Why Teamwork Matters?
Complexity of Code Bases
As smart contracts evolve, they tend to become increasingly complex. It's not uncommon for codebases to consist of hundreds or even thousands of lines of code spread across various modules and libraries. Navigating through such complexity alone can be overwhelming and prone to oversight.
Thanks for reading Verichains! Subscribe for free to receive new posts and support my work.
Comprehensive Coverage
To ensure an in-depth check, it's essential to cover all aspects of the codebase. With multiple team members involved, each bringing their unique perspectives and expertise, the chances of overlooking critical vulnerabilities decrease significantly.
Knowledge Sharing
Collaborative code reviews facilitate knowledge sharing among team members. By discussing and critiquing each other's findings, team members can broaden their understanding of security best practices and emerging threats.
Cross-Checking for Diverse Perspectives
Different individuals approach problem-solving in different ways. By harnessing the collective intelligence of the team, code reviews can benefit from diverse perspectives, leading to more robust security measures.
Tools to Facilitate Collaboration
Automation Security Tools for Smart Contracts
For projects utilizing smart contracts, specialized automation tools can detect blockchain-specific vulnerabilities. Integrating the output of these tools into the code review process provides an additional degree of security examination.
Common tools such as Slither, Semgrep, and 4naly3er all support SARIF export to render on another tool.
SARIF Format, Explorer, and Finding Management
Static Application Security Testing (SAST) tools often generate results in the Static Analysis Results Interchange Format (SARIF). This standardized format allows for seamless sharing and parsing of security findings across different tools and platforms.
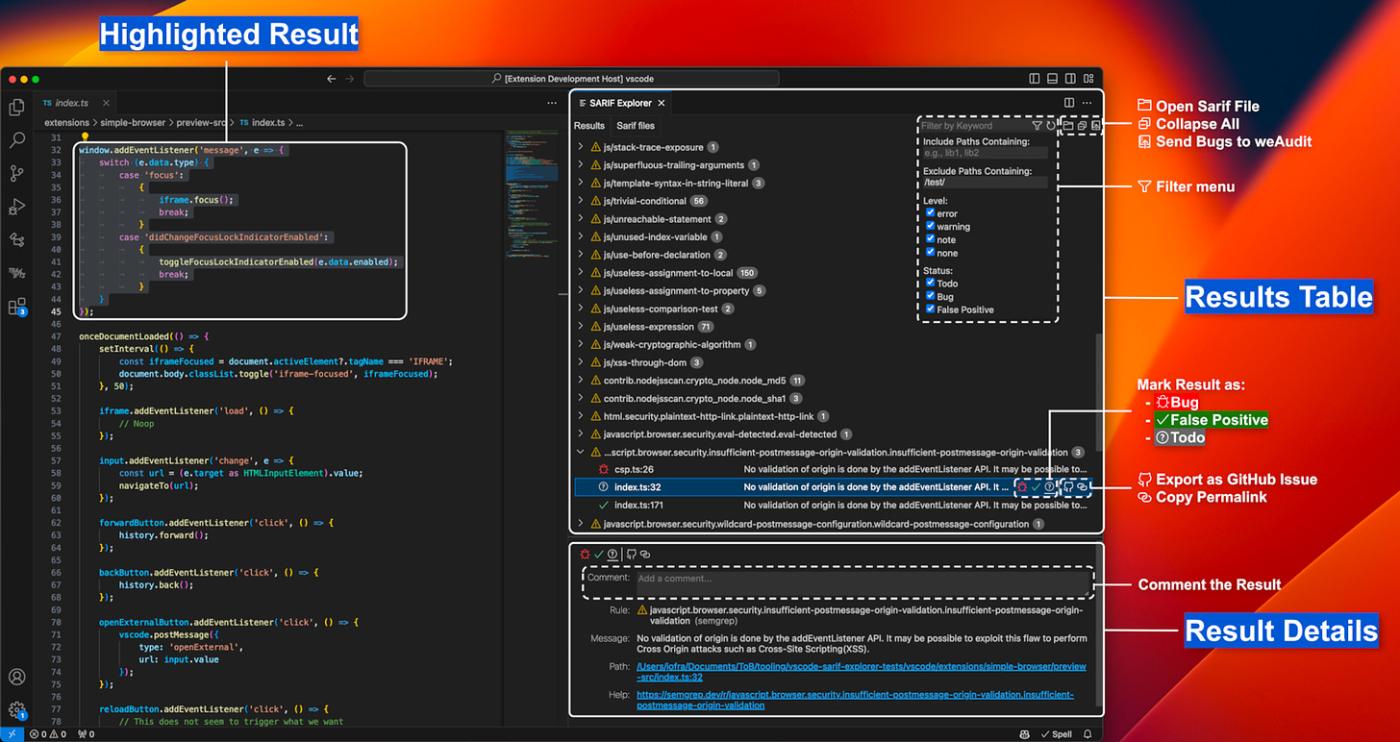
A new tool by Trailofit on the VSCode allows explore SARIF files and management bugs on this: https://marketplace.visualstudio.com/items?itemName=trailofbits.sarif-explorer
The main feature of the tool is the ability to render results on the table, describe details of findings, and mark bugs or false positives.
Utilizing plugins or platforms dedicated to managing security findings streamlines the process of tracking and resolving identified issues. These tools often support features such as assigning tasks, setting priorities, and monitoring progress, ensuring that vulnerabilities are promptly addressed.
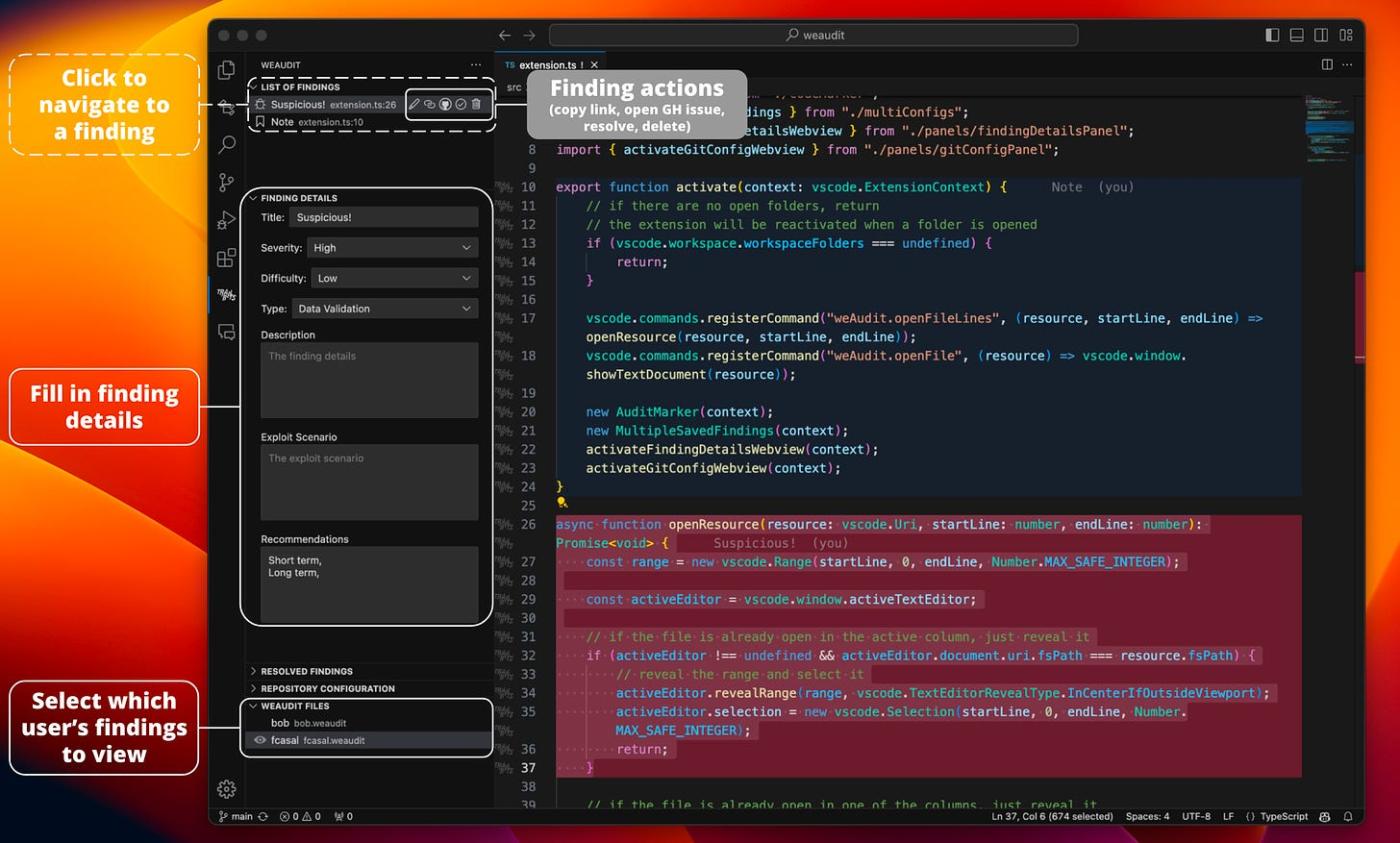
Another tool by Trailofbit that enables managing findings, also integrated with SARIF explorer: https://marketplace.visualstudio.com/items?itemName=trailofbits.weaudit
The main features are highlighting to mark the region as bugs or for notes, managing findings, describing details for those findings, and team members sharing via GitHub.
How It Works in Practice
Exporting Automation Tool Results to SARIF Format: after running automated security scans, export the results to SARIF format to standardize the findings.
Rendering Results in SARIF Explorer: Use SARIF Explorer to visualize and explore the security findings. Team members can navigate through the findings, mark false positives, and prioritize issues for further investigation.
Forwarding Bugs to Finding Management Plugins: Once identified, security bugs should be promptly forwarded to finding management plugins or platforms. This ensures that they are tracked, assigned, and addressed systematically.
Describe details of findings on the WeAudit plugin with severity, likelihood, type of vulnerability, exploitation scenarios, and recommendations to fix them.
Sharing .vscode Folder to team members: To facilitate collaboration, share the .vscode folder containing workspace settings, including any custom configurations or extensions used for security code reviews.
End of the day, each team member will take daily notes and synchronize the .vscode folder with each other via Github.
Suggestions for Improvement
1. Utilizing SARIF for Management Checklists
Extend the use of SARIF beyond just visualizing findings. Utilize its structured format to create and manage checklists for security reviews, ensuring that all necessary steps are followed systematically.
The SARIF explorer allows make bugs or not and also provides make check list that auditors can check step by step.
2. Daily Notekeeping Without Marking Reviewed Files
Encourage team members to maintain daily notes or journals documenting their code review activities and findings. This serves as a valuable reference for tracking progress and sharing insights with the team.
By embracing collaborative teamwork and leveraging appropriate tools and methodologies, organizations can enhance the effectiveness and efficiency of their security code review processes. With shared responsibility and collective expertise, teams can better safeguard their software against potential security threats and vulnerabilities.
3. Exporting results of WeAudit plugin to an audit report
In the process of conducting security code reviews, one crucial step is compiling the findings into a comprehensive audit report. This report serves as the final deliverable, summarizing the identified vulnerabilities, proposed remediation strategies, and overall security posture of the application. Integrating the results of the WeAudit plugin into this audit report ensures that all security issues are adequately documented and communicated to stakeholders.
Conclusion
In conclusion, by embracing collaborative teamwork and leveraging appropriate tools and reporting mechanisms, organizations can optimize their security code review processes. Through shared responsibility, knowledge sharing, and transparent communication, teams can strengthen the resilience of their software applications against potential security threats, thereby safeguarding sensitive data and maintaining user trust. By continuously refining and improving their approach to security code reviews, organizations can stay ahead of emerging threats and ensure the long-term security and integrity of their software products.
Thanks for reading Verichains! Subscribe for free to receive new posts and support my work.