Author: Frontier Lab
Introduction
PhalaNetwork was established in 2018, and at the beginning of the project, Phala Network positioned itself in the privacy computing track, combining the smart contract execution environment with TEE to achieve secure and reliable smart contract execution. At the same time, Phala Network also provides a complete privacy protection mechanism to ensure that user data is controlled by the users themselves. In 2023, due to the AI-driven market trend driven by the US stock market, Phala Network closely followed the AI trend and started working on AI agents, and also closely followed the modular concept, building itself into the execution layer of AI.
Project Basic Information
Basic Information
Website: https://phala.network/
Twitter: https://twitter.com/PhalaNetwork
Discord: https://discord.com/invite/phala-network
Whitepaper: https://docs.phala.network/
Launch time: The Token was launched in 2020
Project Team
Core Team
Marvin Tong: Founder & CEO. Graduated from the Communication University of China with a master's degree, and has been working as a product manager at companies like Tencent and Didi.
Hang Yin: Co-founder & Chief Technology Developer. Graduated from Fudan University in China. Previously an expert in Google's search ML-related fields, one of the Polkadot ambassadors in China, and the founder of Bitcoin Gold.
Zhe Wang: Co-founder & Chief Operating Officer. Graduated from Huazhong University of Science and Technology in China with a master's degree, an expert in the computer hardware laboratory of Huazhong University, and the CTO & CEO of Bitcoin Gold, Xiaohei Technology and Haha Retail.
Jun jiang: Co-founder & CTO. Former site administrator of RubyChina, former CTO of KnewOne, and former software architect of DJI.
Advisory Team
Shun Fan Zhou: One of the authors of the Phala Network whitepaper, a doctoral student in the System Software and Security Laboratory of Fudan University, has published research on attack transactions and defense measures in the Ethereum ecosystem at the top international security conference USENIX Security, and has co-authored multiple papers at top international security conferences.
Sandro Gorduladze: Angel investor and partner at HASH CIB. Sandro set up the research department at HASH, which gained fame for its in-depth reports. Before joining HASH, Sandro worked at PwC Russia, providing tax consulting services to companies in the TMT industry.
Konstantin Shamruk: PhD in Economics from the University of Toulouse, France. He led the economic design analysis work for the Phala Network.
Jonas Gehrlein: Research Scientist at the Web3 Foundation. He is responsible for researching economic issues in the Polkadot ecosystem at the Web3 Foundation. Prior to joining W3F, Jonas obtained a PhD in Behavioral and Experimental Economics from the University of Bern, where he studied human behavior in markets and organizations. Before that, he earned a master's degree in Quantitative Economics from the University of Konstanz.
Zo Meckbach: Polkadot Senior Ambassador, researcher and advocate for Web3 and cybersecurity. She is currently the COO of MH-IT & Service GmbH, and previously held an application analytics position at Google.
Financing
Phala Network has raised around $10 million through one round of financing.
Seed Round
In July 2020, Candaq Group, IOSG Ventures, SNZ, Incuba Alpha Group, nfiChain, Exoplanet Capital and Blue Mountain Labs invested $10 million in this round.
Development Strength
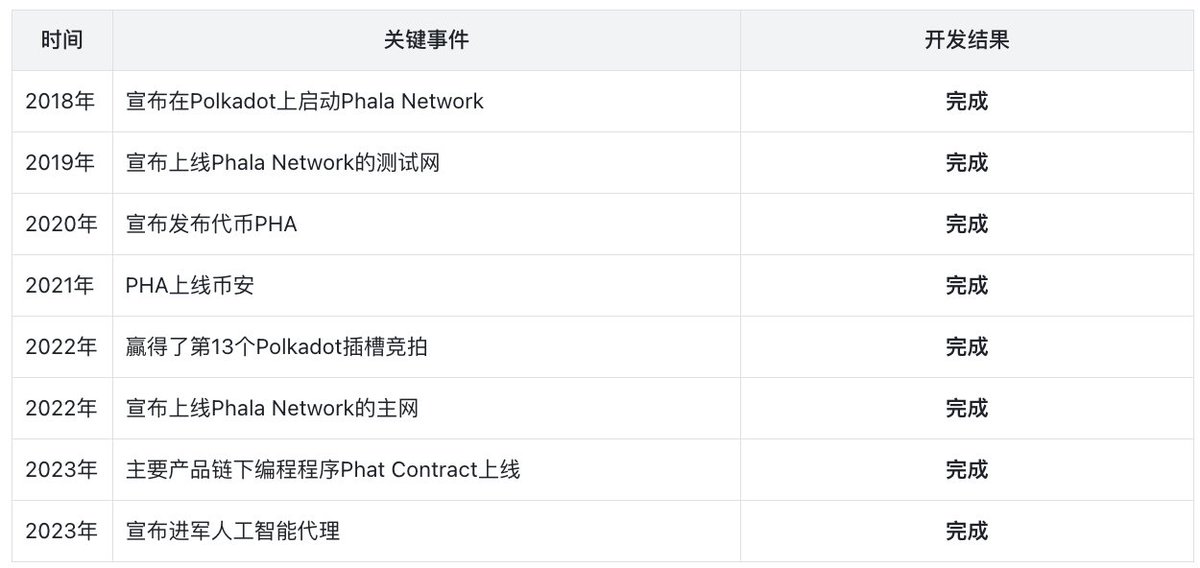
Phala Network was launched in 2018 by the founder Marvin Tong. The key events in the project's development are shown in the table:
From the project development roadmap of Phala Network, the Phala Network team has been able to complete the scheduled project plan on time at each key time point of the project, which shows that the technical development team led by Marvin Tong and Hang Yin is very strong. Although Phala Network has a broader development prospect after entering the AI track, the technical challenges it faces will become greater, and the requirements for the technical development team will become higher.
Technical Features
Phala Network is a privacy computing infrastructure based on the Polkadot ecosystem, aiming to achieve data confidentiality and privacy protection through Trusted Execution Environment (TEE) technology, cloud computing services and cross-chain data confidentiality layer. At the same time, Phala Network adopts an AI co-processor, providing a secure and verifiable computing solution for integrating encryption and AI at the application layer.
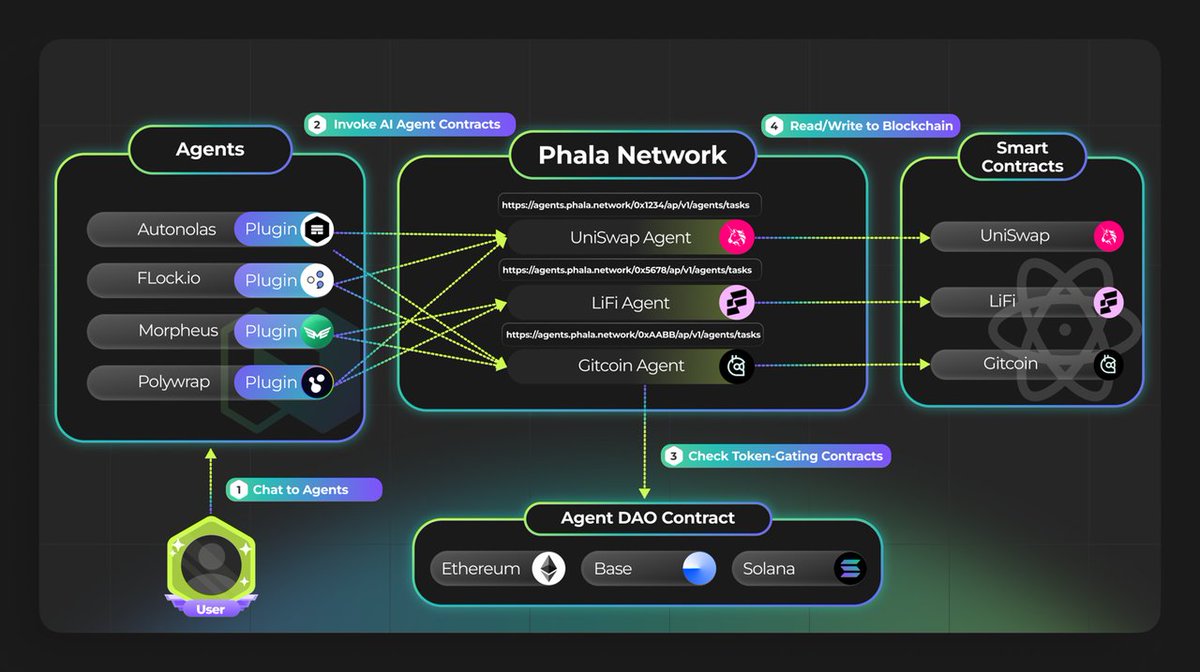
It can be simply understood that Phala Network has added an AI co-processor on the basis of the original privacy computing infrastructure, so that AI agent contracts can be deployed on Phala Network, making Phala Network the execution layer of Web3 AI. Phala Network has used TEE technology to provide privacy protection, and now through Phala Network's AI agent contracts, it can access top-level LLMs and the control rights come from the smart contracts written on the chain.
Schematic diagram of Phala Network's AI Agent (image source: Phala Network whitepaper)
Before adding the AI agent contract, Phala Network's main technical features were to achieve data confidentiality and privacy protection through various technical means. First, Phala Network uses hardware privacy computing technology, especially Trusted Execution Environment (TEE), to ensure the confidentiality and integrity of data during the computation process. All computations running in the TEE guarantee the correctness of program execution and the security of data, and Phala Network also combines zero-knowledge proof technology, which can realize privacy transactions, so that the data of smart contracts does not need to be made public, thereby protecting user privacy. In this way, Phala Network can provide general and easy-to-use confidential smart contracts that support zero-trust cloud services.
The key points are the Trusted Execution Environment (TEE) and the multi-layer key rotation system.
Trusted Execution Environment (TEE): The Trusted Execution Environment (TEE) is a privacy-focused technology that isolates a node's code execution and operations from the main operating system of the computer processor. Phala Network uses Intel's Software Guard Extensions (SGX) for TEE processing. This system ensures that even individuals with physical access, such as Phala Network operators or malicious third parties, cannot view the node's state or manipulate the data processed by the node. Usually, the Trusted Execution Environment is used instead of Zero-Knowledge Proofs (ZKPs). In Phala Network, TEE is not only used to protect the confidentiality and integrity of data, but also supports complex computational tasks. For example, by transferring the execution of smart contracts to secure off-chain workers supported by TEE, Phala Network can fully utilize the computing power of individual workers without worrying about the risk of data leakage or tampering.
Multi-layer Key Rotation System: Phala Network has a group of special worker nodes called "Guardians" whose main task is to ensure the security of computations. In Phala Network, Worker nodes do not have the authority to exit the network at any time, so tasks need to be deployed to redundant Worker nodes with the same key to ensure access to encrypted inputs, outputs and program states. The Guardian nodes are responsible for managing the encryption keys and dynamically allocating the secrets to the worker nodes, ensuring the security and integrity of the data. At the same time, Phala Network adopts a comprehensive key rotation mechanism to ensure the privacy of its contracts and the overall security of the system. This process periodically updates the master key according to the election rules. In the new cycle, new Guardians are elected, and a new master key is generated through a secure key exchange protocol. The new key is used to re-encrypt the Guardian state, which is then distributed and confirmed among the new Guardians. During this transition period, communication between miners and Guardians will be temporarily interrupted to maintain consistency and security. Communication will only resume after the key rotation is complete, with a delay of two on-chain confirmations. In addition to rotating the master key, Phala Network also periodically updates the cluster key and contract key to enhance security.
Here is the English translation of the text, with the specified terms translated as instructed:After adding AI agent contracts, Phala Network's main business has shifted from its previous privacy computing infrastructure to becoming the execution layer for Web3 AI. Its previous privacy computing infrastructure has now become the foundation for the current Web3 AI execution layer, and the existing AI agent contracts are operating on top of the previous privacy computing infrastructure.
AI Agent Contract: The AI agent contract is a tool for users to build smart contracts. Users can use it to control AI agents that can run on-chain or off-chain. These AI agents' code is written in TypeScript/JavaScript and executed on Phala Network's nodes, and they can aggregate data from external APIs and inject custom AI agents. AI agents leverage Phala Network's trustless cloud computing infrastructure for off-chain confidential computations. Technically, the AI agent contracts run on the TEE of the worker nodes, which are managed by Phala Network. A subset of the gatekeeper worker nodes is responsible for key management to ensure network security. These contracts provide developers with powerful tools to leverage AI agents to perform various tasks, and their secure and private execution environment ensures the protection of sensitive data.
pRuntime: The worker nodes host the AI agent contracts in their TEEs, where the TEE protects the code integrity and privacy of the workload, ensuring the contracts' execution is secure and tamper-proof, while providing the network with powerful computing capabilities. pRuntime (Phala Runtime) is a program running inside the TEE, which is the core component of Phala Network's worker nodes. pRuntime is responsible for receiving and executing computation tasks from the Blockchain, ensuring the computations' integrity and security.
In summary, Phala Network has introduced AI agent contracts, making AI agents as easy to run as smart contracts, and allowing AI agents to be managed by smart contracts, enabling them to be dynamically managed and access-controlled. The AI agents can freely call each other, forming complex applications, all running within the TEE to ensure code integrity and privacy. This transformation has allowed Phala Network to leverage the advantages of its previous privacy computing infrastructure as it becomes the execution layer for Web3 AI.
Innovations Compared to Competitors
After introducing the AI co-processor, Phala Network's primary narrative has shifted from the privacy computing infrastructure track to the AI track's algorithm sub-track, with competitors such as Morpheus, QnA3.AI, Fetch.ai, SingularityNet, and ChainGPT.
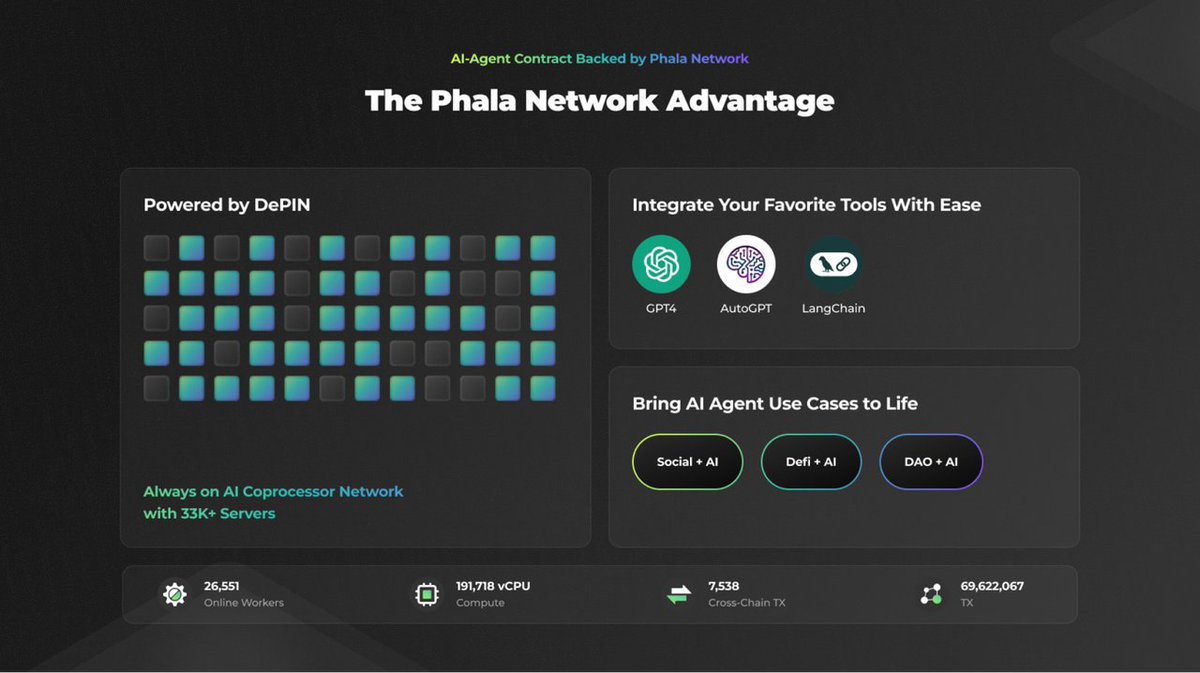
Phala Network's Advantages (Image source: Phala Network whitepaper)
Exceptional Privacy: Phala Network's previous focus on privacy computing has given it inherent privacy advantages. Phala Network uses hardware-based privacy computing technologies, especially TEE, to ensure the confidentiality and integrity of data during computation. All computations within the TEE guarantee the correctness of program execution and data security. Phala Network also combines zero-knowledge proof technology to enable private transactions and protect smart contract data, maintaining user privacy.
Powerful Functionality: Phala Network's introduction of AI agent contracts has given it a significant advantage in the AI agent track. AI agent contracts make running AI agents as simple as running smart contracts, allowing AI agents to be managed by smart contracts and dynamically managed and access-controlled. This also enables EVM smart contracts to extend their functionality off-chain, greatly improving the deployment and efficiency of AI agents.
Rich Integration: Phala Network's use of AI agent contracts allows it to aggregate data from external APIs and inject custom AI agents, eliminating the learning curve for accessing decentralized applications. This enables easy and large-scale integration of external AI tools and projects, such as OpenAI, LangChain, and GPT4.
Broader Applications: The use of AI agent contracts makes the deployment of Phala Network's AI agents very simple and applicable to a wide range of domains. Users can connect their custom AI agents to Social, DeFi, or DAO applications to improve their work and life efficiency.
In summary, Phala Network's outstanding performance has made the deployment and use of AI agents a simple task, solving both the ease of operation and deployment, as well as users' privacy concerns, giving Phala Network a significant advantage in the AI track competition.
Project Model
Business Model
Phala Network's economic model now consists of four roles: miners, stakers, users of AI agent contracts, and users of privacy computing.
Miners: Phala Network's miners are the providers of network computing power, contributing their CPU power to the network in exchange for rewards.
Stakers: To prevent miner misbehavior, Phala Network's mining design requires miners to stake a certain amount of PHA tokens as collateral. Stakers can be either Stakepool or Vault. Stakepool is for miners who provide both computing power and token staking, while Vault allows token holders to stake their PHA without directly operating a node.
Users of AI Agent Contracts: Users running AI agent contracts on Phala Network are now the primary users, paying usage fees in PHA tokens, which is a major source of Phala Network's revenue.
Users of Privacy Computing: Phala Network's excellent privacy computing business will still attract users with real privacy computing needs. The fees paid by these users are also a major source of income for miners and Phala Network.
Phala Network's revenue sources are:
- Fees paid by users of AI agent contracts
- Fees paid by users of privacy computing
Token Model
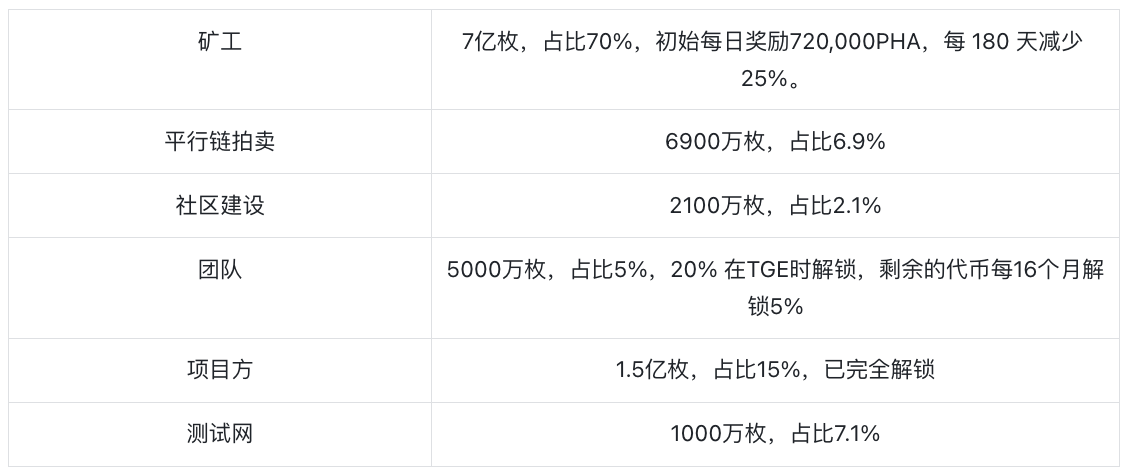
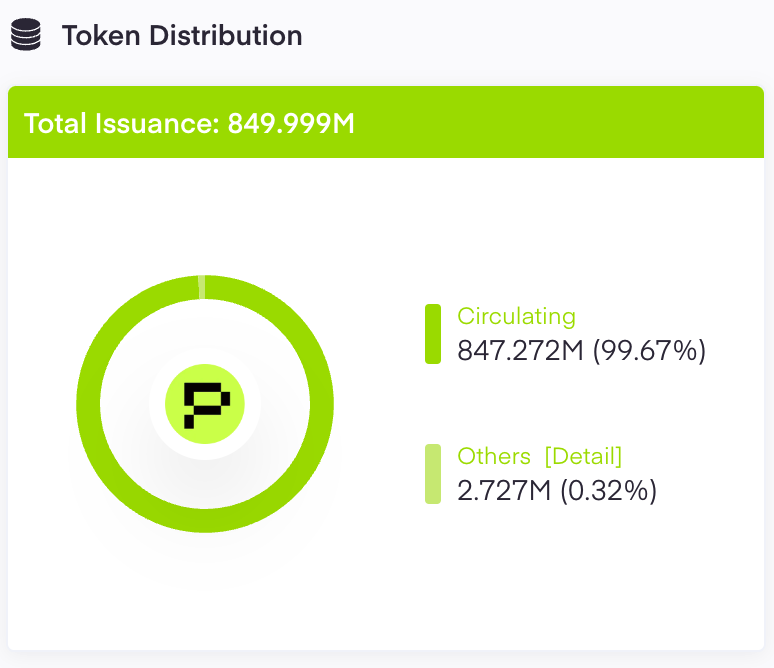
According to the whitepaper, the total supply of $PHA is 1 billion, with a current circulating supply of 738.3 million, or 73.83% of the total. The token distribution is as follows:
PHA Token Utilities:
- Miner Rewards: Miners receive PHA tokens for mining new blocks, in exchange for providing computing power.
- Usage Fees: Users pay PHA tokens to use AI agent contracts and privacy computing services.
- Governance Participation: Staking PHA tokens allows participation in PhalaDAO governance.
- Staking: Miners must stake a certain amount of PHA tokens as collateral to prevent misbehavior.
Valuation of the Value of PHA
According to the whitepaper, the empowerment of the PHA Token in the Phala Network network is moderate, with the addition of a staking mechanism, which indirectly increases the locking of PHA Tokens to increase the value of the project, and now the circulation rate of PHA Tokens has reached 73.83%. From the perspective of circulation rate, the current circulation rate of PHA is slightly high, but it is still in the stage where nearly one-third of the Tokens have not been developed, so in the future development of the project, the increase in the value of PHA Tokens will come more from the inherent value of the Phala Network project, that is, the degree of use of artificial intelligence proxy contracts by market users. If the usage is high, then as the Token price rises, the miner's revenue will also become higher, which will lead to more miners entering the mining and locking more Tokens to reduce the circulation rate, thus forming a positive flywheel. However, there is no scenario of centralized destruction or regular destruction of PHA Tokens, which is a shortcoming in its Token economics. If Phala Network's business does not develop well, its Token price will not rise accordingly.
Token Price Performance
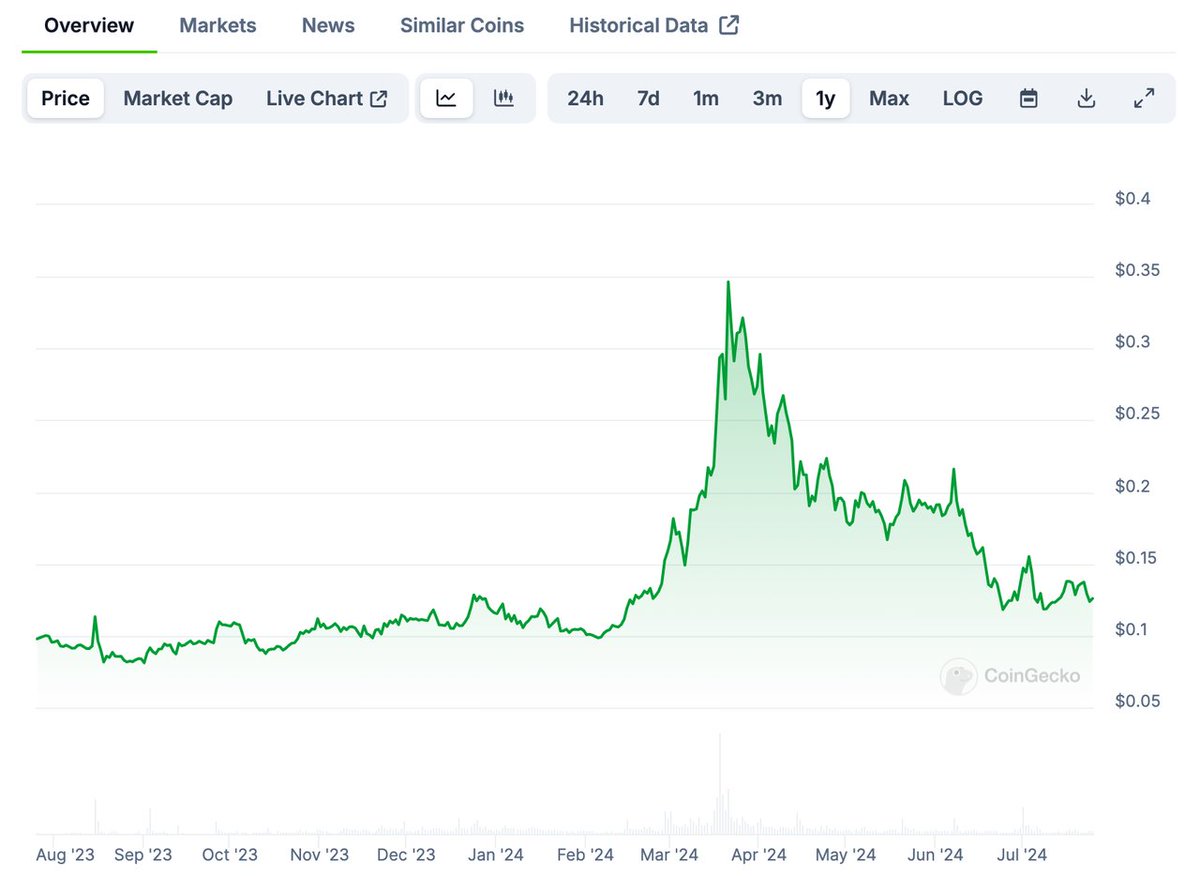
PHA Price Trend
Data source: https://www.coingecko.com/en/coins/phala-network
According to Coingecko's statistical data, PHA has risen by more than 4 times (from a low of $0.0816 to a high of $0.3465) in the past year since July 2023, with the main trading venues being Binance, OKX, HTX and other top exchanges. The rise this year is mainly due to the dividends of the AI track development.
Market Cap
The current price of PHA is $0.126, the current circulating supply is 738,334,838 PHA, and the market cap is: $93.43 million.
FDV
The current price of PHA is $0.126, the total circulating supply is 1 billion PHA, and the market cap is: $126.54 million.
Daily Trading Volume
The daily trading volume of PHA is around $5.66 million.
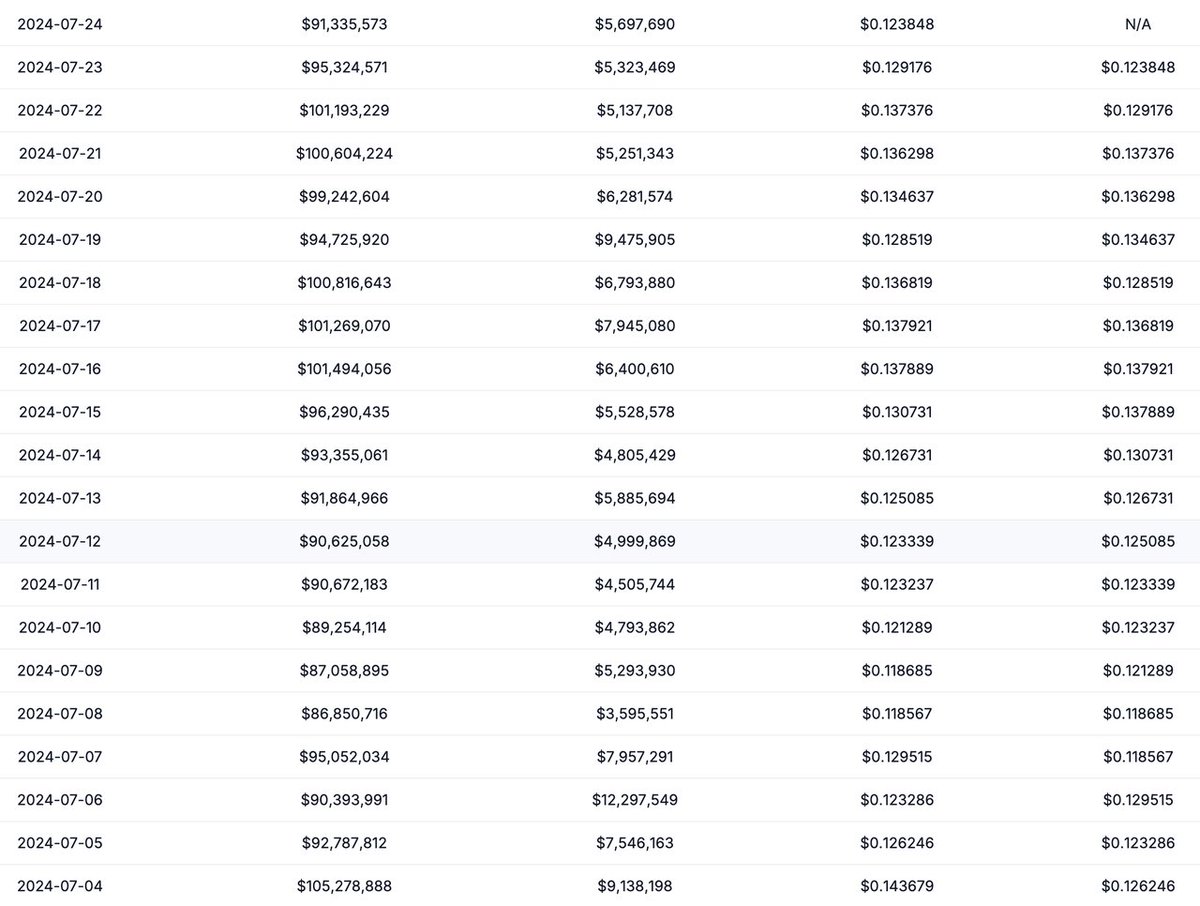
PHA Daily Trading Volume
Data source: https://www.coingecko.com/en/coins/phala-network/historical_data
The daily trading volume of PHA is $5.66 million, and its circulating market cap is about $126.54 million, although the turnover rate is only 4.47%, which is on the low side, but this is more due to the current overall market environment being relatively depressed, and the recent impact of the Mtgox event has caused users to be mostly in a wait-and-see state.
Top 10 Token Holder Addresses
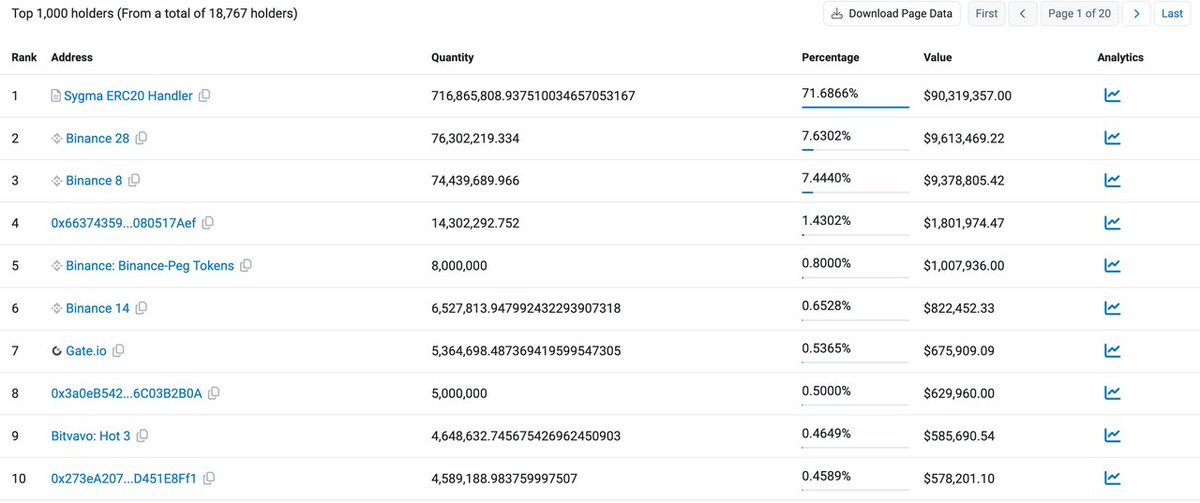
Top 10 PHA Holder Addresses
Data source: https://etherscan.io/token/0x6c5bA91642F10282b576d91922Ae6448C9d52f4E#balances
The figure shows that the top 10 PHA holder addresses hold a total of 92.19%.
PHA Holders
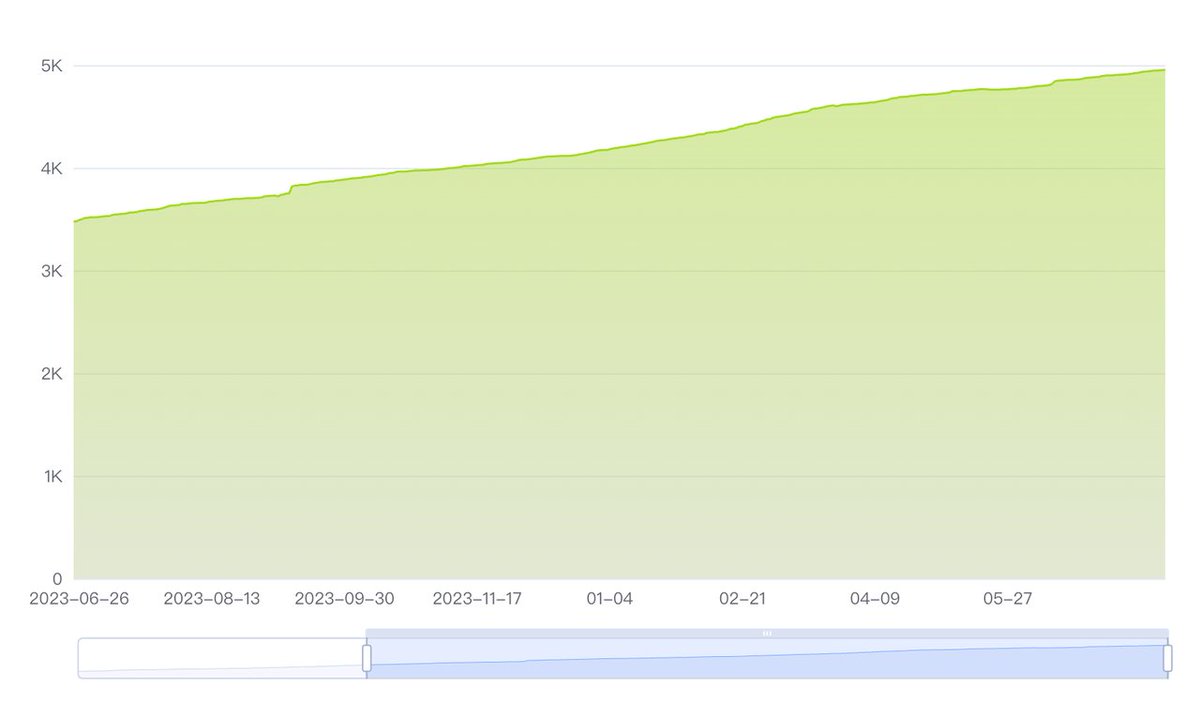
PHA Holders
Data source: https://phala.subscan.io/tools/charts?type=holder
It can be seen that the number of PHA Token holders has been steadily increasing over the past year.
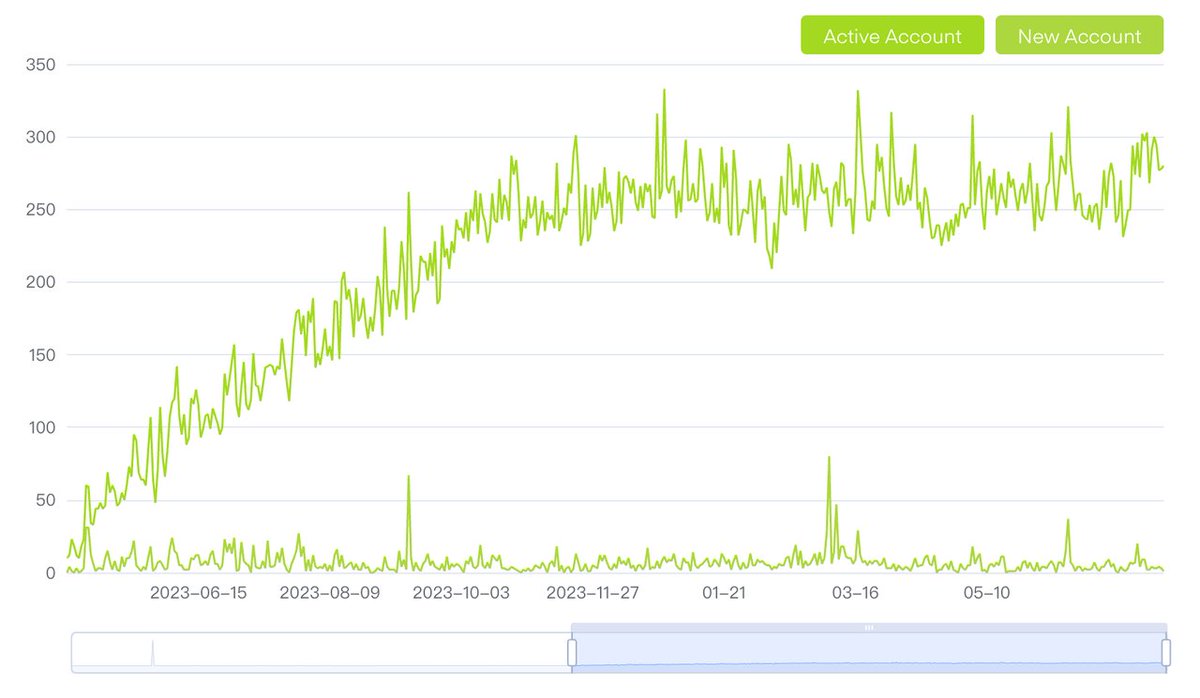
Daily Active Accounts
Daily Active Accounts
Data source: https://phala.subscan.io/tools/charts?type=account
It can be seen that the daily active accounts of Phala Network have been continuously increasing over the past year.
Staking Situation
Actual Circulating Supply of PHA
Data source: https://phala.subscan.io/
From the figure, we can see that the circulating supply of PHA should be 848.27 million, but the actual circulating supply is 738.33 million, so the actual staking amount should be 108.94 million.
Project Risks
Although Phala Network has changed its project's track to the AI track after launching the artificial intelligence proxy contract, which is beneficial to the development of its project and the growth of its Token price, the technical challenges it faces have also increased exponentially. Especially, Phala Network has adopted a relatively complex artificial intelligence proxy contract based on the foundation of privacy computing, and will continue to access new AI Agents in the future, which poses a great challenge to its technical team. Therefore, there will definitely be some system problems in the future, and it remains to be seen how Phala Network's team solves the problems and whether Phala Network's artificial intelligence proxy contract is as powerful as it claims, so there are many uncertain factors at present.
Conclusion
Phala Network has introduced artificial intelligence proxy contracts, making it as easy to run artificial intelligence agents as smart contracts, and managed by smart contracts, realizing real-time management and access control of artificial intelligence agents. Different artificial intelligence agents can freely call each other to build complex applications, and all operations are performed in a trusted execution environment (TEE) to ensure the integrity and privacy of the code. This allows Phala Network to fully utilize the advantages of its previous privacy computing infrastructure and transform it into a Web3 artificial intelligence execution layer. This innovation provides a brand new solution for the security and privacy protection of artificial intelligence applications, and provides strong support for the integration of smart contracts and blockchain technology.
After launching the artificial intelligence proxy contract, Phala Network has positioned the project in the AI track, which is beneficial to the project's development and Token price growth. However, the technical challenges that come with it have also increased exponentially. Especially, Phala Network has adopted a complex artificial intelligence proxy contract based on the foundation of privacy computing, and will continue to access new AI Agents in the future, which poses a huge challenge to the technical team.
In summary, Phala Network's project itself has gained certain advantages in the privacy computing infrastructure track by introducing the trusted execution environment (TEE). And now with the addition of the artificial intelligence proxy contract, if it can proceed as planned in the future, Phala Network will also have certain advantages in the AI track.