A running project in OPTIMISTIC with main token named MO was exploited on Mar 14, 2024 with loss approximately $413k. The exploited contract has two weak points in a function which allows attacker steal USDT from both Loan and Pair contracts.
Overview
Attacker: https://optimistic.etherscan.io/address/0x4e2c6096985e0b2825d06c16f1c8cdc559c1d6f8
Vulnerable Contract:
https://optimistic.etherscan.io/address/0xae7b6514af26bcb2332fea53b8dd57bc13a7838e
Transaction attack: https://optimistic.etherscan.io/tx/0x4ec3061724ca9f0b8d400866dd83b92647ad8c943a1c0ae9ae6c9bd1ef789417
Thanks for reading Verichains! Subscribe for free to receive new posts and support my work.
Exploit Analysis
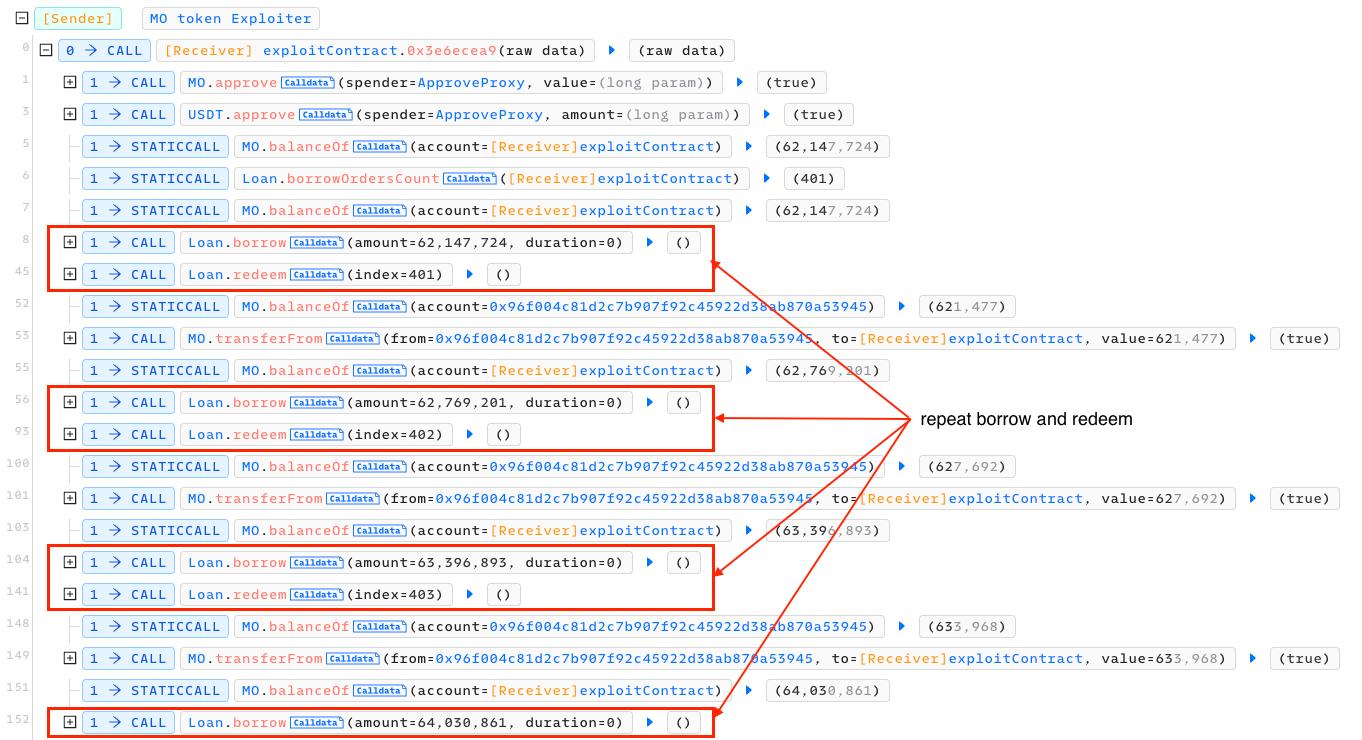
Following the attack transaction, the attack was remarkably simple: utilized a loop to borrow USDT and promptly redeem it. Through multiple iterations of this process within the same transaction, the attacker managed to borrow a substantial amount of USDT and simultaneously swapped MO tokens to obtain more USDT within the pair.
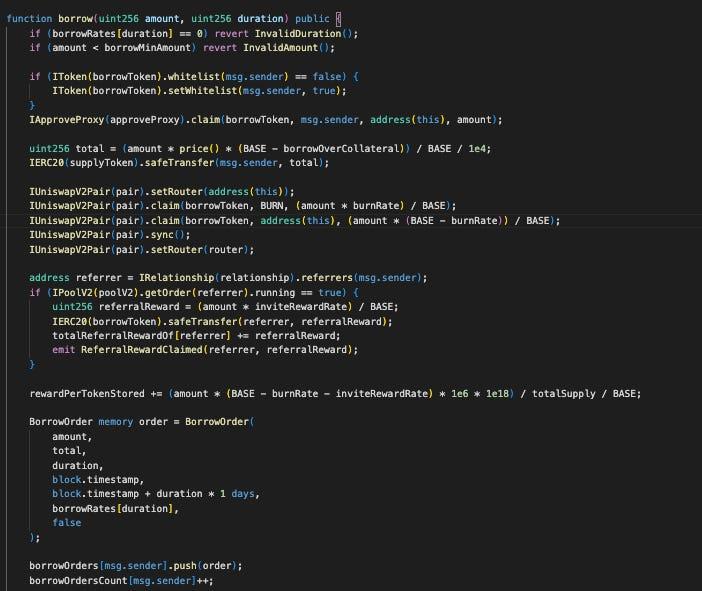
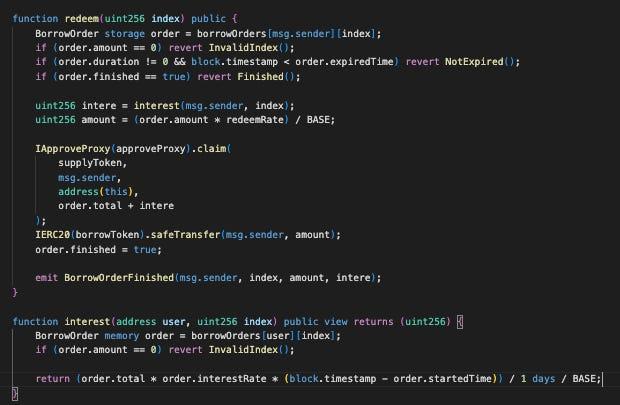
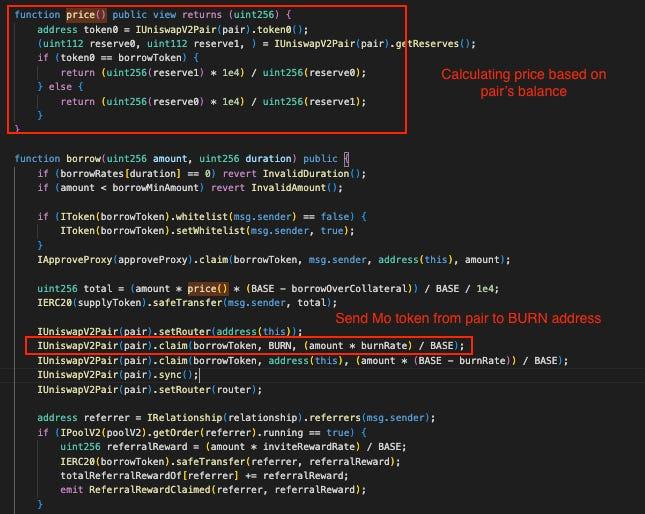
Investigate the borrow function:
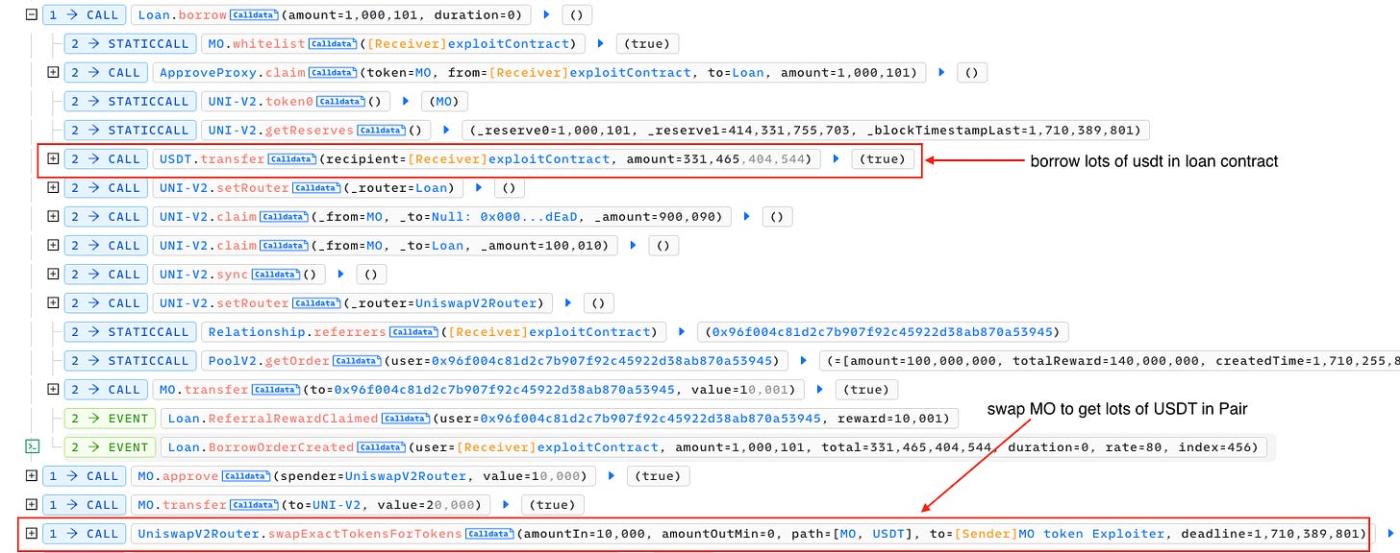
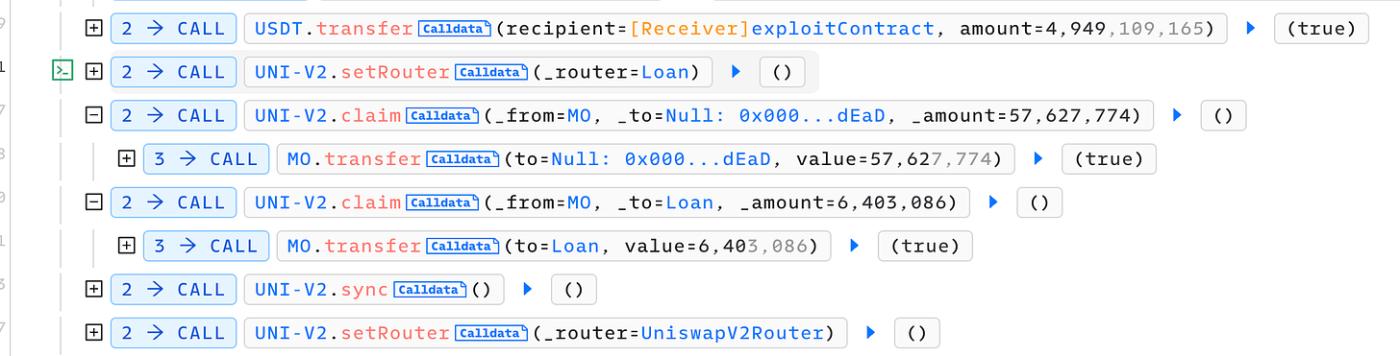
When utilizing the borrow function, users are required to deposit an amount of borrowToken as collateral. The quantity of supplyToken that can be borrowed depends on the collateral amount and market price. Additionally, the amount of borrowToken within the pair is also burned (sent to a BURN address) to boost the market price.
Dive into the redeem function:
The redeem function calculates interest based on the time elapsed, but the timestamp only increases when the block increases. Consequently, if a user redeems their balance within a single block, they won’t incur any fees.
Considering the logic derived from the aforementioned functions, it's apparent that if we borrow and redeem immediately, the market price will be pumped, thus exempting us from charges and enabling us to borrow more USDT in subsequent transactions. Throughout the attack process, the price of the MO token also increases, allowing the attacker to acquire a substantial amount of USDT from the pair through swapping.
The root cause of the vulnerabilities lies in the burning of tokens within the pair and the utilization of market price logic.
Lesson learned
There are two critical weaknesses in the borrow function that we should merit attention.
Firstly, the direct transfer of tokens from the pair to an external destination represents an extreme dangerous action. The balance of tokens within the UniswapV2 Pair is instrumental in calculating the K state, directly impacting the token price. Consequently, any action exhibiting similar behavior should be restricted to the admin side or a clearly verified function.
Secondly, relying on the price calculated from the pair's balance makes the system vulnerable to price manipulation. Even without the inclusion of burning tokens within the pair, the current contract remains susceptible to flashloan attack. Attackers can utilize substantial assets from a flash loan to inflate the MO token price before calling the borrow function and then deflate the MO to the original price. Within the borrowing process, the inflated price allows attackers to steal a significant amount of USDT from the contract.
Thanks for reading Verichains! Subscribe for free to receive new posts and support my work.