North Korean (DPRK) IT workers continue to infiltrate IT companies globally to earn income, often in cryptocurrency, used to finance North Korea’s production of weapons of mass destruction and ballistic missiles. Over the past few years, regulatory actions by the U.S. Treasury’s Office of Foreign Assets Control (OFAC), South Korea’s Ministry of Foreign Affairs (MOFA), and others have targeted individuals and entities enabling these schemes with sanctions, often including cryptocurrency addresses as identifiers.
Chainalysis closely tracks the inclusion of crypto addresses in sanctions designations targeting DPRK IT worker schemes, as well as open-source information on this threat. We closely monitor how the DPRK is using cryptocurrency to generate revenue, move and consolidate funds, and launder proceeds by using fictitious accounts at mainstream exchanges or by leveraging likely unregulated over-the-counter (OTC) traders.
Recent enforcement actions include OFAC sanctions in August targeting a Russian national who facilitated payments to DPRK-based Chinyong Information Technology Cooperation Company (Chinyong), also known as Jinyong IT Cooperation Company, which was sanctioned by OFAC and South Korea’s Ministry of Foreign Affairs (MOFA) in May 2023 for employing DPRK IT workers abroad.
Earlier in 2023, OFAC had sanctioned and included cryptocurrency addresses for Sim Hyon Sop (Sim), a representative of the OFAC-designated Korea Kwangson Banking Corp (KKBC), who has received tens of millions of dollars in virtual currency, some of which came from DPRK IT worker revenues. OTC traders like OFAC SDN Lu Huaying (Lu), a Chinese national based in the UAE, have also been targeted with sanctions for laundering DPRK IT worker funds on behalf of the North Korean regime.
These operations highlight a complex network, heavily reliant on cryptocurrency to generate and launder revenue and as a result, are also exposed to opportunities for law enforcement disruption. As highlighted by the U.S. Department of Justice’s (DOJ) latest forfeiture action on DPRK-controlled funds, advanced blockchain analytics offers both unique insights and a real opportunity to flag and disrupt fraudulent IT worker laundering networks.
This blog will explore the operations, networks, and mechanisms by which DPRK IT workers facilitate their revenue generation and laundering processes. By understanding these networks, law enforcement, regulators, and the private industry can be better equipped to detect IT worker activity on-chain and disrupt flows to the DPRK’s weapons of mass destruction (WMD) program.
Generating revenue in cryptocurrency
DPRK IT workers are usually deployed overseas through facilitators like Chinyong, where they apply for roles in IT companies globally. They succeed by leveraging different obfuscation techniques, including virtual private networks (VPNs); fraudulent or stolen identity documents; and technology, such as artificial intelligence (AI) voice and face software, to conceal their location and identity.
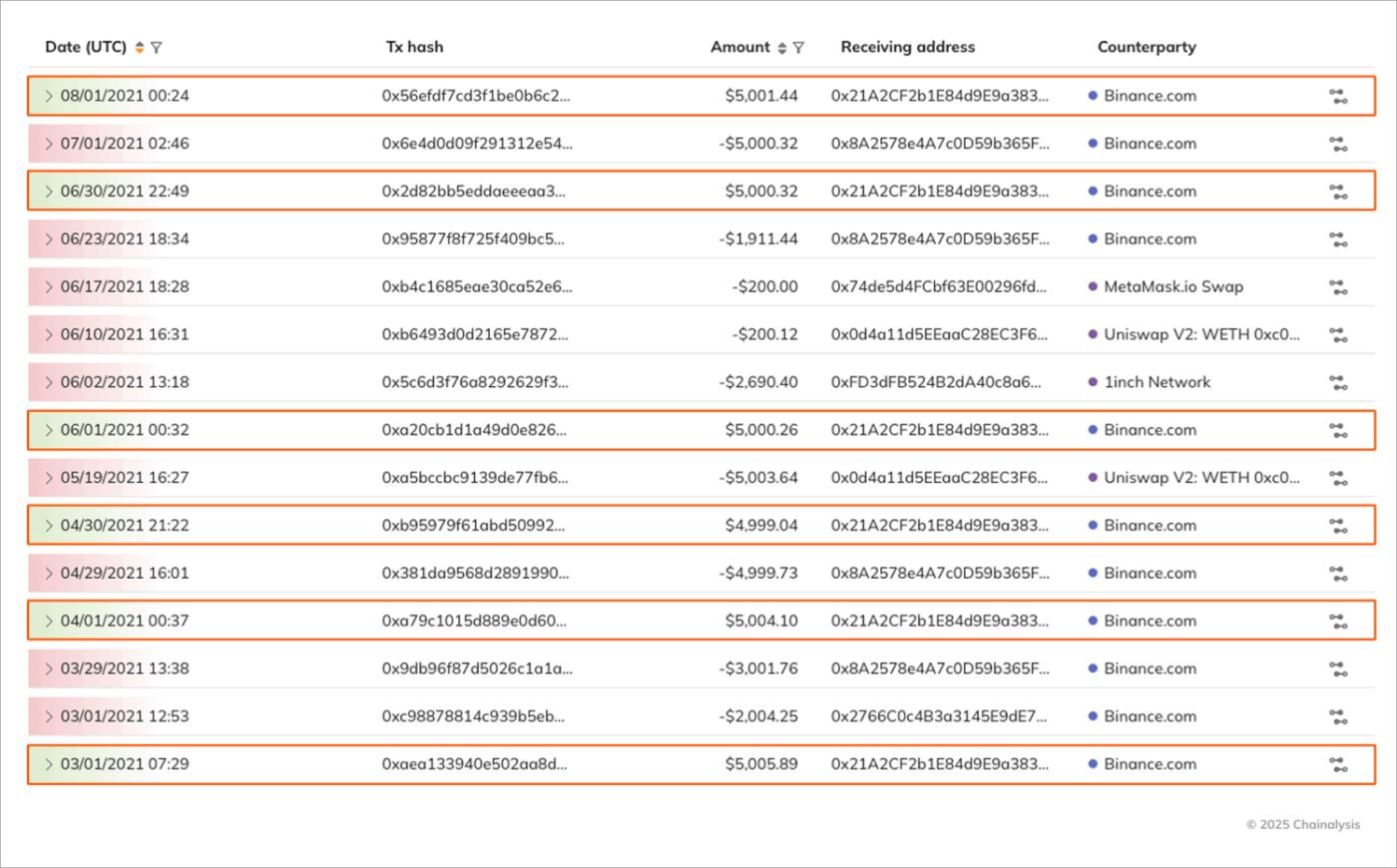
Once hired, DPRK IT workers request payment in stablecoins, likely due to their consistent value, as well as their popularity with OTC traders who can facilitate the off-ramp from cryptocurrency to fiat. From a review of the on-chain activity associated with DPRK IT worker payment addresses, these wallets appear to receive regular payments of consistent amounts, indicative of a salary payment. For example, this DPRK IT worker was receiving payments of roughly $5,000 on a nearly monthly basis:
Obfuscating revenue through blockchain technology
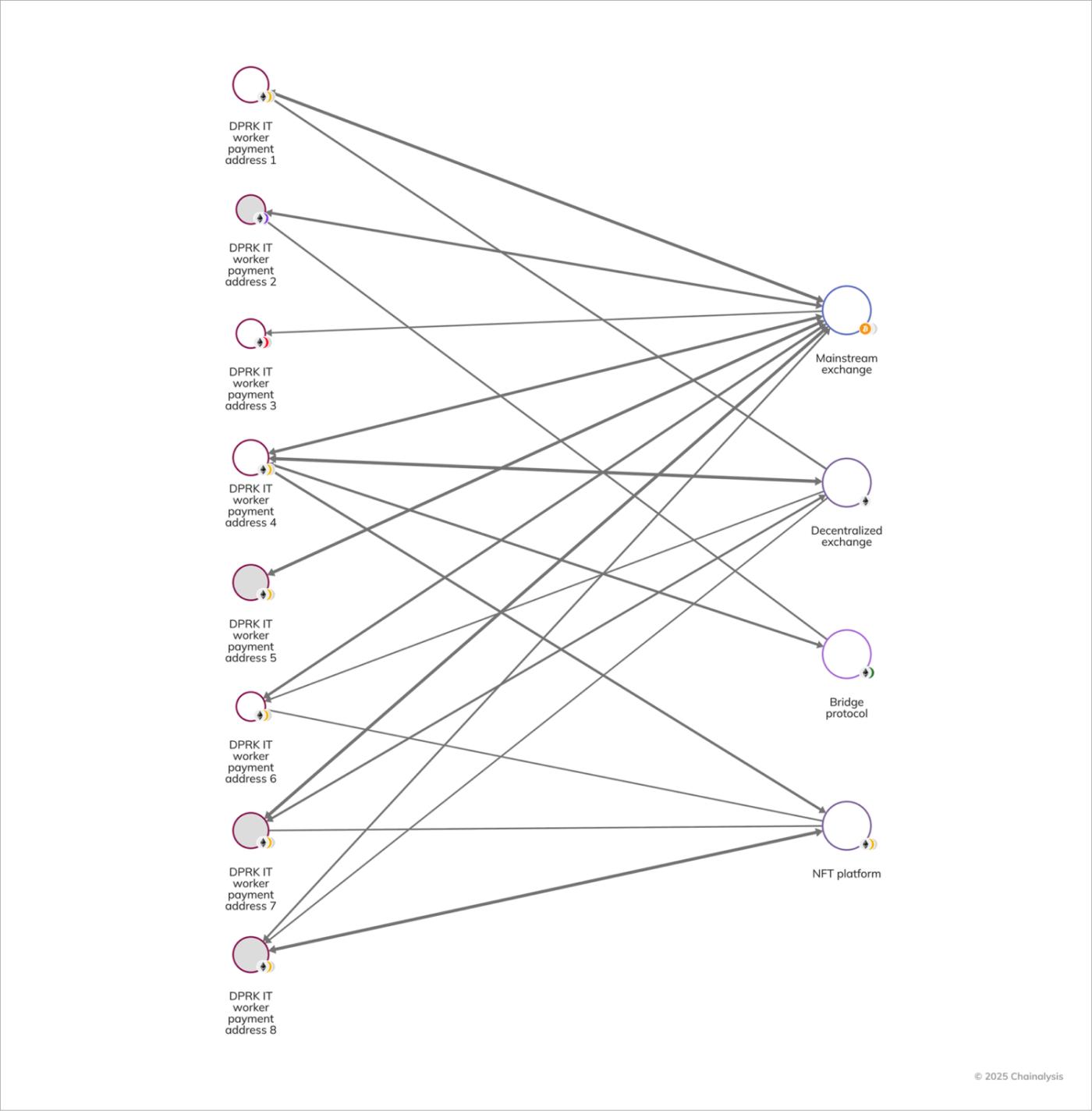
Once their salaries are paid, DPRK IT workers transfer cryptocurrency through a variety of different money laundering techniques. One of the ways in which IT workers, as well as their money laundering counterparts, break the link between source and destination of funds on-chain, is through chain-hopping and/or token swapping. They leverage smart contracts such as decentralized exchanges and bridge protocols to complicate the tracing of funds.
As shown in the Chainalysis Reactor graph below, we can see the use of decentralized protocols and bridges, as well as mainstream exchanges, all of which are leveraged to obfuscate the flow of funds.
DPRK IT workers also rely on intermediaries to facilitate the laundering process and ultimately send funds to North Korea. As laid out in the DOJ forfeiture action on DPRK-controlled funds, IT worker payment funds are laundered by way of consolidation. They are commingled with other proceeds of crime and other DPRK IT workers, through the process of layering before they are funneled to representatives of the regime who use false identity documents to open accounts at mainstream exchanges.
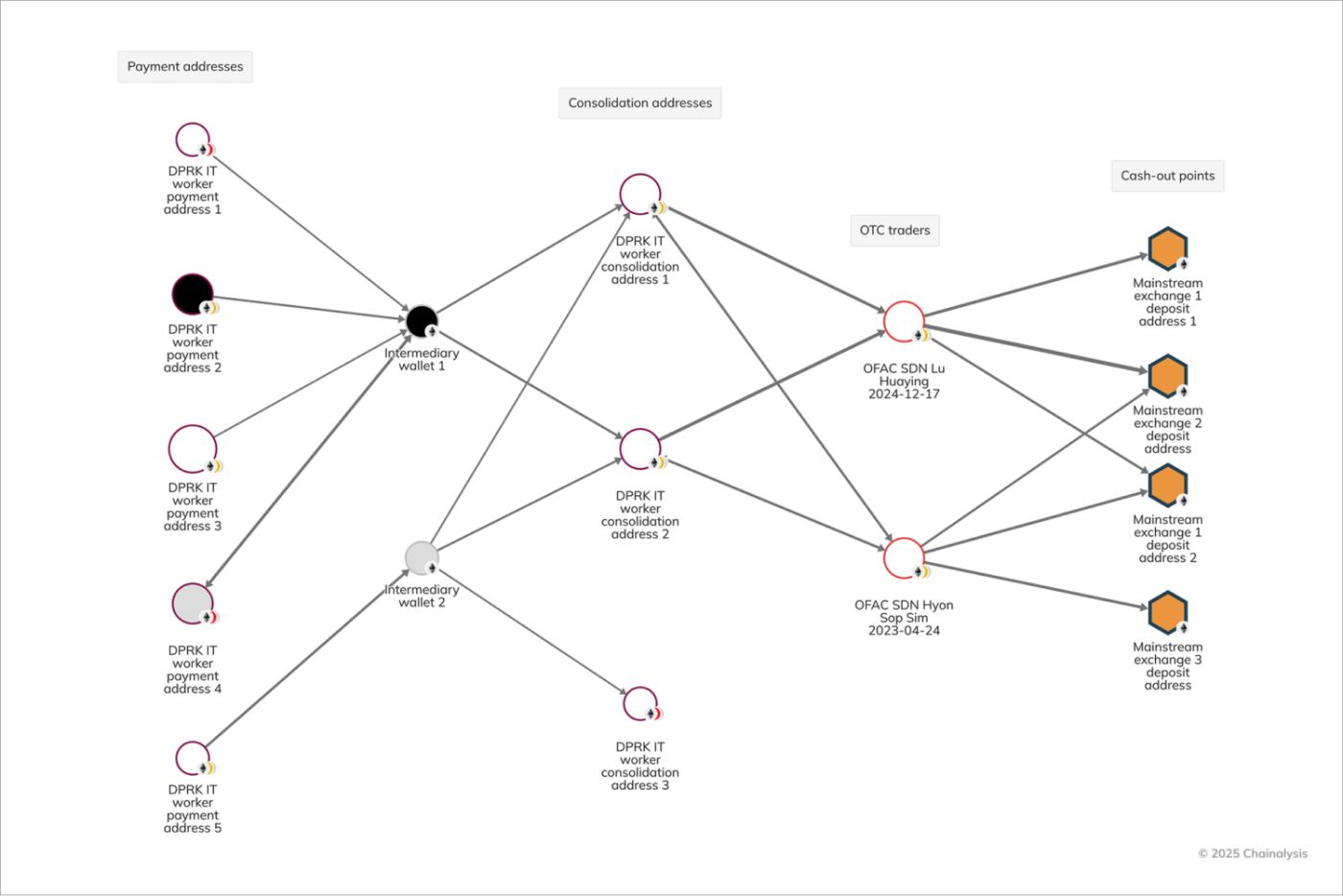
While DPRK launderers have been cited as using false identity documents to open accounts at mainstream exchanges, actors operating in other jurisdictions have used their true identities to open accounts. According to the DOJ forfeiture action, Sim opened accounts at a mainstream exchange using false Russian identity documents, whereas Lu used his own name and UAE residency card to open an account at the now-defunct exchange FTX.

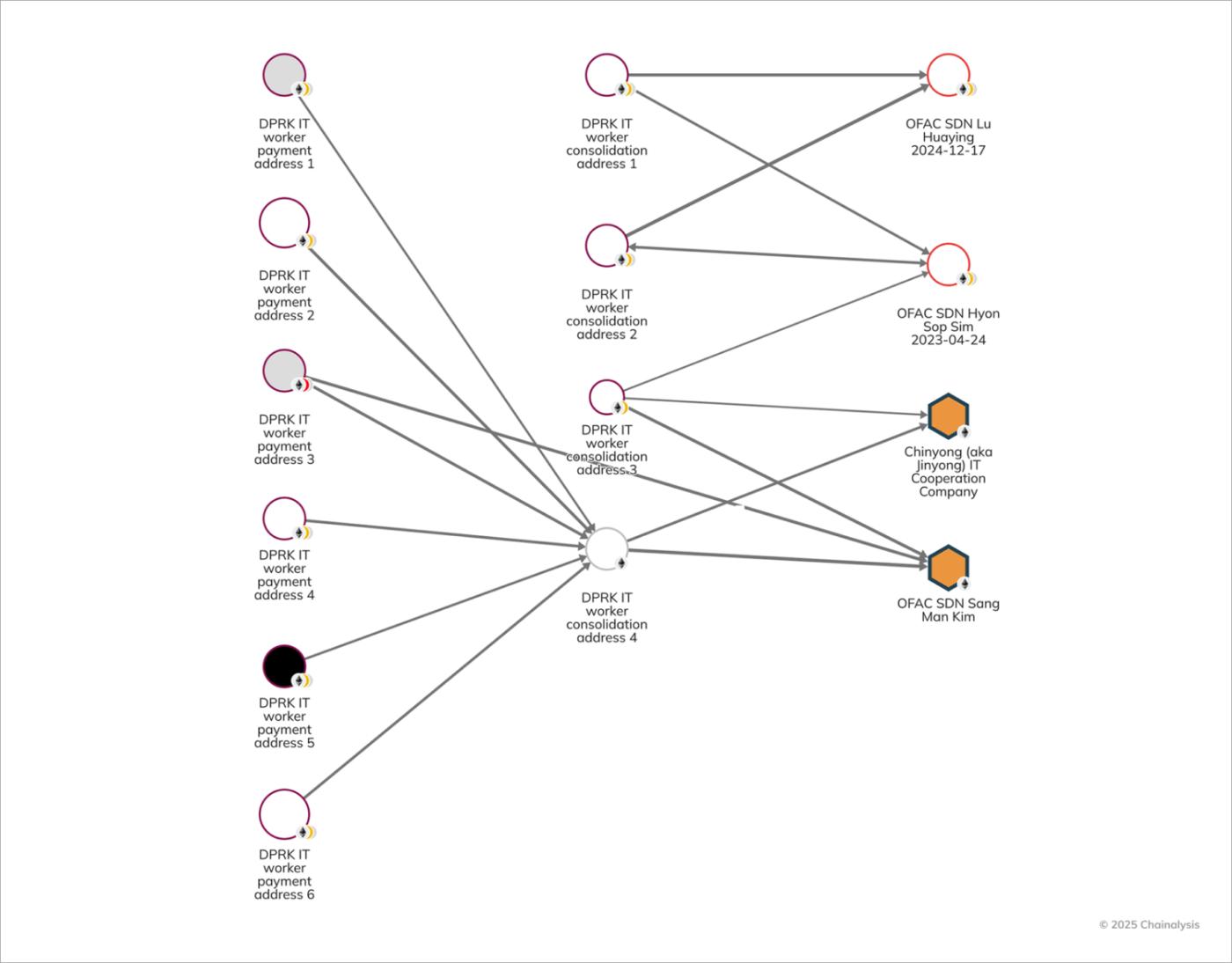
The forfeiture action also flags how DPRK IT worker funds have been funnelled to Kim Sang Man (KIM), a North Korean national and representative of Chinyong; to Sim Hyon Sop (SIM), employed by KKBC, which is a subsidiary of North Korea’s Foreign Trade Bank (FTB); and to OFAC SDN Lu, a Chinese national and OTC trader who was sanctioned in December 2024 for using a UAE-based front company to funnel illicit proceeds to the Pyongyang.
The following Reactor graph shows how DPRK IT workers’ funds were transferred to accounts controlled by KIM at mainstream exchanges, as well as to unhosted wallets operated by SIM and Lu.
Off-ramping revenue to fiat
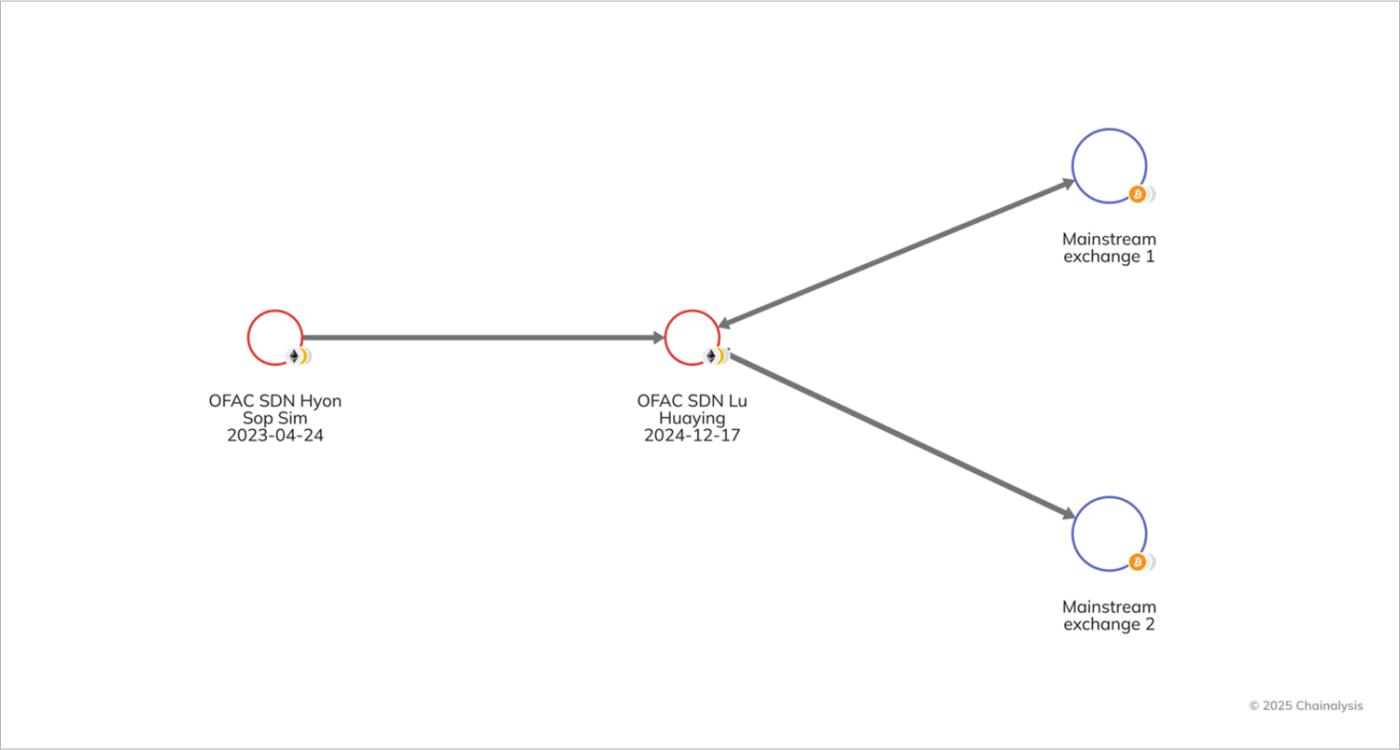
Once DPRK IT workers have laundered their revenue on the blockchain, and sent it to the custody of middlemen acting on behalf of the North Korean government, these funds are converted to fiat currency. This is usually carried out through fictitious accounts operated from mainstream exchanges, or via OTC traders. The graph below illustrates how SIM heavily relies on Lu, sanctioned in December 2024 for facilitating money laundering on behalf of the North Korean government.
Lessons learned for targeting crypto-enabled laundering networks
The recent OFAC designations and DOJ forfeiture actions underscore the global focus on DPRK IT worker schemes and the drive to dismantle their financial networks that let them evade international sanctions. From perpetrators to infrastructure and facilitators, these networks remain prime targets for enforcement actions as they continue to leverage the blockchain to finance the North Korean regime.
Advisories issued by the HM Treasury’s Office of Financial Sanctions Implementation (OFSI) and the Federal Bureau of Investigation (FBI)’s Internet Crime Complaint Center on DPRK IT workers highlight red flags for the private sector to monitor and identify these risks. The advisories include: inconsistent identity, location or credentials; anonymizing infrastructure; irregular payment flows; and behaviour that signals concealment. By looking for these on-chain and off-chain indicators, IT industry stakeholders can play a pivotal role in disrupting the financial pipelines that sustain these actors.
Companies should implement specific checks to identify potential DPRK IT worker activity. Key red flags include IP locations that don’t match stated locations, manipulated identification documents, and reluctance to participate in video calls or use of AI-generated profiles. On the financial side, watch for preferences for stablecoin payments, requests to split payments across multiple wallets, and complex third-party payment arrangements. Be particularly alert to candidates offering advanced technical skills at below-market rates. Building these checks into compliance frameworks, along with detailed documentation of contractor interactions, can help organizations avoid unwittingly facilitating North Korea’s sanctions evasion schemes.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.
The post DPRK IT Workers: Inside North Korea’s Crypto Laundering Network appeared first on Chainalysis.








