The TGBS token has been exploited, and the token pair has been drained due to a vulnerability in the TGBS token contract, allowing for the burning of the TGBS token balance in the pair. The estimated total value of the exploited funds is approximately $150,000.
Overview
Attacker address:
https://bscscan.com/address/0xff1db040e4f2a44305e28f8de728dabff58f01e1
Attack transaction: https://bscscan.com/tx/0xa0408770d158af99a10c60474d6433f4c20f3052e54423f4e590321341d4f2a4
Vulnerable contract (TGBS token): https://bscscan.com/address/0xedecfa18cae067b2489a2287784a543069f950f4
Exploit analysis
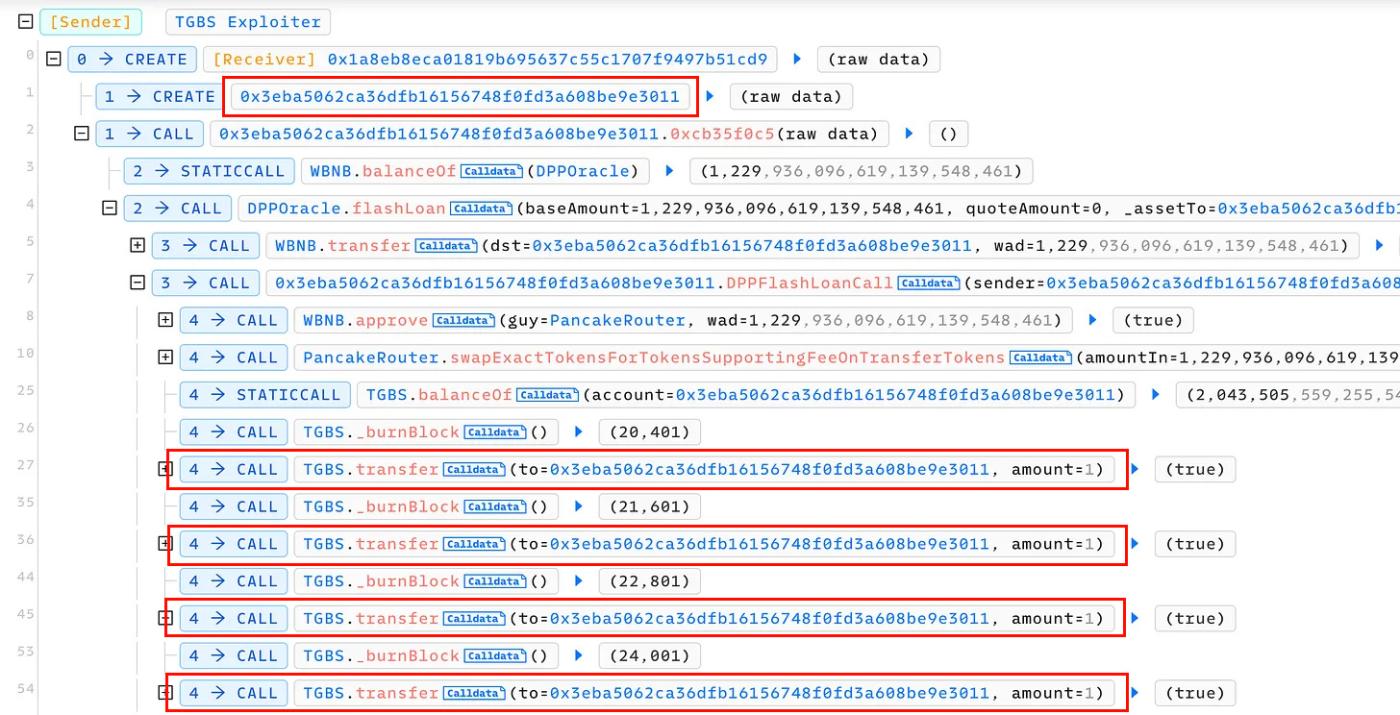
Looking at the exploit transaction, we can see that the attacker's attack contract repeatedly transfers 1 wei of TGBS token to itself. To further analyze the attack, we should examine the transfer function of the TGBS token contract.
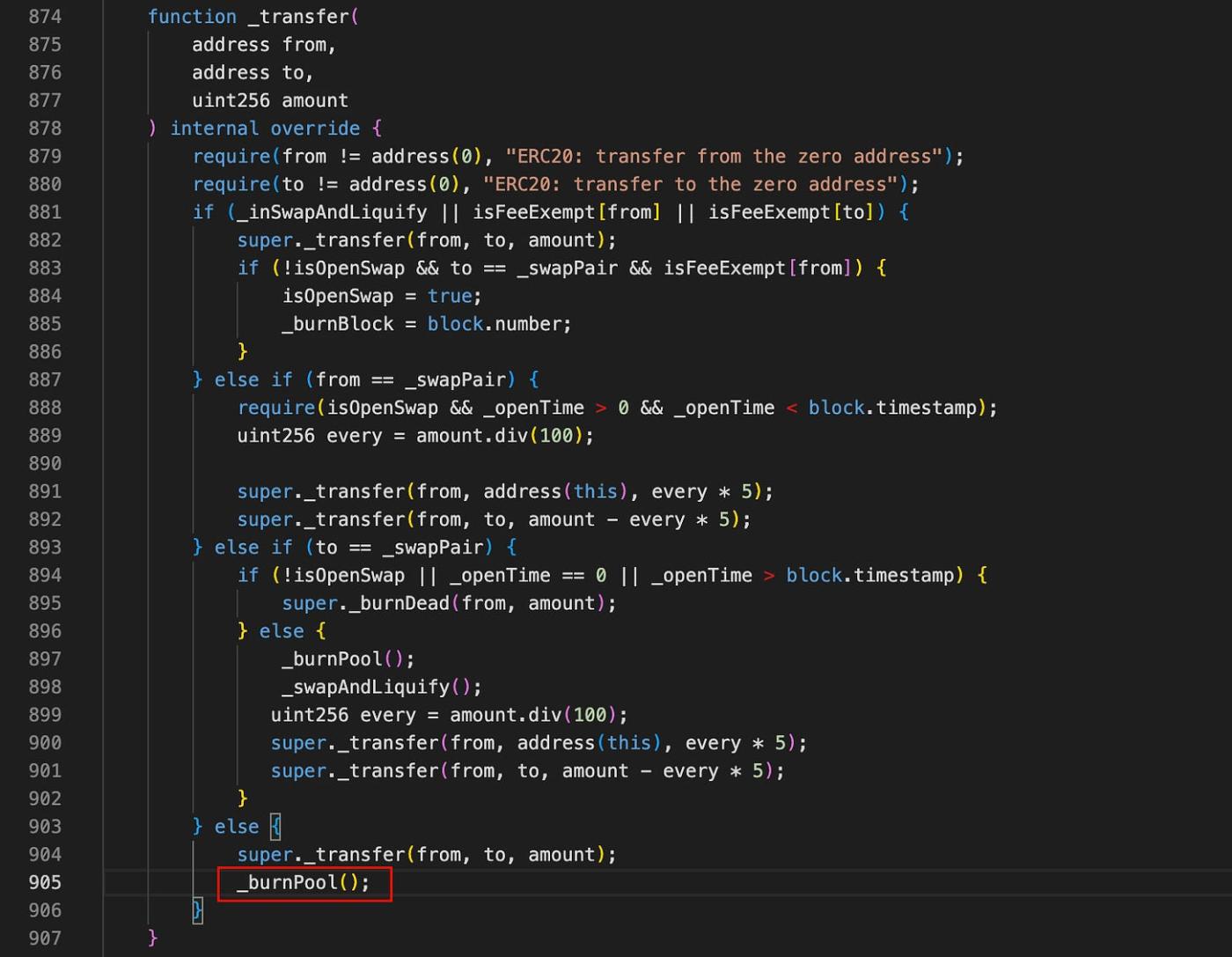
In the _transfer function, we can notice that the _burnPool internal function is called for normal transfers.
It means that, for normal transfers, a small amount of 0.3% of the _swapPair TGBS token balance will be burnt periodically. If the attacker can repeatedly trigger the _burnPool, they can effectively manipulate the TGBS token price in the _swapPair and profit from it. However, we can see that the _burnPool function is protected by the _burnBlock variable, which will be compared with the block.number and increased each time this function is called.
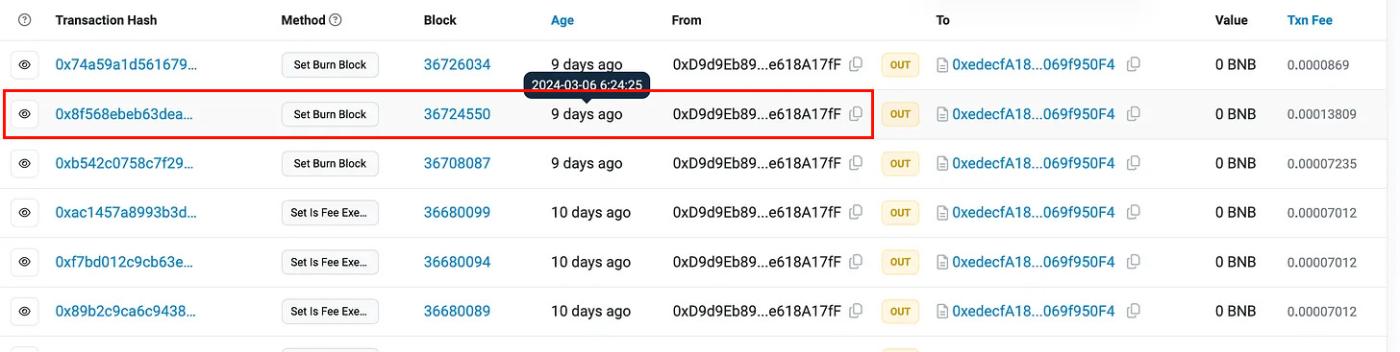
The only function to reset the value of _burnBlock is setBurnBlock, which can only be called by the contract owner.
Upon further analysis of recent transactions that called the setBurnBlock function, we observed that this function was called by the contract owner at 2024-03-06 06:24:25. The attack occurred at 2024-03-06 07:27:55 (approximately 1 hour after the admin called setBurnBlock). After the attack, the _burnBlock was reset back to its normal value at 2024-03-06 07:38:37 by the admin.
Conclusion
We're still not clear whether this exploit is a rug pull or not. However, calling a function that can change the value of important internal variables without any security awareness or public announcement to users is not recommended in any case.