By Douglas Bakkum
Source: https://blog.bitbox.swiss/en/does-airgap-make-bitcoin-hardware-wallets-more-secure/

Since the release of the BitBox02, we've received numerous requests for support for Airgap operation: using the hardware signer directly without plugging it into a computer or phone. While Airgap devices have received significant attention recently, we wanted to delve deeper into their actual security benefits, leading us to conduct a detailed investigation of the topic. We concluded that Airgap communication offers minimal security benefits for hardware signers and may even degrade the user experience. We used publicly available vulnerabilities to verify Airgap's security promises. This article documents our findings.
What is Airgap?
Airgap is a security measure that physically isolates a device from untrusted networks (such as the internet) by removing all network interfaces. For example, airgap computers are often used in safety-critical infrastructure. While this principle is powerful in itself, in practice, data often needs to be exchanged with networked devices. This data, which crosses the "airgap," is typically transferred via USB flash drives. The security of an airgap system relies entirely on the data being transmitted being non-malicious and not being tampered with during transmission. As the famous Stuxnet worm incident demonstrated, without thorough inspection of the data being exchanged, the security benefits of airgap, whether for a nuclear power plant or a cryptocurrency hardware signer, are illusory.
In the context of cryptocurrency wallets, the term "airgap" refers to the physical separation and lack of direct connection between a signing device, such as a hardware signer (which protects private keys), and a potentially insecure internet-connected computer (which creates transactions to be signed and broadcasts signed transactions). Any communication between the two requires crossing the "airgap," typically by physically exchanging SD cards or scanning QR codes. Crucially, this communication is unavoidable. This communication includes not only the transaction data mentioned above, but also larger amounts of data such as those used to update the hardware signer's firmware or the wallet's own information (such as the public key (or address) for receiving coins).
Unlike plugging a hardware signer directly into your computer, the Airgap hardware signer works with software installed on your computer that supports PSBT (Partially Signed Bitcoin Transactions). You can create an unsigned transaction in the app and then encode it as a QR code for the hardware signer to scan, or save the transaction as a file and then use a microSD card for the hardware signer to read.
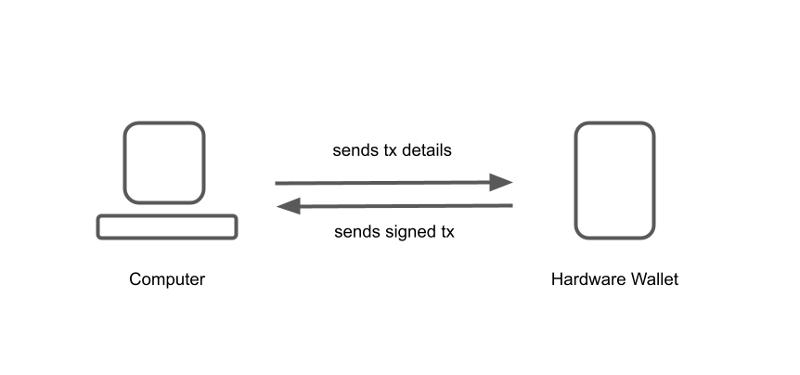
After the hardware signer signs a transaction with its private key, it returns the signed transaction to the computer by displaying a QR code on the screen or writing the signed transaction to a microSD card. The companion application on the computer imports the signed transaction and then broadcasts it to the network.
Additional Note: While this article focuses on the security risks and vulnerabilities of hardware signers, it's important to emphasize that hardware signers are still widely considered the most secure way to transact with cryptocurrencies. This is because the private keys that access and unlock the coins are always securely stored within the hardware, never leaving the hardware signer. In contrast, software wallets are more vulnerable to malware and theft, while storing coins on exchanges carries its own set of risks . Furthermore, converting old desktop computers into dedicated airgap devices is sometimes recommended, but this is difficult to guarantee security and is susceptible to various attacks .
The myth of Airgap's impenetrable security
The lack of a physical connection between the two devices makes it easier for people to perceive the connection as “secure.” At the same time, plugging a hardware signature device into a computer like a USB drive might make it feel less secure.

However, we concluded that this perceived security benefit, and the way it was promoted as a “silver bullet,” far exceeded its actual reality, which could lead to a false sense of security.
Here are three main reasons why airgap doesn't improve security much in practice:
1. Communication is still going on
While there's no physical connection like a USB cable, information still needs to be exchanged between the hardware signer and the host computer. The primary difference between a wired connection and an AirGap connection is bandwidth. A QR code transfers far less data than a USB connection. However, we've found that bandwidth impacts user experience, not security.
Because Bitcoin transactions themselves are small in size, any communication channel is sufficient to transmit them. As demonstrated by the Stuxnet incident, no communication channel inherently prevents the sending and receiving of data other than the intended data (in this case, Bitcoin transactions). This data could still be malicious. Therefore, hardware signers still have the responsibility to thoroughly inspect and sanitize all received data.
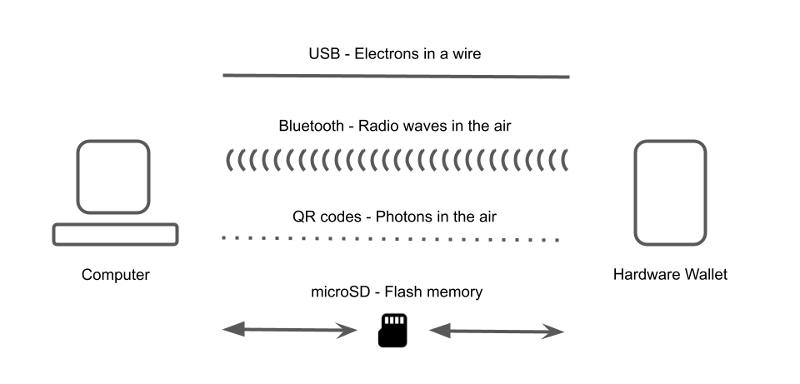
If the hardware signer receives tampered data and doesn't properly verify it, it doesn't matter if it's airgap or not. Once an attacker finds an exploitable vulnerability, whether it's through a malicious QR code, a transaction file, or data transmitted via USB connection or Bluetooth, it can be used to launch an attack.
Airgap transmission is essentially just another communication channel, albeit one that requires more manual user interaction. Each channel presents its own attack vectors, and whenever information is exchanged, the hardware signer must diligently sanitize the data. Specifically, the threat model for the hardware signer must assume that the computer or phone it communicates with is compromised. Therefore, any information other than what the hardware signer itself displays cannot be trusted.
2. Communications can still be tampered with
A significant attack vector is malware that can tamper with communications without being detected. For example, it could change the receiving or change address, or replace a co-signer in a multi-sig setup. Again, the hardware signer's firmware should be able to catch such behavior, but AirGap itself offers no help:
- QR codes can be maliciously tampered with at multiple levels, including through upstream libraries that control the camera image or QR code rendering, backdoors implanted in the camera firmware, or through malware running on the host computer.
- Through the microSD card, other programs can secretly monitor its contents, modify PSBT files, or write additional data to the card without the user's knowledge. The specific access rights depend on the operating system used.
- USB communication itself also does not mitigate this attack vector.
A common method for detecting and preventing data tampering is to encrypt all communications between the companion app running on the computer and the firmware (the BitBox02 implements this using the Noise Protocol Framework ). Even so, the communication channel isn't completely secure if the computer running the app is compromised (which is why you should always verify transaction details on the hardware signer's built-in screen), but encrypting the communication makes it much more difficult for an attacker to eavesdrop or tamper with the information.
3. Airgap isn't more transparent in daily use
Another common promotional point for the Airgap Signer is that data shared between devices is more transparent and verifiable than using a USB connection.
“This stronger security model ensures you know exactly what information you are receiving” – Foundation Devices
“By using QR code transmission, we eliminate the potential risk of malware intrusion and provide a level of transparency that is not possible with Bluetooth or USB.” – Keystone
“Our cold wallets only use QR codes to transmit data, and the QR code format is controllable, verifiable and transparent.” – Ellipal
To verify this, let’s look at a simple Bitcoin transaction created using the Sparrow wallet: it contains one input, one recipient, and a change address.
- Sample Bitcoin Transaction -
The wallet supports exporting unsigned transactions in two ways:
- PSBT files , stored in binary format, cannot be read directly. You cannot open them and inspect their contents. The only way to do this is to load them into a Bitcoin wallet. Therefore, the wallet is still responsible for sanitizing the data.
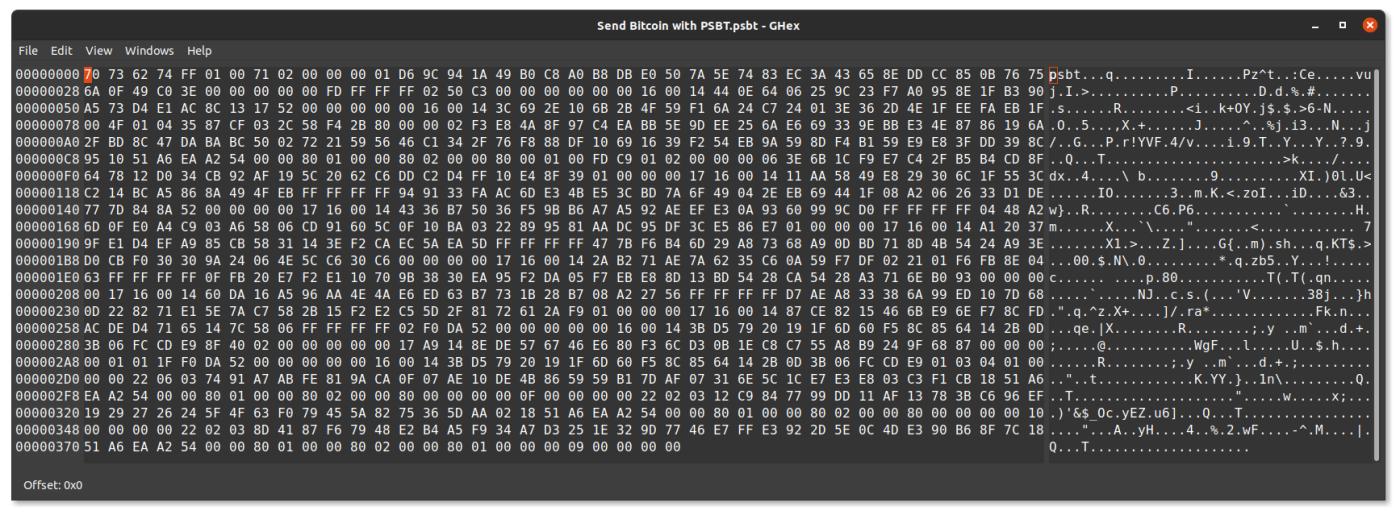
- Binary contents of PSBT files -
- QR codes present the same information in a visual format. Because transaction data is too large to be displayed using a single QR code, dynamic QR codes are used. Similarly, the information contained within cannot be read directly and requires verification through another wallet.
- Dynamic QR code containing binary transaction data -
If you try to read the data with a regular QR code scanner, you’ll only see a bunch of unreadable gibberish:

- Part of the QR code content read by a common QR code scanner -
Whether using a PSBT file or a QR code, the data can be verified not only on a compatible hardware signer, but also using other wallets. However, in our opinion, whether this approach actually provides any additional security benefits is questionable (since sanitizing data and allowing you to verify it on the built-in screen is the primary function of a hardware wallet), and it is unrealistic to expect users to do this frequently.
Other considerations
Each communication channel has its advantages and disadvantages. Here are some additional considerations for hardware signer communication methods:
- The microSD card itself contains a tiny computer (a.k.a. a microcontroller) running firmware that can be hacked . If you need to plug a tiny computer into a hardware signer to use it, is that really an airgap?
- External library dependencies should be minimized to reduce the attack surface. This applies not only to USB drivers, but also to drivers for microSD card readers and built-in cameras.
- The QR code on your screen or the text information in the application may be leaked through peeping or surveillance camera shooting, thus affecting your privacy.
- Wireless communication modes such as Bluetooth and NFC broadcast identification information, which may cause privacy issues.
Like most things in life, there is no “single best choice.”
Reality Check: Can Airgap protect you from the 2020 hardware signer vulnerability?
Let's review all known Bitcoin-only vulnerabilities from the beginning of 2020. The purpose of this list is simple: to check if airgap communication can prevent these vulnerabilities.
Overall, none of the vulnerabilities we studied relied on the data transmission layer—the channel through which information is exchanged between the hardware signer and the computer or phone. This means that all of these vulnerabilities are exploitable regardless of whether the device is AirGap enabled or not.
If you're interested in the vulnerabilities themselves, we've provided links to more detailed information so you can understand the full picture. None of the following vulnerabilities have been proven to have actual exploits, and some are more theoretical or difficult to exploit for other reasons.
Supply Chain Vulnerabilities: Attacker-Controlled Firmware (Coldcard, March 2020)
This vulnerability allows an attacker to flash malicious firmware and reset the device to a compromised "factory" state. For detailed analysis, see: Report , Manufacturer Announcement
Airgap doesn't work: this is a physical attack vector
OP_RETURN is treated as a change output (Trezor, March 2020)
This vulnerability allows skipping user confirmation, potentially affecting Layer 2 protocols (such as Omni layer)
For detailed analysis, see: Manufacturer Announcement
Airgap doesn't work: This is a transaction verification issue
Malicious Change in Mixed Transactions (Trezor, March 2020)
Change may be sent to a 1-of-2 multi-signature address partially controlled by the attacker,
For detailed analysis, see: Shift Crypto Report , Second Report (March 2020), and Manufacturer Announcement
Airgap doesn't work: This is a transaction verification issue
Insufficient field length checks (Trezor, March 2020)
The vulnerability allows the
prevhashfield in a transaction to exceed the expected 32 bytes, potentially including a hidden output that sends funds to the attacker.For detailed analysis, see: Manufacturer Announcement
Airgap doesn't work: This is a transaction verification issue
Inconsistent transaction input cleaning (Trezor, March 2020)
The vulnerability allows transactions containing single-signature inputs and 1-of-2 multi-signature outputs (partially controlled by the attacker) to be accepted without user verification.
For detailed analysis, see: Manufacturer Announcement
Airgap doesn't work: This is a transaction verification issue
Generating massive fees via two SegWit transactions (all vendors, March 2020)
A malicious wallet could trick a user into signing the same Bitcoin transaction twice, for example by faking an error after the initial signing, forcing the user to try again, and then creating a transaction with a hefty miner fee. The attacker could then collect these fees by colluding with the miners.
For detailed analysis, see: Shift Crypto , Ledger , Trezor , and CoinkiteAirgap doesn't work: This is a general validation design issue with BIP-143
JTAG/SWD interfaces are enabled on unprotected processors (Ledger, June 2020)
The debug interface of the Ledger Nano X's microcontroller unit (MCU) is enabled. This could allow a supply chain attack, but does not allow access to internal keys.
For detailed analysis, see: Report , Manufacturer Announcement
Airgap doesn't work: this is a physical attack vector
Bitcoin Fork/ Altcoin Cross-Account Signatures (Ledger/Trezor/Keepkey, August 2020)
A user could be tricked into signing a Bitcoin transaction, only to have details of a testnet or Altcoin displayed on their device screen.
For detailed analysis, see: Report , Ledger , TrezorAirgap doesn't work: This is a transaction verification issue
Bitcoin Mainnet/Testnet Cross-Account Signature (Coldcard, August 2020)
A user could be tricked into signing a Bitcoin mainnet transaction, only to have their device screen display details from a testnet.
For detailed analysis, see: Shift Crypto’s report and manufacturer announcementAirgap doesn't work: This is a transaction verification issue
Ransomware attack targeting passphrase processing (Trezor/Keepkey, August 2020)
A wallet created by a user with a passphrase on a host computer can be exploited by malware to use a different passphrase on a hardware signer, thereby ransoming all future funds transferred into the wallet.
For detailed analysis, see: Report , Manufacturer Announcement 1 , Manufacturer Announcement 2
Airgap does not work: regardless of the communication method used, the passphrase must be entered or verified directly on the device
Remote Multi-Signature Theft Attack (Coldcard, November 2020)
The vulnerability stems from the device not checking whether it is part of a newly created multi-sig wallet, allowing an attacker to trick a user into creating a multi-sig wallet controlled by the attacker.
For detailed analysis, see: Report , Manufacturer Announcement 1 , Manufacturer Announcement 2
This is a common wallet verification issue where data from external collaborators or third-party participants could be malicious:
- If you set up your multisig wallet entirely on your own, you can mitigate this vulnerability by simply passing the microSD card between multiple hardware signers. This also works with devices connected via QR code or USB (although no one has implemented this yet).
- If the multisig wallet is set up by an external collaborator or a malicious co-signer, even if the device is fully airgap, it will be useless.
SCP Length Extension Attack (Ledger, May 2021)
The vulnerability allows an attacker to decrypt a block of application data and firmware updates without causing any security impact (because the data is not confidential and is publicly available).
For detailed analysis, see: Manufacturer Announcement
Airgap doesn't work: when downloading new firmware, data can be read anywhere
These are all publicly disclosed hardware signer-related vulnerabilities we are aware of. Sources (also covers older vulnerabilities): Shift Crypto , Ledger , Trezor , Hardware Signer Vulnerability List
The most relevant example we could find of earlier attacks was the " Potential Data Leakage When Using U2F (Universal Secondary Authentication) " reported in 2018. However, this example was also not about the USB transport layer, but rather about how U2F data is encoded (i.e., parsed) before being transmitted over USB.
Besides invasive attacks that require physical hijacking of the hardware signer, vulnerabilities typically occur at the logical layer, where the hardware signer fails to properly verify or parse transaction details.
Additionally, it's important to realize that AirGap cannot protect you from malicious firmware. If the hardware signer itself is compromised, there are countless ways to leak the private key (e.g., via Bitcoin signing ).
Airgap still has its place
Airgap Integration
Communication methods like QR codes or microSD cards can in some cases be used for other purposes, such as convenience and user experience, depending on the devices involved:
- When communicating using a QR code or microSD card via the PSBT standard, third-party apps can more easily integrate and mix and match with hardware signers.
- QR codes are a convenient method of communication that works well with common hardware that can easily connect to camera accessories, such as Seedsigner or Spectre DIY .
- QR codes are also helpful when communicating with devices that restrict USB connectivity, such as iPhones.
It’s important to note that while “PSBT” is sometimes used synonymously with “airgap,” it’s actually another standard for moving unsigned transactions to another device for signing, unrelated to any specific communication method. This enables interoperability between multiple devices and software wallets, which is a key reason to support PSBT nativeization.
"Zero Communication" Security
From a security perspective, we've found the only use of airgap to be recommendable is when using a hardware signer in a "full" airgap scenario, with no external communication. Importantly, this doesn't refer to "airgap communication" as commonly used in the hardware signer world, but rather to no communication with untrusted devices at all, or "zero communication." While this is obvious in theory, the "remote multi-signature theft attack" mentioned above provides a practical example. However, "zero communication" isn't always feasible: to prepare and ultimately broadcast a transaction, the signer requires external data about how many coins it currently owns and where to send them.
Zero-communication operation reduces the attack surface for operations that require no external information, such as creating or recovering wallet seed phrase, generating receiving addresses, naming wallets, enabling/disabling optional passphrases, and more. Of course, zero-communication operation can be implemented on any hardware signer, even those not advertised as airgap. For example, when a hardware signer is connected to a power bank, its screen can display the receiving address.
Airgap communication can limit potential attacks that require continuous communication with the hardware signer, such as those that continuously probe the device. However, the hardware signer is specialized and has a strict communication protocol that aborts any connection that violates the protocol. Implementing a strict communication protocol is straightforward compared to other security challenges, and we are not aware of any successful probing attacks of this nature.
Ease of use is the cornerstone of security

- Transaction Signature Steps -
Using an Airgap hardware signer significantly sacrifices ease of use. Sending a PSBT transaction via Airgap communication requires more steps, keystrokes, concentration, and time.

- Transaction signing steps in Airgap mode -
Users become part of the communication channel, essentially acting as middlemen, but with no good way to audit what data they are transferring. This increases operational friction without providing any clear security benefits.
An AirGap device needs to have most of its user interface integrated into the firmware. All but the most basic operations are more easily accomplished using an external desktop or mobile app connected to the hardware signer.
That’s why we not only produce the hardware, but also developed the beginner-friendly BitBoxApp to make using the BitBox02 very simple. Through strict transaction verification rules, strict USB communication protocols and end-to-end encryption, the BitBox02 ensures the security of the communication channel while providing a simpler user experience.
Furthermore, future implementations of important security or privacy protocols may further complicate the Airgap user experience. For example, the " anti-klepto " protocol, designed to prevent the leakage of user private keys and first implemented in the BitBox02, requires a new round of information exchange between the hardware signer and the computer to prevent malicious tampering with transaction signatures. If an Airgap device implements this security mechanism, sending a transaction will require users to perform an additional round of manual QR code scanning.
in conclusion
So, what does this mean for the design decisions of hardware signer manufacturers and the purchasing decisions of users? In our opinion, the choice of communication mode is more about user experience and application integration than security factors, at least from a technical perspective.
Of course, if a market "feels" that one communication method is better than others, then it makes business sense to satisfy that need. However, while marketing claims are bound to be exaggerated, this can mislead users and ultimately damage the reputation of the entire industry. Therefore, it is in everyone's best interest to monitor each other and ensure the truthfulness of marketing claims.
A common saying is that "complexity is the enemy of security." In other words, simplifying the user experience as much as possible is inherently a security advantage because it reduces the chances of user error. When we designed the BitBox02 two years ago, we believed that a USB port that could be plugged directly into new computers and phones would provide the best user experience without sacrificing security. Our research on airgap communication in this article demonstrates that our decision has stood the test of time.
Another common saying is that there's a "trade-off between security and ease of use." But we believe this is a false dichotomy, and the purpose of hardware signers is to make security simple. Our advanced security model is highly recognized by experts, and it allows users to not worry about their assets being stolen. The way we designed the BitBox02 and BitBoxApp is to hide the complexity behind the scenes and make it easier for users to operate. We do provide advanced feature options , which may not be needed by the vast majority of users at the beginning, but their value will gradually become apparent as you embark on your journey to financial independence. For example, directly connecting to your own Bitcoin full node, using the Tor network for better privacy protection, Coin Control, etc.
This article challenges conventional wisdom in the industry, and we understand it may be seen as controversial. We're very open to different voices and will continue to explore this topic in the future. We look forward to hearing your thoughts .
Frequently Asked Questions
What does airgap mean in the context of a hardware signer?
Airgap is a security measure that physically isolates a device from untrusted networks, such as the internet. In cryptocurrency wallets, it means there's no direct connection between the signing device and the internet-connected computer; communication typically occurs via a QR code or SD card.
Can Airgap make hardware signers more secure?
Although airgap can provide some security advantages, this paper concludes that airgap communication provides minimal security improvements to hardware signers and may even degrade the user experience.
Can Airgap prevent all vulnerabilities?
No, many vulnerabilities exploit the hardware signer logic layer, where the device fails to properly verify or parse transaction details. These vulnerabilities can exist regardless of whether the device is airgap enabled or not.
Are there any advantages to using airgap?
Airgap does have its uses in terms of user experience and application integration. For example, using QR codes for interacting with devices equipped with camera accessories is convenient, while the PSBT standard enables interoperability between multiple devices and software wallets.
What are the key points about airgap and hardware signer?
Choosing a communication mode for a hardware signer is more about user experience and application integration than security. The key is to ensure that the selected method does not sacrifice security while still providing a good user experience.








