The fall of the exchange FTX triggered the second "Lehman crisis" in the cryptocurrency world this year.
By Yuqi Xie, Foresight Research
Cover: Photo by Max Letek on Unsplash
Key Takeaways
- The essence of digital asset custody is the custody of customers’ private keys . Private key custody is divided into self-custody and three-party custody. Self-custody means that users use cold/hot wallets to host their own private keys. Three-party custody refers to the use of Multisig, HSM and MPC. The type of security measures basically manages the customer's private key to ensure that a malicious single actor cannot transfer assets without the consent of other interested parties, eliminating the problem of a single point of evil.
- Custodians can be divided into direct custodians, hosting technology providers, and mixed solution providers according to whether they directly escrow users’ private keys. Direct custodians participate in customer private key management, and are further divided into direct custodians subject to government supervision and those not subject to supervision. Private key custodians, representing manufacturers including Anchorage Digital (valued at $3B). The customer of the technology provider service to B does not hold the assets under custody, and the responsibility for private key management is borne by the customer. Representative manufacturers include Fireblocks (valued at $8B). The mixed solution provider not only directly participates in hosting but also exports hosting technology externally, representing manufacturers including Bitgo (valued at $1.2B, DGC gave up the acquisition)
- The cryptocurrency custody industry is developing rapidly, and the industry AUM and penetration rate are increasing rapidly. Since 2019, digital asset custody assets have increased by 600%, and as of January 2022, the scale of cryptocurrency asset custody will reach $223B. Of the 150 cryptocurrency hedge funds with an AUM of $2 billion, 52% used custody services in 2018, rising to 81% in the past two years. In 2021, the primary capital market of the digital asset custody industry responded enthusiastically, with a total financing amount of $4.5B, a year-on-year increase of 457%.
- Encrypted hosting services have a high threshold, and core competitiveness includes sufficient capital, technology, and trust thresholds. In the future , national regulatory licenses are also important factors for winning traditional institutional customers. Most of the service objects are enterprise-level customers, including project parties, trading platforms, Token Funds, family wealth funds, hedge funds, mortgage lending platforms, etc.
- The single-asset custody business model is not high-quality, and its custody fees will further decline with industry competition. It is expected that encrypted asset custody will become the supplier's traffic entrance in the future, and encrypted custody providers will further expand asset value-added services to expand profit sources and enhance industry competitiveness, such as PoS mining commissions, transaction commissions within custody, lending fees, and legal currency fund channels Asset value-added services such as commissions.
1. Introduction: FTX Thunderstorm Exposes CEX Asset Custody Security Issues
The fall of the exchange FTX triggered the second "Lehman crisis" in the cryptocurrency world this year. Multiple criminal evidences such as related transactions and user fraud have once again exposed the risk of centralized exchanges wantonly misappropriating customer assets to the public. Centralized exchanges have always won the majority of customers with the advantages of fast transaction speed and convenience, but the security of asset custody has not received enough attention. Most users unconsciously choose the tradeoff of trading experience and security. Compromise, taking custody risk in exchange for transaction convenience.
FTX’s transaction service terms clearly stated that “user assets do not belong to FTX Trading, and users enjoy absolute control over their accounts at any time.” Warn the industry that CEX asset custody based on exchange credit endorsement is extremely risky .

The essence of the CEX exchange is that buyers and sellers transfer encrypted currency assets to the exchange's own account, and the exchange conducts asset custody + order matching. Once the user's assets are transferred to the exchange account, the assets are actually out of the user's control. User assets are not protected by commercial insurance (although FTX once hinted on twitter that FTX US is insured by the FDIC), once the risk of hacking or the exchange goes bankrupt, the user's assets will be completely irrecoverable.
How does the asset custody mechanism in the traditional Web2 financial field protect the security of user assets, prevent institutional adverse selection and moral hazard, and various systemic risks derived therefrom? What are the specific solutions for Web3 asset custody at present, and how to improve the security of asset custody in the Web3 field, so as to avoid the recurrence of malicious incidents by CeFi centralized institutions such as FTX and Celsius? This article will start from the traditional asset custody field and the industry structure of encrypted currency assets, and explore the present and future of the development of the encrypted asset custody industry.
2. Traditional Asset Custody Industry: Custody License as the Core Threshold
1. Basic content
- Escrow means entrusted custody. While the investor entrusts an independent third party to invest in securities, equity and other entrusted funds, an independent third party, namely a custodian bank and other financial institutions, is entrusted to help investors keep their funds/securities , and to play a role in fund transfer and supervision of investment institutions Responsibilities to ensure the safety of customer assets. The main users of the domestic custody business are public funds.
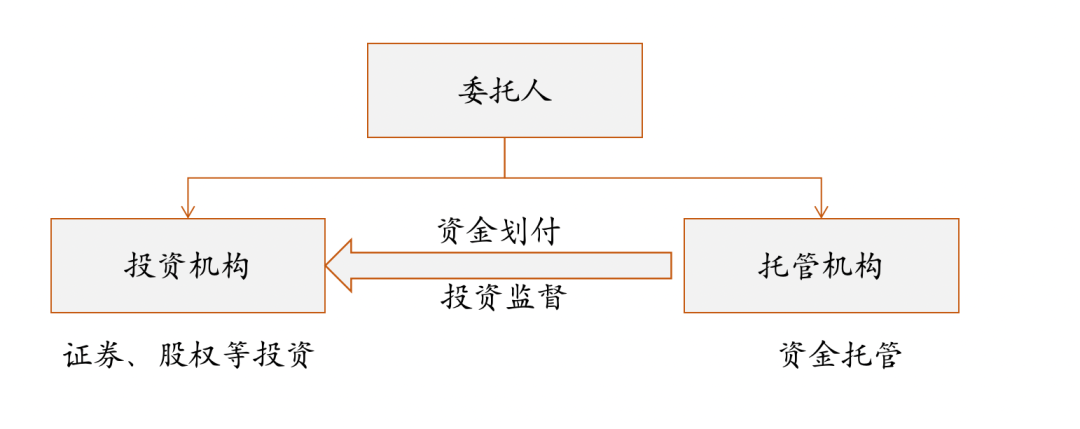
In March 2019, the "Guidelines for the Asset Custody Business of Commercial Banks" issued by the China Banking Association clarified that the asset custody business of commercial banks refers to the commercial bank as an independent third party, in accordance with the provisions of laws and regulations, signed with the client, manager or trustee. Custody contract, the intermediary business of commercial banks that keeps the entrusted assets according to the agreement, performs the rights and obligations stipulated in the custody contract, provides custody services, and charges custody and custody fees.
- Asset custody is divided into fund custody and securities custody .
- Fund depository: The essence of the transaction is not reviewed. The purpose is to prevent client funds from being misappropriated , mainly including transaction settlement funds of securities clients, online lending funds, reserve funds of payment institution clients, and risk protection funds, etc.
- Securities depository: mainly refers to the securities depository and settlement institutions accepting the entrustment of securities companies to centrally store the securities delivered by customers and securities companies. At present, there is only one securities depository and clearing institution in my country. Its functions include opening and managing securities accounts; maintaining the balance of client securities and self-owned securities deposited by securities companies through the bookkeeping system, providing services such as inquiries and collecting dividends, and recording the creation, change and termination of the custody relationship between securities companies and customers .
- The core purpose of asset custody is to prevent client funds from being misappropriated , mainly including transaction settlement funds of securities clients, online lending funds, reserve funds of payment institution clients, and risk protection funds, etc.
2. Main functions
Traditional asset custody can be mainly divided into four functions: asset custody, fund transfer, accounting, and investment supervision. The asset custody business of commercial banks is divided into two categories: basic services and value-added services.
- Basic services: account management, liquidation, accounting, investment supervision, reporting, information disclosure, etc.
- Value-added services: foreign exchange transactions, cash and Liquidity management, securities lending, brokerage transactions, securities issuance, performance evaluation, risk management, fund administration management, tax management, collateral management, etc., to provide customers with comprehensive financial solutions.
3. Industry Status
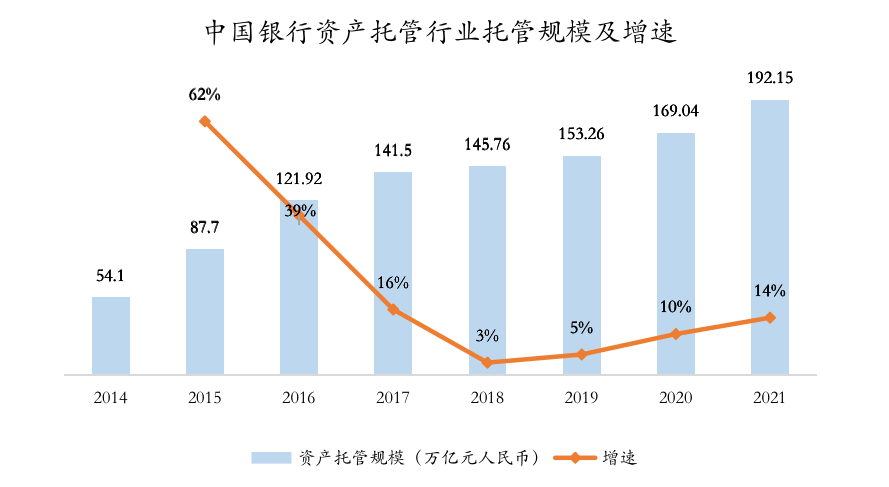
(1) The asset scale of the traditional custody industry has steadily increased, and the custody market size in 21 years has reached nearly 200 trillion yuan.
- Asset custody business is a relatively important type of off-balance-sheet or intermediate business of commercial banks. According to the China Banking Association, the asset custody scale will reach 169 trillion and 192 trillion by the end of 2020 and 2021, respectively, with a year-on-year increase of 14.55% in 2021.
- The asset custody business is one of the important directions for the transformation and development of banks. On the one hand, the asset custody business is an off-balance sheet business, with very low capital occupation and high comprehensive income, which helps to improve ROE; on the other hand, asset custody can become the entrance for banks to obtain customers, and provide other services to customers through asset custody.
(2) The industry takes the custody license as the core barrier, and the market presents an oligopolistic competition pattern, and the market share is highly concentrated.
- The main participants in traditional asset custody are mainly commercial banks, and also include securities companies, China Bond Depository / CITIC Depository / China Securities Depository.
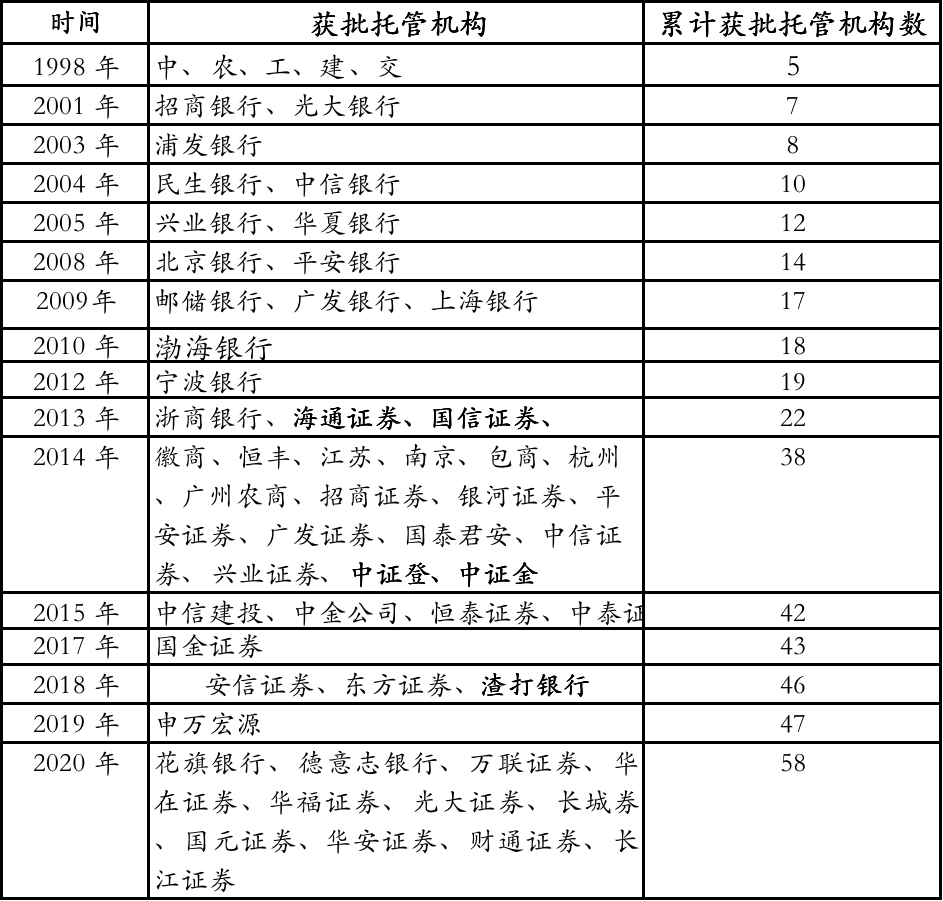
- Before 2013 , the only domestic financial institutions engaged in asset custody business were banks.
- At the end of 2013, the China Securities Regulatory Commission issued the first securities investment fund custody license to a securities company, which became an important milestone in the expansion of the type of custody institution from commercial banks to securities firms. At present, the domestic financial institutions that can engage in asset custody business are mainly banks, securities companies, and professional institutions such as China Financial Information Registration and Custody Center, China Securities Regulatory Commission, and China Securities Regulatory Commission.
- The competitive landscape of the asset custody industry presents an oligopoly pattern, with a high degree of industry concentration.
- At present, 60 institutions have obtained fund custody licenses: 30 banks and 30 securities firms.
- There are 10 banks with a custody scale of more than 10 trillion (a total of 150 trillion), and 13 banks with a custody scale of more than 5 trillion (a total of 170 trillion), all of which are national banks.
Table 1: Time for various institutions to obtain securities investment fund custody qualifications
(3) The competition in the industry is becoming more and more fierce, and the custody fee rate is decreasing year by year. There are three main sources of profit for the asset custody business: custody fee income, interest income from deposit accumulation, and payment and settlement income. Due to the homogenization of hosting business, the number of players in the industry continues to increase, and the competition intensifies, the average hosting fee rate has decreased year by year. According to the China Banking Association, the average custody fee rate in China has dropped from 0.119% in 2011 to 0.031% in 2020.

(4) Custody of public funds is still the foundation and core of asset custody business of commercial banks
- Commercial bank asset custody initially mainly refers to the custody of public funds, and then based on this, the scope of business and objects of operation have been continuously expanded.
- In addition to public funds, the custody of various asset management sub-industry funds, insurance and pension funds, tripartite fund supervision, QFLP and QDLP funds, etc. also fall into this category. The reason why the scale of asset custody business of commercial banks far exceeds the scale of public funds.
(5) The infrastructure of the commercial bank custody system is mainly provided by the third-party financial IT company
- Upstream IT suppliers (Hang Seng Electronics, Winsun, Vertex Software, etc.) mainly provide the underlying clearing and delivery systems and independent hosting business technology systems.
- Technical systems specifically include network systems, application systems, security protection systems, and data backup systems.
3. Digital asset custody industry: with brand and technology as the core threshold
1. Basic content
- Crypto asset custody, also known as digital asset custody, can be defined as the safe custody and protection of a client's encrypted assets. Third-party institutions put customers in control of their private keys through professional services that manage customers' private keys, or technology providers that provide custom custody solutions to reduce potential theft, hacking and other forms of risk.
- The core task of the custodian is still to ensure the security of customers' digital assets . However, due to the digital native and public-private key encryption characteristics of such assets, the private key directly represents the ownership and use rights of the asset , and the custodian does not need and cannot store the asset itself, but directly protects the owner's key to ensure asset security.
2. Solution Classification
Private key custody is divided into two types of solutions: self-custody and three-party escrow. Self-custody means that users use cold/hot wallets to escrow their own private keys. Three-party escrow means using Multisig, HSM and MPC. Carry out basic management to ensure that a malicious single actor cannot transfer assets without the consent of other interested parties, eliminating the problem of a single point of evil.
(1) Self-custody: hot wallet/cold wallet self-custody wallet derives private key and its corresponding public key and on-chain address through Seed Phrase and hierarchical deterministic structure (Hierarchical Deterministic) . Self-hosted wallets allow users to generate private keys used to sign transactions and recover all private keys using a Seed Phrase .
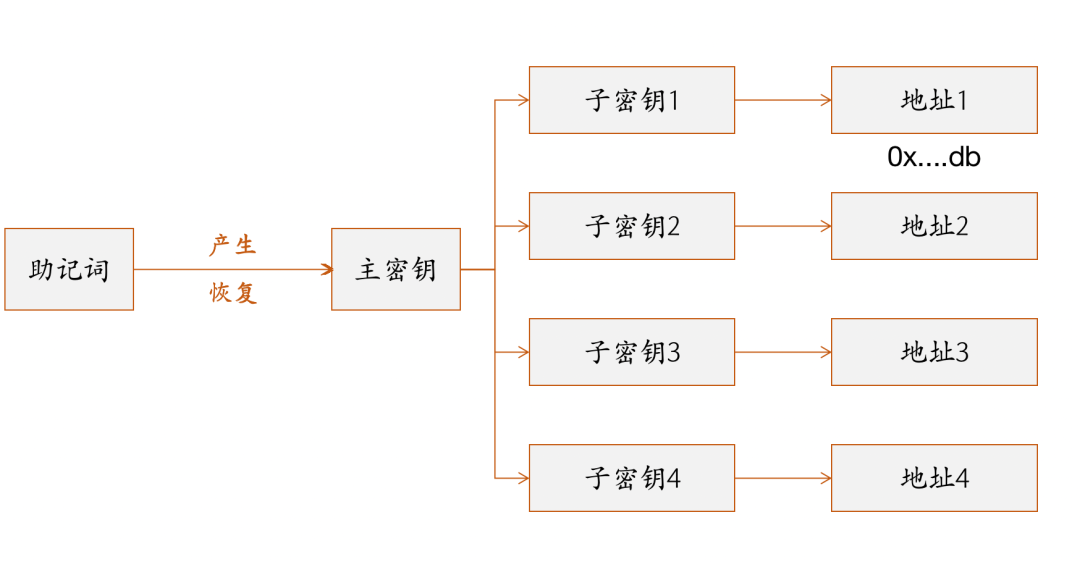
Self-hosted wallets are divided into hot wallets and cold wallets. The difference is that hot wallets (Metamask) are always connected to the Internet, while cold wallets (Ledger, Trezor, etc.) are not and can protect private keys offline.
- Advantage: Completely eliminate credit risk.
- Disadvantages: Seed Phrase and keys directly determine the right to use and ownership of assets, and the self-custodial wallet will most likely cause a single point of failure due to external hacker attacks.
(2) Third-party hosting
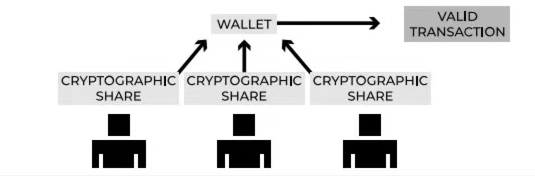
Usually, it provides a security solution for storing and managing private keys for institutions such as DAO or hedge funds, and solves single point of failure through additional security measures.
- Multi-Signature: Through smart contracts, "multiple private key signatures" are used to confirm transactions.
- A multi-signature wallet is a smart contract that improves security by requiring multiple private keys to sign transactions before execution. It is an on-chain function that is directly integrated at the blockchain level. Transactions can only be sent if multiple wallets sign the transaction together.
- In a multisig wallet, custody of assets is shared among trusted parties, with signers trusting other signers not to act maliciously.

- Advantage:
- No single point of failure: multiple signatures are required to execute a transaction. Flexible access control: Users can customize different access rules, set time locks, spending limits, etc. Programmable Recovery of Keys: Wallets can offer multiple options for recovering funds back into the smart contract itself. Operational transparency: On-chain signature authorization policies and aggregates explicitly use key quantities and objects used to sign transactions, making operations more transparent and straightforward, allowing auditing of those involved in a transaction if something goes wrong.
- disadvantage
- Higher fees: Smart wallets have higher fees than regular single-address transactions due to the need to verify multiple signatures. Operations such as adding/removing owners and changing thresholds also require on-chain transactions.
- Poor scalability: requires custom implementation on non-EVM chains.
- More expensive recovery: While recovery logic is programmable, on-chain fees need to be paid to execute it.
- MPC (Multi-Party Computation): Transactions are confirmed through "signatures with private key shares reaching the threshold".
- Multi-party computation (MPC) is a protocol that uses complex cryptography to distribute computation among multiple parties, where multiple computers need to agree in order to access confidential data. No single computer on the network can individually access data, providing a trustless environment for storing private information.
- MPC wallets eliminate single points of failure by using a Threshold Signature Scheme (TSS). The TSS scheme allows multi-party nodes to jointly generate keys and signatures, but neither party will have a complete key, that is, no node can do evil by signing privately without the joint consent of other nodes.
- Advantage:
- No single point of failure: complete private keys are never centralized on one device.
- Flexible and adjustable signature scheme: Organizations can dynamically adjust the signature scheme, and the approval quorum can be modified as individual and organizational needs evolve.
- Reduce transaction and recovery costs . An MPC wallet is represented on-chain as a single address with the same gas cost as a regular private key address. Recovery of lost key shares can also be done off-chain.
- Disadvantage: Low key generation transparency. Signing authorization policies and approving quorums are managed off-chain, so these custom rules are still subject to centralized failure. Off-chain rules and signatures hinder transparency and require stricter operational audits.
- HSM (Hardware Security Model): Transactions are mostly confirmed by "multiple parties signing on their respective hardware".

(3) Other value-added services
- Insurance Services:
- Custodians provide insurance services for institutions and large enterprises with a large number of assets that need to be stored, such as key recovery services or insurance for segregated assets.
- Most custodians adopt custom insurance policies, and custodians work with insurance brokers to assess their risk profile, develop an insurance policy, and find underwriters who will indemnify them in the event of a claim.

- Audit Services:
- Traditional regulated custodians are subject to annual audits and periodic inspections under the Custody Act to provide additional client protection when registered custodians hold client assets.
- Three-party audits are available for regulated cryptocurrency custodians because cryptocurrencies fall under securities laws. Cryptocurrency services and technology have been thoroughly checked by third-party auditors who verify the effectiveness of a custodian's control systems (security, privacy, usability, etc.).
3. Industry Development
(1) The penetration rate of digital hosting services is rising rapidly.
- Accelerated penetration in the Crypto field: According to PwC data, 52% of the 150 cryptocurrency hedge funds with an AUM of $2 billion used custody services in 2018, and this proportion has risen to 81% in the past two years.
- Traditional finance began to increase crypto business:
- Traditional financial institutions: According to the Ernst & Young report, 31% of hedge funds plan to allocate encrypted assets in the next 1 to 2 years. In addition, traditional banks (State Street and BNY Mellon) are also willing to provide digital asset custody services.
- Traditional FinTech companies: Robinhood, Venmo, PayPal App, etc. have a large number of C-end users. In order to achieve differentiated competition, Web2 payment and transaction tools are continuing to increase their encrypted asset business, providing a huge market space for To B service providers in the encrypted asset industry.
(2) The cryptocurrency custody market will usher in the first year of explosion in 2021.
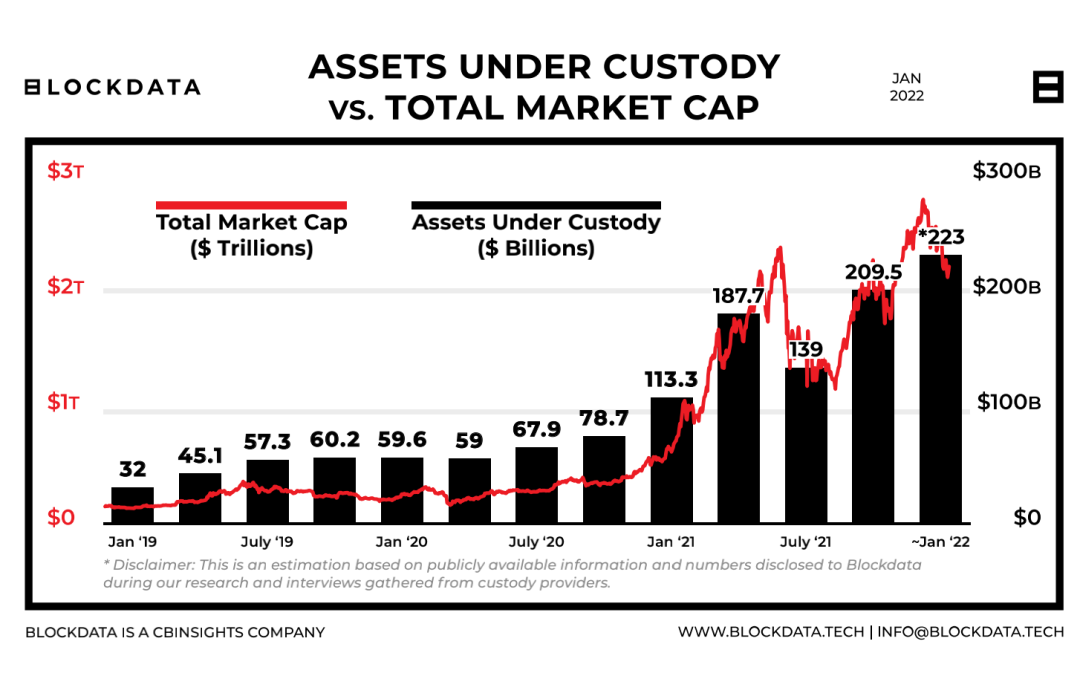
- Industry scale: Since 2019, digital asset custody assets have increased by 600%, and as of January 2022, the scale of encrypted asset custody has reached $223B.
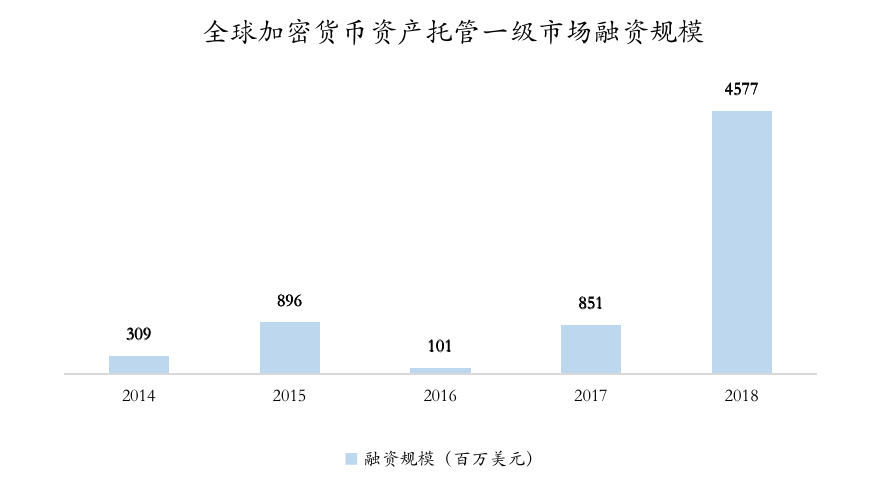
- Financing scale: In 2021, the primary capital market of the digital asset custody industry will respond enthusiastically, with a total financing amount of $4.5B, a year-on-year increase of 457%.
4. Competitive landscape
At present, encrypted asset custody service providers can be classified according to whether they directly host private keys and the type of service customers. (1) According to whether to directly escrow the user's private key, it can be divided into direct custodians, escrow technology providers and hybrid solution providers.
- Direct Custodian:
- Responsible for the management and security of the customer's private key. Custodians need to protect these private keys, maintain control of customers' private keys, and prevent unauthorized access. Direct custodians are divided into government-regulated custodians and unregulated custodians.
- Representative vendors include Genesis, Coinbase, Gemini, Paxos, etc.
- Managed Technology Provider:
- Responsible for providing technical infrastructure for hosting services. Allow customers to use to establish their own transaction verification management rules, and provide the technology to store their assets. Private keys are managed by the client.
- Representative vendors include Fireblocks, Qredo, Ledger, etc.
- Hybrid Solution Provider:
- It not only directly participates in hosting, but also provides technical solutions to B-side customers.
- Representative manufacturers include Bitgo, Copper, etc.
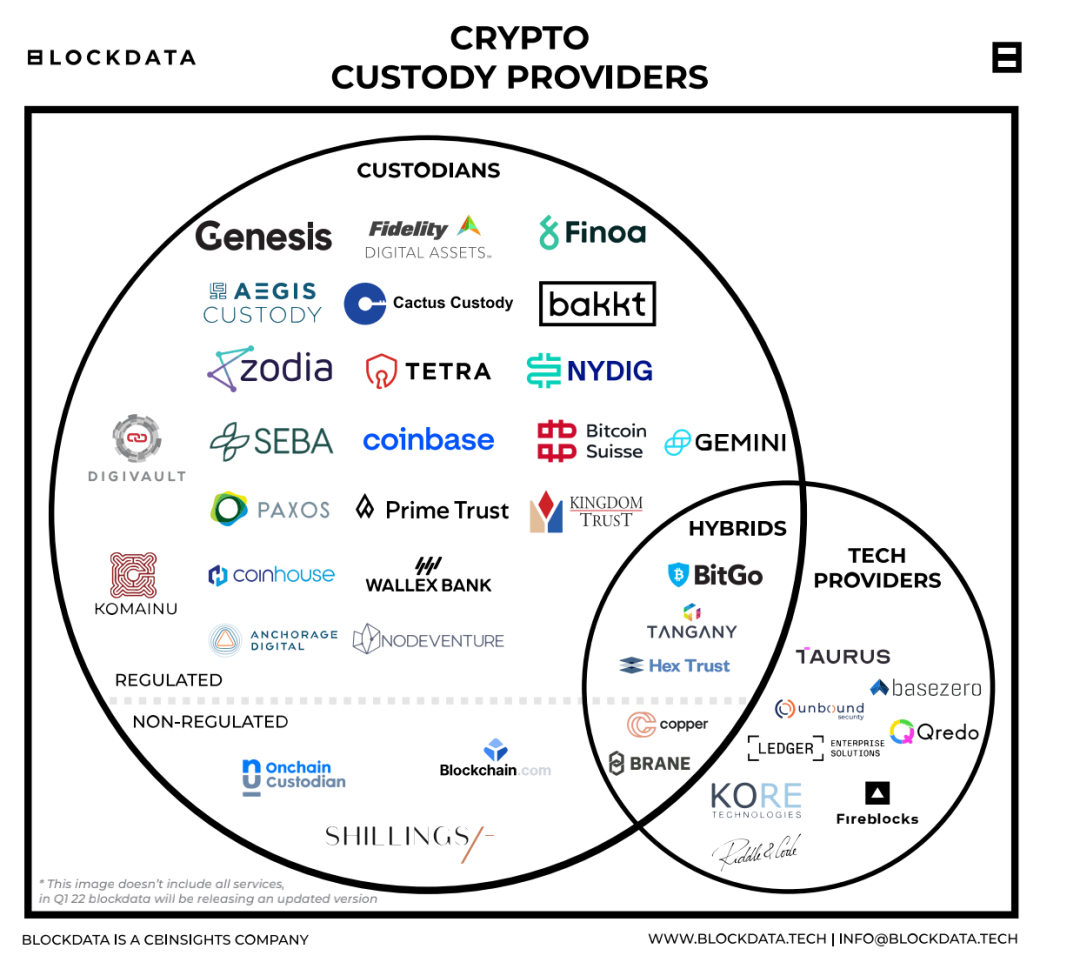
(2) According to the types of service customers, custody providers can be divided into custodians who only provide third-party custody services for institutions, custodians who only serve retail investors , and custodians who provide custody services for both institutions and retail investors.
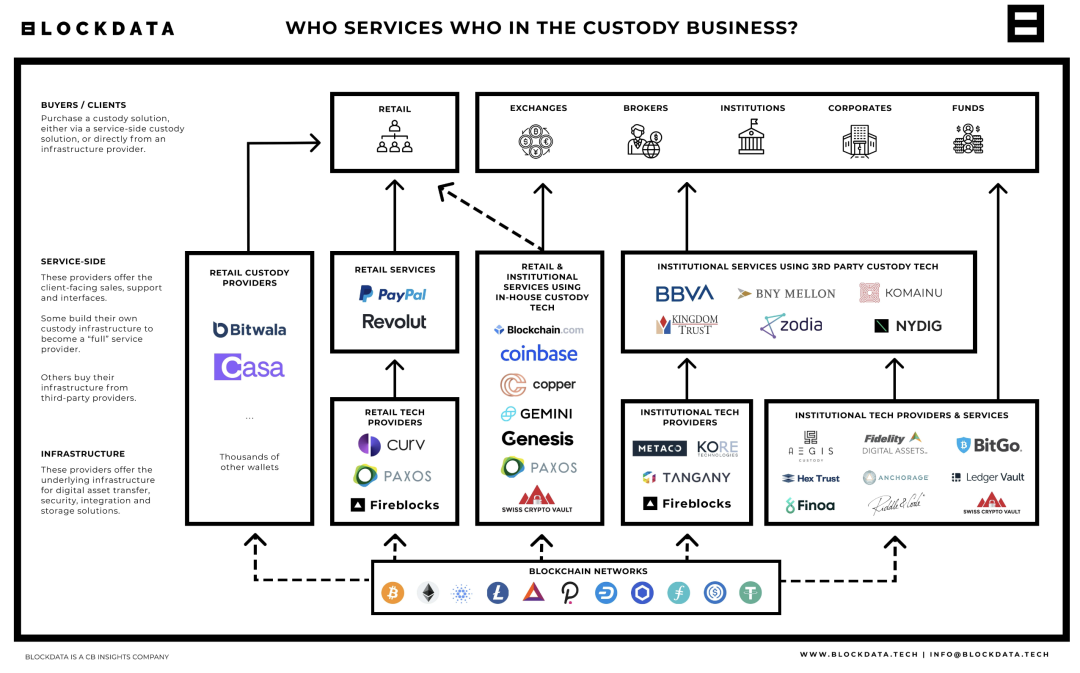
4. Some thoughts
1. The original sin that has led to successive systemic risks in the cryptocurrency market is centralized participants, not decentralized protocols.
Whether it was the serial thunderstorms of CeFi institutions such as Sanjian Capital and Celsius in the first half of 2022, or the serious defeat of FTX in the second half of the year. It has always been the centralized players, not the decentralized protocols, that have caused the crypto ecosystem to collapse one after another. But why is the decentralized world full of such centralized transaction characteristics? Because capital and currency circles like and chase centralization. The former cryptocurrency pioneer SBF does not use decentralized technology with strict technical logic, but uses a variety of false propaganda methods to make users have an illusion about the security of assets, trample on customer trust, and betray industry beliefs.
2. Although the FTX storm is detonating a crisis of confidence in the industry, CEX will not be completely replaced by DEX in the future.
CEX has always been one of the most embarrassing existences in the encrypted world based on the principle of "de-trust and decentralization". However, compared with DEX, whether it is due to the friendliness to C-end users such as fast transaction speed and convenient operation, or the professionalism to B-end users such as the ability to provide value-added services in real time, CEX has a long-term future in the development of cryptocurrency. It is necessary to exist for a period of time, and CEX will not withdraw from the stage of history because of the bankruptcy of FTX.
In the context of the cheap dollar brought about by the Federal Reserve's QE policy, most users' demand for highly risky cryptocurrency Derivatives transactions soared in the past. Under the high trading enthusiasm and optimism, most users only pursue trading experience and often ignore the most basic but core demand for asset custody security protection. FTX is also in this context, with differentiated services such as Derivatives trading and the ultimate trading experience created by mechanisms such as relaxing margin types, it has rapidly expanded its volume and won the trust of customers in the short term, but it also suffered from misappropriation of customer assets, etc. Fraud personally destroys trust.
3. There is no narrative that is too big to fail in the currency circle. In the absence of supervision, CEX should not assume the function of credit intermediary. CEX needs to make better use of decentralized mechanisms to improve transparency and maximize trust, otherwise it can only rely on the entry of traditional regulatory agencies to cover all kinds of fraud and risks.
We must respect the operating laws of traditional financial markets. The important experience of the traditional financial world is that the end result of the "centralized mechanism + no supervision" model is often fraud, adverse selection and various systemic risks.
The final logic of the two Lehman crises in the currency circle is similar: under the background of Liquidity, financial institutions use high leverage + high risk investment to expand their balance sheets crazily, which leads to the subsidence of assets and the mismatch of balance sheet maturity. Liquidity began to be locked, and institutions generated a large number of bad debts, which immediately detonated a Liquidity crisis and a crisis of trust, which eventually led to large-scale bankruptcies. The same story was staged in the subprime mortgage crisis in 2008 and the mutual financial thunderstorm in 18 years. Centralized trust intermediaries cannot be separated from external supervision.
In the absence of supervision , centralized institutions such as CEX should not assume the function of trust intermediary, and cannot operate according to the mechanism of traditional commercial banks. The current situation of the thundering CeFi can be described as crazy, "The assets of exchange customers are directly handed over to deposit and loan institutions such as FTX CEX or Celsius. The whereabouts of customer assets is completely opaque, without any external supervision or protection. It all depends on the quality of the organization .” But as long as it is a centralized institution, it must have the risk of adverse selection and the tendency to do evil. Regardless of whether it is SBF this time, eventually CEX client assets may still be misappropriated and turned into another individual's personal property in the Bahamas.
The most urgent task of rebuilding market confidence is to regulate the development of CEX . How to make good use of the decentralized mechanism such as the full reserve system + Merkel savings certificate or other asset custody methods to improve the transparency of CEX and maximize trust is an urgent problem to be solved today. . If you cannot make good use of the decentralization mechanism to achieve trustlessness, you can only cover various risks by strengthening external credit through tripartite trust or the exit of regulatory agencies.
4. Avoid creating the illusion of asset security, "Code is Law" & "Not your key, not your assets"
De-trusting is still under development, and mastering the private key is extremely important. The bankruptcy of FTX has once again reminded all participants in the cryptocurrency world that compared with traditional financial markets, the cryptocurrency market is always more disordered and immature than imagined. Always remember not to bring the illusion/illusion of asset security in the web2 world into the currency circle. The traditional financial market has a mature risk prevention mechanism, a scientific risk control mechanism, strict legal supervision, various types of commercial insurance protection, and a national credit guarantee. Systemic risks such as large-scale runs and Liquidity crises can be reduced as much as possible. Only in this way can retail investors safely put money into commercial banks or conduct investment activities such as purchasing public funds, and the safety of customer assets can be guaranteed. Even for FTX, which once wanted to be the "mother of the currency circle", there will never be a narrative of "too big to fail" in the decentralized encrypted world. The only thing users can trust in Web3 is "distrust".
Finally, mastering the private key and Seed Phrase and protecting assets are always the first priority of transactions.
[References] 1. https://xueqiu.com/3302797049/220026666
2. https://medium.com/1kxnetwork/wallets-91c7c3457578
3. https://www.blockdata.tech/blog/general/crypto-custody-the-gateway-to-institutional-adoption
4. https://web3caff.com/zh/archives/8113
5. https://mp.weixin.qq.com/s/g21pqOl6het5dxDSDVx8vA
6. China Merchants Securities: Detailed explanation of asset custody business, a must for bank transformation
Disclaimer: As a blockchain information platform, the articles published on this site only represent the personal views of the authors and guests, and have nothing to do with Web3Caff's position. The information in the article is for reference only, and does not constitute any investment advice or offer, and please abide by the relevant laws and regulations of the country or region where you are located.







