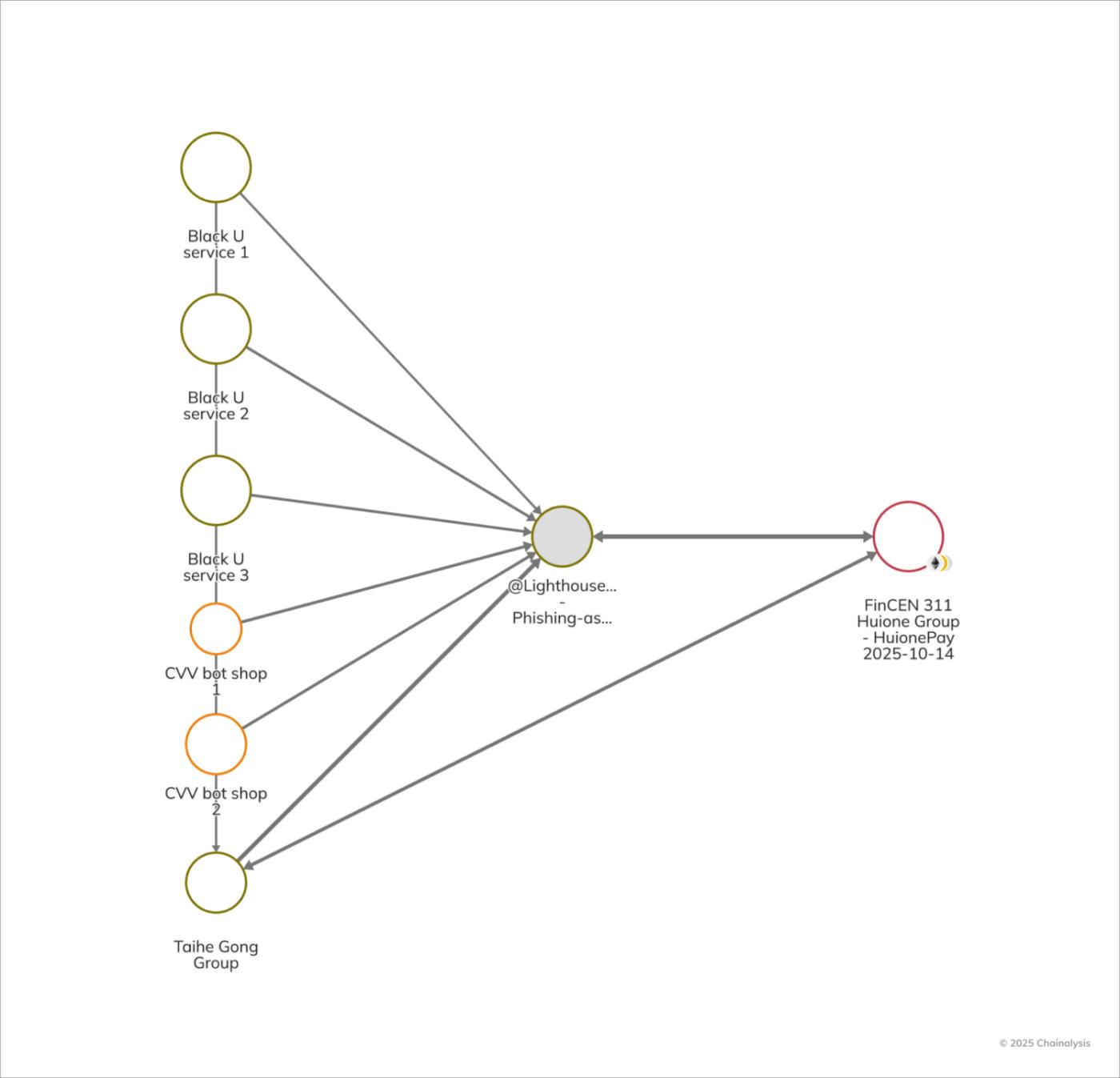
The E-ZPass case illustrates how low-cost fraud infrastructure can be. Some phishing kits appear to have been purchased for less than $500. However, even inexpensive scams can be devastating when deployed at scale. The E-ZPass scheme, part of another toll fraud campaign, sent 330,000 texts per day, raised $1 billion over three years, and affected over one million victims in over 121 countries, according to a Google lawsuit. According to Cisco Talos , the phishing kits ranged in price based on functionality, from $50 in cryptocurrency for "full-featured development" to $30 for "proxy development," and $20 for version updates and support. Lighthouse received over 7,000 deposits over three years, raising over $1.5 million in cryptocurrency.
Unfortunately, Lighthouse is not the only vendor. Gary Warner, Director of Intelligence and Analysis at DarkTower, is tracking eight major Chinese-language "Crime-as-a-Service" groups on Telegram, each with multiple vendors offering iMessage and RCS phishing services. According to Warner, the goal of these phishing campaigns is to acquire credit cards into mobile wallets and then use "remote tap-to-pay" services around the world to purchase and resell luxury goods and electronics, thereby deploying them in a network of "shoppers" who can launder money through trade. From designing, hosting, and distributing phishing campaigns to shopping, receiving cash, and purchasing goods, these Chinese criminal groups have it all on Telegram, with some groups boasting over 300,000 members. All sales and advertising are settled in stablecoins. Warner also points out that much of the money laundering overseas is also aimed at converting goods and cash into stablecoins to facilitate overseas remittances.
Private Sector Impersonation: Coinbase Impersonation Campaign
In December 2025, the Brooklyn District Attorney's Office indicted 23-year-old Brooklyn resident Ronald Spektor as the mastermind behind a sophisticated cryptocurrency fraud that resulted in losses of approximately $16 million. Spektor and his accomplices impersonated Coinbase customer service representatives and used bribed user information to incite fears of "unauthorized account access" and convince victims to transfer their cryptocurrency to "secure" wallets controlled by the fraudsters. Furthermore, a former Coinbase customer service representative recently arrested in India was allegedly accused of receiving $250,000 in bribes as part of the same fraud, highlighting that even with robust technical security measures, human trust remains one of the most vulnerable vulnerabilities to exploit. This insider exploit exposed the data of approximately 70,000 customers and enabled credible impersonation attacks.
This scam exploits the trust placed in cryptocurrency exchange users by convincing them that the scammers are representing "legitimate customer service," demonstrating how impersonation scams are evolving to exploit users' concerns about the security of their accounts. This case illustrates how exchange impersonation techniques are becoming increasingly sophisticated, causing significant harm to victims who thought they were protecting their digital assets. Brooklyn District Attorney Gonzalez stated, "Our department remains committed to cracking down on all cases of cryptocurrency fraud. This is a serious problem that is exploding across the United States. We will utilize the latest technology to investigate criminals, freeze assets where possible, and provide support to victims."
Tracing identity fraud funds reveals evolution of DeFi money laundering methods
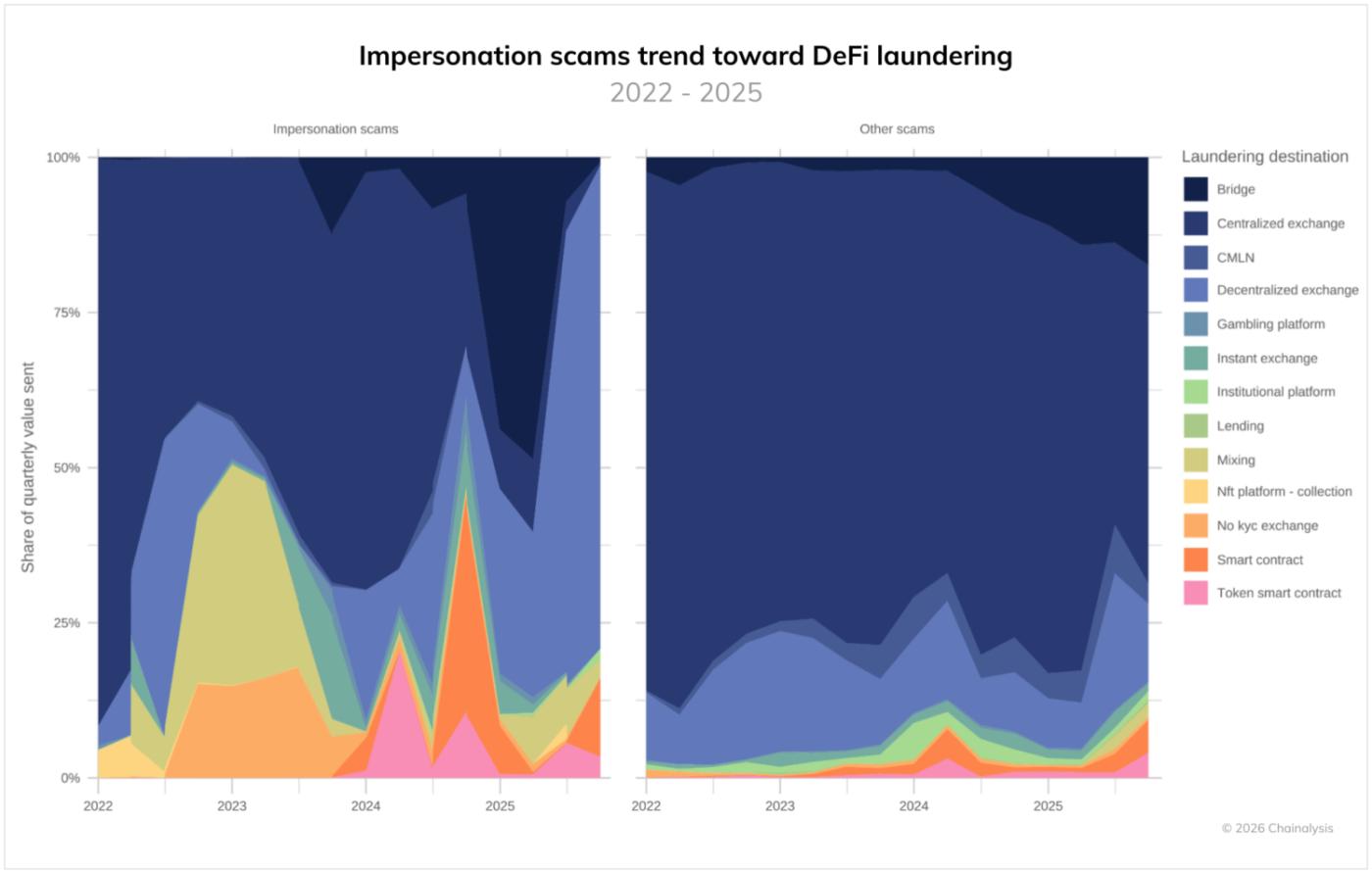
Impersonation fraud has its own unique laundering patterns, heavily dependent on the decentralized finance (DeFi) ecosystem. This contrasts with other frauds, which still primarily rely on centralized exchanges for laundering funds (a trend we'll touch on later in the discussion of romance fraud). Interestingly, impersonation fraud has seen unique waves of multi-layered funds using DeFi. 2024 saw a surge in laundering via smart contracts and token smart contracts, followed by a plateau in 2025, alternating with new waves of bridges (first half of 2025) and DEXs (second half of 2025). These trends demonstrate that fraud techniques are constantly adapting, changing the primary laundering point and the services they use.
AI and advanced tools accelerate fraud sophistication
We are moving towards an era in which almost all fraud will incorporate some form of AI. While many fraudsters purchase AI tools using traditional payment methods, some acquire them on-chain, making their transactions visible. By analyzing the difference between fraud with visible on-chain connections and tools such as facial recognition substitution software, deep fake technology, and large-scale language models (LLMs) provided by Chinese AI vendors (many of which are Telegram-based), we can estimate the scale and efficiency of AI.
As shown in the figure below, 76% of AI-powered scams fall in the time-weighted high-value, high-frequency region. This means that the majority of scams with clear on-chain ties to Chinese AI vendors, such as Telegram, are characterized by (1) faster escalation (i.e., a higher rate of growth in incoming transactions) and (2) higher damage scale (higher daily USD transaction volume), which are significantly different from scams without clear on-chain links to AI vendors.
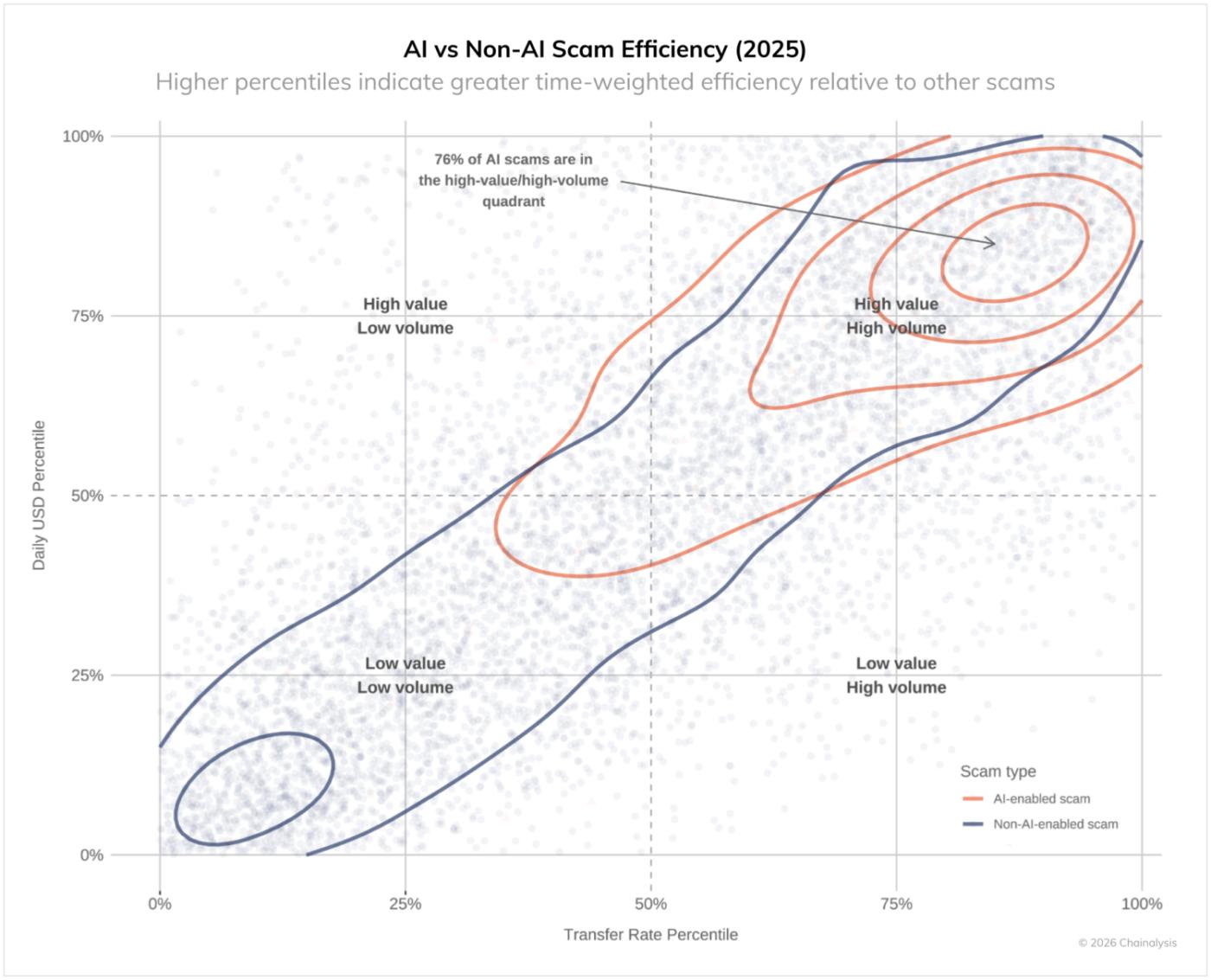
AI-based fraud: Losses increase 4.5 times
According to a July 2025 report by JP Morgan, fraudsters are increasingly using deepfake technology and AI-generated content to perform more sophisticated impersonations in romance and investment scams. Our analysis shows that frauds linked to on-chain AI vendors extract an average of $3.2 million per case, 4.5 times more than the average of $719,000 for unlinked frauds. These AI-related frauds are also significantly more efficient per hour.
- Median daily revenue: $4,838 ($518 for non-AI fraud)
- Average number of transactions per day: 35.1 (non-AI fraud was 3.89, 9x more trading activity)
These metrics indicate greater operational efficiency and the potential for reaching a wider range of victims. The increase in transaction volume indicates that AI is enabling fraudsters to reach and manage more victims simultaneously, which is consistent with our analysis of the industrialization of fraud. Meanwhile, the increase in fraud volume also suggests that AI is making scams more convincing.
"Cryptocurrency fraud is growing in scale and sophistication, with organized crime groups leveraging identity theft, online infrastructure and AI tools to target victims at scale and speed," said Will Lyne, head of the Metropolitan Police's Economic and Cybercrime Division. "At the same time, law enforcement's response capabilities are evolving dramatically. By leveraging specialized skills, international cooperation and financial and digital intelligence, we are better equipped to identify criminal networks, seize illicit assets and disrupt harmful activity."
The industrialization of fraud
The Lighthouse case represents another important trend in the professionalization and commercialization of the tools fraudsters use to carry out sophisticated, large-scale fraud. Lighthouse Enterprises operated a complex business model with multiple roles across the fraud and fraud supply chain.
- Development group: Providing phishing software and templates
- Data broker group: Providing lists of target victims
- Spammer group: Providing tools for sending large amounts of fraudulent SMS
- Theft Group: Specializing in the Monetization of Stolen Confidential Information
- Management Group: Online recruitment and cooperation forum management
This modular offering significantly lowers the barrier to entry for cryptocurrency fraud, allowing even less skilled criminals to carry out sophisticated phishing attacks. Many campaigns leverage social media, using automated messaging to target the platforms' vast user bases. In these cases, fraudsters purchase social media accounts in bulk and contact them via SMS or phishing kits.
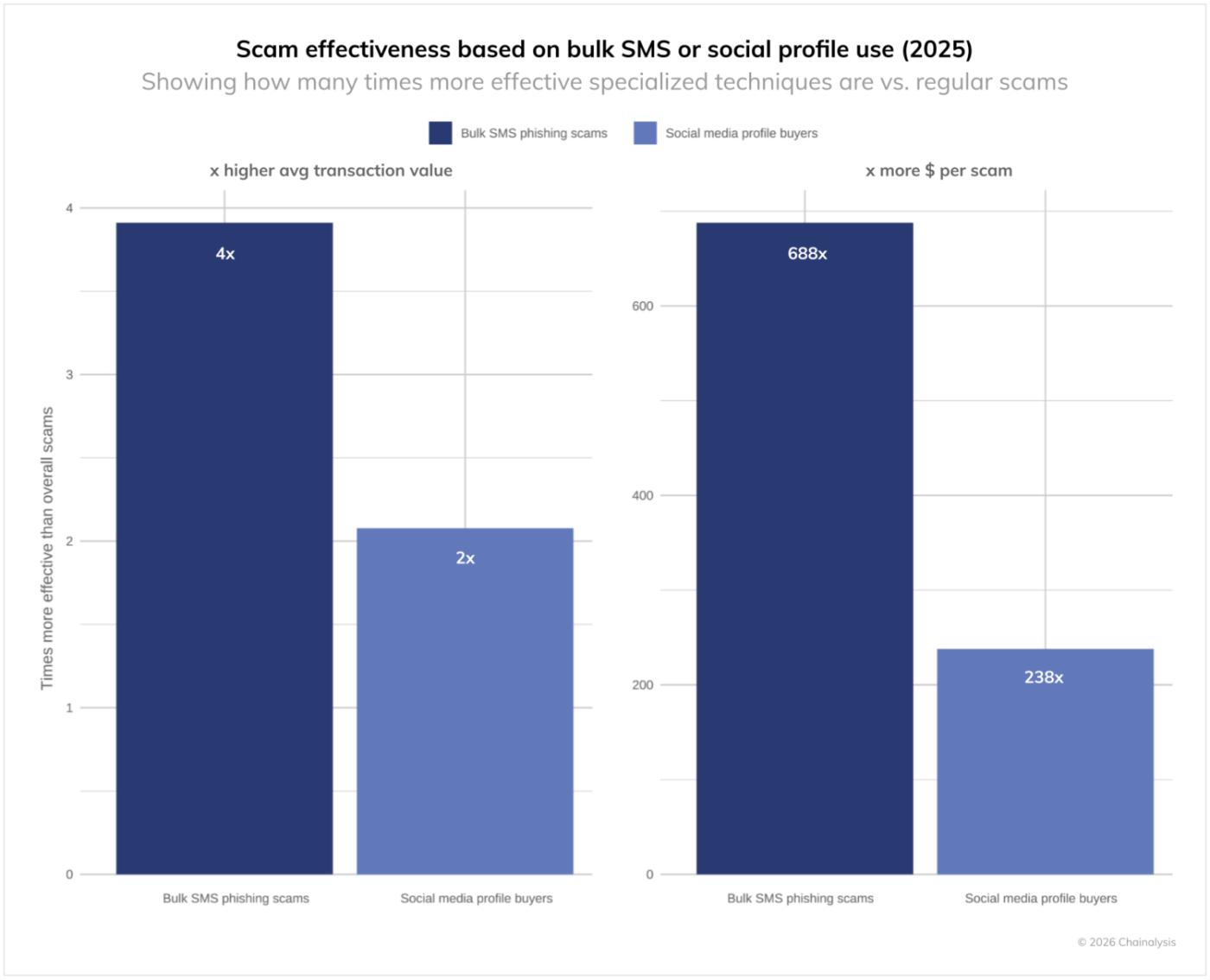
The damage caused by this large-scale industrialization is enormous: scams using these phishing kits are 688 times more effective than regular scams in terms of monetary value and four times more effective in terms of average transaction size, while scams using bulk purchases of social media accounts are 238 times more effective in terms of monetary value and twice as effective in terms of average transaction size.
The United Nations Office on Drugs and Crime (UNODC) has long warned about the use of malware in fraud campaigns, and this trend is becoming more prevalent on-chain. Chinese fraudsters, in particular, often incorporate stealer malware and remote access trojans (RATs) into their scams, allowing them to extract accounts without directly interacting with the victim. This significantly lowers the bar for fraudsters to succeed, as they only need a single click, rather than building a relationship with the victim.
Law enforcement offensive and largest ever seizure
The growing scale and sophistication of fraud led to unprecedented law enforcement activity in 2025, resulting in two of the largest fraud-related cryptocurrency seizures ever.
Jian Wen and Yadi Zhang
In November 2025, the UK Metropolitan Police secured a guilty verdict in an international cryptocurrency money laundering case, successfully seizing approximately 61,000 bitcoins (worth approximately £5 billion), the world's largest such case. Chinese national Zhimin Qian (also known as Yadi Zhang) was sentenced to 11 years and 8 months in prison for leading a multi-billion pound investment fraud that victimized more than 128,000 people in China between 2014 and 2017. His accomplice, Seng Hok Ling, was also sentenced to approximately five years for money laundering. This case demonstrates the scale and sophistication of cross-border cryptocurrency money laundering networks and the threat posed by criminals attempting to turn illicit cryptocurrencies into physical assets through complex international schemes.
"This was a lengthy, complex and unprecedented investigation. Significant effort was put into tracing the funds and understanding their attempts to convert them into assets in the UK. With the assistance of our UK and overseas contacts, and Chainalysis, we were able to trace the movement of crypto assets, locate related assets and ultimately recover over 61,000 bitcoin," said Detective Inspector Isabella Grotto.
Based on information from 2018, the investigation also revealed that Qian had fled to the UK under a false name and attempted to launder his funds through luxury real estate. The seizure and conviction demonstrate a significant improvement in our ability to track and disrupt global fraud and cryptocurrency money laundering, and the effectiveness of blockchain transparency.
The Prince Group
In a major blow to the global fraud ecosystem, the U.S. Department of Justice (DOJ) has indicted Chen Zhi, chairman of Prince Group, for overseeing a forced labor scam operation in Cambodia that operated a global cryptocurrency fraud operation in which trafficked people were forced to engage in romance and investment scams, and which used cryptocurrencies to launder funds globally.
Concurrent with these indictments, U.S. authorities also launched a comprehensive attack on the group's economic foundations, uncovering international money laundering networks and seizing and confiscating over $15 billion in fraudulent proceeds. In October 2025, the U.S. Treasury Department's Office of Financial Action (OFAC) and the U.K. Financial Conduct Authority (FCDO) coordinated to impose sanctions on 146 entities, including the Prince Group, citing "listed international crimes, including the establishment and operation of cyber fraud operations relying on human trafficking and modern slavery." Chen was arrested in Cambodia in January 2026 and extradited to China, highlighting the interjurisdictional challenges of uncovering global fraud networks.
These actions mark a shift from victim relief to the structural dismantling of criminal networks.
Tickmilleas
The U.S. government is in the process of seizing the scam domain tickmilleas[dot]com, which was operated from a scam base in Tai Chang on the Myanmar-Thailand border. The site posed as a financial services company and tricked victims, primarily from the United States, into transferring BTC, ETH, USDT, and USDC to the scammers' wallets. Blockchain analysis revealed that funds were rapidly transferred via cryptocurrency exchanges in the U.S. to multiple wallets and aggregation addresses, a pattern typical of professional money laundering. The operator has ties to Chinese-backed organized crime in Southeast Asia and is protected by the DKBA (a U.S. Treasury OFAC-sanctioned armed group).
These cases highlight the scale of modern cryptocurrency fraud operations, their fusion with traditional organized crime, and the serious human rights violations they pose to both victims and those forced to engage in fraud. While international law enforcement agencies are improving their investigative and prosecution capabilities, the industrialization of fraud on a global scale remains a major challenge.
Strong regional ties with East Asia and Southeast Asia
Our on-chain analysis continues to show that cryptocurrency fraud is strongly linked to operations based in East and Southeast Asia. While the Huione Guarantee platform we identified in our 2025 report was removed from the U.S. financial system via FinCEN's 311 designation, similar operations are expanding across the region.
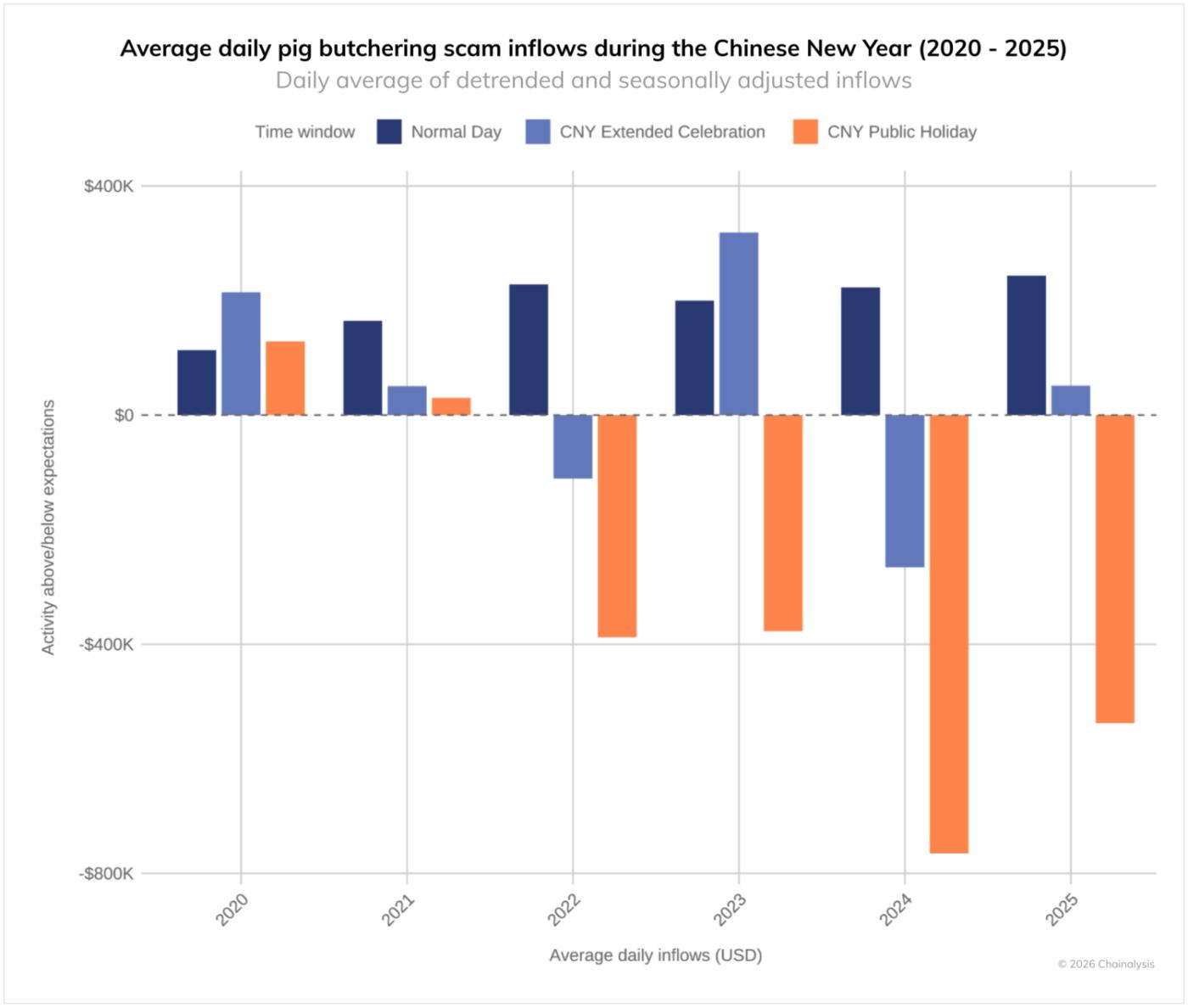
The region's centrality to romance scams (pig butchering) is a hallmark of the fraud ecosystem. The graph below shows the "holiday effect" associated with Chinese New Year (the first seven days of the 15-day New Year). Starting around 2022, Huione began to play a central role in laundering money for fraud hubs such as KK Park, and there was a noticeable drop in romance scam activity during the seven days of the Lunar New Year. This pattern suggests that actors from the region play a significant role in the fraud ecosystem.
Our research shows that Southeast Asian romance fraud networks are leveraging CMLNs (Chinese-language Money Laundering Networks) to generate billions of dollars annually. They utilize multi-layered wallet structures, exchanges, shell companies, and informal banking channels to launder funds and convert them into hard assets (such as real estate and luxury goods). The Prince Group case exemplifies this model, with fraud operators and underground laundering networks relentlessly shifting their infrastructure and expanding.
ATM fraud targeting elderly people, money laundering via collateral services and CMLN
Fraud targeting seniors is one of the most costly scams in the United States, with Americans 60 and older losing $4.9 billion in 2024 alone, the highest number of any generation ( AARP , FBI). According to the FBI's IC3, victims aged 60 and older reported losses of $2.8 billion to cryptocurrency scams in 2024, and the role of cryptocurrency is expanding. Elderly fraud takes many forms, but cryptocurrency ATMs are gaining attention as a new entry point for fraud. In particular, Bitcoin ATM scams have seen a sharp increase in recent years, with a high proportion of victims being seniors. Seniors are particularly vulnerable due to their large retirement savings and lack of familiarity with digital payments.
On-chain analysis shows that a significant portion of funds transferred from cryptocurrency ATMs in the United States are routed to wallets at CMLNs and collateral services based in Southeast Asia, making these the primary transit points in a global fraud infrastructure. While not all ATM-origin funds flow directly to CMLNs, cryptocurrency ATMs still play a vital role as a payment conduit for fraudsters targeting the elderly. Elderly people who are tricked into converting their cash into cryptocurrency at ATMs are quickly laundered through CMLNs and integrated into the global financial system.
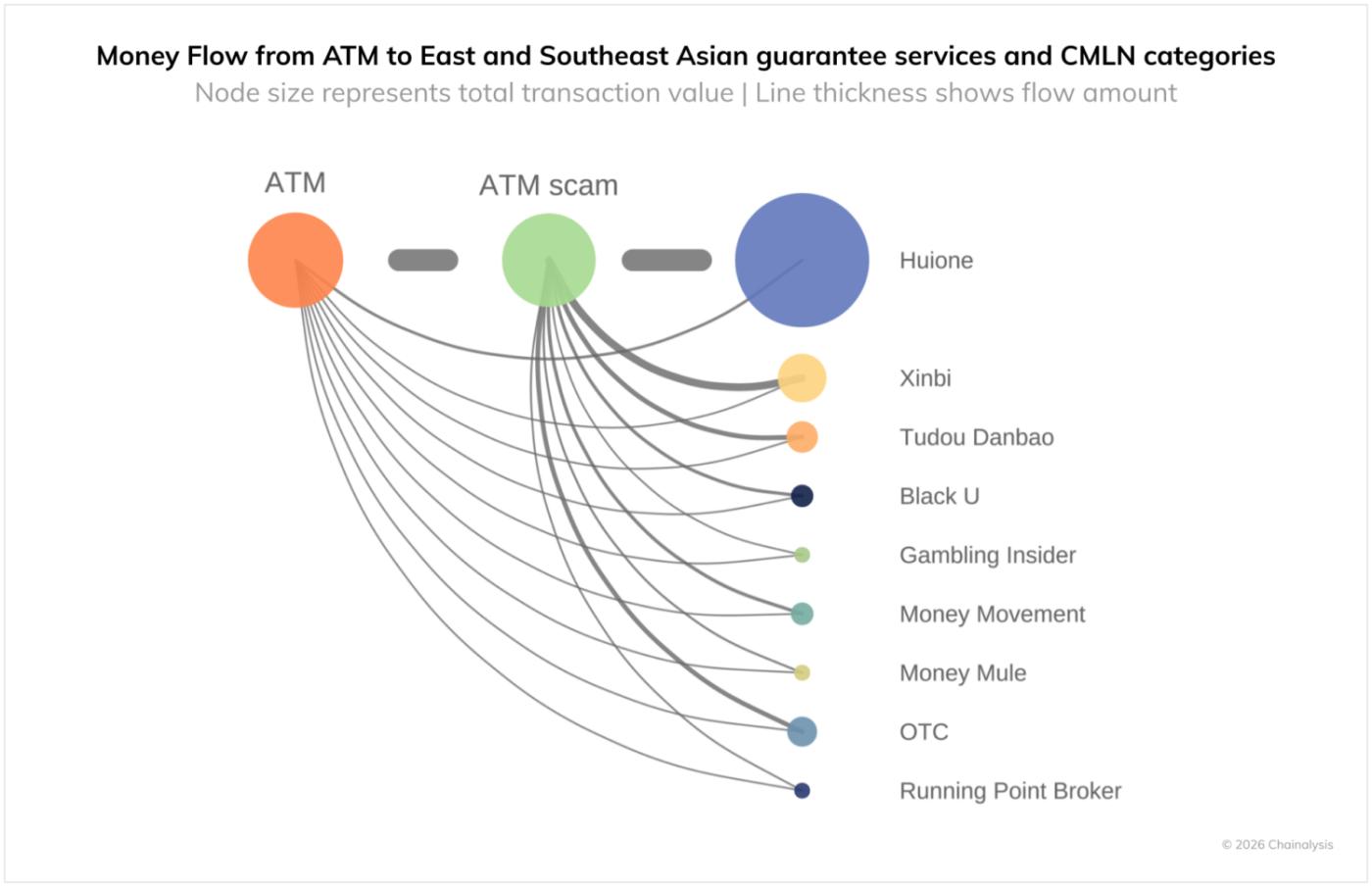
Regional infrastructure extending beyond KK Park and Huione
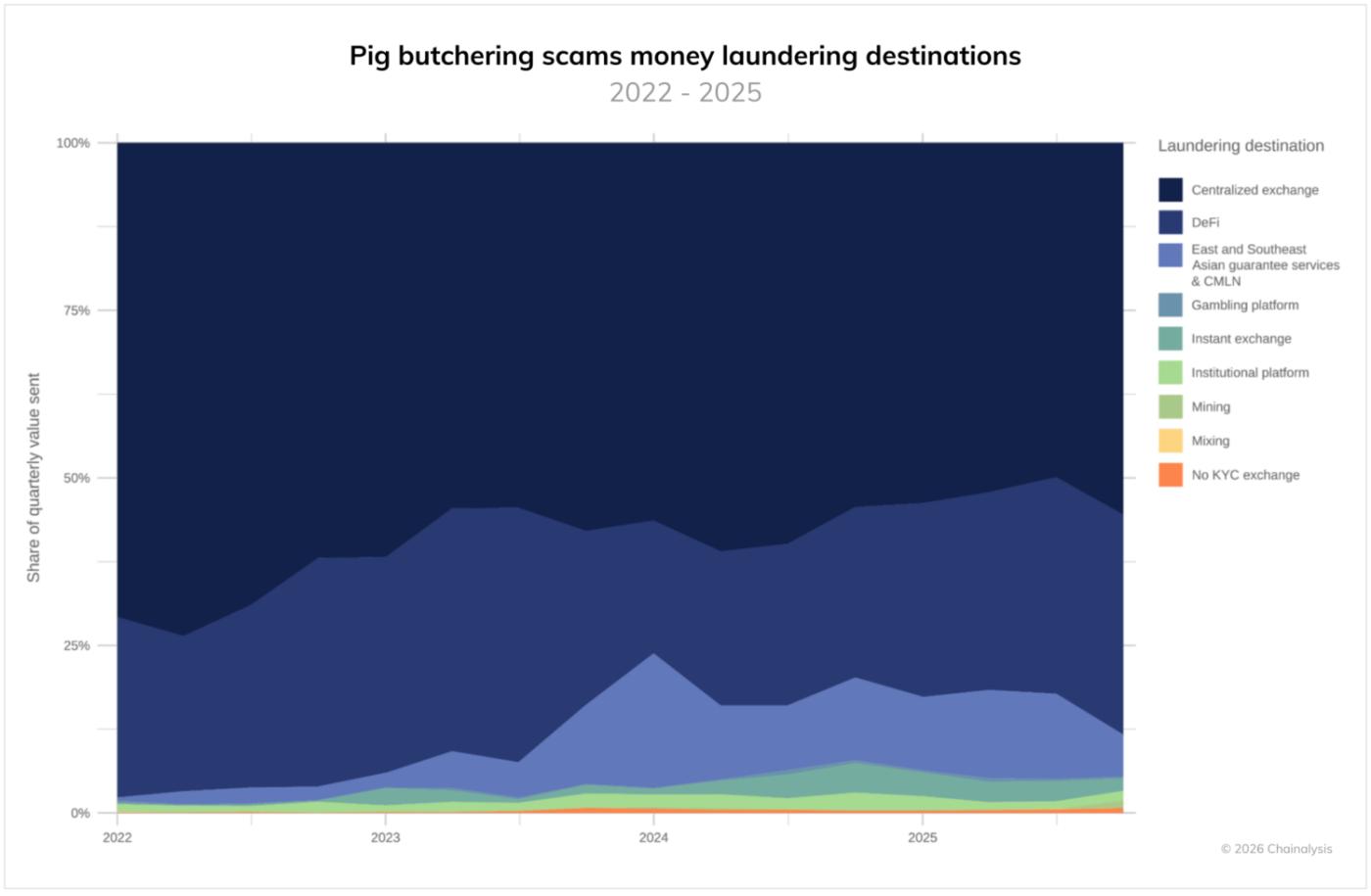
Regional ties are also evident in the distribution of cash-out destinations for fraudulent proceeds. In Q1 2022, less than 1% of romance scam money laundered through CMLN accounted for more than 20% in Q1 2024, and will remain above 10% in 2025. The growth in CMLN-related activity coincides with a decline in money laundering and liquidation on centralized exchanges, likely due to a fear of exchanges freezing funds. This suggests that CMLN has a long-term, sustained connection between romance scams targeting individuals in the United States, Canada, and Europe and Chinese-language laundering services in Southeast Asia.
Proactive and multidisciplinary response is essential to industrialize cryptocurrency fraud
The 2025 data shows that cryptocurrency fraud is becoming increasingly sophisticated, organized, and efficient. AI tools, phishing as a service, and the convergence of different fraud methods are lowering barriers to entry, allowing fraud to occur at scale. While the large-scale busts in 2025 are encouraging, fraud networks remain a significant concern. These international criminal groups, based in jurisdictions with weak governance, are flexible and persistent, continuing to evolve their infrastructure and operating models.
There is no single solution to these persistent industrial frauds; an effective multi-faceted approach is required.
- Strengthening damage prevention: Promoting the spread of real-time fraud and money mule detection systems such as Chainalysis Alterya to financial institutions and cryptocurrency businesses, and introducing advanced detection tools to protect victims themselves.
- Strengthening cross-border law enforcement cooperation: accelerating the tracing and freezing of funds to disrupt capital flows and make it more difficult to monetize illicit proceeds.
- International capacity building and technical assistance: Support for strengthening institutions and law enforcement systems
As we move towards 2026, we expect fraudsters to become even more likely to employ multiple techniques and technologies simultaneously.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient's use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claims attributable to errors, omissions, or other inaccuracies of any part of such material.
The post Cryptocurrency fraud and fraud losses will hit a record high of approximately $17 billion in 2025 due to a surge in identity theft and AI use appeared first on Chainalysis .