*This article has been automatically translated. Please refer to the original article for accurate content.
North Korean (DPRK) technology workers continue to infiltrate technology companies around the world and generate revenue, often in cryptocurrency, to fund North Korea's production of weapons of mass destruction and ballistic missiles. Over the past few years, regulatory agencies, including the U.S. Treasury Department's Office of Foreign Assets Control (OFAC) and the South Korean Ministry of Foreign Affairs (MOFA), have imposed sanctions on individuals and organizations that enable these schemes. Sanctions designations often include cryptocurrency addresses as identifiers.
Chainalysis is closely tracking the addition of cryptocurrency addresses to sanctions designations targeting North Korean IT worker schemes, as well as open-source intelligence on this threat. We are monitoring North Korea's use of cryptocurrencies to generate revenue, move and aggregate funds, and launder proceeds through the use of fictitious accounts on mainstream exchanges and potentially unregulated over-the-counter (OTC) brokers.
Recent regulatory enforcement actions include OFAC sanctions in August 2025 targeting Russian nationals who facilitated payments to North Korea's Chinyong Information Technology Cooperation Company (Chinyong, also known as Jinyong IT Cooperation Company). Chinyong was sanctioned by OFAC and the South Korean Ministry of Foreign Affairs in May 2023 for employing North Korean IT workers overseas.
In early 2023, OFAC sanctioned Sim Hyon Sop (Sim), the representative of Korea Kwangson Banking Corp (KKBC), and designated his cryptocurrency address. Sim has received tens of millions of dollars in cryptocurrency, including a portion of the proceeds of North Korean IT workers. His counterpart, Lu Huaying (Lu, a Chinese national residing in the UAE), has also been sanctioned for his involvement in laundering IT worker funds for the North Korean regime.
These activities highlight complex networks that rely heavily on cryptocurrencies to generate and launder revenue, creating opportunities for law enforcement. As the U.S. Department of Justice's (DOJ) latest seizure order demonstrates, advanced blockchain analytics offers unique insights and effective tools to detect and disrupt illicit money-laundering networks operated by IT workers.
This blog describes the networks, mechanisms, and operations used by North Korean IT workers to generate and launder revenue. Understanding these networks can help law enforcement, regulators, and private companies detect on-chain IT worker activity and disrupt the flow of funds to Weapons of Mass Destruction (WMD) programs.
Earning revenue from crypto assets
North Korean IT workers are typically sent overseas through intermediaries such as Chinyong to apply for jobs at IT companies around the world. They use a variety of obfuscation methods to hide their location and identity, including virtual private networks (VPNs), fake or stolen IDs, and AI voice and facial recognition technology.
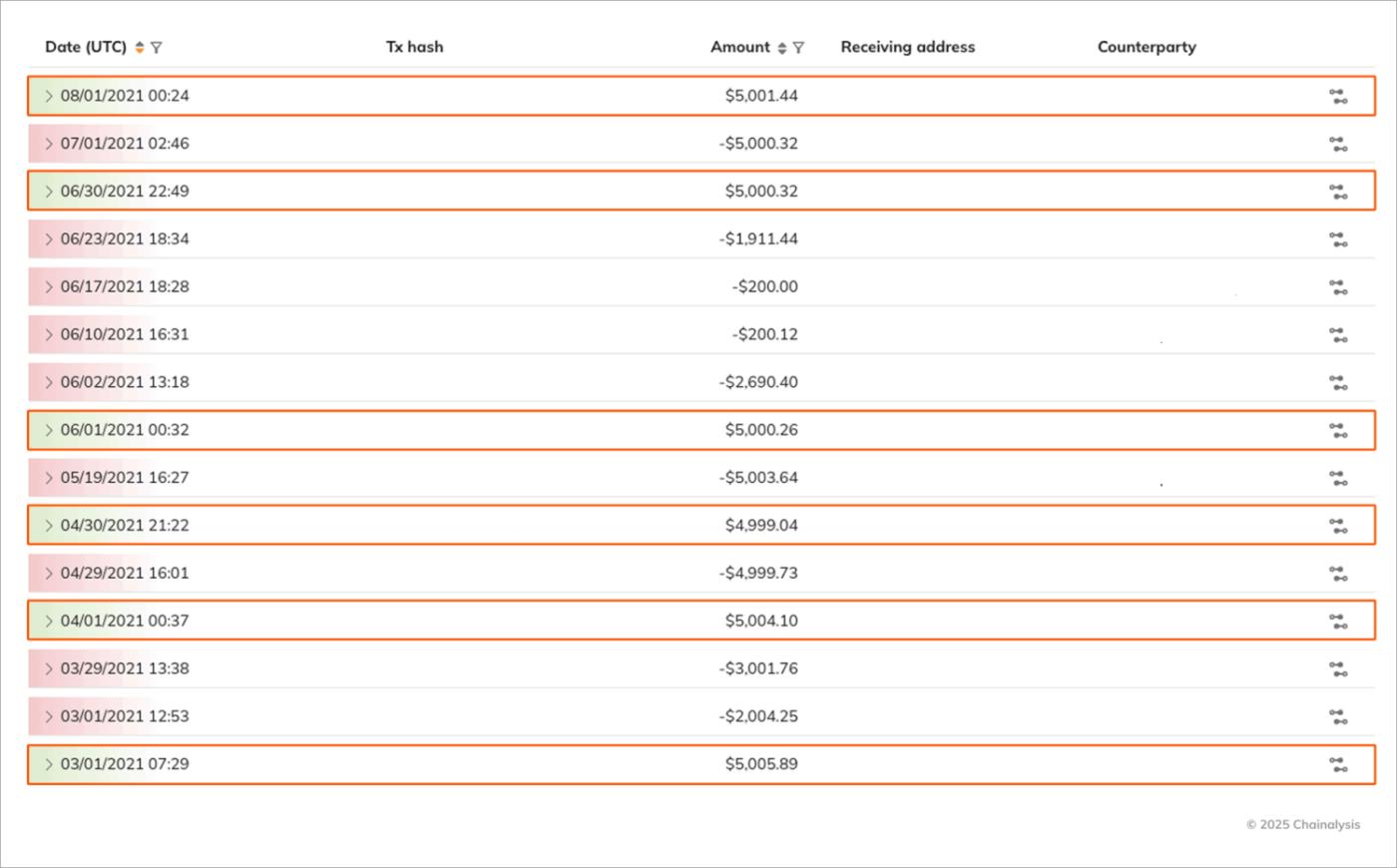
Once hired, they request payment in stablecoins, which have stable value and are popular with over-the-counter (OTC) traders. Examination of on-chain activity associated with the payment addresses of North Korean IT workers reveals that these wallets receive regular payments of approximately $5,000 per month, suggesting they are payroll payments.
Concealing revenues through blockchain technology
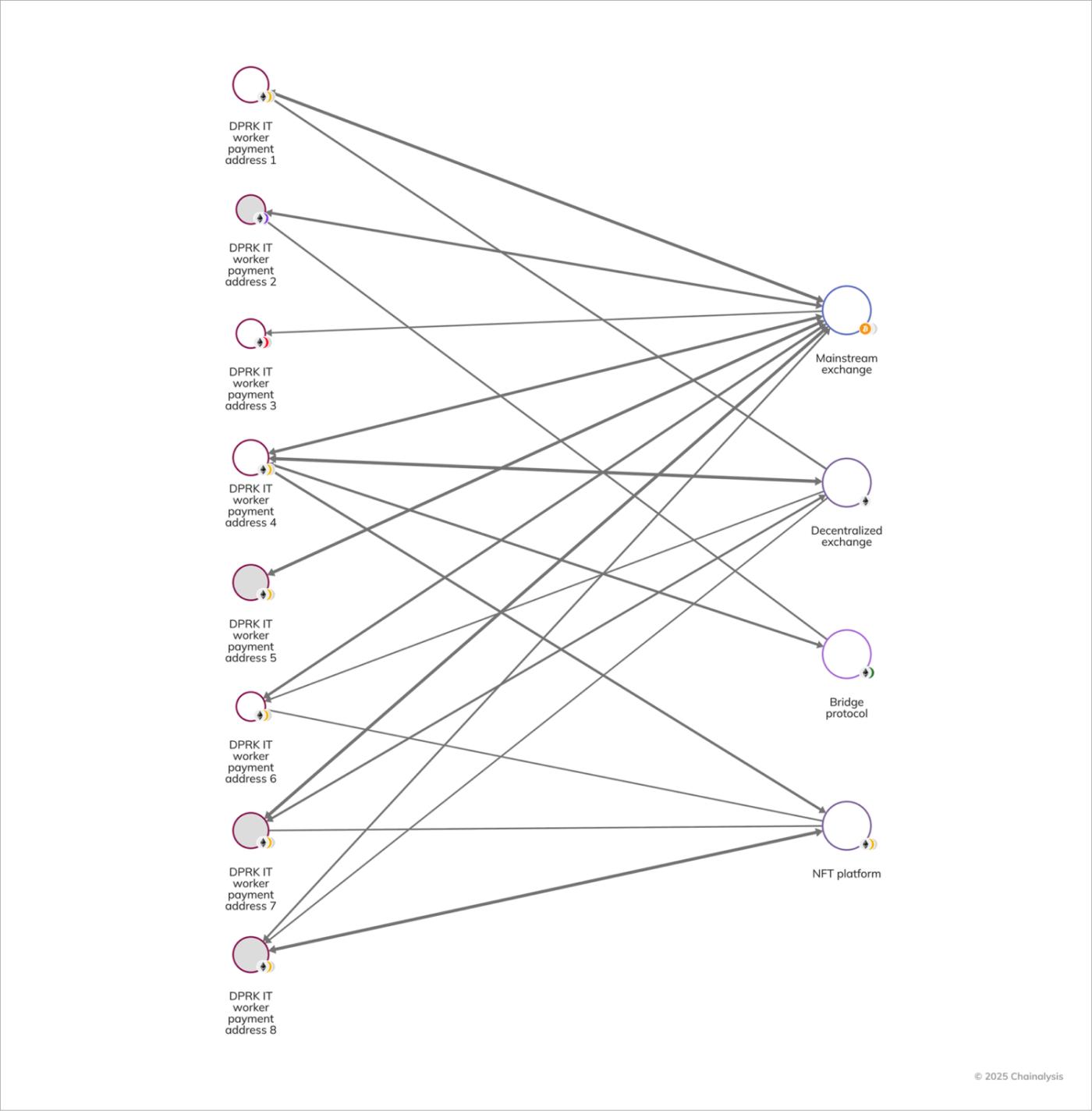
After receiving their paychecks, North Korean IT workers move their crypto assets using multiple money laundering techniques. Chain hopping and token swaps are some of the ways IT workers and money launderers separate the origin and destination of funds on-chain. They also utilize smart contracts such as decentralized exchanges (DEXs) and bridge protocols to make it difficult to trace the funds.
The Chainalysis Reactor graph below shows how decentralized protocols, bridges, and popular exchanges are being used to hide the flow of funds.
North Korean IT workers also use intermediaries to facilitate the money laundering process and ultimately transfer the funds to North Korea. According to the DOJ funds seizure order, the IT workers' payment funds are layered with other criminal proceeds and North Korean IT workers' funds and transferred to regime officials who open accounts on mainstream exchanges using false identities.
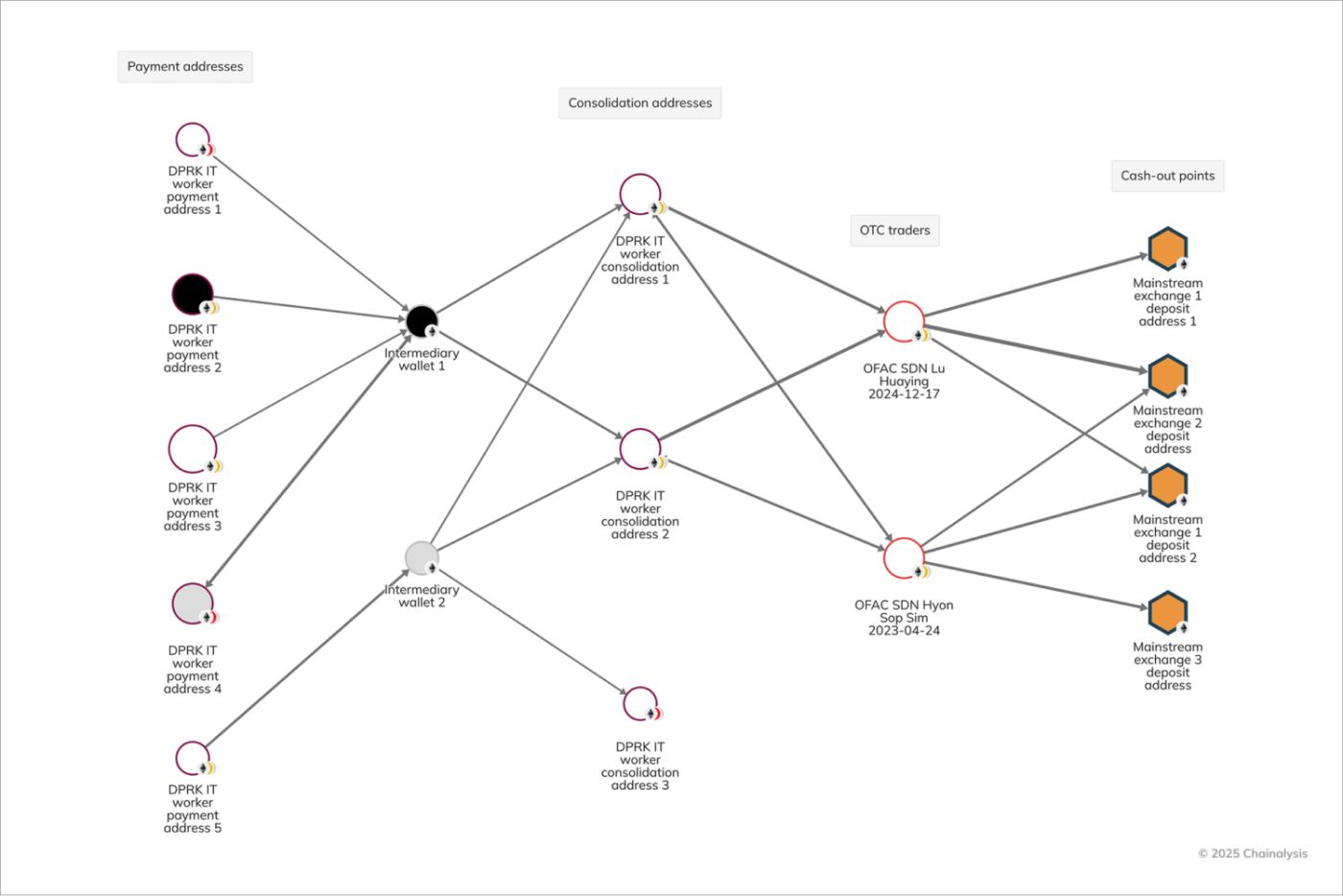
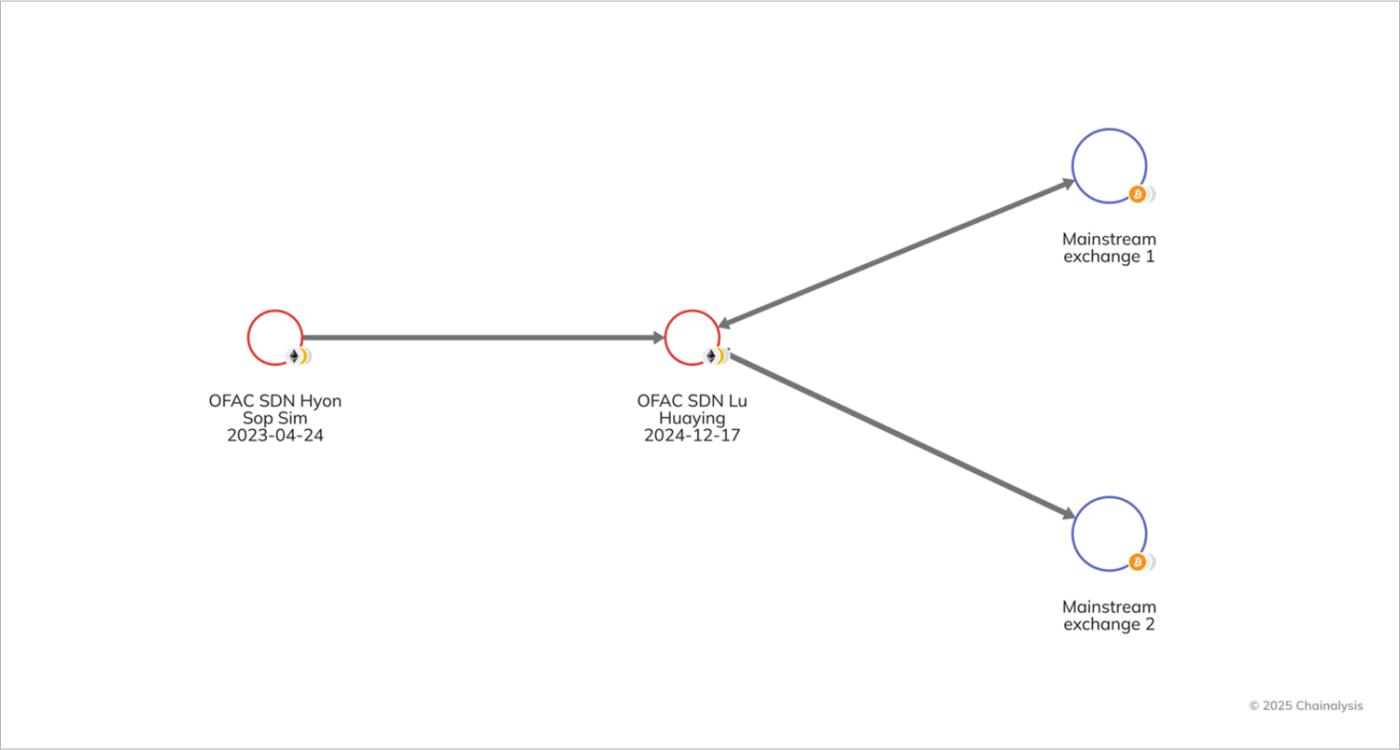
North Korean money launderers often open exchange accounts using fake identities, while those operating in other countries often do so under their real names. According to the DOJ order, Sim used a fake Russian identity card, while Lu opened an account on FTX (now closed) under his own name and a UAE residency card.

The seizure order also noted that the funds belonging to North Korean IT workers were transferred to Kim Sang Man (KIM), the representative of Chinyong, Sim Hyon Sop (SIM), who is affiliated with KKBC, and Lu, an over-the-counter trader who was sanctioned in December 2024 for using a front company in the UAE to transfer illicit funds to Pyongyang.
The reactor graph below shows the flow of funds from North Korean IT workers to KIM’s exchange accounts and unhosted wallets operated by SIM Lu.
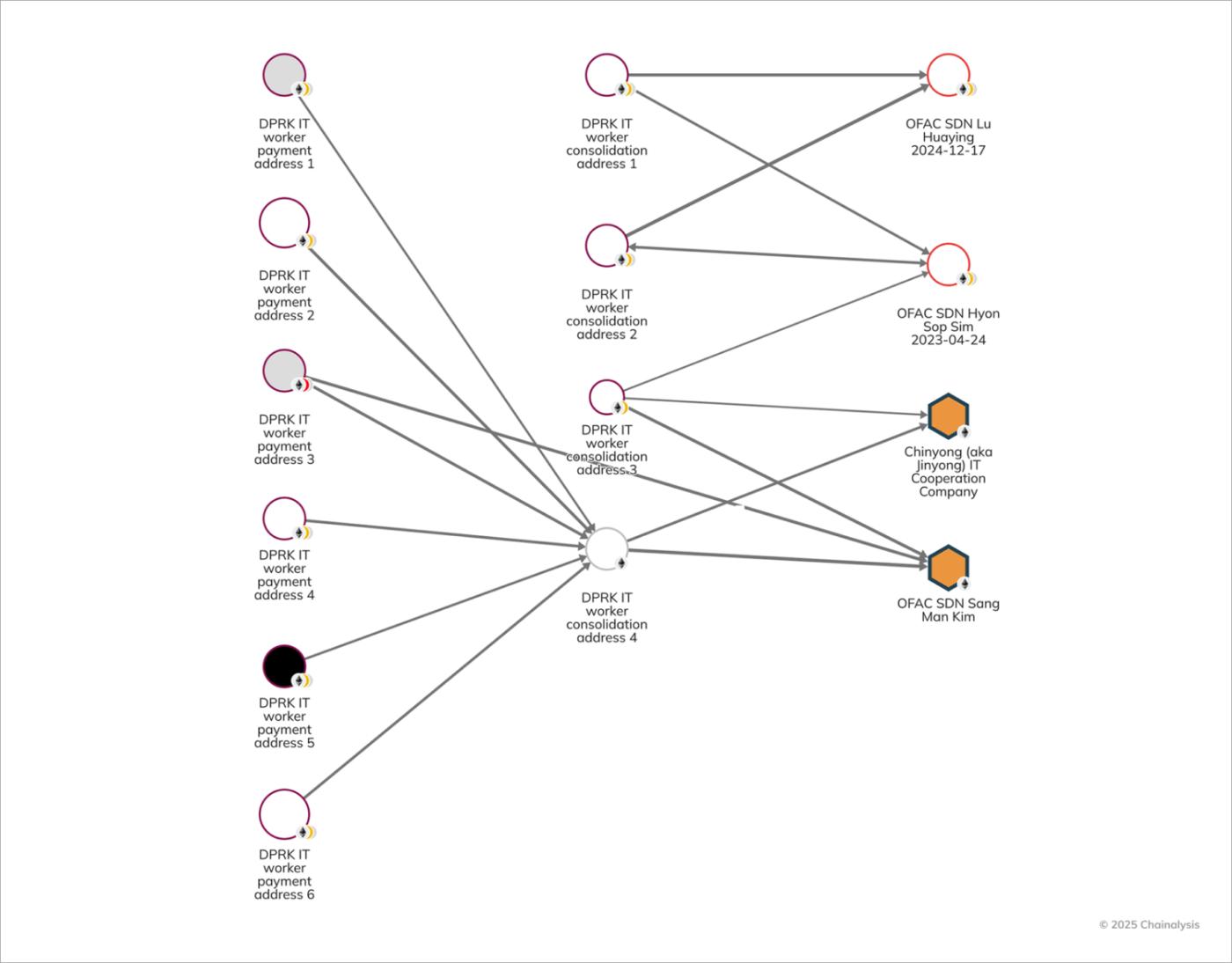
Converting earnings into fiat currency
After North Korean IT workers launder their earnings on the blockchain and transfer them to agents of the North Korean regime, these funds are converted into fiat currency, often through phantom accounts on mainstream exchanges or over-the-counter (OTC) brokers. The graph below shows how SIM's heavy reliance on Lu to launder money for the North Korean regime is evident.
Response to money laundering networks using cryptocurrencies and lessons learned
The recent OFAC designation and DOJ seizure order highlight growing international restrictions on North Korean IT labor schemes and efforts to disrupt their financial networks. From their contributors to their infrastructure and intermediaries, these networks will continue to be a prime target for law enforcement.
Advisories issued by the UK Treasury OFSI and the US FBI's Internet Crime Complaint Center outline red flags that private companies should monitor and identify. Key red flags include mismatches between identity, location, and certificates, the use of anonymization infrastructure, irregular payment flows, and behaviors indicative of concealment. By checking both on-chain and off-chain indicators, IT industry participants can make a significant contribution to disrupting these financial pipelines.
For companies to identify the activities of North Korean IT workers, they need to perform specific checks, such as: IP address mismatch with declared address, manipulated ID, refusal to make video calls or use of AI-generated profiles, preference for payment in stablecoins, requests for installment payments to multiple wallets, requests for complex third-party payments, and lower-than-market compensation compared to high technical skills. By incorporating these checks into their compliance systems and keeping detailed records of interactions with contractors, companies can avoid the risk of unknowingly aiding North Korea in sanctions evasion.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient's use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claims attributable to errors, omissions, or other inaccuracies of any part of such material.
The post Inside North Korean IT Workers' Cryptocurrency Money Laundering Network appeared first on Chainalysis .








