Say Goodbye to Compromise: How Ethereum Plans to Win Back Your Trust by 2026.
Written by: Stacy Muur
Compiled by: AididiaoJP, Foresight News
Over the past decade, Ethereum has made deliberate compromises. It traded trust in centralized third parties for convenience, autonomy for user experience, and decentralization for mainstream adoption.
Every time you check your wallet balance, you're essentially trusting companies like Alchemy or Infura. Every time you use a decentralized application, your data is being leaked to servers you never chose.
But 2026 will be a turning point. From that year onward, Ethereum will no longer ask: Is it worth diluting our core values to gain mainstream acceptance? The answer is—no longer.

Future Vision:
- Easily run a full node again (zero-knowledge Ethereum Virtual Machine + block-level access list)
- Verifiable remote procedure calls, rather than blind trust (Helios Light Client)
- Privacy payment with the experience of public payment
- A wallet that transcends fragile seed phrase(social recovery)
- An unstoppable decentralized application interface (hosted by InterPlanetary File System)
- Censorship-resistant block construction (forced inclusion list mechanism)
Historical Review: How We Came to Where We Are Today
While the base layer remains decentralized, Ethereum's infrastructure is becoming increasingly centralized.
Running a node has evolved from requiring only a regular laptop to demanding over 800GB of storage and up to 24 hours of synchronization time. Decentralized applications have transformed from simple HTML web pages into massive server-side behemoths that leak your data everywhere. Wallets have evolved from user-configurable remote procedure calls into service providers that have built-in tracking of your every move.
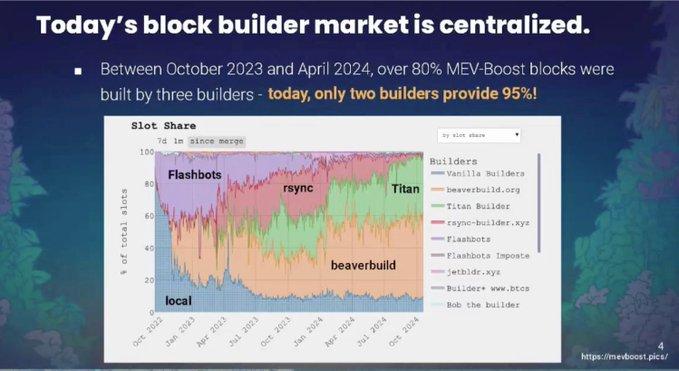
Most notably, 80-90% of Ethereum blocks are now produced by just two builders. This concentration means that the decision to include a transaction in a block is in the hands of a few entities who can arbitrarily review any transaction.
These were not mistakes, but pragmatic choices made to expand the network within the constraints of the proof-of-work mechanism.
But the cost is real: the trust assumption has infiltrated systems that should be "trustless"; single points of failure have proliferated; and users have lost true autonomy. We have achieved decentralization of the ledger, but have brought the access layer back to centralization.
Vision 2026: Seven Pillars
1. All nodes return to the masses
Current dilemma: The requirement of over 800GB of storage, 24-hour synchronization, and continuous online access deters most users.
Solution: Block-level access lists will fundamentally change this. You can think of it as a "directory" for each block, accurately informing you in advance which data states will be affected by the block. Your computer can prefetch all data in parallel before transactions are executed. Non-conflicting transactions can be executed simultaneously on different processor cores. Data shows that 60-80% of transactions do not overlap.
Combined with zero-knowledge proofs—which verify blocks without re-executing all transactions—synchronization time will be significantly reduced, and storage requirements will become easier to manage. Running nodes will move from being "limited to professional infrastructure companies" back to being "capable of being done by ordinary laptops."
2. Helios: Validate your remote procedure calls
Imagine this attack scenario: You're exchanging tokens on Uniswap. A malicious remote procedure call service provider you're connected to displays a false price. Unaware of this, you sign the transaction and receive fewer tokens than you should have. The service provider then launches a sandwich attack and profits from it. You remain completely unaware.
While this hasn't happened with mainstream service providers yet, it's technically entirely possible. The crux of the matter is: you're relying on someone else to tell you the true state of the blockchain.
Helios' solution: It solves this problem in 2 seconds. It's a lightweight client that confirms blocks by tracking a "synchronization committee" of 512 validators who rotate approximately every 27 hours. A block is considered valid canonical if more than two-thirds of the committee members have signed its header. When you query your balance, Helios requests a Merkle proof from a remote procedure call service provider you don't fully trust and verifies it locally. The service provider can refuse to answer, but it cannot lie.
It can run anywhere: laptops, mobile phones, browser extensions. Simply set it as your MetaMask remote procedure call service provider, without changing any other settings, and every decentralized application you use will become "trustless".
This technology is now open source and can be integrated.
3. ORAM and PIR: Privacy Inquiry
Every query you send to a remote procedure call service provider reveals your behavior: which addresses you monitor, which protocols you use, and when you use them.
ORAM hides access patterns through a tree structure. The server can know you are accessing data, but cannot identify which specific data. Signal's encrypted communication application uses this technology, reducing its server costs by 100 times.
PIR allows you to query a database without exposing what you're looking for. You send an encrypted query request, the server processes the encrypted data, and you receive the encrypted answer, which you then decrypt. The response data size remains essentially constant regardless of the database size.
Existing practical applications:
- Oblivious Labs: A Privacy-Friendly WBTC Balance Inquiry
- sprl.it: Privacy-enhancing ENS domain name resolution
- QuietRPC: Exploring Privacy-Friendly Remote Procedure Calls
The challenge lies in the dynamic data: recoding 33 million data entries could take anywhere from 4 to 20 minutes. The solution is to combine periodic data snapshots with on-chain authentication. For most query scenarios (such as checking balances or verifying voting eligibility), a few minutes of data latency is acceptable for privacy reasons.
4. Social Recovery: Say Goodbye to Vulnerability Seed Phrase
The current wallet's difficult choice:
- Losing the seed phrase → Losing everything
- Seed phrase stolen → Lose everything
- Cloud backup → Self-sovereignty is compromised by a pre-installed backdoor
The social recovery mechanism mitigates risk. You hold a daily signing key and set up multiple "guardians" (such as friends, family, and other devices on your device). Recovering your wallet requires approval from at least 3 out of 5 guardians. Setting a time lock (e.g., 48-72 hours) not only prevents immediate theft but also provides a legitimate recovery window.
Your phone fell into a lake? Contact your guardian, they will approve a new key, a time lock will be activated, and you will regain access after a waiting period. If someone steals your key and tries to do the same, you can cancel the operation during the time lock period.
Security: An attacker would need to control at least 3 out of 5 guardians simultaneously. You have several days to prepare. Each guardian has only partial privileges, and no tech company can install a backdoor.
Currently, wallets like @ready_co and @Safe already support this feature. The goal for 2026 is to make it a standard feature in all wallets, providing an easy-to-use experience for everyone.
5. Set privacy payment as the default option.
Privacy tools already exist, but the user experience is terrible: they require different apps, are complex to operate, cost 3-5 times more in gas, and have limited support. Almost no one uses them.
2026 Goal: Privacy-Focused Payment Experience = Public Payment Experience. Using the same wallet, the same interface, and similar costs. Privacy will become a simple "checkmark," not a complex project requiring research.
Key technologies include: zkSNARKs (proving you have funds without revealing their source), stealth addresses (using a one-time address for each transaction), and deep integration with account abstraction.
6. FOCIL: Censorship-resistant privacy protection
If the block builder refuses to include privacy transactions, then privacy payments are meaningless. With 80-90% of blocks produced by two builders, censorship is a breeze.
FOCIL makes censorship impossible:
At any given time, the system randomly selects 16 validators who choose transactions from the transaction mempool to construct a "must-have" list of transactions. The block builder must then package these transactions into the block they produce. Block validators will only vote on blocks that contain all the "must-have" transactions. Without sufficient votes, a block cannot become a valid block.
Why it works:
- Based on the committee: Only one out of 16 validators needs to be honest.
- Enforced by consensus: The mechanism is built into the core consensus rules and cannot be bypassed.
- Completed within the same period: No delay.
- At any point within a block: the builder can still optimize the value that miners can extract, but cannot censor it.
For privacy transactions: As long as one honest validator includes your privacy transaction in the "must-include" list, it will definitely be included in the block. Builders who want to censor it will face financial losses.
7. Decentralized application hosting based on IPFS
When you visit app.uniswap.org, you are actually loading a web application from their servers. If the servers go down, you will be unable to access it. If the servers are hacked even for a second, a malicious interface could wipe out your wallet. If they are under pressure, they can show different interfaces to different users.
IPFS Solution: This solution uses content addressing to host application interfaces (identified by file hashes, not server addresses). Anyone can provide these file services. Updating the application interface means generating a new hash. The ENS system then maps a friendly domain name to the latest hash.
- Advantages: No single point of failure, cannot be hijacked, resistant to censorship, verifiable.
- Challenge: Application updates mean address (hash value) changes. Solution: The ENS record always points to the latest hash value, and the update governance is gradually transferred to the decentralized autonomous organization.
Why this is crucial
"In the 'world computer,' there is no centralized ruler. There are no single points of failure. There is only passion and consensus." — Vitalik Buterin
If Ethereum eventually becomes just another platform that requires trusting a middleman, why don't users just use services like Amazon Web Services directly?
The answer must be: Ethereum offers truly unique value: genuine ownership, genuine permissionlessness, real censorship resistance, and complete autonomy.
But these features are only truly meaningful when they are readily available. A theoretically decentralized system that can only be accessed through centralized bottlenecks is nothing more than a "decentralized performance."
Success or failure hinges on this:
- Success: Ethereum will become the infrastructure of the open internet, allowing users to truly control their wealth and data, with privacy becoming the default option.
- Failure: Regulation was captured by specific entities at the access layer, users turned to more "honest" central bank digital currencies, and the cypherpunk ideals were extinguished.
The pragmatic approach of the past decade has proven the viability of blockchain technology. Now, we must demonstrate that it can continue to evolve without abandoning its core principles.
Conclusion
All of this won't be achieved in the next upgrade. Building a trustless system with a great user experience takes time. Coordinating the work of hundreds of developers will take even longer.
But our commitment remains unwavering. Every future decision will be measured by this standard: Does it enhance the system's "trustless" nature and user autonomy?
In 2026, we concluded that sacrificing core values for mainstream adoption was no longer worthwhile. We believed that "good enough" decentralization was far from good enough. We believed that users deserved a better experience than relying on infrastructure providers to access so-called "trustless" networks.
The technological puzzle is coming together. Helios already provides verifiable remote procedure calls. ORAM/PIR has demonstrated the feasibility of privacy queries. Social recovery mechanisms are running in production. FOCIL's anti-censorship specifications have been established. The path forward is clear.
Now, it's time for Ethereum to continue building the future.







