⚠️CrossCurve $3 Million Theft Analysis 👉On the evening of February 1, 2026, the CrossCurve (@crosscurvefi @ceo_eywa) cross-chain bridge was attacked, resulting in the theft of approximately $3 million. The vulnerability primarily stemmed from the fact that the `expressExecute` method of the CrossCurve Axelar receiver contract allowed anyone to call it. Attackers used this to trick the contract into believing that cross-chain funds had arrived, thus allowing the CrossCurve PortalV2 contract to unlock the assets. 👉The attackers stole a total of $3 million from the ETH and ARB chains, using Jumper Exchange for cross-chain operations. Most of the funds remain untouched. Below is a detailed analysis diagram and the vulnerable code. #Crypto #CrossCurve #DeFiSecurity #BlockchainSecurity
This article is machine translated
Show original
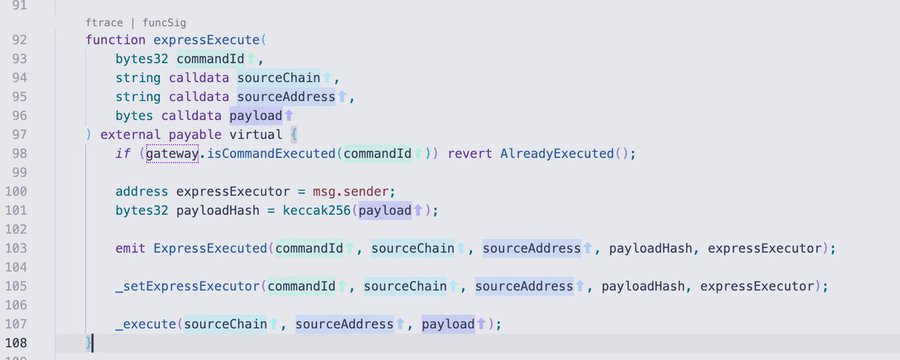
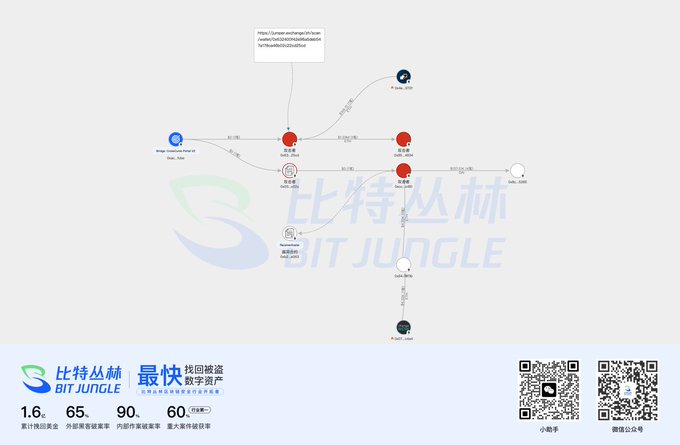
From Twitter
Disclaimer: The content above is only the author's opinion which does not represent any position of Followin, and is not intended as, and shall not be understood or construed as, investment advice from Followin.
Like
Add to Favorites
Comments
Share
Relevant content





