What happens when an "impenetrable" digital fortress encounters a state machine determined to knock on its door?
In October 2025, an announcement from the U.S. Department of Justice sent a chill through the hearts of Bitcoin believers worldwide. The announcement announced the successful seizure of $15 billion worth of Bitcoin, all of which originated from a Cambodian criminal empire controlled by a Chinese individual named Chen Zhi.
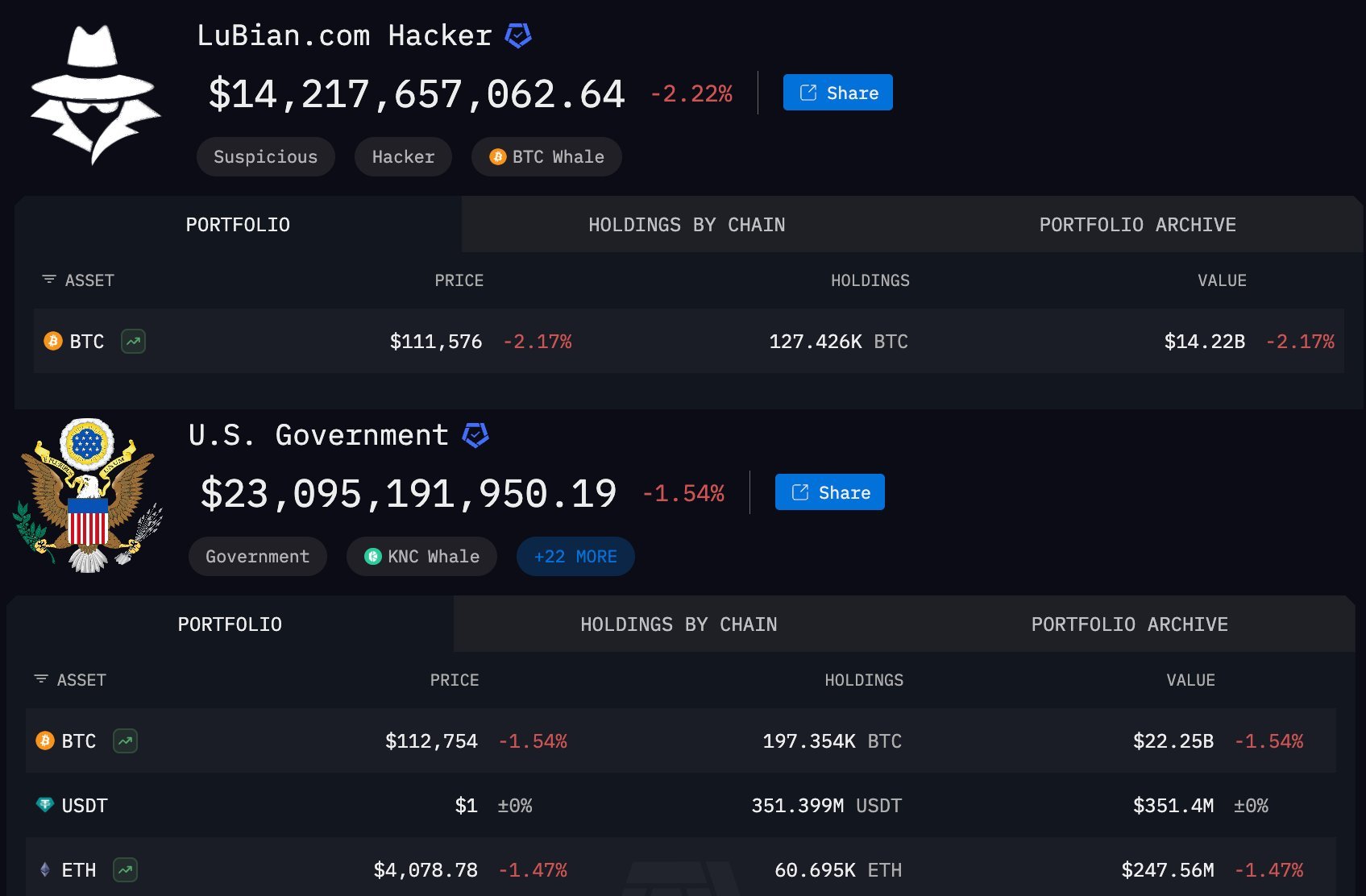

This wasn't just another news story about cash or gold being seized. The paradox was that this astronomical amount of Bitcoin was believed to be stored in a personal cold wallet, for which Chen Zhi himself controlled the private keys—the crypto world's universally recognized and sacrosanct gold standard of "self-custody."
"Not your keys, not your coins"—this cornerstone tenet of the Bitcoin world—suddenly seems powerless in the face of the long arm of state power. A core question lingers in the mind of every Bitcoin holder: If even isolated cold wallets can be forcibly confiscated, what remains of the financial sovereignty we believe in?
Many people speculated that there must have been an insider or that the physical equipment had been seized. But the truth is far more disturbing: the government could have calculated your private key out of thin air without even having to find you or pry open your safe.
Based on various community information and analysis, the situation appears to be this: the government lacks the ability to "break" the Bitcoin protocol itself, which remains secure. However, they have found a new approach—targeting "people" and "vulnerable code." Their arsenal is a combination of tactics: legal action, on-chain analysis techniques, and various other means to obtain private keys.
Original Sin: The “Not Random” Private Key
The story all began with a company called "Lubian Mining Pool" (Lubian.com).
According to community intelligence, Lubian is a Bitcoin mining pool founded by Chinese individuals. It rose to prominence in 2019, briefly ranking among the top ten global mining pools thanks to its computing power and low fees. However, in an effort to save on transaction fees for bulk transfers to miners, Lubian's developers made a fatal mistake: rather than using industry-standard wallet software, they wrote their own program for bulk address generation.
Their program had a "ridiculous" problem: the "random numbers" used to generate private keys were actually not random at all.
To understand this, let's use an analogy. A truly secure Bitcoin private key is like a lottery ticket with 256 numbers, each of which is drawn independently and randomly between 0 and 1. The probability of guessing the correct numbers on this lottery ticket is infinitesimally lower than finding a needle in a haystack; it's cosmically impossible.
But Lubian's program was like a broken lottery machine. Instead of randomly selecting numbers from a near-infinite number of possibilities, it seemed to be stuck, consistently printing tickets with highly similar numbers. For example, the first 224 numbers were always fixed, with only the last 32 changing.
Hackers discovered the lottery machine's malfunctioning pattern. Instead of having to guess a 256-digit astronomical number, they only needed to guess the final 32 digits, a limited number of possible combinations. This made cracking the machine incredibly difficult, going from "impossible for even a god" to "solvable for mere mortals." The hackers easily copied every private key the faulty machine could generate and emptied the corresponding wallets.
Lubian planted the atomic bomb himself.
The mysterious hacker's "Christmas robbery"
On December 28, 2020, someone pressed the detonator.
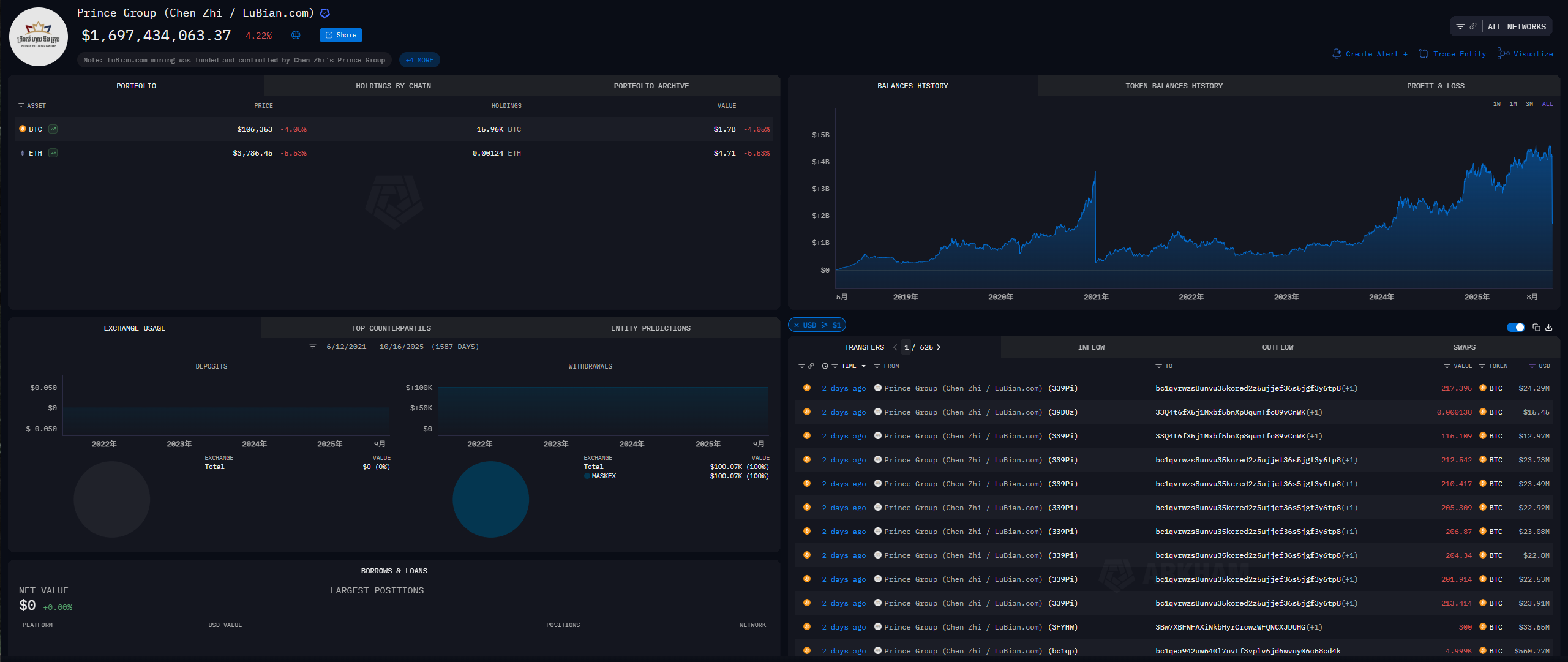
Independent security researcher Christian Reitter's report confirmed that on that day, one or more mysterious actors had apparently discovered a critical vulnerability in Lubian. Within just two hours, a frantic transfer of assets began.
- A total of approximately 136,951 bitcoins (worth approximately $3.7 billion at the time) were swept from hundreds of weak private key addresses controlled by Lubian.
- The actor's method was precise and he seemed to have complete control over the private keys of these addresses, and he transferred money as easily as if he were transferring money from his own wallet.
- About 9,500 of the bitcoins were transferred back to an address that Lubian continued to use, suggesting the actor may not have intended to wipe out the group, or that this was a chaotic mix of a white hat rescue and a black hat attack.
Lubian officials are being extremely secretive about the incident, their website is down, and their official account hasn't been updated since. They seem completely stunned.
Even more dramatic is that, in July 2022, nearly two years after the incident, someone began broadcasting messages to the hacker’s address via the OP_RETURN function on the chain:
“MSG from LB. To the whitehat who is saving our asset, you can contact us through [email protected] to discuss the return of asset and your reward.”
"LB" clearly refers to Lubian. They seemed to still hold out hope that the other party was a "white hat hacker" and attempted to recover their losses by "discussing asset return and your rewards." However, this belated letter fell on deaf ears.
The US government's "mantis stalking cicada"
Fast forward to 2025. Another protagonist of the story, "Crown Prince" Chen Zhi, and the criminal empire behind him have come into the sight of the U.S. government.
Prosecutor's documents paint a hellish picture: Chen Zhi's "Prince Group" operated at least ten prison-like "fraud parks" across Southeast Asia, imprisoning thousands of workers lured by false promises of high-paying jobs. They were subjected to violence and torture, forced to perpetrate the notorious "pig slaughter" investment scam against people around the world. This operation, labeled a "humanitarian disaster" by the US Department of Justice, provided unassailable legitimacy for the government's subsequent transnational manhunt.
Investigations revealed that his astronomical criminal proceeds were laundered through the now-defunct Lubian mining pool—Chen Zhi was the mastermind behind Lubian. Recent intelligence suggests his wealth is far greater than imagined, with total holdings potentially reaching 220,000 BTC. It's no wonder that since the 2017 bear market, the legend of the "Prince" being the biggest buyer has persisted in the over-the-counter (OTC) market—he single-handedly sustained the prolonged bear market.
Now, the "Trident" in the hands of the US government has finally found its place.
The Spear of the Law: Locking Up Criminal Assets
Chen Zhi's undisputed "pre-crime" provides the US government with its strongest legal weapon. They are not seeking to seize ordinary assets, but rather proven illegal proceeds closely linked to large-scale crime. In the US, statutes such as the United States Code provide a clear basis for confiscating criminal property. The robust civil forfeiture power allows for the prosecution of assets even before the owner has been convicted of a crime, significantly lowering the barrier to action.
Technology Eyes - Locking You in on a Transparent Ledger
The government's goal was no longer to target Lubian's long-empty addresses, but to track the whereabouts of over 130,000 bitcoins transferred by the mysterious hacker in 2020. Using digital hounds like Chainalysis, investigators linked the flow of these stolen funds to Chen Zhi's criminal network on the complex blockchain, ultimately proving the funds were indeed stolen money.
Action Arm – Seizing Private Keys from Hackers
This is the new core mystery: How did the government obtain the private key from the mysterious hacker (or hackers)? Public information is very secretive about this, and this vagueness itself is a deterrent. There are several main theories at present:
- Second crack: Since the vulnerability is public, the US government is fully capable of using its own national computing resources (mathematicians, hackers, supercomputers) to independently calculate the private key again, just like the hackers did back then.
- Hacker arrested: The U.S. government may have successfully located and captured the hacker in 2020 through technical tracking and traditional investigation, and forced him to hand over the private key through judicial transactions.
- Voluntary surrender: Another possibility is that Chen Zhi, who is still on the run, in order to "cut off his tail and survive", took the initiative to reach a secret agreement with the US government and hand over the assets controlled by his network in exchange for certain compromises.
- Traditional infiltration: Of course, the most traditional means cannot be ruled out, such as a "ghost" within the criminal group defecting and providing intelligence.
Regardless, the US government played the role of a mantis stalking a cicada, unaware of the oriole behind. They used the clues left by the hacker attack and ultimately successfully nationalized the huge amount of assets that originally belonged to Lubian, were stolen by hackers, and were the source of criminal proceeds.
From the Auction Gavel to the National Treasure: America's New National Strategy
A more profound change has occurred in the U.S. government's attitude toward these confiscated assets.
In the past, exemplified by the Silk Road case, the U.S. Marshals Service would liquidate confiscated Bitcoin into U.S. dollars through public auctions. This was more of a routine operation for disposing of criminal proceeds, with the government acting as the “seller.”
A new paradigm: Strategic Bitcoin Reserve An executive order signed in March 2025 completely changed the rules of the game. The order announced the establishment of a "Strategic Bitcoin Reserve" with a strikingly clear core principle: Bitcoin deposited in the reserve "may not be sold" and will be maintained as a strategic asset of the United States (compared to "digital gold").
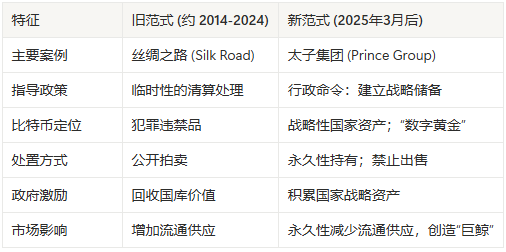
This new policy effectively transforms the U.S. Department of Justice, the FBI, and other law enforcement agencies into the world’s most efficient and legal Bitcoin hoarders. The core mission of combating crime is seamlessly integrated with the strategic goal of increasing national reserves, creating a powerful positive feedback loop.
Is your Bitcoin at risk?
Back to the most important question for all players: "Do I need to worry about my Bitcoin?"
The answer provided by this case is: what you need to worry about may not be a strong government, but stupid code.
The root cause of this storm is an epic code vulnerability that, according to incomplete statistics, has affected over 220,000 addresses . Even more outrageous is that, to this day, some people are still transferring funds to these publicly leaked addresses. You can check if your address is affected by the vulnerability by following this link: https://git.distrust.co/milksad/data
This gives us ordinary players the following inspiration:
- Your first line of defense is your code, not your safe. Your sense of security shouldn't come from how well you've hidden your seed phrase seed phrase , but from your confidence that the software that generated it is absolutely reliable. Never use wallet software that's unidentified, closed-source, or hasn't been rigorously audited by the community.
- The government's target isn't you. For the vast majority of law-abiding individuals, there's little need to worry. The government's target profile is clear: large criminal organizations with serious "precursor crimes" (such as large-scale fraud, drug trafficking, and money laundering). Without this foundation, legal action cannot be launched.
The red line that cannot be crossed is always the "predicate crime." The rule of law and the Fourth Amendment to the U.S. Constitution (prohibiting unreasonable searches and seizures) remain the ultimate safeguards for the property of law-abiding citizens. However, the real long-term risk lies not in the arbitrary seizure of assets, but in the potential expansion of the definition of "predicate crime." While this is true, it presupposes that your private key must be a true private key —a cryptographic product generated through sufficiently strong, verified randomness.
This $15 billion bloodbath sounded the alarm for the entire industry: in the dark forest-like world of encryption, any tiny, self-righteous code shortcut may lead to an abyss of no return.








