Author: Stacy Muur
Compiled by: TechFlow TechFlow
Original link:
https://x.com/stacy_muur/status/2019325467116126348
TechFlow Dive: Over the past decade, Ethereum has made carefully calculated compromises. It traded trustlessness for convenience, autonomy for user experience, and decentralization for mainstream adoption. But 2026 marks a turning point. This is the year Ethereum no longer asks, "Is diluting itself for mainstream adoption worthwhile?" The answer is—no longer. Stacy Muur details Vitalik's vision: making full nodes easy to run again through ZK-EVM + block-level access lists; enabling verifiable RPC through Helios light clients; enabling private payments through ORAM/PIR; transcending fragile seed phrase through social recovery; achieving unstoppable dapp UIs through IPFS hosting; and achieving censorship-resistant block building through FOCIL. The recentralization of the infrastructure layer must end.
Over the past decade, Ethereum has made carefully calculated compromises. It traded trustlessness for convenience, autonomy for user experience, and decentralization for mainstream adoption.
Every time you check your wallet balance, you're trusting companies like Alchemy or Infura. Every time you use a dapp, your data is leaked to servers you never chose.
But 2026 marks a turning point. It's the year Ethereum stops asking itself, "Is it worth diluting itself for mainstream adoption?" The answer is—no longer.

Vision
- Full nodes are easy to run again (ZK-EVM + block-level access list)
- Verifiable RPCs, not blind trust (Helios Light Client)
- Private payments with public payment UX
- A wallet that transcends fragile seed phrase(social recovery)
- An unstoppable dapp UI (IPFS hosted)
- Censor-resistant Block Building (FOCIL)
Problem: Recentralization of Infrastructure
Even though the base layer remains decentralized, Ethereum's infrastructure is becoming increasingly centralized.
Nodes have evolved from laptop-friendly to requiring 800+ GB of storage and 24/7 synchronization. DApps have evolved from simple HTML pages into server-side monsters that leak your data everywhere. Wallets have shifted from user-controlled RPCs to hard-coded providers that track everything you do.
Most notably, 80-90% of Ethereum blocks are now produced by just two builders. This centralization means that transaction content is controlled by a small number of entities that can censor anything they want.
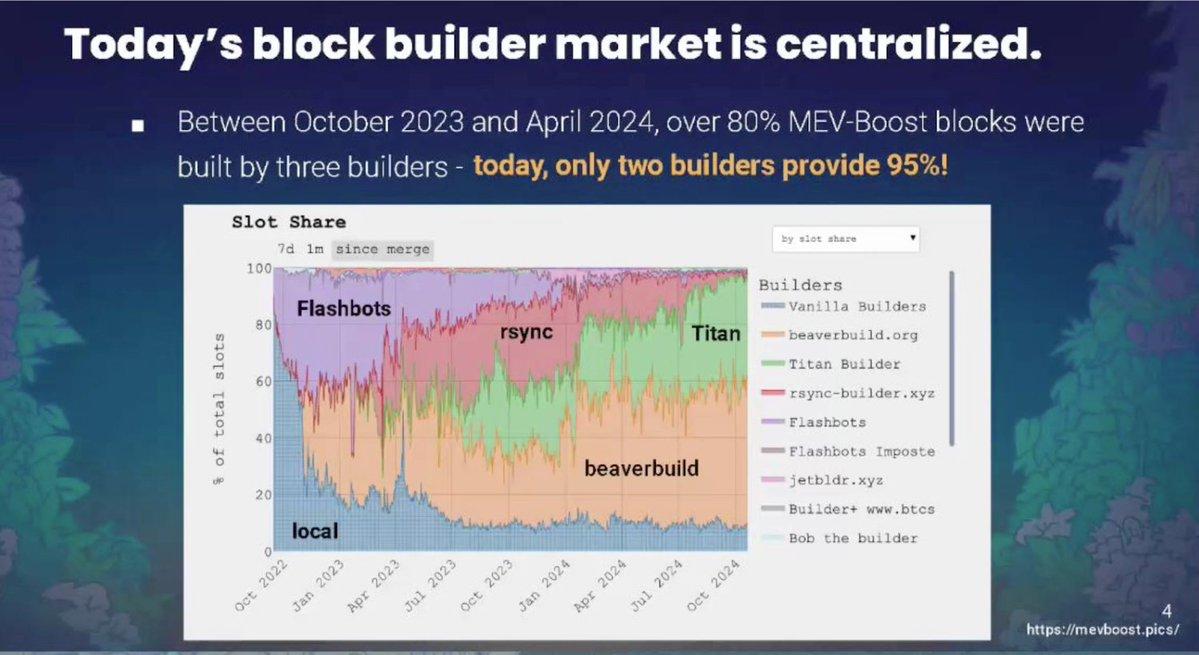
These are not mistakes; they are pragmatic choices made when scaling under proof-of-work constraints.
But the costs are real: the assumption of trust quietly creeps into "trustless" systems, single points of failure surge, and users lose true autonomy. We've decentralized the ledger, but recentralized the access layer.
The picture of 2026
Full node
The reality today: 800+ GB of storage, 24/7 synchronization, and continuous operation are required. Most users have given up.
Block-Level Access Lists (BALs) fundamentally change this. Think of the BAL as a directory for each block, telling you in advance which states a block will access. Your computer prefetches everything in parallel before execution begins. Conflicting transactions run concurrently on separate cores. Analysis shows that 60-80% of transactions are non-overlapping.
Combined with ZK proofs that verify blocks without re-executing everything, synchronization time is significantly reduced, and storage becomes manageable. Running nodes have moved from "infrastructure companies only" back to "decent laptops."
Helios: Validating RPCs
Imagine this attack: You're exchanging tokens on Uniswap. Your malicious RPC shows you fake prices. You sign in to accept fewer tokens than you're entitled to. The RPC performs a sandwich attack and keeps the profits. You never see it happen.
This hasn't happened with major providers yet, but it's technically possible. The problem: you're trusting someone else to tell you the state of the blockchain.
Helios resolves this in 2 seconds. It's a light client that tracks the validator "synchronization committee" (512 validators, approximately a 27-hour cycle). If 2/3+ of the block headers are signed, it's canonical. When you check the balance, Helios requests Merkle proofs from an untrusted RPC and verifies them locally. The RPC can refuse to answer but cannot lie.
It can run anywhere: laptops, mobile phones, browser extensions. Use it as your MetaMask RPC, and every dapp becomes trustless without requiring any other changes.
The technology exists today, is open source, and is ready for integration.
ORAM/PIR: Private RPC Query
Every RPC query reveals your behavior—which addresses you're observing, which protocols you're using, and when you're using them.
ORAM (Unintentional RAM) uses a tree structure to hide access patterns. The server sees the data you access but cannot determine which data it is. Signal Messenger uses this, which reduces costs by 100 times (from 500 servers to 6).
PIR (Private Information Retrieval) lets you query a database without revealing what you want. You send an encrypted query, the server processes the encrypted data, and you decrypt the answer. The response size remains constant (approximately 3KB) regardless of the database size.
A real-world implementation exists today:
- Oblivious Labs: Private WBTC Balance Checker
- Private ENS Analysis
- QuietRPC: Exploring Private RPC
The challenge is the dynamic state: recoding 33 million elements takes 4-20 minutes. The solution involves periodic snapshots with on-chain proofs. For most uses (balance checks, voting eligibility), a few minutes of staleness is acceptable for privacy guarantees.
Social Recovery: Beyond Vulnerability Seed Phrase
Current wallets force an impossible choice:
- Losing the seed phrase → Losing everything
- Seed phrase stolen → Lose everything
- Cloud Backup → Sovereignty Victimized by Backdoor
Social recovery distributes trust. You have a daily signing key plus "guardians" (friends, family, other devices). Recovery requires 3/5 guardian approval. A time lock (48-72 hours) prevents immediate theft while allowing legitimate recovery.
Dropped your phone into the lake? Contact the guardians, they approve a new key, the time lock is activated, and you regain access. If someone steals your key and tries to do the same, you cancel the time lock during its duration.
Security: An attacker needs to gain access to 3/5 of the guardians simultaneously. You have several days to respond. Each guardian has only partial power. There are no backdoors from tech companies.
Argent and other wallets support this today. The 2026 goal: to make it the standard everywhere, with a user experience that anyone can use.
Public UX for private payments
Privacy tools exist but are painful: different apps, terrible UX, 3-5 times the gas cost, and limited support. Almost no one uses them.
2026 Goal: Privacy = Public Experience. Same wallet, same interface, comparable costs. Privacy becomes a checkbox, not a research project.
Technology: zkSNARK (proves you have funds without revealing which ones), hidden addresses (one-time addresses for each transaction), and account abstraction integration.
FOCIL: Censorship-Resistant Privacy
If the builder refuses to include a private payment, the private payment is worthless. Since 80-90% of blocks come from two builders, censorship is easy.
FOCIL (Fork Select Force Include List) makes censorship impossible:
In each time slot, 16 validators are randomly selected to construct a "containment list" (8KB each) from the mempool transactions. The block builder must include these transactions. Proofers only vote for blocks that satisfy the containment list. Without voting, a block cannot become a canonical block.
Why it works:
- Based on the committee: Only 1 out of 16 honest validators is needed.
- Fork selection is mandatory: it's built into the consensus mechanism and cannot be bypassed.
- Same slot: No delay
- Any location within a block: The builder optimizes the MEV but cannot censor it.
Regarding privacy: If a validator contains your private transaction, it must be included in the block. The builder cannot censor it without incurring financial loss.
IPFS Hosted dApp
When you visit Uniswap, you load a web application from their servers. If the servers go down, you're locked out. If hacked in a second, a malicious UI can drain your wallet. Under pressure, they provide different UIs to different users.
IPFS solution: Uses content-addressable hosting UI (identified by a hash, not a server). Anyone can provide content. Changing the UI changes the hash. ENS maps friendly names to hashes.
Advantages: No single point of failure, impossible to hijack, resistant to censorship, verifiable.
Challenge: Updates mean new hashes. Solution: ENS records point to the latest hash, gradually decentralizing governance to DAO.
Why this is important
"In the world's computer, there is no centralized hegemon. There are no single points of failure. There is only love." — Vitalik Buterin
If Ethereum is just another platform that requires a trusted intermediary, why not use AWS?
The answer must be that Ethereum offers something truly different: true ownership, true permissionlessness, real censorship resistance, and true autonomy.
But these are only important when they are accessible. A system that is theoretically decentralized but accessed through centralized bottlenecks is merely a decentralized theater.
bet:
- Success: Ethereum has become the infrastructure of the open internet, users control their wealth/data, and privacy is the default.
- Failure: Regulatory capture at the access layer, users abandoning encryption in favor of honest CBDCs, the cypherpunk dream dies.
in conclusion
A pragmatic decade has proven the effectiveness of blockchain. Now we are proving that they are effective without abandoning their principles.
This won't all be released in the next version. Building a trustless system with a great UX takes time. Coordinating hundreds of developers will take even longer.
But commitment is absolute. Every decision is evaluated against the following criteria: Does it increase trust and autonomy?
2026 will be the year we decide that mainstream adoption at the expense of core values is not worthwhile. Decentralization that is "good enough" is not good enough. Users deserve something better than trusting infrastructure providers to access "trustless" networks.
Technical components are in place. Helios provides verifiable RPCs today. ORAM/PIR proves private queries are valid. Social recovery is present in production. Censorship resistance for FOCIL has been specified. The road is clear.
Now let Ethereum build it.







